In 2026, the era of 'checkbox compliance' is dead. For US-based founders in Health Tech, Fintech, and the Pharmacy Benefit Management (PBM) space, the landscape has shifted violently. The ability to demonstrate a verifiable, rigorous security posture is no longer just a luxury - it is the primary prerequisite for market participation.
US organizations today face a binary choice: build a fortress of verifiable security or accept market exclusion.
The shift is driven by a global threat environment that has rendered traditional checklists obsolete. But there is a silver lining. HITRUST certification has emerged as the definitive signal of trust in this chaotic market. The data backs this up: in 2024, environments maintained by HITRUST certified companies posted a staggering 99.41% breach-free rate, even as ransomware attacks decimated their non-certified peers.
For a founder, a HITRUST certification is more than a plaque on the wall; it is a strategic war chest. In the high-stakes world of B2B SaaS, it is often the single variable that differentiates a six-month sales cycle from a two-year stall. Major enterprise players like UnitedHealth Group, Kaiser Permanente, and Anthem now view HITRUST certification as non-negotiable in vendor contracts.
Note to founders: In U.S. healthcare, HITRUST certification in 2026 has become a proxy for risk maturity. HITRUST Alliance reporting shows certified organizations have been offered cyber insurance premium reductions of up to ~25%, with investors increasingly viewing certification as a trust signal.
What is HITRUST certification?
To define HITRUST certification accurately in 2026, we have to look past the acronyms. At its core, it is the validation of your security program against the HITRUST Common Security Framework (CSF).
Think of the CSF not as a static list of rules, but as a ‘superset’ of compliance. It harmonizes over 60 authoritative sources - including HIPAA, NIST SP 800-53, ISO 27001, PCI DSS, and the GDPR - into a single, certifiable standard.
The HITRUST Common Security Framework (CSF) solves the problem of fragmented compliance by replacing isolated security silos with a single, streamlined operational model:
- Harmonized Standards: The HITRUST framework integrates over 60 authoritative standards into a single, certifiable standard.
- Unified Assessment: Rather than juggling distinct audits for every partner, startups undergo one rigorous assessment to achieve HITRUST certification, demonstrating compliance across multiple domains.
- Universal Reporting: This single audit generates a report that simultaneously satisfies the unique requirements of hospitals, payers, and federal regulators.
Don't guess your security gap. See exactly where you stand in minutes. Start your free 14-day trial of ComplyJet today.
The v11.7 difference: Cyber Threat-Adaptability
This is where HITRUST certification separates itself from static models like SOC 2. A SOC 2 report captures a moment in time based on criteria that might not change for years. In contrast, HITRUST is ‘Cyber Threat-Adaptive’.
- Annual Evolution: The framework is updated no less than annually to reflect the current threat landscape.
- Real-Time Defense: The 2025-2026 updates introduced specific protections against ransomware and phishing derived directly from real-world threat intelligence.
When you adopt this framework, you aren't just applying for a HITRUST logo; you are implementing a living defense system that evolves as fast as the attackers do.
Who needs to upgrade from HIPAA to HITRUST?
One of the most frequent points of confusion for founders is HITRUST vs HIPAA. In 2026, the distinction is sharper than ever: HIPAA is the legal floor; HITRUST is the operational ceiling.
While every organization handling protected health information (PHI) must legally comply with HIPAA, the law itself has historically been vague. It often uses the term "addressable" to allow for flexibility, which, ironically, has created a massive lack of standardization.
This vagueness makes it nearly impossible for covered entities to trust the security of their business associates based on a self-attested HIPAA checklist alone.

The need to upgrade is no longer just about "best practices." It is being driven by three specific, high-pressure forces in 2026.
The regulatory push: HIPAA 2026 overhaul
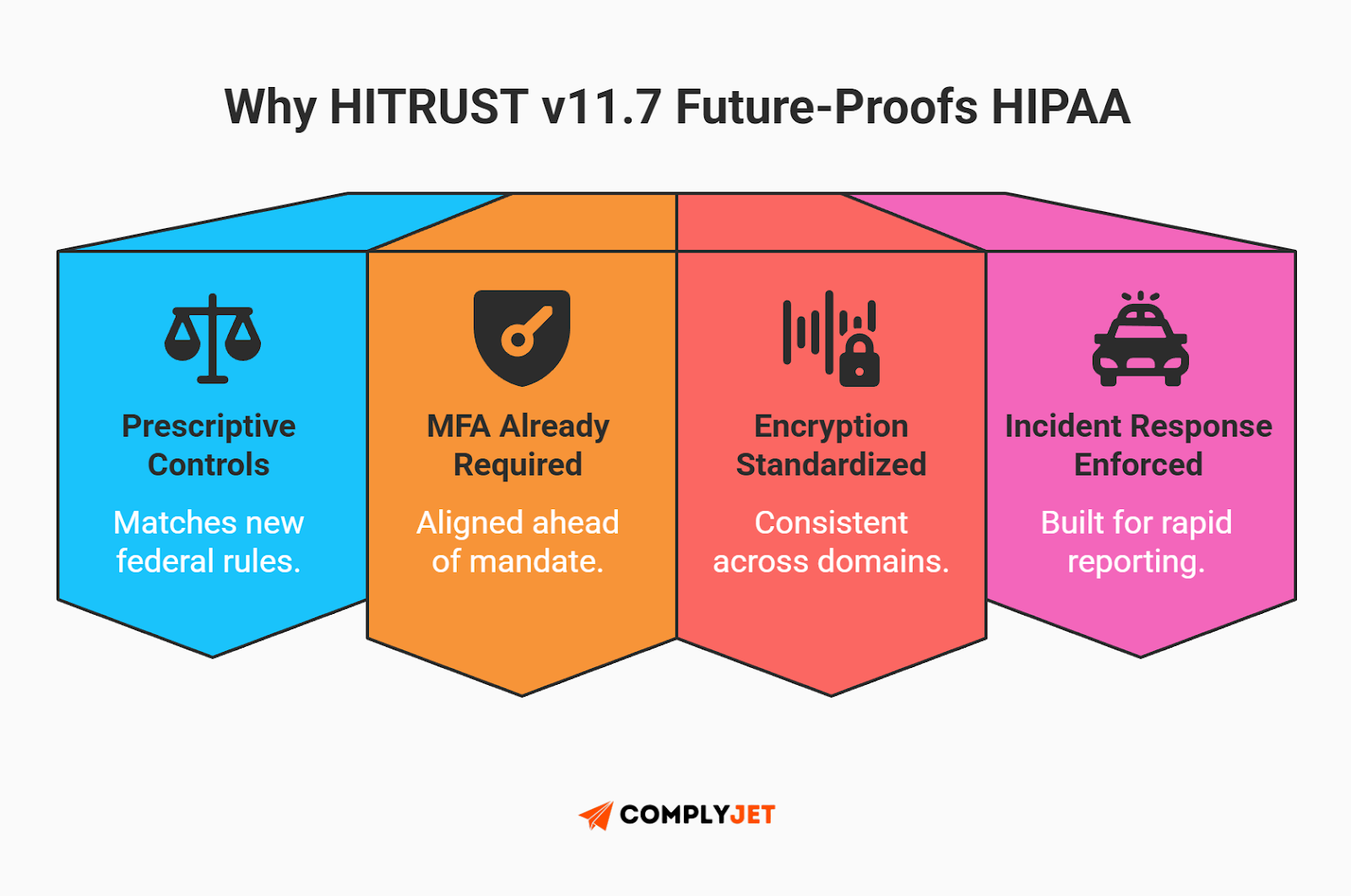
If you are relying on the flexibility of the old HIPAA rules, you are walking into a trap. The Department of Health and Human Services (HHS) has scheduled a final rule for May 2026 that modernizes the HIPAA Security Rule - the most significant shift in two decades.

The Shift: The core change is a move away from the flexible "addressable" implementation specifications toward rigid, "prescriptive" mandates. Things that used to be "good to have" are becoming federal requirements. Organizations pursuing HITRUST certification are effectively future-proofing themselves, as v11.7 is already aligned with these stricter standards.
HIPAA 2026 mandates vs. HITRUST certification alignment:
The market push: HITRUST for PBMs & the CAA 2026
Pharmacy Benefit Managers (PBMs) and the Fintech platforms that support them are currently in the crosshairs of the Consolidated Appropriations Act 2026 (CAA 2026). Signed in February 2026, this law introduces the most extensive reforms in history, specifically targeting transparency and fiduciary accountability.
The new law forces a massive shift in HITRUST for PBMs:
- Delinking Rebates: The law "delinks" PBM compensation from drug rebates in Medicare Part D. This forces the industry toward flat administrative fees and requires passing through 100% of rebates to payers, a process that HITRUST certification validates for transparency.
- The End of Spread Pricing: PBMs can no longer hide margins in "spread pricing" arrangements without disclosure.
The $10,000/Day Risk Transparency is now mandatory. PBMs must provide reporting on net spending and rebates semi-annually. The penalty for reporting failures is severe: civil monetary penalties of $10,000 per day.
In this environment, an r2 level HITRUST certification is the only way to prove your "black box" is actually a transparent, secure vault. Large players like Navitus have already moved to r2 to validate that their claims processing platforms meet these fiduciary standards. When a PBM is certified, it proves to regulators that the financial data being reported is accurate and protected.
The legal push: State laws & no more 'Cure Periods'
While federal laws grab the headlines, state laws are quietly removing your safety net. 2026 marks the arrival of new comprehensive privacy laws for HITRUST certification in Indiana, Kentucky, and Rhode Island.
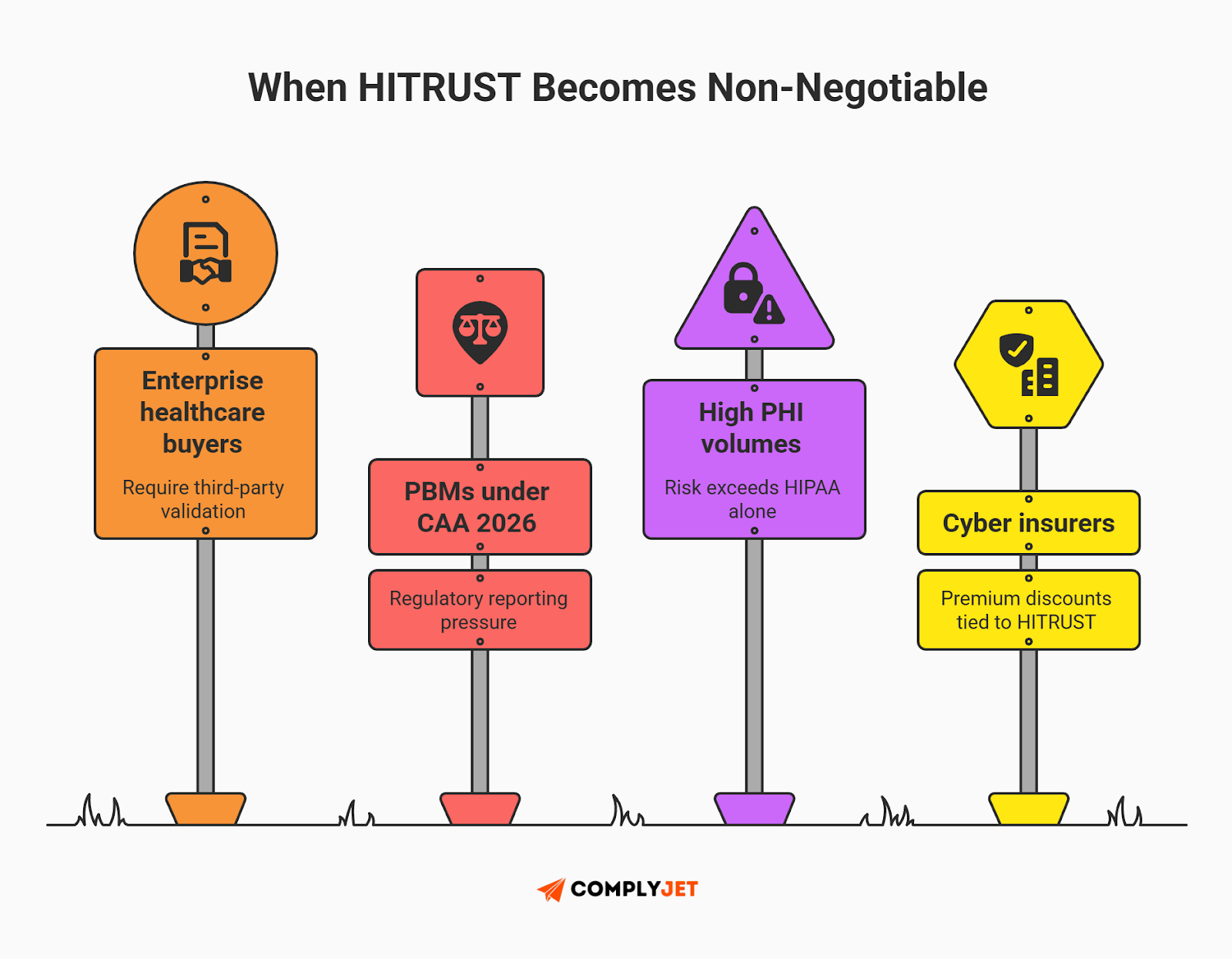
Most critically, existing privacy laws in California, Colorado, and Oregon are actively removing 'cure periods' in 2026.
- Previously: If you were caught violating a privacy statute, you had 30-60 days to "cure" (fix) the issue before being fined.
- Now: That grace period is gone. Businesses can be fined immediately for violations.
This creates an environment of immediate liability. HITRUST v11.7 solves this by providing a single framework that maps to all 50 state requirements, saving you from the nightmare of maintaining 50 separate compliance programs.
HITRUST certification levels
In 2026, the HITRUST Alliance offers three distinct HITRUST certification tiers. For a founder, the selection of the correct tier is a strategic decision that balances the level of assurance needed against the time and financial resources available.
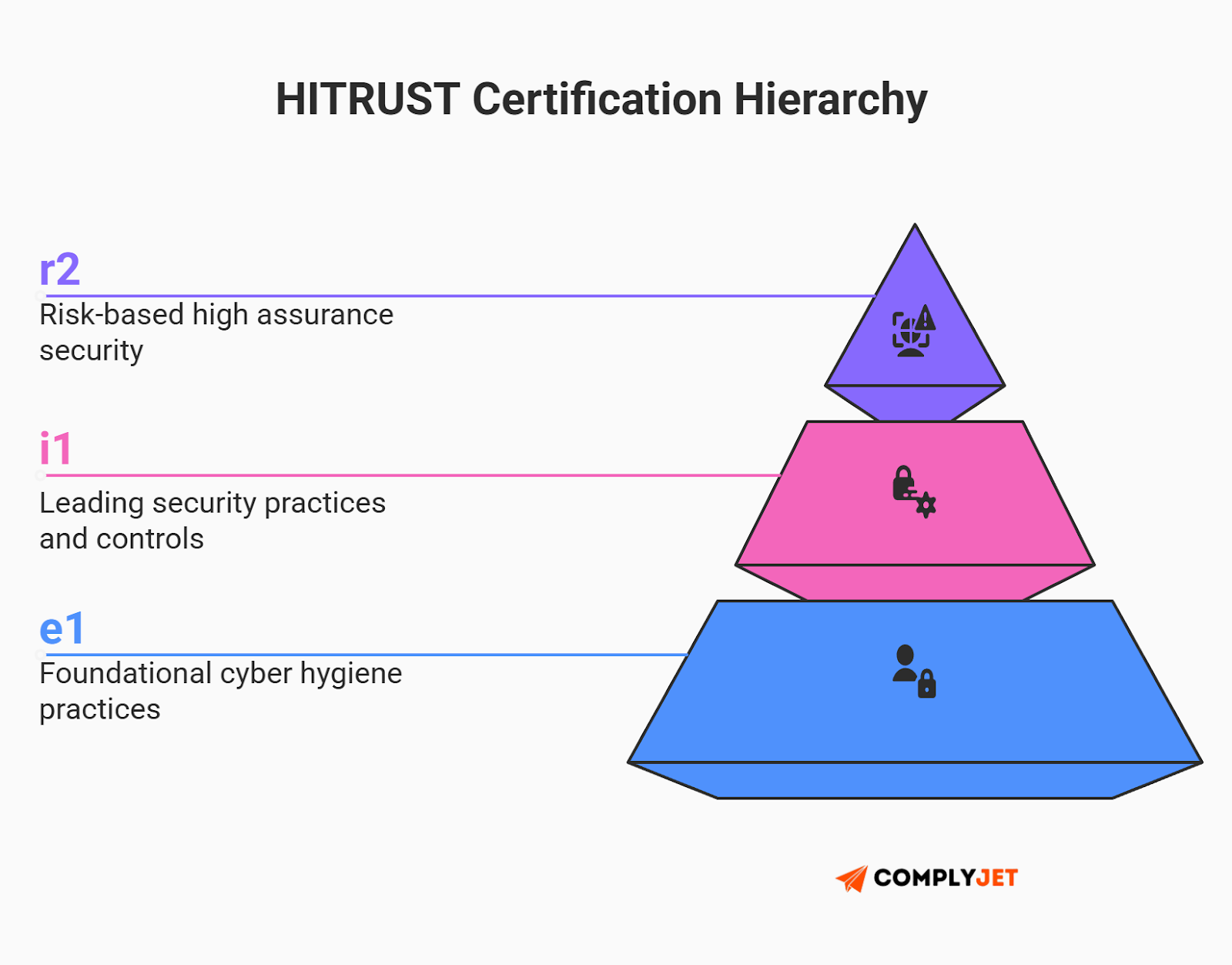
The genius of the modern framework lies in its scalability. Because all three HITRUST certification levels are built on the same Common Security Framework (CSF), you can start small and scale up. An organization can begin with an e1 to close its first few deals, and then progressively build toward an r2 without throwing away previous work. This allows you to scale your compliance maturity in lockstep with your revenue.
Here is how to choose the right vehicle for your current HITRUST certification stage:
HITRUST e1 (The essentials)
- Best For: Seed-stage startups and low-risk vendors.
- The Commitment: 44 requirements.
- Validity: 1 Year.
The e1 is the entry-level HITRUST certification, focusing strictly on "cyber hygiene" and foundational security practices. If you are a young startup and a hospital prospect asks for a third-party validation, the e1 is often your "minimum viable product" for compliance.
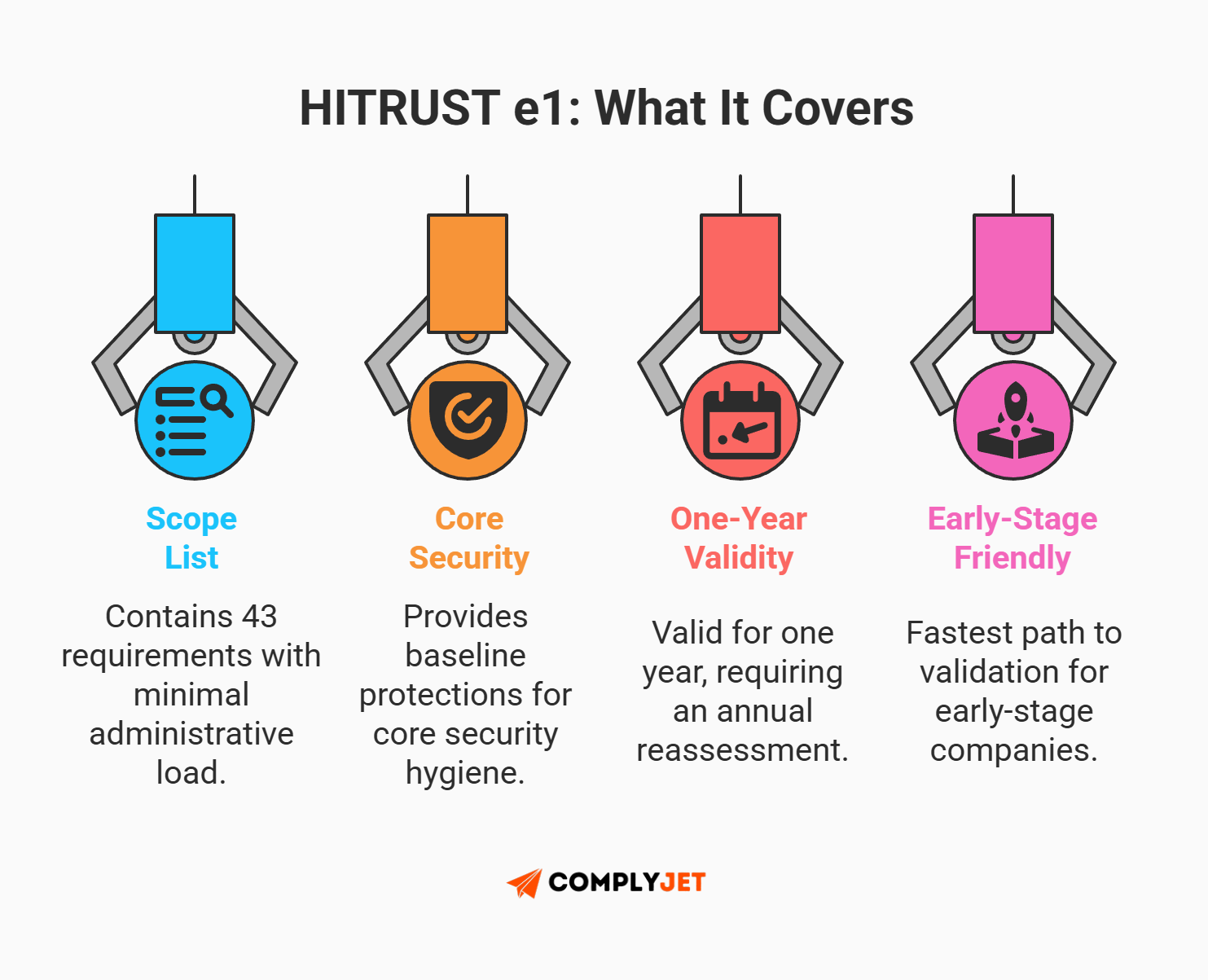
It covers the non-negotiables: User authorization, basic incident response, and patch management. The v11.7 update optimized this baseline to just 44 requirement statements, ensuring that small teams aren't crushed by administrative weight. It provides a low-effort way to demonstrate a validated security posture to early partners without burning 6 months of runway.
HITRUST i1 (Leading practices)
- Best For: Growth-stage companies.
- The Commitment: ~182 requirements.
- Validity: 1 Year (with a Year 2 shortcut).
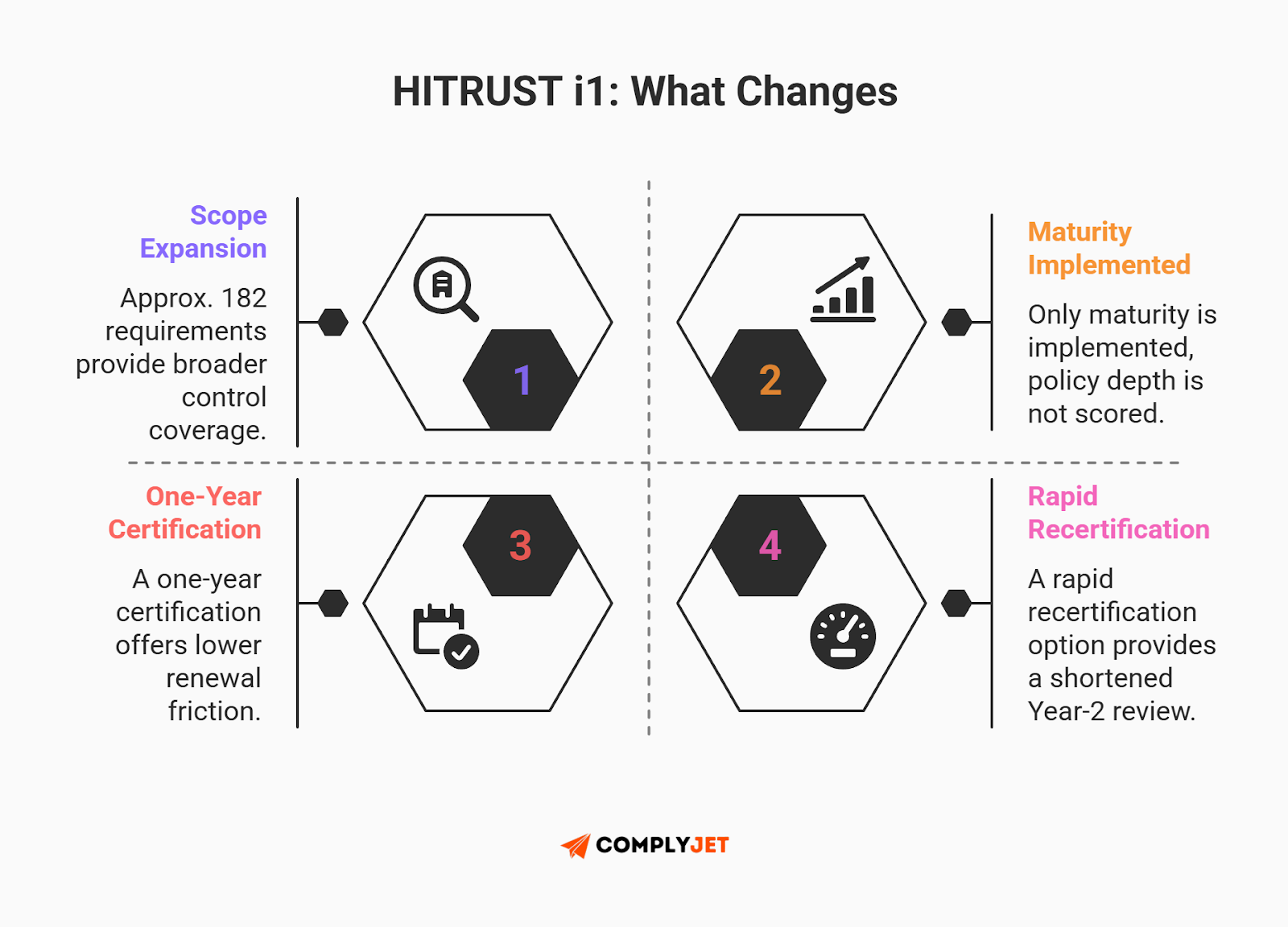
The i1 assessment is the middle ground, designed for organizations with established security programs that need more robust assurance than the e1. It tests against leading cybersecurity practices to address broader threats but keeps the scope manageable by only evaluating the ‘Implemented’ maturity level (ignoring Policy and Process documentation scores).
The Rapid Recertification Advantage: The killer feature of the i1 is the Rapid Recertification option. While the certification is valid for one year, in the second year - assuming your environment hasn't significantly degraded - you can undergo an abbreviated review. This focuses on a smaller subset of requirements, making the i1 a highly cost-effective option for growth-stage companies looking to maintain momentum.
HITRUST r2 (Risk-based high assurance)
- Best For: Enterprise, PBMs, and high-volume data handlers.
- The Commitment: 250 - 2,000+ controls.
- Validity: 2 Years.
The r2 is the Gold Standard. It is the most rigorous HITRUST assessment available and is the mandatory tier for PBMs reporting under the CAA 2026 or vendors handling massive volumes of sensitive health data.
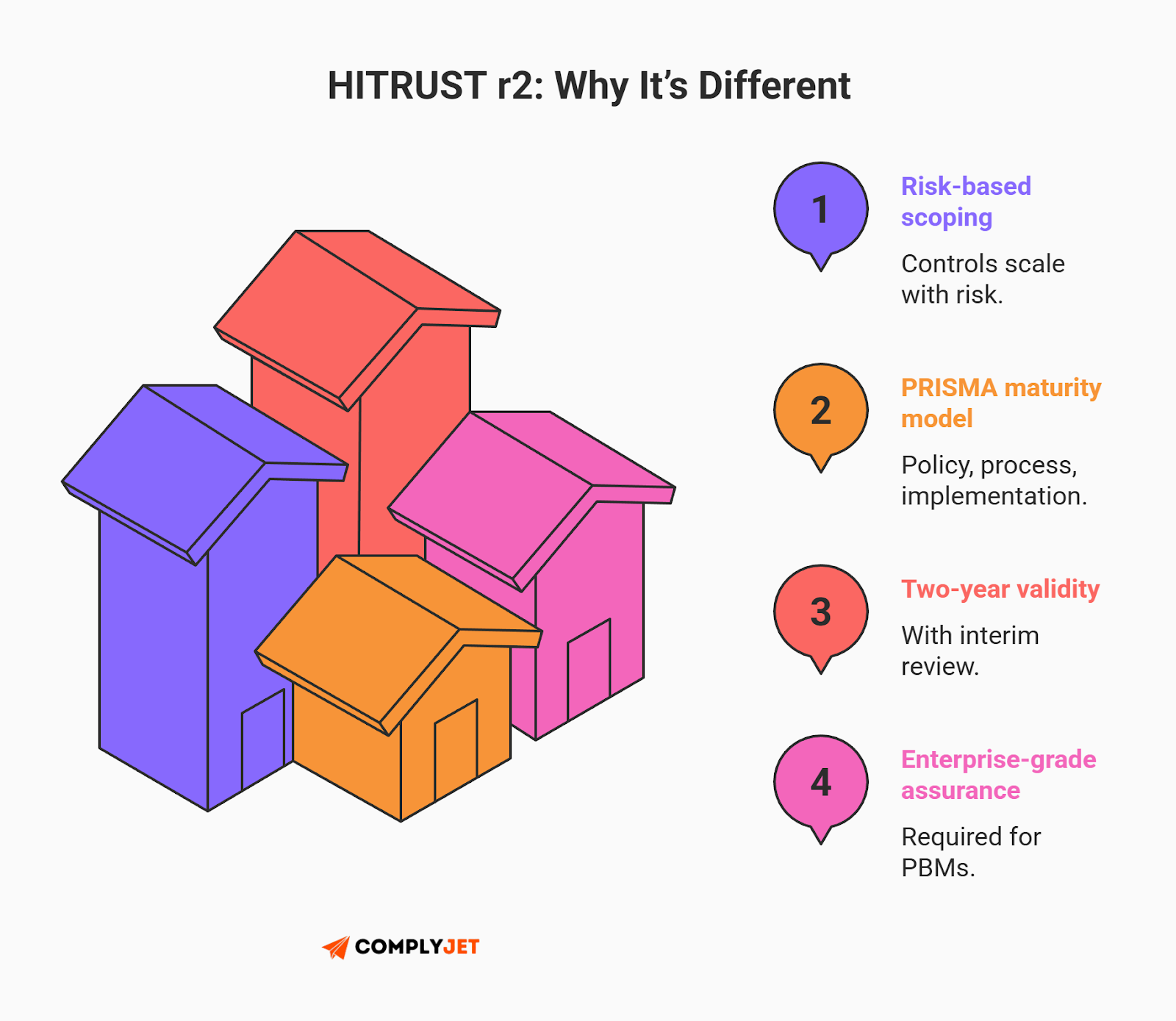
Unlike the e1 or i1, the r2 is predictive and risk-based. The number of controls scales based on your specific risk factors (volume of records, regulatory landscape, etc.). Crucially, it evaluates maturity across five levels (PRISMA), requiring you to prove not just that a control is "Implemented," but that it is backed by written "Policy" and "Process".
This is the certification that gets you into the room with UnitedHealth or Anthem. It is valid for two years, though it requires a mandatory interim assessment at the 12-month mark to ensure you haven't drifted.
Tip for founders: Confused about the tiers? Start where you are. Don't let a consultant oversell you an r2 if an e1 satisfies your current contracts. Use the scalability of the framework to let your compliance budget grow only when your revenue does.
HITRUST certification requirements
Achieving certification requires more than just configuring firewalls; it demands a documented ‘culture of security’. Similarly, unlike the broad SOC 2 controls, HITRUST has over 2000 prescriptive controls. To navigate the HITRUST certification requirements successfully, you must understand the two dimensions of the assessment: the Breadth (Domains) and the Depth (Maturity).
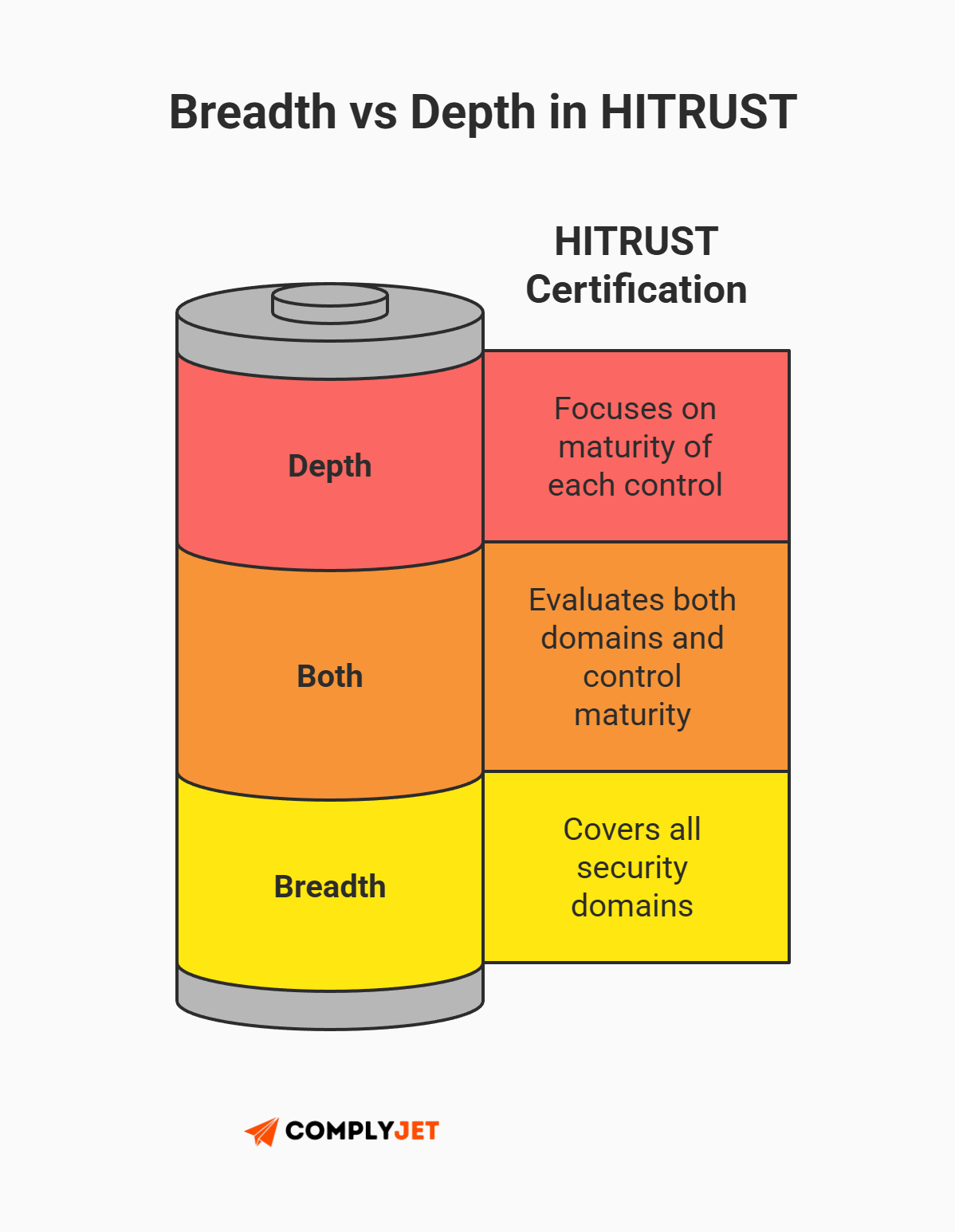
The breadth: 19 Domains of the CSF
The HITRUST framework is comprehensive. For an r2 certification, organizations must demonstrate compliance across 19 control domains. While you cannot ignore any of them, the heavy hitters that typically trip up founders include:
- Access Control: Role-based access, least privilege, and mandatory MFA.
- Incident Management: A tested plan for responding to breaches (crucial for the new 24-hour reporting rules).
- Third-Party Assurance: Vetting the security of your own vendors.
- Endpoint Protection: Securing laptops and mobile devices.
- Business Continuity: Ensuring operations survive a disaster.
The depth: PRISMA Maturity Model
This is where HITRUST certification may get tricky. Unlike binary pass/fail audits, the HITRUST common security framework uses the PRISMA scoring rubric to evaluate the maturity of each control.
- Policy: Is there a written rule defining the control?
- Process: Is there a step-by-step guide (procedure) for how to perform it?
- Implementation: Is the control currently active and working?
- Measured: Are you tracking metrics on its performance?
- Managed: Are you using those metrics to improve the control over time?
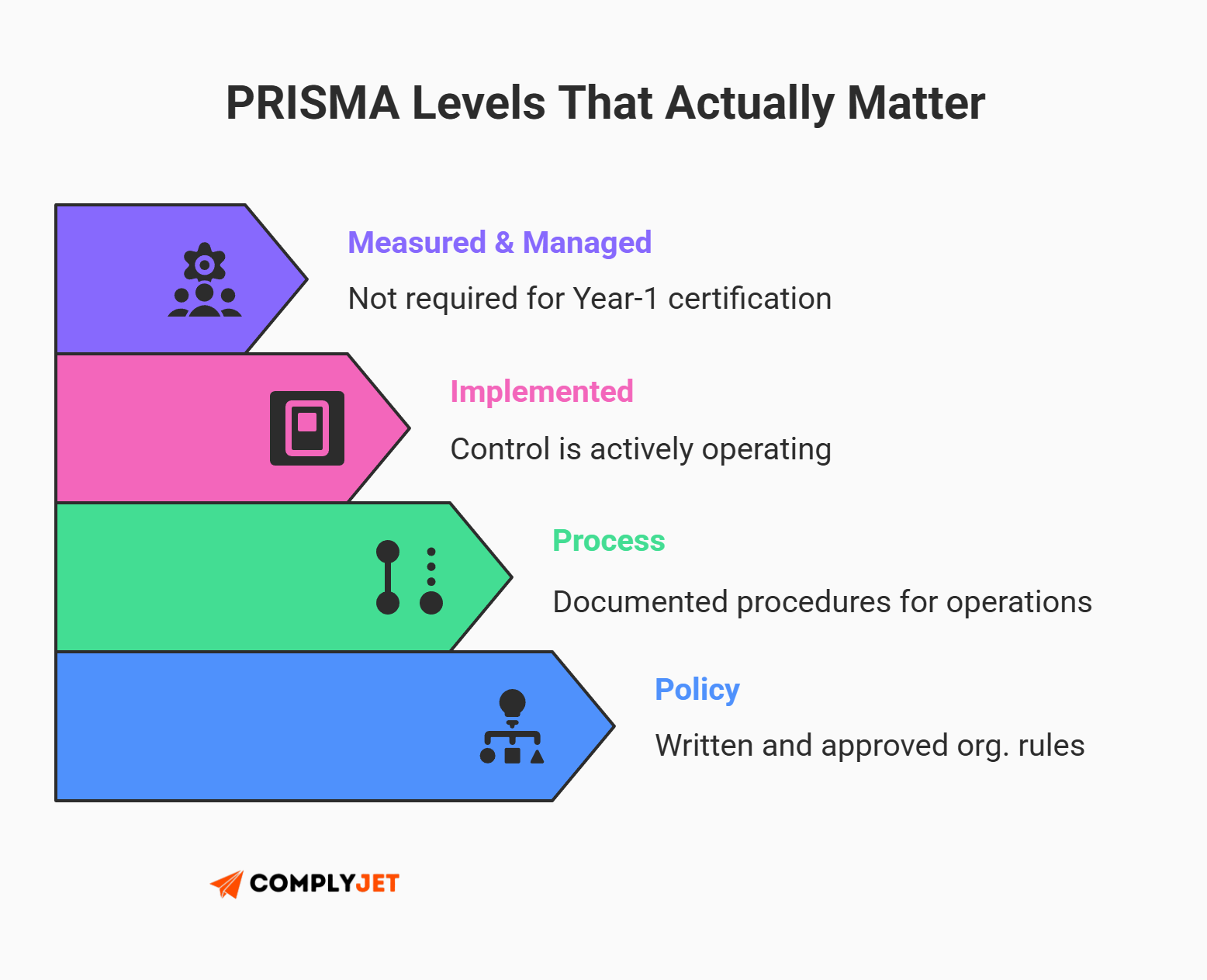
To pass an r2 assessment, you generally need a maturity score of at least "3" (on a 1-5 scale) for the first three categories.
Tip for founders: Don’t boil the ocean in Year 1. You don’t need “Measured” or “Managed” to pass HITRUST. Chasing metrics before policies and execution is how teams fail. Win with Policy, Process, and Implementation first. Optimize later.
HITRUST certification cost breakdown for 2026
Let’s be blunt: The total HITRUST certification cost can induce severe sticker shock. For a young founder, seeing a six-figure compliance line item feels like burning the runway.
However, the most successful founders in 2026 reframe this expense. They do not view it as a sunk cost; they view it as a capital asset. When you factor in reduced cyber insurance costs, lower breach risk, and smoother enterprise procurement, it’s no surprise that a HITRUST-commissioned Enterprise Strategy Group model shows certified organizations can achieve a modeled ROI of up to 464%.
The total cost is a combination of the check you write (Direct) and the time you burn (Indirect).
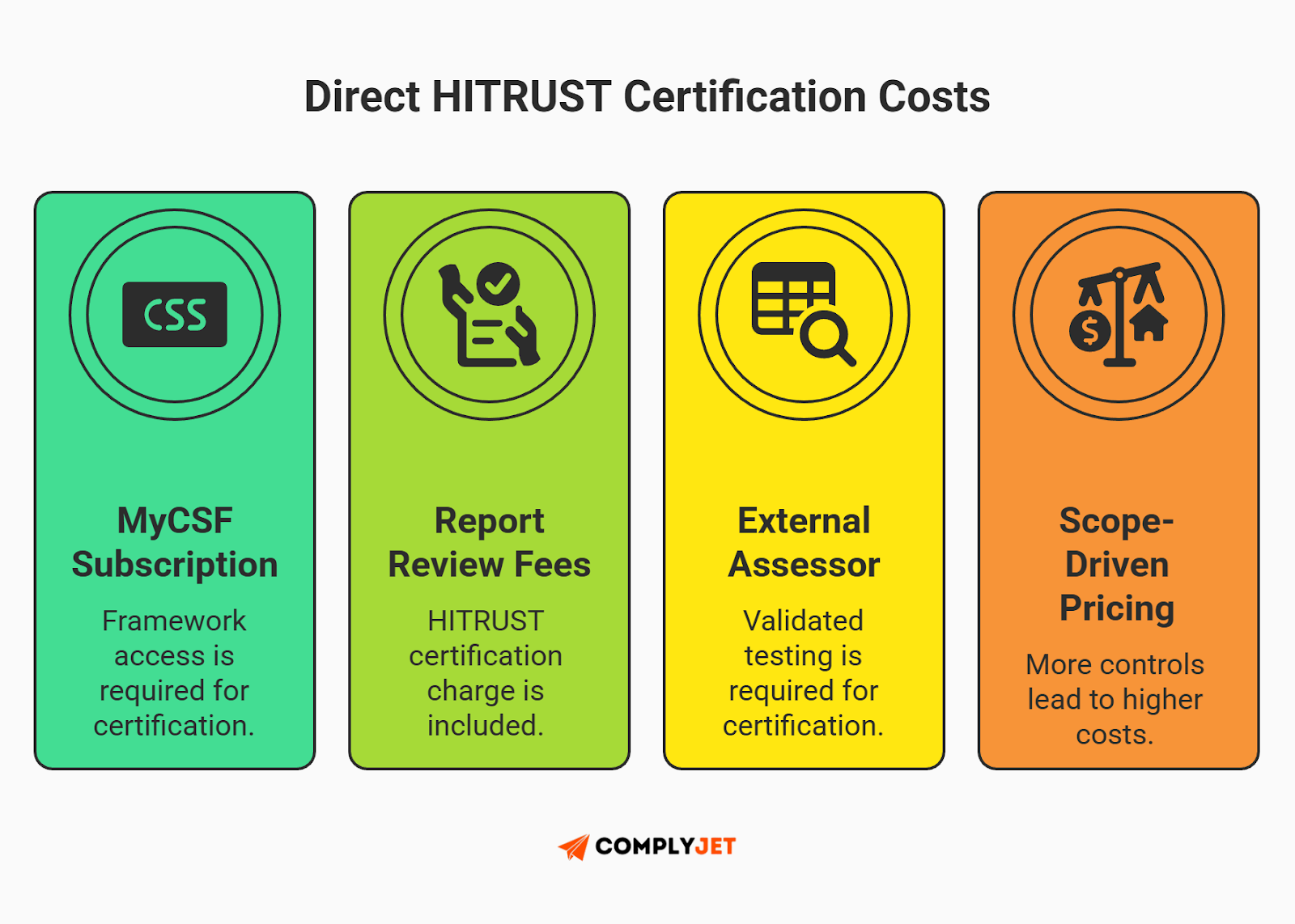
Direct costs
Your hard costs will flow to two entities: the HITRUST Alliance (for access/processing) and your external HITRUST auditors (for the testing).
Important Disclaimer: All quantitative metrics cited are derived from publicly released HITRUST Alliance reports and partner disclosures. They are meant to be noted as indicative and not definitive.
- MyCSF Subscription: Access to the MyCSF portal is mandatory for managing your assessment.
- Corporate Subscription: For long-term compliance, expect to pay approximately $18,100 per year.
- Assessment-Only Access: If you are bootstrapping, you can opt for a 90-day "assessment-only" access for $3,000 to $6,000, though this is less common for companies maintaining a continuous security program.
- Report Credits: You must pay HITRUST to review and certify your final report. These fees are tiered: ~$6,000 for e1, ~$7,000 for i1, and up to ~$9,000 for r2 assessments.
- External Assessor Fees: This is your largest expense. You must hire an authorized external assessor firm to perform the validated HITRUST audit.
- e1 Estimate: ~$20,000 - $40,000.
- i1 Estimate: ~$40,000 - $80,000.
- r2 Estimate: ~$60,000 - $150,000+.
Tip for founders: Scope carefully. Complexity costs: HITRUST r2 quotes may assume ~250 controls. Go beyond that, and auditors usually charge ~$50 per extra control. A bloated scope can quietly add $17,500+ to your bill.
Indirect costs
The 'hidden' HITRUST certification cost is your internal labor. Without automation, a typical HITRUST audit consumes 300 to 750+ hours of your team's time. That is engineering time spent taking screenshots instead of shipping code.
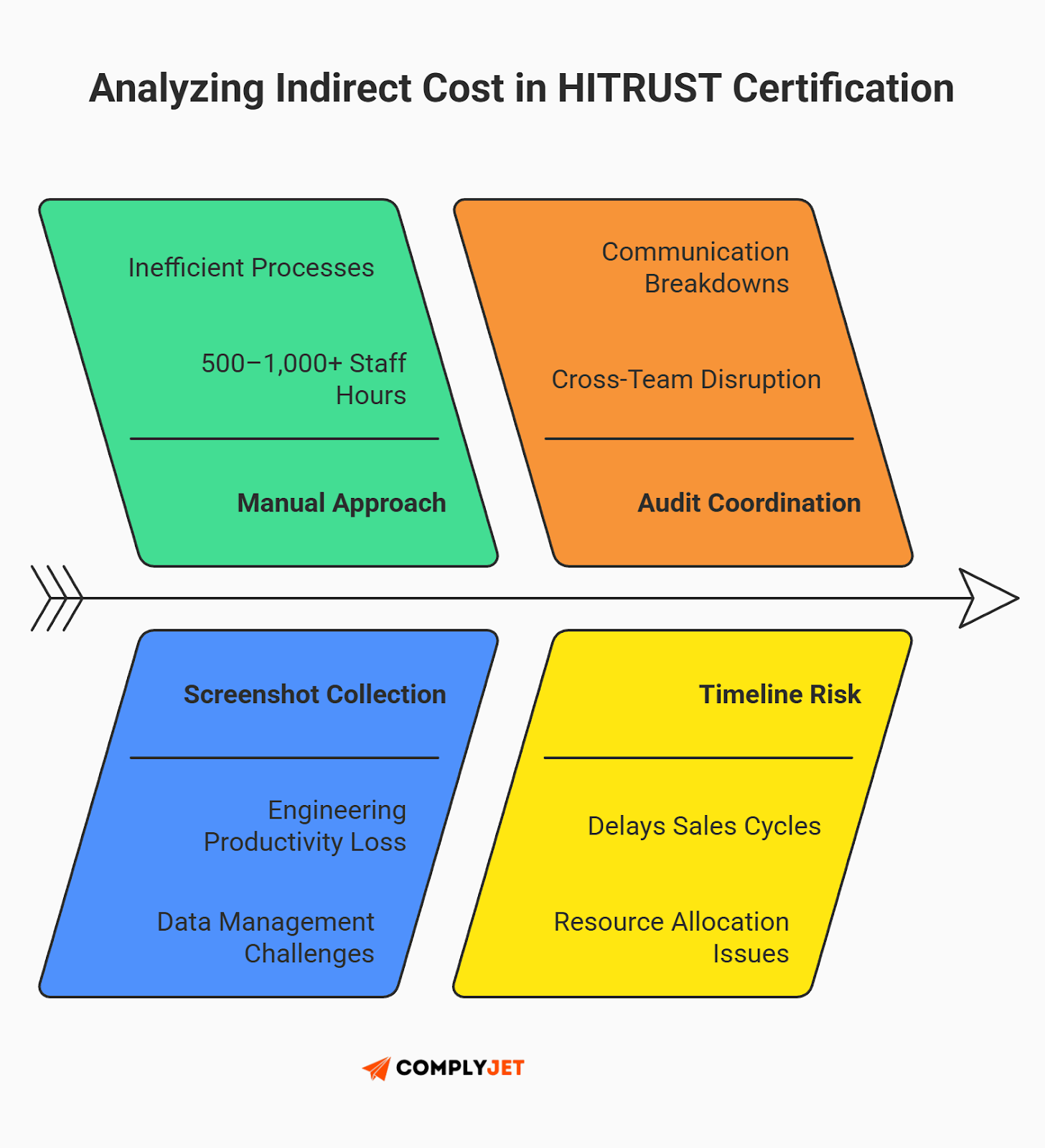
- The Manual Path: 500-1,000+ hours (Engineer/CTO time).
- The Automated Path: Smart founders in 2026 utilize GRC automation platforms like Vanta or Sprinto. While these tools add a subscription fee ($5k-$20k), they reduce the manual labor of evidence collection by up to 60%. Spending $15k on software to save $50k in engineering salary is a trade you should make every time.
Stop overpaying for compliance automation. Get HITRUST ready for 40% less than the competition. See ComplyJet’s startup-friendly pricing structure.
Common failures in HITRUST audits and how to fix them
A failed HITRUST audit in 2026 is rarely due to poor technical security; it is almost always due to documentation deficiencies or a failure to demonstrate control consistency.
If you feel overwhelmed, you are in good company. Statistics show that 62% of r2 assessments require at least one Corrective Action Plan (CAP) before they can be finalized. This means the majority of companies do not pass "clean" on their first try. However, understanding the most common failures in HITRUST audits can help you avoid the most expensive traps.
Failure 1: The 90-day evidence window
The Trap: Timing is everything. A unique and rigid requirement of HITRUST is that all technical testing and evidence must be performed within a mandatory 90-day window before the assessment date.
Many founders fail because they treat evidence collection like a college term paper - starting too early or too late. If you take a screenshot of your firewall configuration 95 days before your submission, that evidence is void. You will be forced to redo the work, delaying your certification and burning engineering hours.
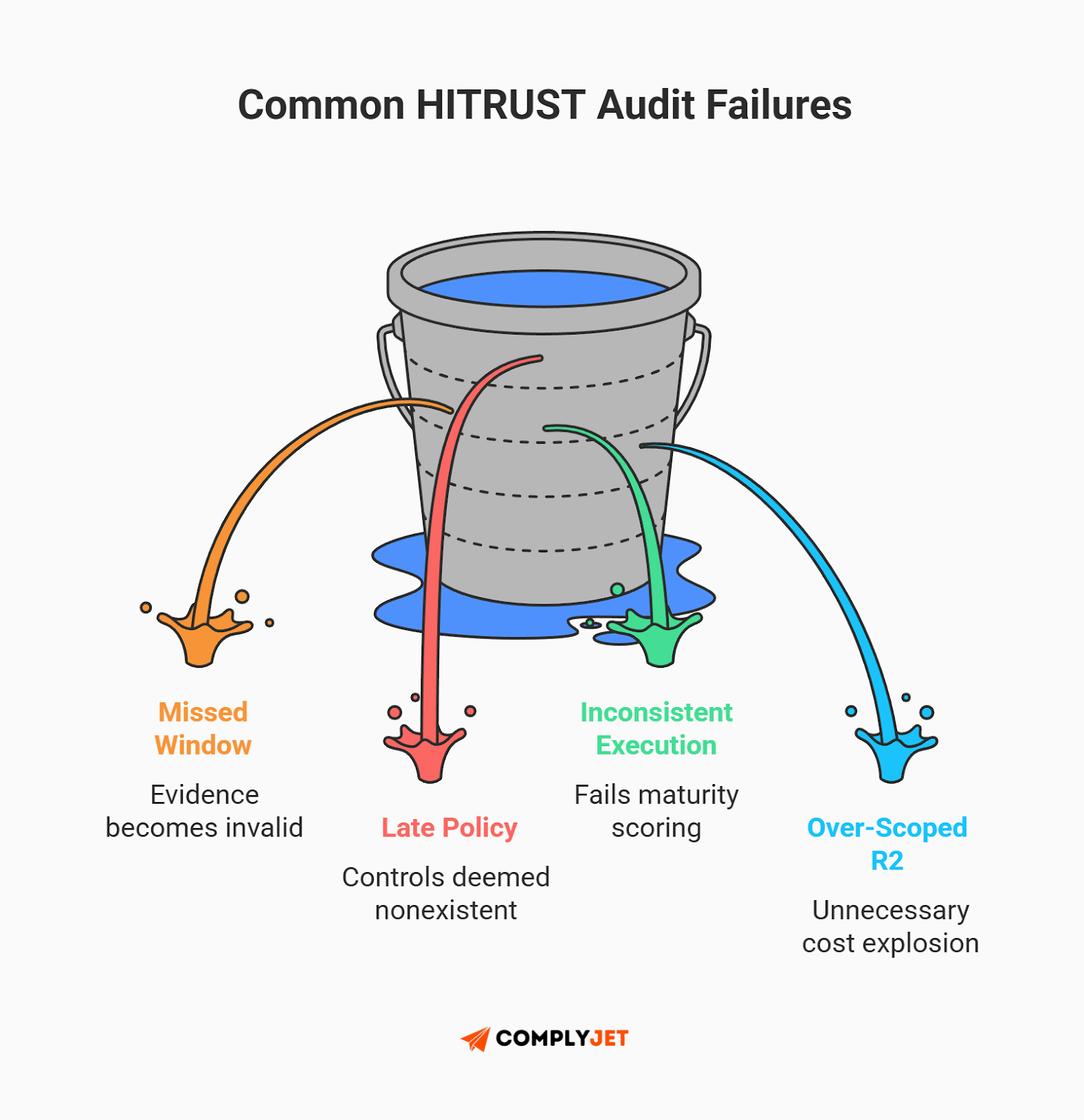
Failure 2: "If it's not written, it doesn't exist"
The Trap: HITRUST is an evidence-based framework, not a "trust me" framework. If a security control is not documented in a formal policy and procedure, it does not exist in the eyes of the auditor.
Crucially, policies must be in place for at least 60 days before the audit begins. You cannot frantically write your "Incident Response Policy" the night before the auditors arrive. If the policy wasn't active and governing your organization for that 60-day window, you will fail that control.
The fix: External Inheritance
You do not need to secure the entire stack yourself. The smartest way to reduce failure risk is to make use of HITRUST assessments that have already been completed by your cloud providers.
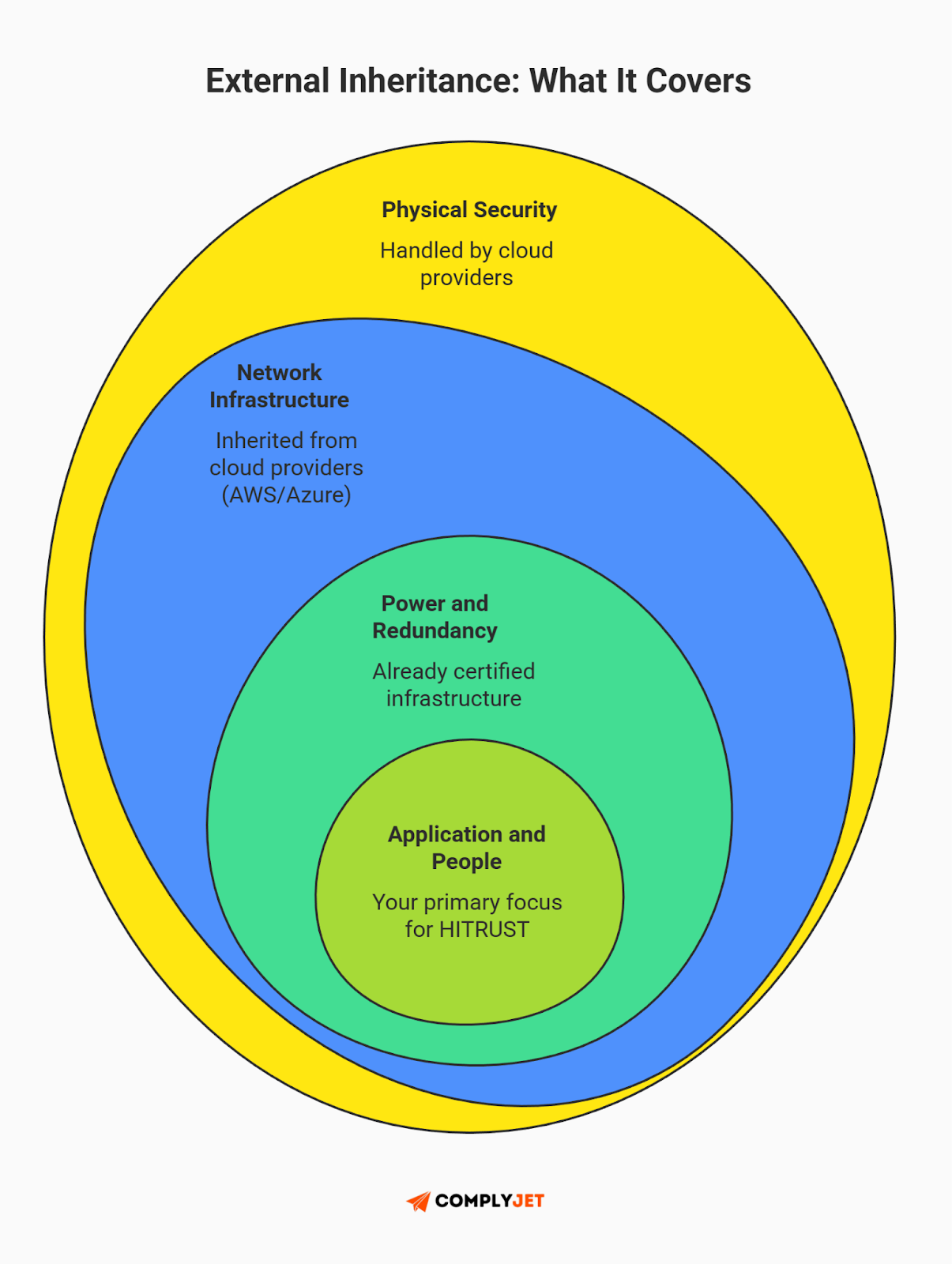
This concept is called External Inheritance and is a massive efficiency hack. If you host on AWS, Microsoft Azure, or Google Cloud, they have already achieved HITRUST certification for their physical data centers and network infrastructure. You can ‘inherit’ their scores for those controls rather than testing them yourself.
Stat Check: HITRUST Alliance's reports indicate that in 2024, nearly 70% of r2 assessments used inheritance, resulting in a 14% reduction in total assessment hours. By inheriting the hard stuff (physical security, power, network redundancy), you free up your team to focus strictly on the controls you actually own - your application and your people.
Future trends: AI & the modern threat landscape
The most significant shift for those seeking HITRUST certification in 2026, is the convergence of cybersecurity with AI governance. As US enterprises rush to integrate Generative AI and Large Language Models (LLMs) into their products, they are creating massive new attack surfaces that traditional security frameworks were never designed to protect.
HITRUST has responded to this shift by evolving the HITRUST framework into a comprehensive tool for securing the entire "AI Stack."
Securing the AI Stack
It is no longer enough to just secure the database where your user info lives. In 2026, you must secure the training data, the model weights, and the inference engine itself.
- The Threat: Adversarial attacks can poison training data or trick models into revealing sensitive PHI (data leakage).
- The Solution: The HITRUST AI Security Assessment evaluates these specific layers. It covers providers of generative AI, predictive machine learning, and rule-based expert systems, addressing risks from the underlying data to the final model output.
The AI Add-on Strategy
For founders, the best news is that you do not need a separate, disjointed audit for your AI features. HITRUST allows you to treat AI security as an "Add-on". You can pair these AI-specific controls directly with your standard e1, i1, or r2 assessment.
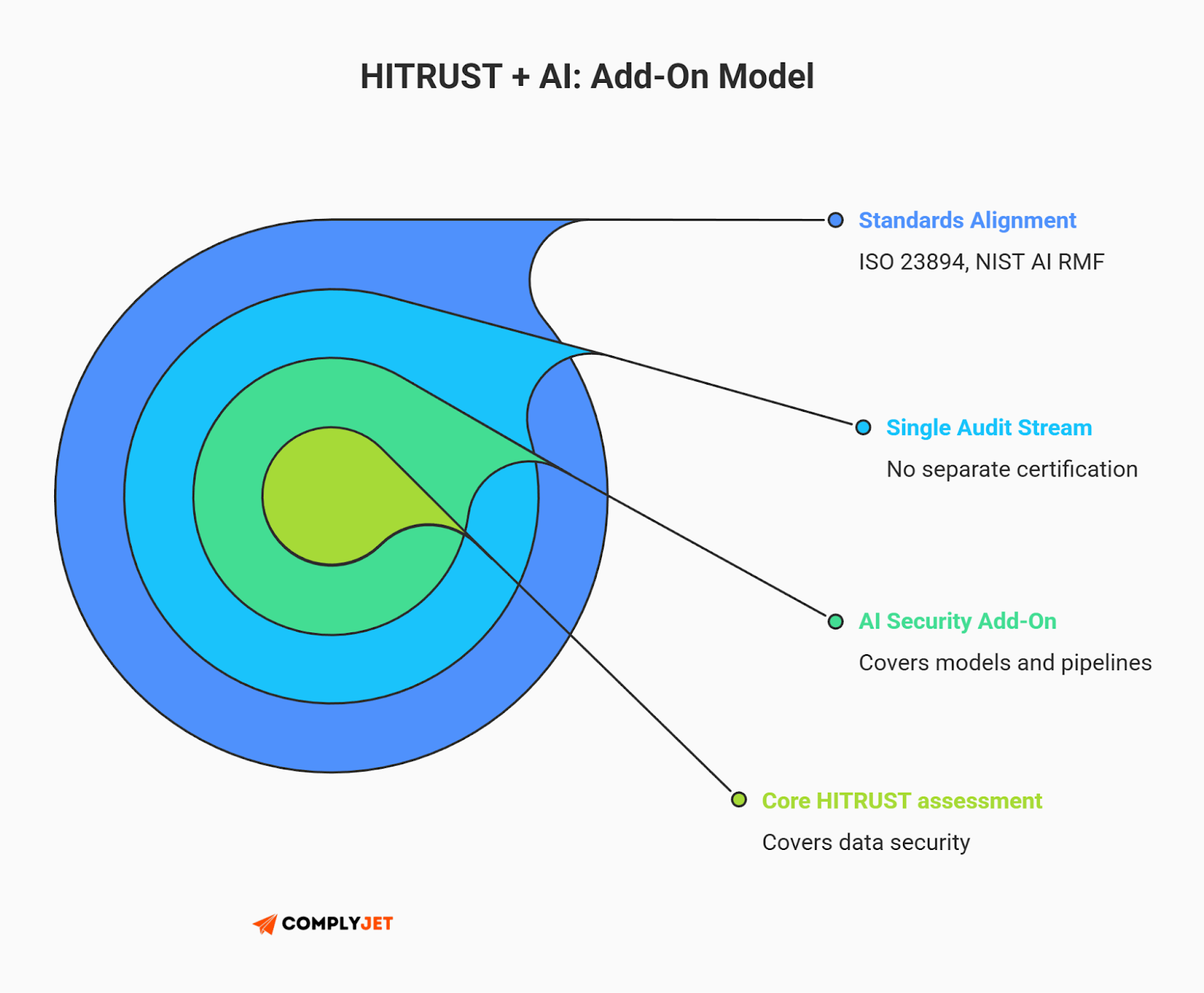
This allows you to meet multiple compliance needs - HIPAA for your data and AI security for your algorithms - within a single, streamlined solution.
Tip for founders: The new AI Risk Management Assessment is harmonized with ISO 23894 and the NIST AI RMF. This means that by adopting the HITRUST framework for your AI today, you are automatically aligning with international standards, reporting on your AI performance in terms that global partners understand.
FAQs for 2026 HITRUST certification
How do I fast track the HITRUST certification program?
Use "External Inheritance" from cloud providers (AWS/Azure) to save 14% of assessment hours. Pair this with GRC automation tools like Vanta or ComplyJet to cut manual evidence collection by 80%, reaching e1 readiness in as little as 80 labor hours. This is the only way to fast track HITRUST certification program timelines effectively.
Is HITRUST certification worth it for US startups in 2026?
HITRUST certification is worth it for US startups when it directly enables enterprise deals or shortens security reviews. In healthcare and regulated fintech, many buyers treat HITRUST as a baseline trust signal rather than a differentiator.
How much does HITRUST certification cost for a US startup?
For US startups in 2026, HITRUST certification typically costs $35,000 to $100,000+, depending on the assessment tier (e1, i1, or r2), scope, and use of automation. Most early-stage companies reduce cost by starting with e1 or i1 and scaling over time.
Can a startup skip r2 and just do e1?
Yes. HITRUST e1 is designed specifically for low-risk startups. It serves as a foundational "cyber hygiene" badge and acts as a traversable stepping stone to i1 or r2 as you scale.
Do PBMs need HITRUST certification in 2026?
PBMs must meet CAA 2026 transparency mandates or face $10,000-per-day civil penalties. HITRUST r2 certification provides the mandatory third-party validation to satisfy these fiduciary reporting requirements.
What is the difference between HIPAA and HITRUST?
HIPAA is the vague legal floor ("addressable"); HITRUST certification is the prescriptive operational ceiling. HITRUST translates ambiguous laws into a verifiable, testable control set that auditors can actually certify.
How much does the MyCSF portal cost?
Corporate subscriptions start at ~$18,100/year for full analytics. Bootstrapped startups can opt for 90-day "assessment-only" access for $3,000-$6,000, though this sacrifices continuous compliance tracking.
What is i1 Rapid Recertification?
For HITRUST i1 holders, Year 2 offers a "Rapid Recertification". If your environment hasn't degraded, this abbreviated review assesses fewer requirements, saving significant time and money.
Is HITRUST valid globally?
Yes. While rooted in US healthcare, HITRUST integrates GDPR and ISO 27001. A single certification demonstrates compliance to international partners in Europe and Asia without separate audits.
Do ISO 27001 controls map to HITRUST certification?
Yes. HITRUST builds on ISO 27001 clauses but adds depth. While ISO 27001 uses 93 broad controls for management, HITRUST expands this to over 2,000 prescriptive controls for high-risk environments.
What happens if I fail the QA review?
Failures usually trigger a Corrective Action Plan (CAP), not a rejection. Common causes are missing documentation (policies/inventories) or failing to implement controls within the mandatory 90-day evidence window.
Does HITRUST prevent all breaches?
No, but certified environments boasted a 99.41% breach-free rate in 2024. Of the few breaches, 50% stemmed from unpatched vulnerability exploits, not control failures.
When does HITRUST certification become mandatory in the US?
HITRUST certification becomes effectively mandatory in the US when customers, regulators, or insurers require independent security validation beyond HIPAA. In 2026, this is increasingly driven by HIPAA Security Rule changes and healthcare supply-chain risk requirements.
The final takeaway
In 2026, HITRUST certification has moved beyond the realm of technical compliance to become a core component of enterprise risk management and business strategy.
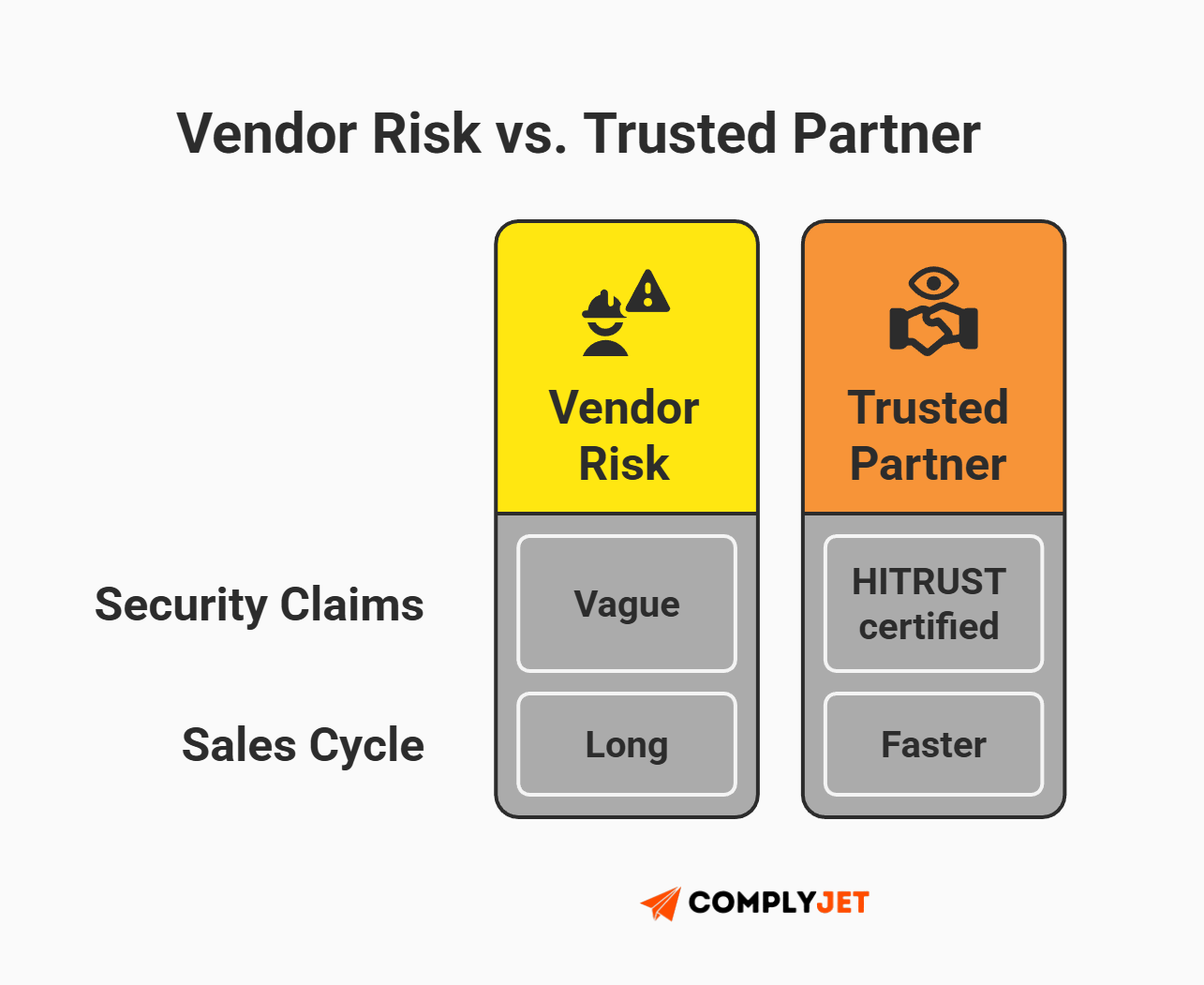
The market has drawn a line in the sand. On one side are Vendor Risks - companies with vague security claims and slow sales cycles. On the other are HITRUST certified companies - organizations that have transformed compliance into a competitive moat. By achieving this standard, you stop asking for trust and start proving it, effectively moving your brand from a potential liability to a "Trusted Partner" in the eyes of enterprise buyers.
This shift has also ushered in a host of lucrative careers pertaining to GRC and cybersecurity in the tech sector, the details of which you can find in our definitive guide to a successful career in GRC.
The path to the first page of market relevance involves choosing the right HITRUST certification assessment tier - starting with e1 to establish a baseline, then maturing to i1 or r2 as regulatory requirements like the CAA 2026 and the new HIPAA Security Rule take hold.
Don't navigate this shift alone. Book a demo with ComplyJet's founder today to figure out which HITRUST tier is right for your needs, and build a compliance roadmap that scales with your revenue.



