Information security is not a mere checkbox exercise anymore, but a crucial condition to earn your customer’s trust. And that trust is exactly what keeps million-dollar businesses hanging in the balance.
Among all the compliance frameworks existing, ISO 27001 certifications give your company a globally recognised way of proving your commitment to safeguarding data & systems.
Particularly, ISO 27001 for startups builds confidence to climb those mountainous enterprise deals, where even a minor mistake can become a roadblock to closing deals.
In this guide, you will learn how ISO 27001 works, and we’ll walk you through implementation, timelines, certification cost, and common challenges. If you're a part of a young team still prepping for its first audit, check out our article focusing on running an ISO 27001 internal audit.
If you want personalised guidance on ISO 27001 for startups, have a chat with the founders; they are experts in the security domain with over a decade of experience.
Let’s dive into the article.
What is ISO 27001?
ISO 27001 is an international standard jointly developed by both ISO and IEC. It is known as the best standard for information security management systems (ISMS).
In simple terms, the ISO 27001:2022 framework has 2 parts:
- Part 1:Includes clauses 0-10. Clauses 0-3 contain Introduction, Scope, Normative references, Terms and definitions. Clauses 4 -10 are mandatory requirements to set up an ISMS and achieve ISO 27001 certification.
- Part 2: It contains Annex A, a list of 93 controls categorised into 4 types- Organisational, People, Physical, and Technological. These controls aren’t mandatory, but they support the clauses of ISO 27001 and their requirements.
This risk-driven framework defines the required standards that companies of any size can use to minimise security risks and protect sensitive data by:
- Identifying your information risks
- Applying appropriate controls( Annex A)
- Ongoing monitoring and improvements
ISO 27001 for startups, smaller teams, and organisations means replacing ad-hoc security measures with a structured, systematic, and secure process.
You can follow this holistic approach to establish the process to perform risk assessment, draft controls and policies, and implement security checks that fit your organisation’s needs.
An ISMS helps your organisation prevent costly information security mistakes. It helps manage people, processes, technology, and vendors.
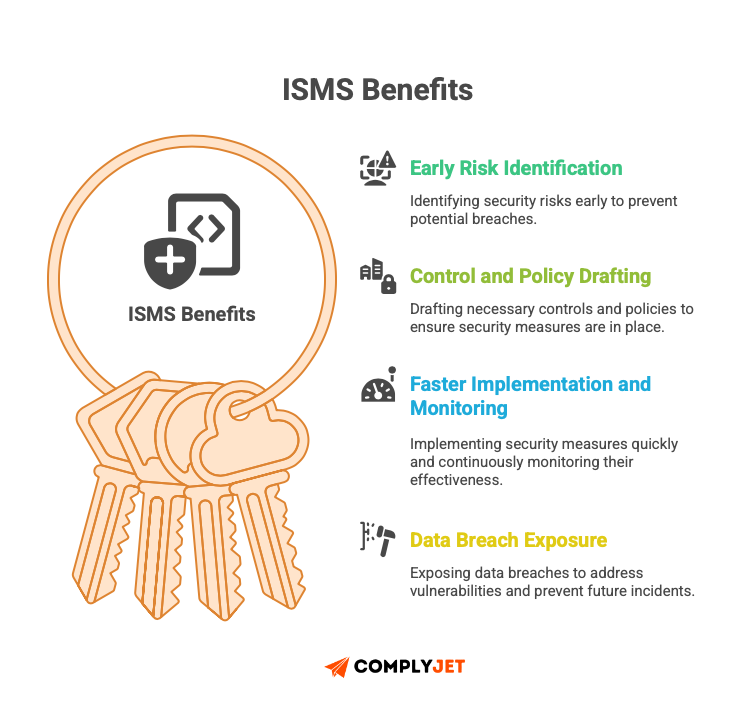
This standard’s real outcome includes an ISMS policy, risk treatment plan, statement of applicability, and audit records, which stand as concrete artefacts to show your customers and investors.
Core Philosophy of ISO 27001: CIA Triad
ISO 27001 is built on the core idea of the CIA triad – Confidentiality, Integrity, and Availability. Each principle covers a key aspect of information security.
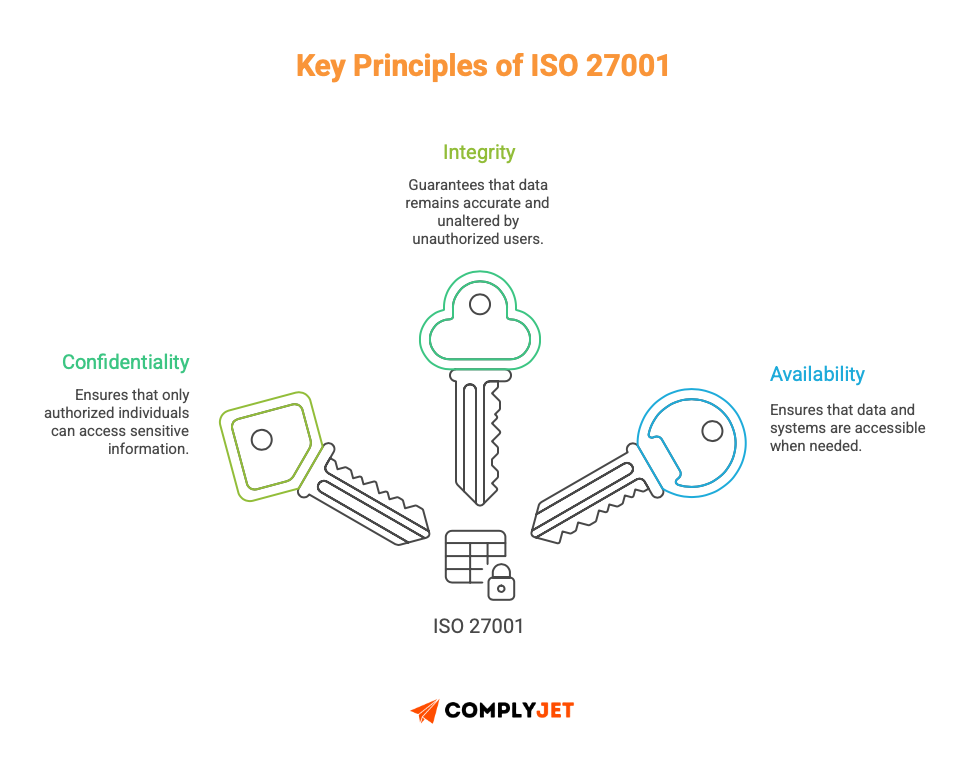
- Confidentiality: Ensure only authorised persons can access the systems and important information.
- Integrity: Ensures that only properly authorised persons can change the data in systems.
- Availability: Ensure authorised users can access the necessary data whenever they need it (via backups and redundancy).
ISO 27001 for Startups: Should You Start Early or Wait? Every Founder’s Dilemma
For many founders, ISO 27001 feels like one of those things you'll get to someday in your compliance journey; maybe after product-market fit, after revenue stabilizes, or after the next funding round. But in reality, waiting too long often becomes a growth bottleneck.
Especially if your company is a global market, and European countries are targeted, you cannot miss this framework.
Here’s the pattern across most fast-moving startups:
- You don’t need ISO 27001 on Day 1,
- But you absolutely feel the pain when a major customer suddenly demands it.
A common question among founders:
Should we get ISO 27001 certified before deals slip away, or should we wait until it's unavoidable?
The smarter path is usually to start early enough to avoid delays, but lean enough to not stall your product roadmap.
Early-stage companies that begin with foundational security policies, basic risk assessments, and lightweight controls can drastically shorten their certification timeline later.
Instead of scrambling when an enterprise prospect asks you for: ‘Can you share your ISO 27001 certification?’
If your startup handles customer data, integrates with enterprise systems, or plans to sell globally, the cost of waiting is often far greater than the cost of starting early.
Myth vs Fact: Is ISO 27001 Only for Large Teams?
A general myth among startups and small teams is that ISO 27001 is only meant for large organizations with big security teams and complex infrastructure.
But the fact is, ISO 27001 is designed for companies of any size, including 5–20 member startups.
The standard doesn’t prescribe headcount, technology, or maturity of the company. It simply requires you to evaluate your risks and implement controls proportionate to your business.
In fact, small teams have a hidden advantage:
- Fewer systems → easier to map data flows
- Fewer stakeholders → faster policy implementation
- Less bureaucracy → smoother audits
Today, most high-growth SaaS startups achieve ISO 27001 with a lean team consisting of a founder, a PM, and sometimes an engineering lead.
One such example is DETOXI, a German digital health startup founded in 2024. Their mission is to help combat digital stress and online addiction.
When they decided to partner with German public health insurance for funds, it was an idea that could potentially reshape their revenue trajectory.
One thing that was non-negotiable was ISO 27001 Certification.
With only 4 employees and bigger dreams, they had strong internal security practices, but no formal ISMS, no audit history. That seemed like a complex task to achieve a mandatory requirement for collaboration.
With constraints like limited resources, endless security questionnaires, and no in-house compliance team, the chief production officer knew they needed a structured process and practical tools to navigate this.
The idea that you need a large security department is outdated.
All you need is a smart platform like ComplyJet to help you automate your ISO 27001 for startups. So you can focus on the growth engine.
When ISO 27001 Might Be Overkill
While ISO 27001 is a powerful growth enabler, it’s not mandatory for every startup at every stage. There are cases where it might be unnecessary or too heavy:
- You don’t store or process customer data: A product still in prototype or internal-only usage doesn’t need certification.
- Your customers are small businesses with simple requirements: SMBs usually rely on basic security hygiene, not formal audits.
- You don’t integrate with enterprise systems: If your product never touches sensitive data or third-party systems, ISO may not deliver an immediate ROI.
- You’re still validating product-market fit: If the product is changing every week, setting up a full ISMS can slow you down.
- You have no enterprise pipeline for the next 12–18 months: If you won’t face security questionnaires or vendor assessments soon, starting with lightweight policies is enough.
However, once you begin targeting mid-market or enterprise customers, ISO 27001 shifts from a ‘nice-to-have’ to a deal accelerator.
How to Get ISO 27001 Certification
Getting ISO 27001 certified isn't as complex as it sounds. Most startups assume it requires months of bureaucracy and enterprise-level processes. It doesn't.
You need structure, not heavy processes. Here's how to do it without diverting your product roadmap.
Step-by-Step Process for Startups

- Define your scope
- Perform a lightweight risk assessment
- Draft essential policies
- Control mapping & implementation
- Collect evidence continuously
- Conduct an internal audit
- Conduct audit certification process
- Continuously monitor
These steps are categorised into stages for easier implementation.
Stages of Implementation (Mapped for Startups)

Stage 1: Readiness (1-2 weeks)
This is where you get everyone aligned before you start building anything.
Hold a kick-off meeting with stakeholders like the CEO, CTO, engineering lead, and answer the most important questions, like defining the scope and risk assessment.
Smaller teams mean fewer approvals. You're not waiting on legal, compliance, and security committees. Your CEO can approve the policy on a simple Slack thread.
Step A: Define Your Scope
Start small. Don't try to certify your entire company on day one.
Your initial scope should cover:
- The product customers pay for
- Backend systems that store the customers’ data
- Key teams that touch the customer data often
Everything else? You can skip (like internal tools, HR systems, or non-customer-facing operations) for now.
This isn’t hiding anything. Auditors understand phased approaches. A startup with 20 employees doesn’t need the same scope as a 1000-person company.
A narrow scope →fewer controls→ faster certification. You can expand the scope later when you scale.
Step B: Perform a Lightweight Risk Assessment
Identify security risks that could compromise customer data or operations.
You don't need enterprise risk management software. Open a spreadsheet and list out all the things that could be realistic threats:
- Someone has unauthorised access to customer data
- A vendor you integrated with breached data
- Employee laptops are getting stolen or compromised
- A code vulnerability in production
- Accidentally deleting data during migration
For each risk, document:
- What could go wrong if it happens
- How likely is it
- What control prevents it
- Who’s responsible
Auditors want proof you've thought through your risks. A simple, honest assessment beats a 50-page document nobody in your team reads.
Step C: Draft Essential Policies Your Team Actually Uses
Here's the truth about security policies: if your team doesn't follow them, they're useless. And if they're written in legal language, nobody's following them.
Required policies include:
- Access control: Who gets access to the systems, and how they request it
- Incident response: What happens when something could go wrong
- Encryption: How you encrypt data and mention the standards your team follows
- Vendor management: How you evaluate third-party tools before signing contracts
- Data retention: How long you store customer data
Stage 2: Implementation (3-6 weeks)
This is exactly where you actually secure systems. Roll out controls, configure tools, document processes, and vet vendors.
You're already using modern cloud tools. You don't need to retrofit legacy systems or negotiate with on-prem IT.
Step D: Controls Mapping & Implementation
Most founders think ISO 27001 for startups means rebuilding their entire security program.
Not really.
You are probably doing 60-70% of what is required already. You haven’t just documented it.
ISO 27001 includes Annex A, a list of 93 controls categorised into 4 types. This list sounds like a lot. But here’s what nobody tells you: you don’t need to implement all 93 controls. You simply implement the controls that address your specific risks.
Here's how Annex A breaks down:
Organizational controls (37 controls): Policies, roles, and procedures. Things like who approves vendor contracts, how you handle security incidents, and who's responsible for what.
Key Organizational Controls Every Startup Needs:
- A.5.1- Policies for information security
- A.5.19 - Information security in supplier relationships
- A.5.23 - Use of cloud services
- A.5.24 - Information security incident management
- A.5.30 - ICT readiness for business continuity
People controls (8 controls): Hiring, training, and offboarding. Background checks, security awareness training, and what happens when someone leaves.
Key People Controls for Startup:
- A.6.1 - Screening
- A.6.2- Terms and conditions of employment
- A.6.3 - Security awareness
- A.6.4 - Disciplinary Process
- A.6.5 - Responsibilities after termination

Physical controls (14 controls): Physical security, like office access, equipment protection, and secure disposal of hardware. If you're fully remote, half of these won't apply to you.
Key Physical Controls for Startup (If On-Site):
- A.7.2 - Physical entry
- A.7.4 - Physical security monitoring
- A.7.7 - Clear desk and clear screen
- A.7.10 - Storage media
- A.7.14 - Secure disposal
Technological controls (34 controls): The technical stuff, like access management, encryption, backups, and monitoring.
Key Technological Controls for Every Startup:
- A.8.5 - Secure authentication
- A.8.10 - Information deletion
- A.8.13 - Information backup
- A.8.24 - Cryptography use
- A.8.25 - Secure development life cycle
These controls are only a few of the common ones for startups. There are more controls you might need to implement to achieve ISO 27001 certification.
You have to document which controls you’re implementing, and why you’re excluding the others. That is called a Statement of Applicability.
Now here’s the interesting part: you might already be implementing most of the controls.
Technical controls you likely have:
- Single sign-on (SSO) with MFA
- Automated backups with tested recovery
- Logging and monitoring (who did what, when)
- Secure development lifecycle (code reviews, branch protection)
- Encryption at rest and in transit
- Vulnerability scanning
Organisational controls you might already be doing:
- Onboarding checklist (laptop setup, access provisioning)
- Offboarding checklist (revoke all access within 24 hours)
- Quarterly access reviews
- Vendor security assessments
People control your handling:
- Background checks during hiring
- NDA Confidentiality
- Security awareness training
ISO 27001 isn't about perfect security. It's about to prove you have consistent, documented controls.
Step E: Gather Evidence Continuously
Auditors need proof that your controls actually work. Evidence includes:
- Access logs showing MFA is enforced
- Screenshots of backup configurations
- Approval emails for vendor onboarding
- Incident response tickets with timestamps
- Training completion records
- Quarterly access review spreadsheets
Set up folders organized by control area. Drop evidence in as you go, not two days before the audit.
Pro tip: Use shared drives or compliance tools that automatically capture evidence. Manual collection eats up weeks.
Stage 3: Internal Audit (1 week)
Internal audit is like cheap insurance. You’re finding the gaps when they’re easy to fix. An independent reviewer (consultant or compliance tool) tests your ISMS readiness.
Step F: Conduct an Internal Audit
Before the real audit, run an internal review. Most startups hire a consultant or use a compliance platform for this.
The internal auditor will:
- Review your policies and procedures
- Check if controls are actually implemented
- Test evidence completeness
- Identify gaps before the real audit
Budget 3-5 days for this. You'll find gaps. Fix them before an external auditor shows up.
Stage 4: External Audit (2-4 weeks)
The certification body conducts Stage 1 and Stage 2 audits.
Key activities:
- Stage 1: Submit documentation for review
- Fix any documentation gaps
- Stage 2: Auditor interviews and control testing
- Fix minor non-conformities if needed
Fewer employees mean fewer interviews. Fewer systems mean faster control testing.
Step G: Actual Certification Process
This is the official audit performed by an accredited certification body (like A-LIGN)
Stage 1 audit (Documentation Review): The auditor reviews your ISMS documentation. They check if your policies, risk assessment, and scope are complete. No surprise failures here if you did Step 6 properly.
Stage 2 audit (Evidence Verification): The auditor interviews your team, tests controls, and verifies evidence. They want to see:
- Does MFA actually work when they try logging in?
- Are backups tested?
- Do employees follow the incident response plan?
- Is access actually reviewed quarterly?
If you pass, you get certified. If there are minor issues (non-conformities), you fix them and resubmit evidence.
Auditors aren't trying to fail you. They want to certify you. Be honest, show your work, and don't try to fake evidence.
Stage 5: Certification (immediate) & Continuous Monitoring (ongoing)
You receive your ISO 27001 certificate, valid for three years.
This certification is proof that you have a system that works consistently, not that you have perfect security.
But here’s what founders forget: certification isn’t the end. Annual surveillance audits ensure you maintain compliance.
ISO 27001 isn't a one-time project. You need to:
- Maintain evidence collection
- Update risk assessments when systems change
- Conduct quarterly access reviews
- Run security training annually
- Prepare for surveillance audits
You can maintain ISO 27001 in a few hours per month if you build it into your normal operations.
The companies that struggle are the ones that treat it as a separate compliance project. The companies that succeed treat it as documentation of how they already work.
Realistic Timelines (Startup Edition)
Without guidance, ISO 27001 takes 6-12 months. With the right approach, startups move much faster.
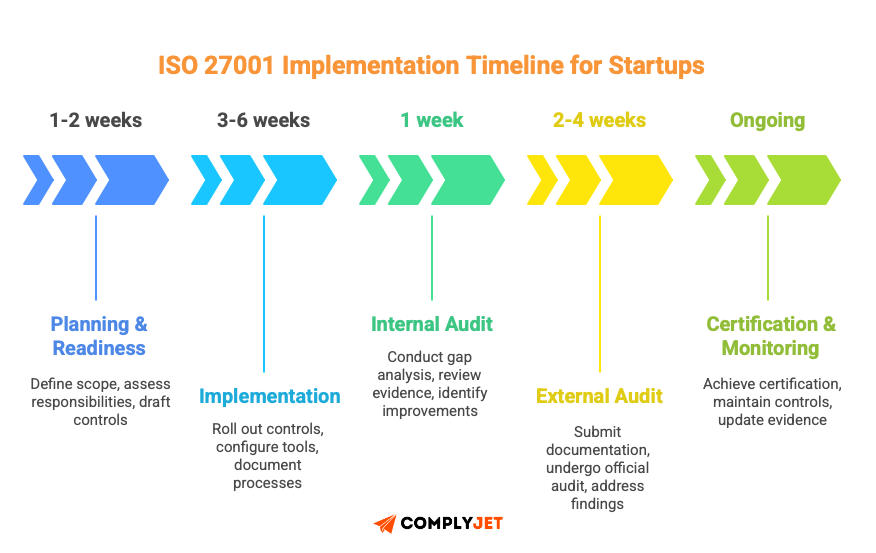
Timeline scenarios for different situations:
Fast-moving startup with established engineering practices: 6-10 weeks
- You have already implemented MFA, GitHub correctly, and have documented processes in place.
- Formalize everything and gather evidence.
Lean team using compliance automation: 4-8 weeks
- By automating evidence collection, policy templates, and audit coordination you can simplify the process.
- This enables you to concentrate on product development without distraction.
Building everything from start with manual processes: 10-14 weeks
- During this time, you're simultaneously building security controls and documentation.
- This demands the founders attention more.
Time-sensitive enterprise deals: 4-6 weeks
- Stressful but possible with external help.
- Expect late nights and weekends.
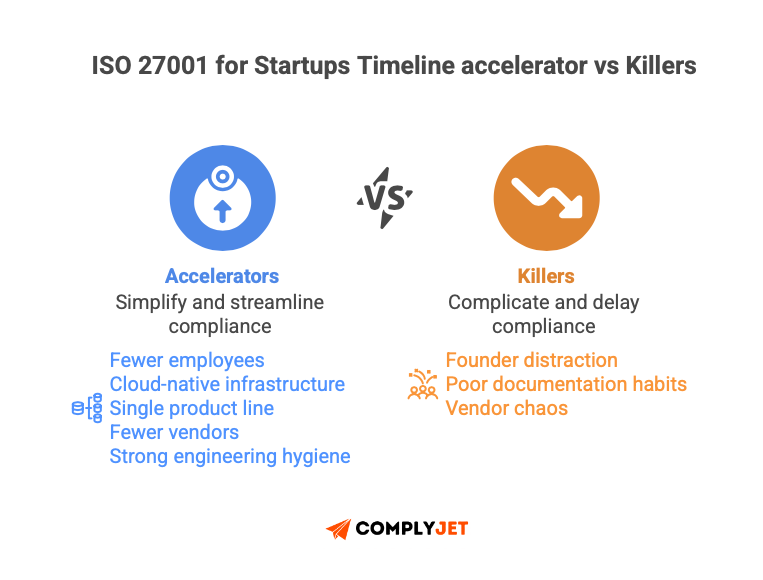
Timeline accelerators:
- Fewer employees means easier coordination
- Cloud-native infrastructure → no legacy systems
- Single product line →narrow scope
- Fewer vendors → less due diligence
- Strong engineering hygiene →controls already exist
Timeline killers:
- Founder distraction→ compliance stalls when nobody owns it.
- Poor documentation habits →scrambling for evidence later
- Vendor chaos →using 50 SaaS tools without contracts
Common Challenges for Startups
- Founders Juggling Compliance with Product Roadmap: Compliance competes with shipping features. Engineers resent "security paperwork."
How to handle it: Assign an owner (usually CTO or security-minded engineer). Block 5-10 hours per week for compliance work. Don't try to squeeze it into spare moments.
- Lack of Documentation: Startups operate informally. ISO requires written policies, approval trails, and logs.
How to handle it: Start documenting as you go. Use templates. Don't overthink it. A 2-page policy beats no policy.
- Vendor Security: Early-stage teams use dozens of SaaS tools without security reviews.
How to handle it: Create a simple vendor assessment form. Ask for SOC 2 reports or security questionnaires. Document risk acceptance for low-risk tools (like Figma or Notion).
- Evidence Collection: Screenshots, logs, and approval emails are time-consuming when done manually.
How to handle it: Use compliance tools that auto-capture evidence. Set calendar reminders for quarterly reviews. Create shared folders with clear naming conventions.
- Cultural Adoption: Everyone must follow security practices consistently, not just engineering.
How to handle it: Run onboarding training. Make it clear why this matters (customer trust, enterprise deals). Celebrate good security behaviour.
- Audit Anxiety: First-time founders fear scrutiny. What if the auditor finds something terrible?
How to handle it: Auditors aren't looking to embarrass you. They want to certify you. Be honest about gaps. Show you're fixing them. That's enough.
Most of these challenges disappear with early preparation and the right tools. Startups that treat ISO 27001 as a structured project finish faster and with less stress than those that treat it as bureaucratic busywork.
Certification Costs & ROI Analysis
ISO 27001 Certification cost is not cost-effective, but it is not as expensive as founders assume. Most certification costs depend on company size, scope, compliance platform, and consultants' charges.
Typical Certification Costs for Startups
Here we present the average numbers for the ISO 27001 certification cost for startups.
Cost Component
Typical Range
Compliance Software
$3,000 – $12,000/year
Consultant Fees (Optional)
$5,000 – $20,000
External Auditor Fees
$6,000 – $15,000
Internal Team Time
30–80 hours
Total Cost
$10,000 – $40,000
You can expect to carve out some budget for extra add-ons like pentest services, gap analysis, vulnerability assessment and more.
Is It Worth It? (ROI for Startups)
ISO 27001 isn't just a compliance cost. For most startups, it's a revenue accelerator that pays for itself within months. Below are the benefits of ISO 27001 certification:
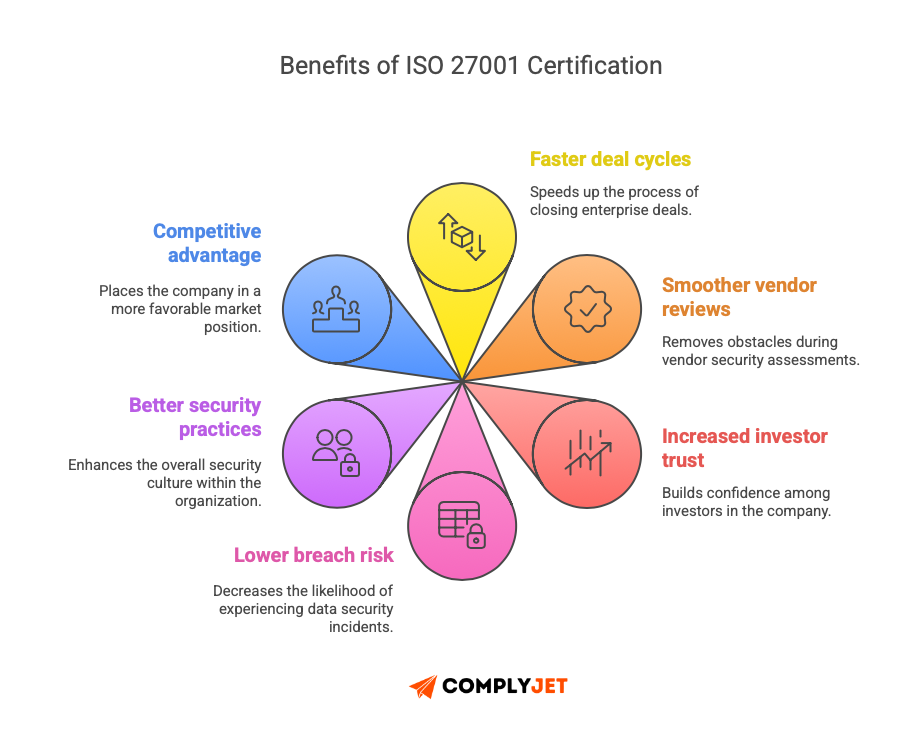
For growing SaaS companies like yours, a single closed deal can easily cover the entire certification cost. For mid-market startups, it often pays back 10x–30x within the first year.
ISO 27001 with ComplyJet: A Mere Compliance Badge or a Strategic Advantage?
For startups, ISO 27001 is much more than a badge. It's a signal of maturity where the founder stops operating as an entrepreneur and begins to emerge as an industry leader.
It is a point where the change happens in how customers, investors, and partners see you.
A founder can either say,
‘Trust us, we take security seriously,’ or prove it with a globally recognized certification.
Traditional ISO 27001 implementations take 6-12 months with consultants who bill by the hour and manually build everything from scratch. Founders drown in documentation while product roadmaps stall.
ComplyJet compresses this to 2-4 weeks by treating compliance as a product problem.
Pre-built policy templates, automated evidence collection, and integrations with tools you already use (AWS, GitHub, Slack) eliminate manual work. Evidence is captured continuously, not two days before audits.
The real difference: traditional approaches make compliance feel like overhead. ComplyJet turns it into infrastructure that runs in the background. You stay audit-ready year-round without constant founder involvement.
When enterprise customers send security questionnaires, you respond in hours, not weeks. This speed advantage matters during competitive deals, especially for startups.
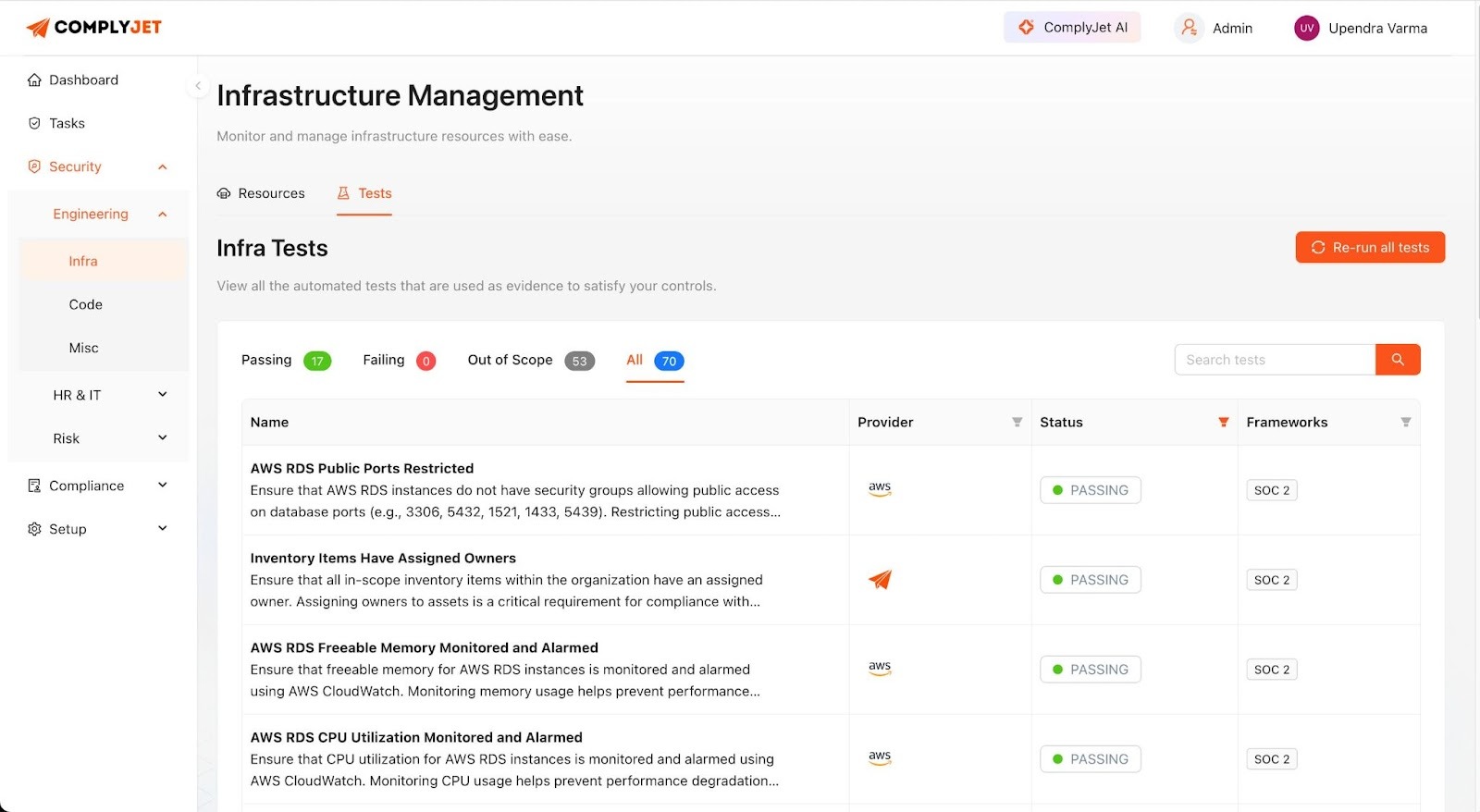
While non-compliant competitors scramble to answer security questions, you're already moving to contract negotiation. ISO 27001 stops being a checkbox and becomes your unfair advantage.
FAQ
1. How long does ISO 27001 take for a startup?
Most startups complete it within 6–12 weeks if they follow a lean approach.
2. IS ISO 27001 legally mandatory?
No, ISO 27001 is not legally mandatory, but it is a standard trust pillar for enterprises to sign contracts and close deals.
3. Do we need a dedicated security team?
No. Many startups get certified with just a founder + product manager + engineering lead. All you need is a compliance platform that will be an extension of your team. Uplifting manual workload, automating evidence collection, and updating.
4. Can we start with SOC 2 instead?
SOC 2 is US-focused. ISO 27001 is global. For international customers, ISO gives stronger coverage. You can learn more about ISO 27001 vs SOC 2 here.
5. Do we need expensive consultants?
Optional. Modern compliance tools automate 60–70% of the process.
6. What happens after certification?
You undergo annual surveillance audits and maintain controls and evidence.
7. What’s the biggest mistake startups make?
Waiting until an Enterprise deal walks in with a 6-figure ARR and asks for compliance documentation to sign the contract. Eventually forcing a rushed, painful sprint for compliance certification.
8. Does ISO 27001 cover cloud security?
Yes. The 2022 update includes modern cloud, DevOps, and SaaS-focused controls.
Summary:
ISO 27001 for startups isn’t just a regulatory checkbox; it’s a growth strategy. Whether you’re a 5-person SaaS team or an emerging mid-market startup, ISO 27001 helps you build predictable, secure operations that scale smoothly.
Early-stage companies that invest in structured security win trust faster, close enterprise deals sooner, and avoid last-minute compliance chaos that slows momentum.
The key is to start lean, prepare early, and treat security as a business enabler, not a burden.
It is a simple yet important fact: ‘reactive compliance costs more than proactive compliance.’
Start your free trial for ISO 27001 for startups today!
.png)


