You just got the Slack notification every B2B founder dreams of: "Enterprise Contract Signed." The virtual champagne pops, and for a moment, the stress of the last six months vanishes. Then, the follow-up email arrives from the buyer's procurement team. Attached are a 250-question security questionnaire, a request for a SOC 2 Type II report, a HIPAA BAA, and proof of PCI compliance.
They see you process credit cards, so they demand PCI DSS. They know you serve healthcare clients, so they require HIPAA. And because you handle user data, they want to see your PHI vs PCI vs PII compliance roadmap. In an instant, your product roadmap for the next two quarters is effectively dead.
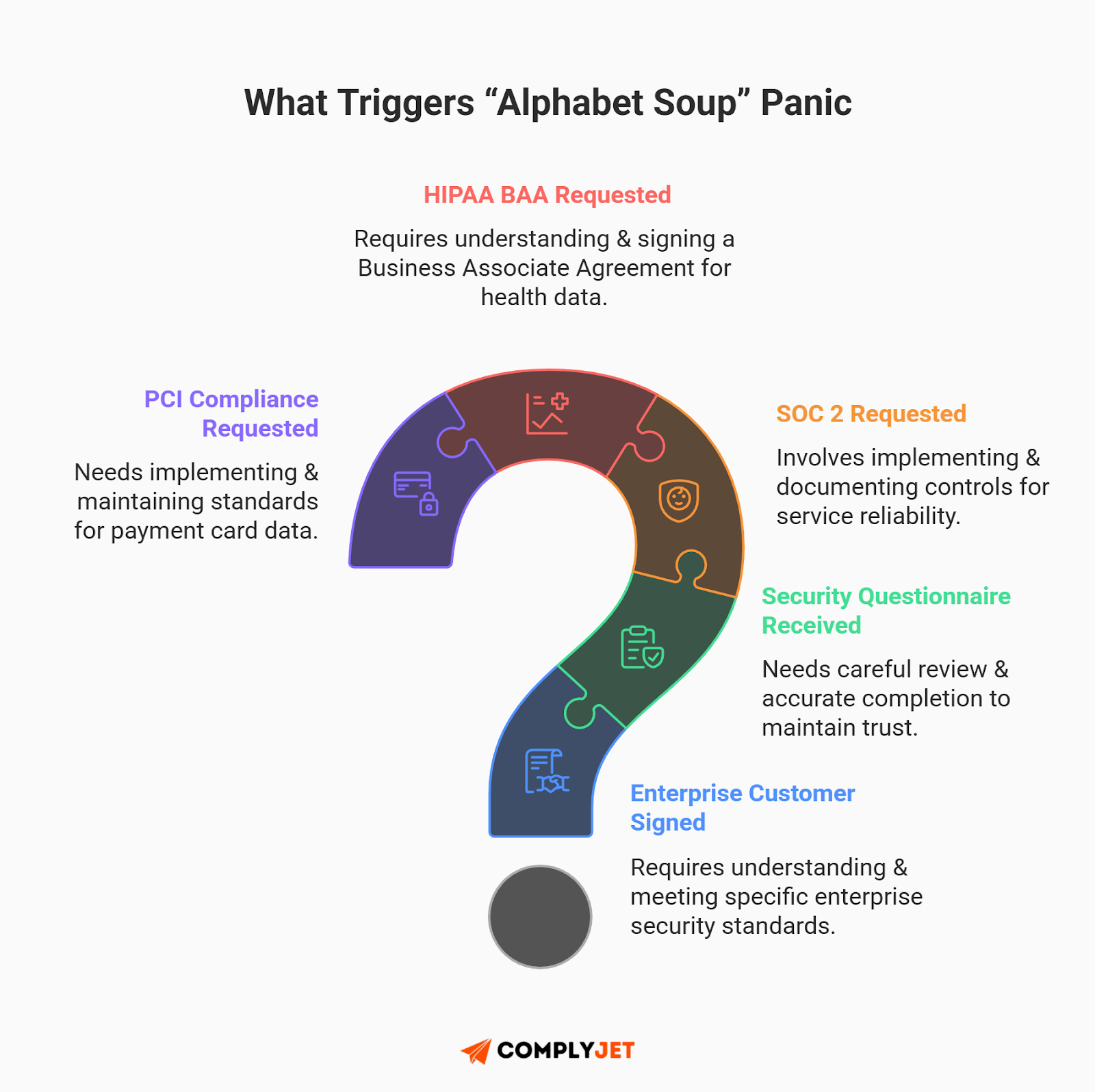
This is what we call the "Alphabet Soup" panic. Most founders look at these requirements and see three separate, insurmountable mountains to climb. They think they need three different consultants, three separate budgets, and three redundant sets of security tools. This is a costly mistake that kills engineering velocity.
The truth is, mastering PHI vs PCI vs PII compliance isn't about satisfying three different regulators. It is about solving one singular problem: SaaS data classification. Whether it's a patient's diagnosis, a credit card number, or a user's home address, the mechanics of securing that data are nearly identical. If you treat them as silos, you will drown in overhead. If you treat them as flavors of the same asset, you can build a system that satisfies everyone.
This guide moves past the dictionary definitions to focus on the operational reality of building a B2B compliance strategy that allows you to build once and comply everywhere.
What is PHI vs PCI vs PII?
Before we can discuss how to optimize your scope, we need to establish a shared vocabulary. While these terms are often thrown around interchangeably in sales calls, they represent very different legal and technical obligations. To build a resilient PHI vs PCI vs PII compliance strategy, you must first understand the unique DNA of the data you are handling.
Automated compliance can help, without burning a hole through your wallet. ComplyJet is built specifically for lean teams who need enterprise-grade compliance without the enterprise-grade price tag. Check out our transparent pricing structures.
PII (Personally Identifiable Information)
PII is the broadest category. According to the National Institute of Standards and Technology (NIST), PII is any information about an individual maintained by an agency, including any information that can be used to distinguish or trace an individual‘s identity.
- Examples: Full name, SSN, passport number, email address, or even an IP address in certain contexts.
- The Regulator: In the US, there isn't one single "PII law," but rather a patchwork including the CCPA (California) and various state breach notification laws. Internationally, the GDPR is the gold standard.
PHI (Protected Health Information)
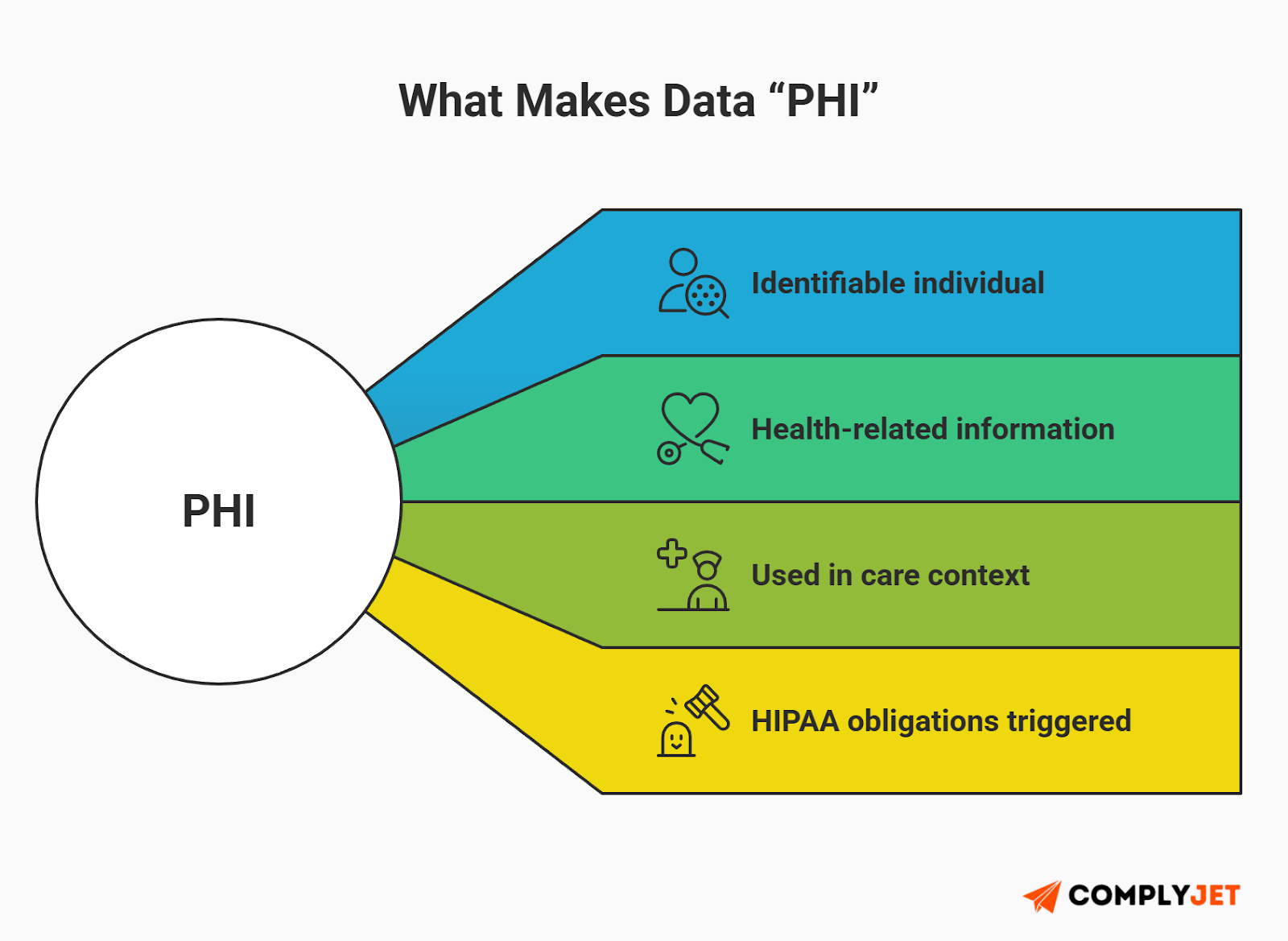
PHI is PII that is specifically linked to health records or healthcare provision. Under the Health Insurance Portability and Accountability Act (HIPAA), PHI is any information in a medical record that can be used to identify an individual and that was created, used, or disclosed in the course of providing a health care service.
- Examples: Medical history, test results, health insurance details, and even appointment dates when linked to a name.
- The Regulator: The Department of Health and Human Services (HHS) and the Office for Civil Rights (OCR).
PCI (Payment Card Industry Data)
Unlike the others, PCI isn't a federal law; it's a private industry standard. The PCI Data Security Standard (PCI DSS) was created by the major card brands (Visa, Mastercard, etc.) to reduce credit card fraud. Failing to distinguish this from legal mandates is a primary reason why PHI vs PCI vs PII compliance efforts become so bloated.
- Examples: Primary Account Number (PAN), CVV, expiration date, and track data.
- The Regulator: The PCI Security Standards Council (PCI SSC). While not "the law," failing to comply can lead to your merchant account being revoked - meaning you can no longer accept payments.
Understanding these foundational differences is the first step toward a successful PHI vs PCI vs PII compliance posture.
The Context Trap
The biggest mistake founders make when approaching SaaS data classification is treating it as a static exercise. They flag fields like "Name" or "Email" in their database and assume they have mapped their risk.
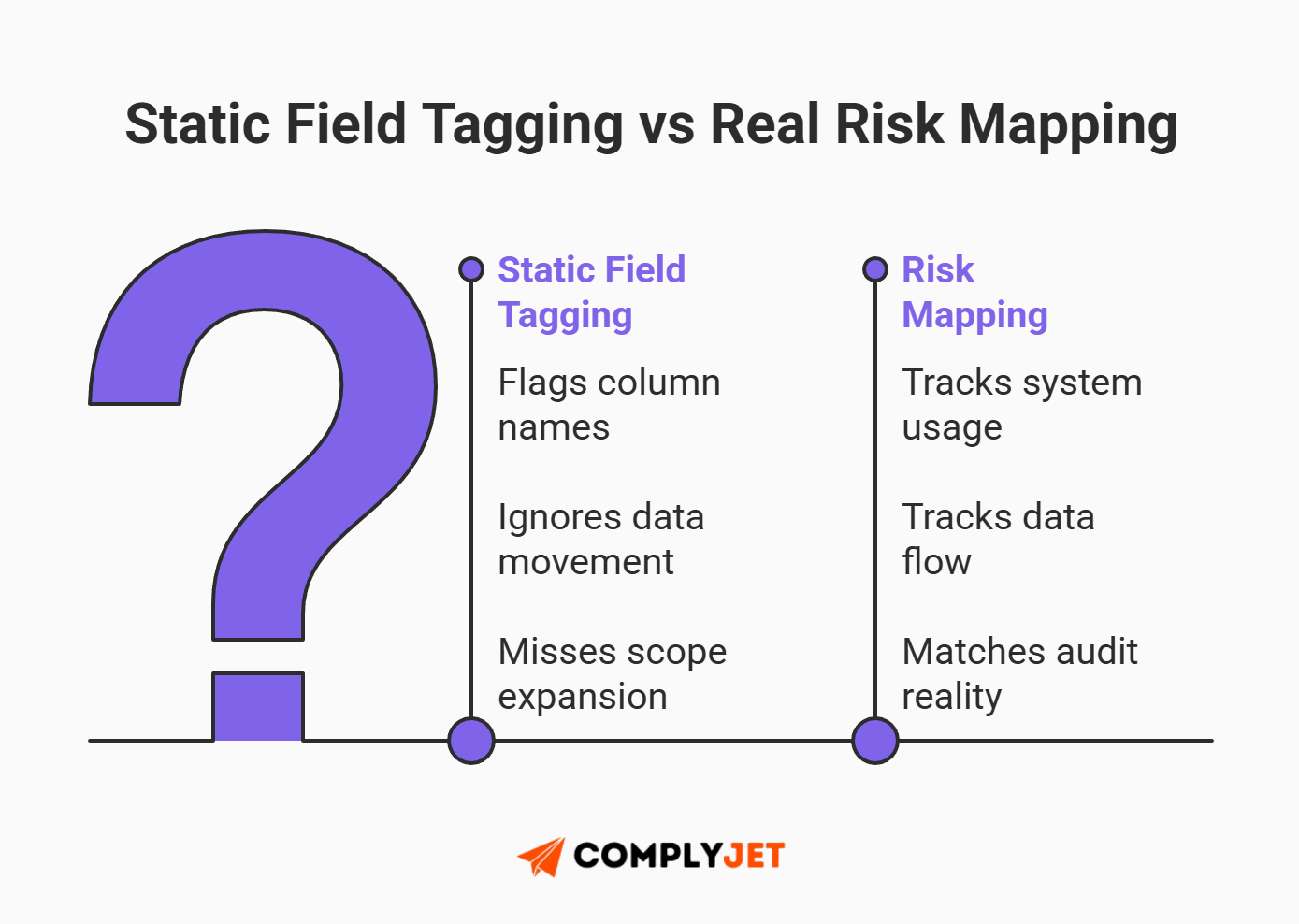
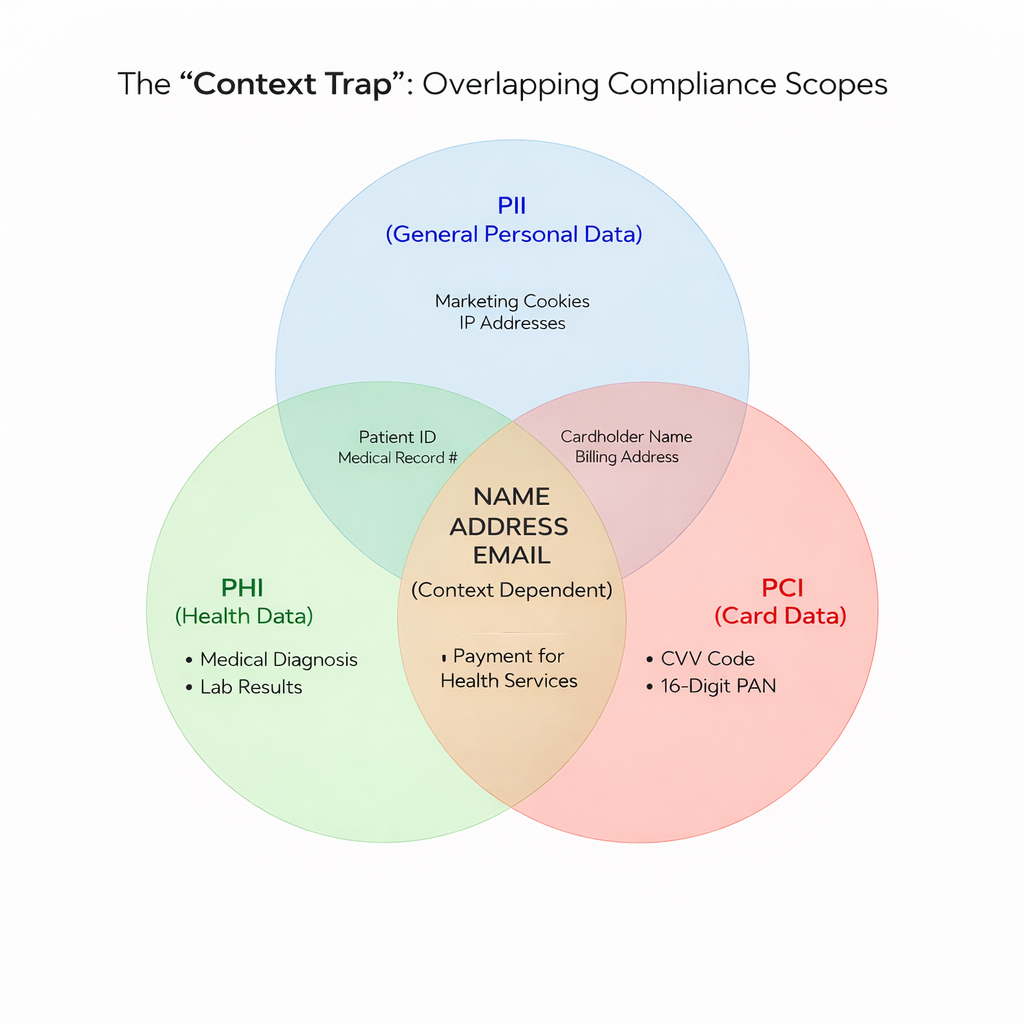
In reality, data is not static; its risk level depends entirely on context. This is where most teams get their scope wrong. To understand effective compliance, you must stop looking at the content and start looking at the flow. Let's look at the "Name Game" using a hypothetical user, "Jane Doe":
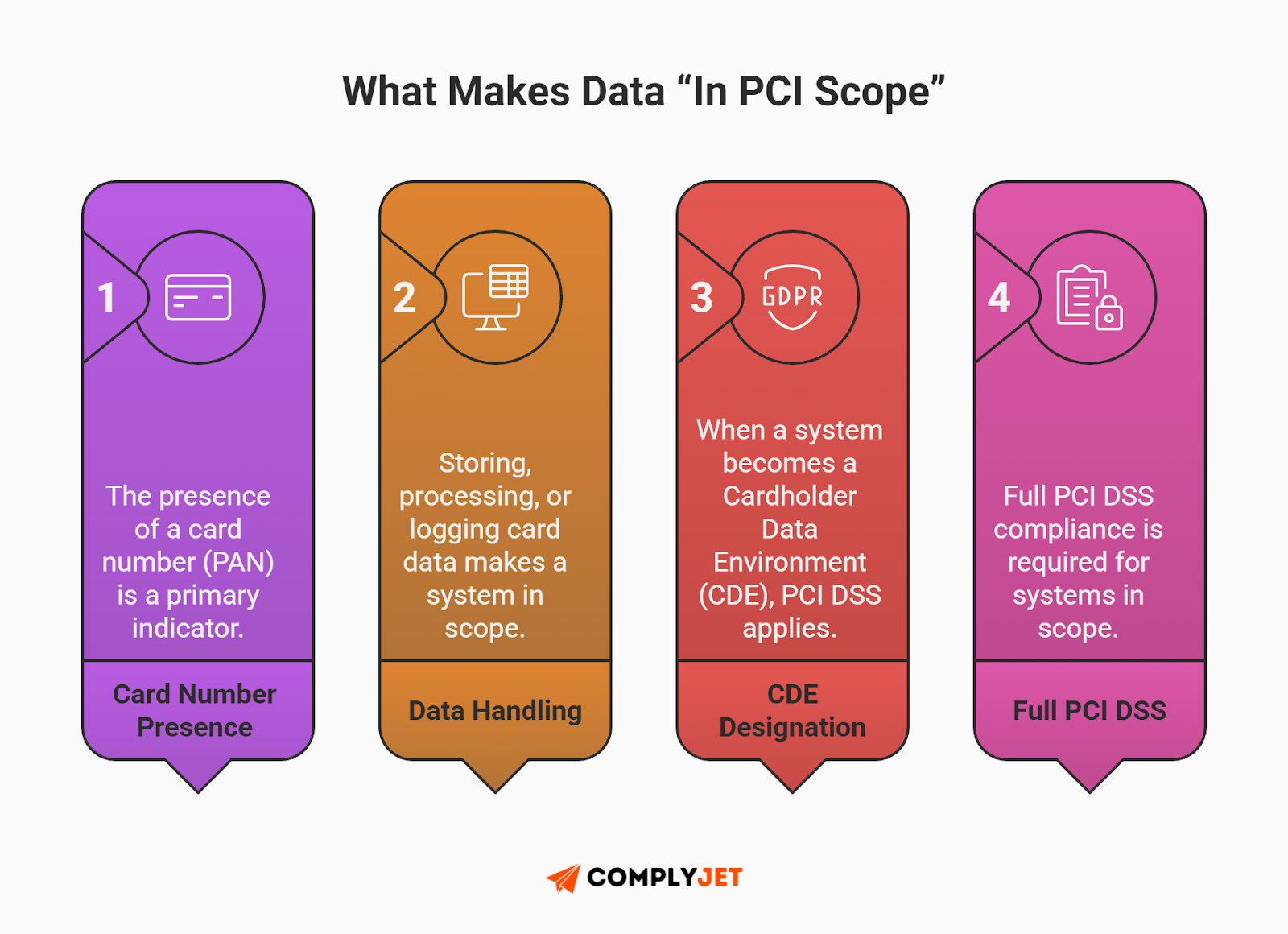
- Scenario A (Standard PII): Jane Doe is on a Mailchimp marketing list for your SaaS newsletter. This is standard PII. It requires protection, but a leak is rarely a "company-ending" event.
- Scenario B (PCI Scope): Jane Doe appears in a transaction log next to a 16-digit card number. Suddenly, her name is part of the Cardholder Data Environment (CDE). Under PHI vs PCI vs PII compliance rules, that log file is now subject to the full weight of PCI DSS audit requirements.
- Scenario C (PHI Scope): Jane Doe appears on an intake form describing a peanut allergy. Now, that same text string is PHI. A leak doesn't just mean a fine; it triggers federal HIPAA notification requirements.
The Founder's Takeaway: If you treat "Jane Doe" the same way across all three scenarios, you are failing. You are likely either over-spending on security for your marketing list or dangerously under-protecting your health records.
Processor vs. Controller: Determining Your Legal Role
This context shift is often the most confusing part of navigating PHI vs PCI vs PII compliance. It gets even murkier when you consider your legal role. In the world of SaaS, you rarely own the data. You process it.
- Under GDPR: You are a Data Processor.
- Under HIPAA: You are a Business Associate.
- Under PCI: You are a Service Provider.
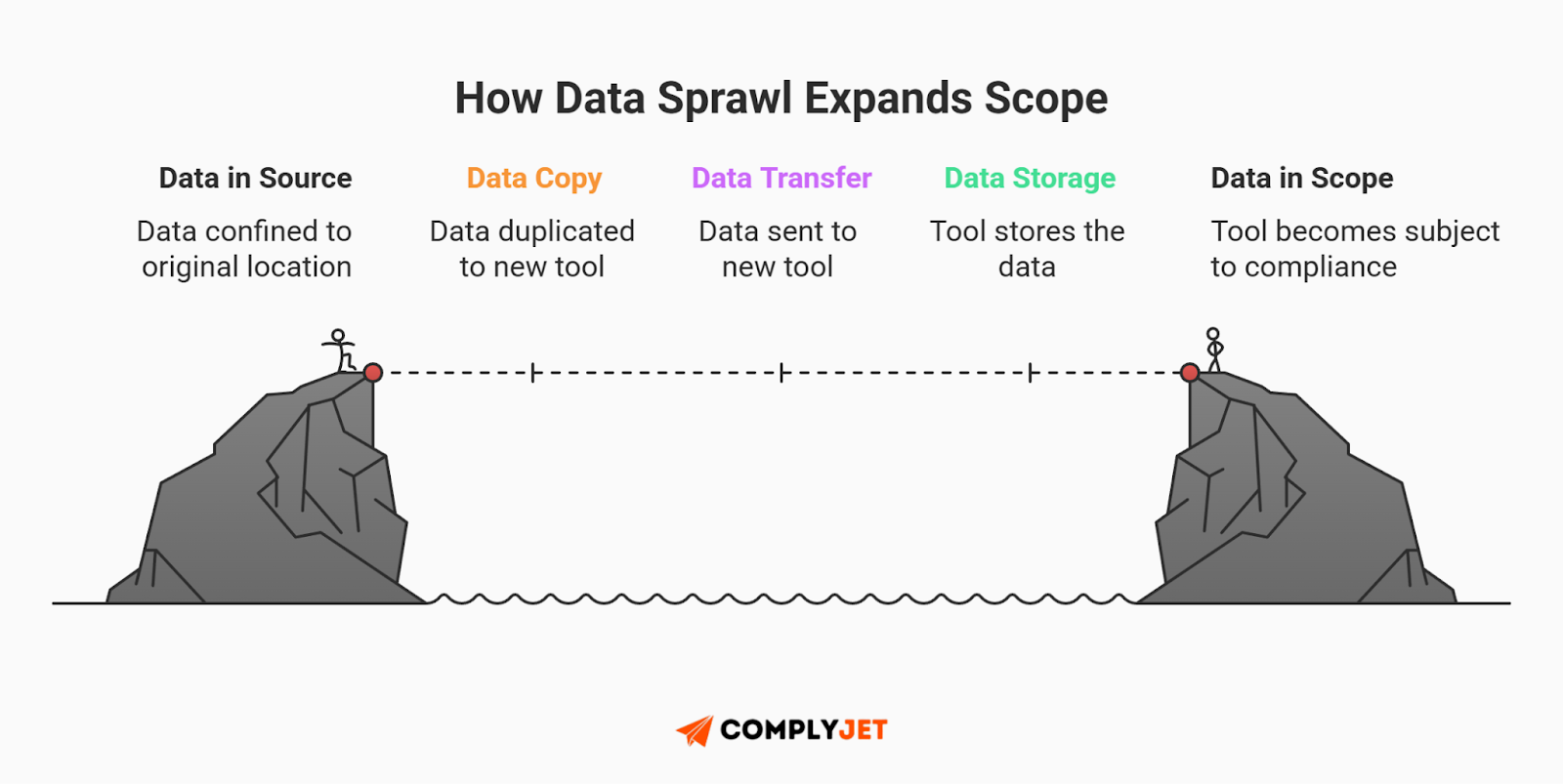
This distinction matters because data sprawl is the silent killer of startups. If your application pulls a name from a low-risk marketing database and pushes it into a high-risk analytics tool, you have inadvertently upgraded that data's classification. You are now legally responsible for the security of every environment that data touches.
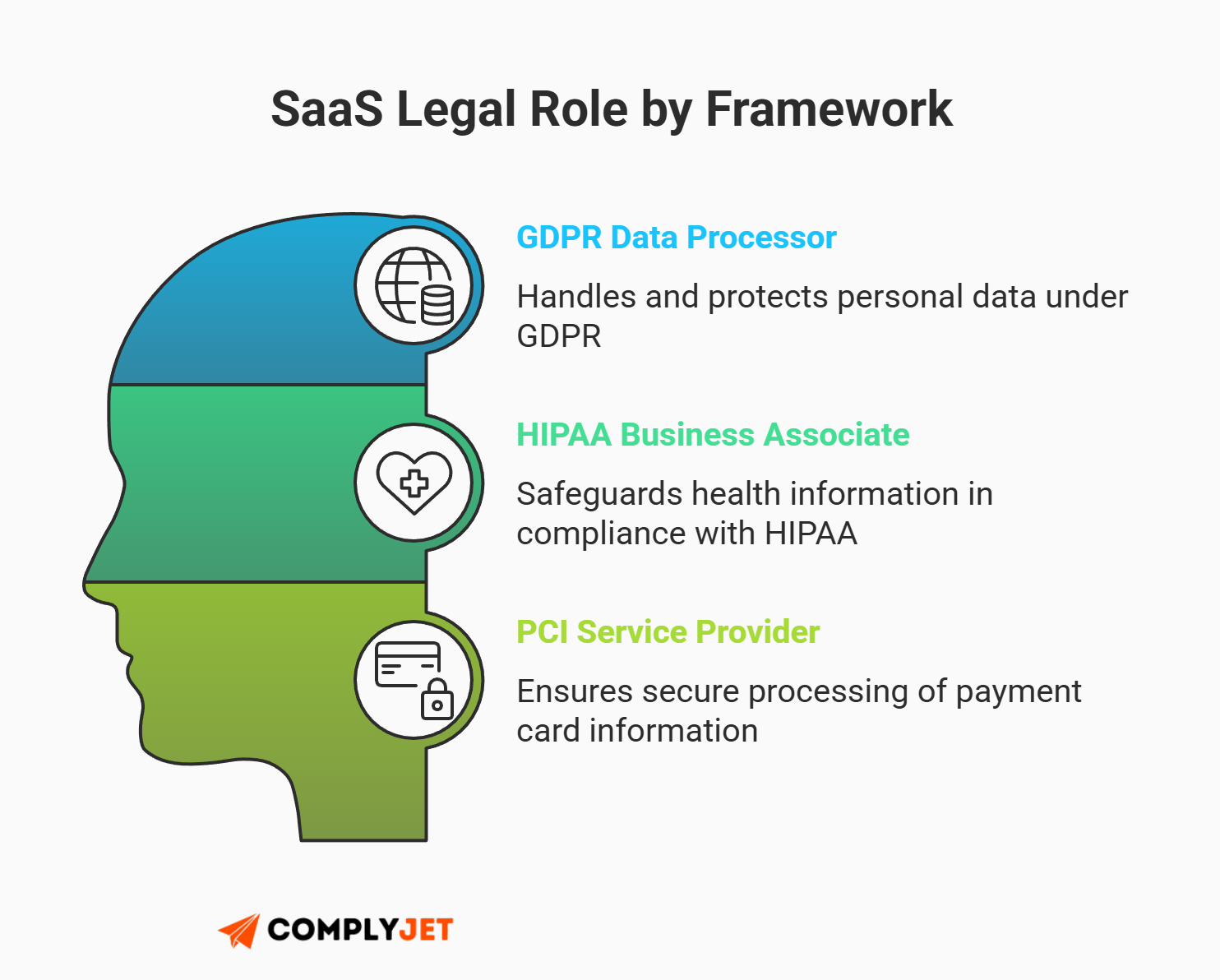
Effective PHI vs PCI vs PII compliance requires you to map not just where data is, but where it goes.
Strategic Descoping or “The Art of Not Touching Data”
The single most effective way to secure sensitive data is to never touch it. This is the core of PCI descoping and a primary pillar of maintaining PHI vs PCI vs PII compliance.
Many technical founders instinctively want to build everything themselves - custom payment forms, proprietary storage buckets, and unique encryption layers. From a compliance perspective, this is a fatal error. Every time sensitive data touches your infrastructure (your RAM, your logs, your database), your liability - and your audit cost - explodes. The smartest engineering strategy isn't about building stronger walls; it's about ensuring the data never enters your environment in the first place.
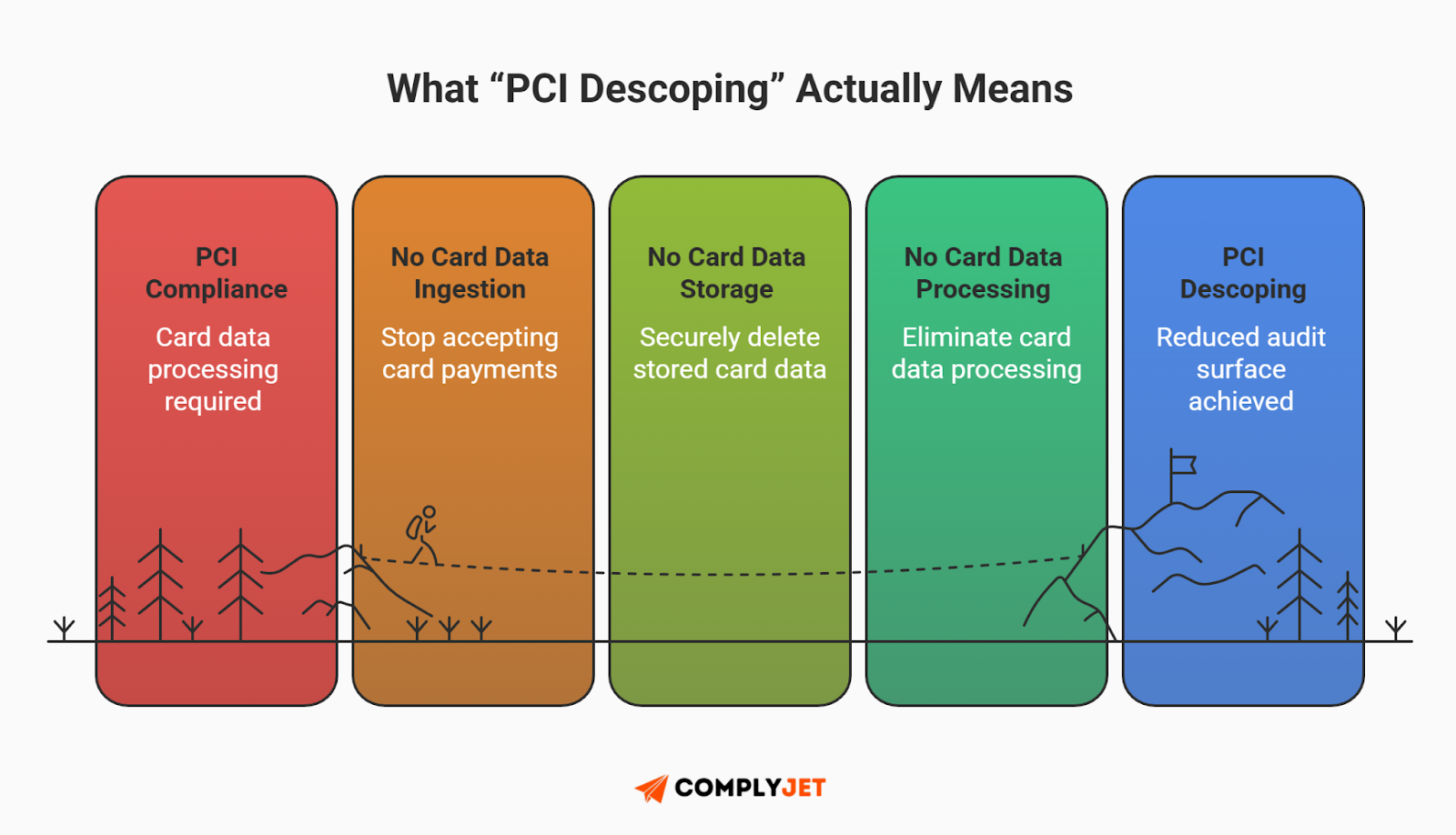
Tokenization vs. Encryption
There is a dangerous misconception in the world of PHI vs PCI vs PII compliance that encryption equals descoping. It doesn't.
Encryption protects the data from hackers; Tokenization protects you from auditors.
If you encrypt credit card numbers in your database, you are still holding the data and the keys. If a hacker compromises your server, they might get both. Your entire infrastructure remains "in scope" for an auditor. To achieve true PCI descoping, you must move to Tokenization.
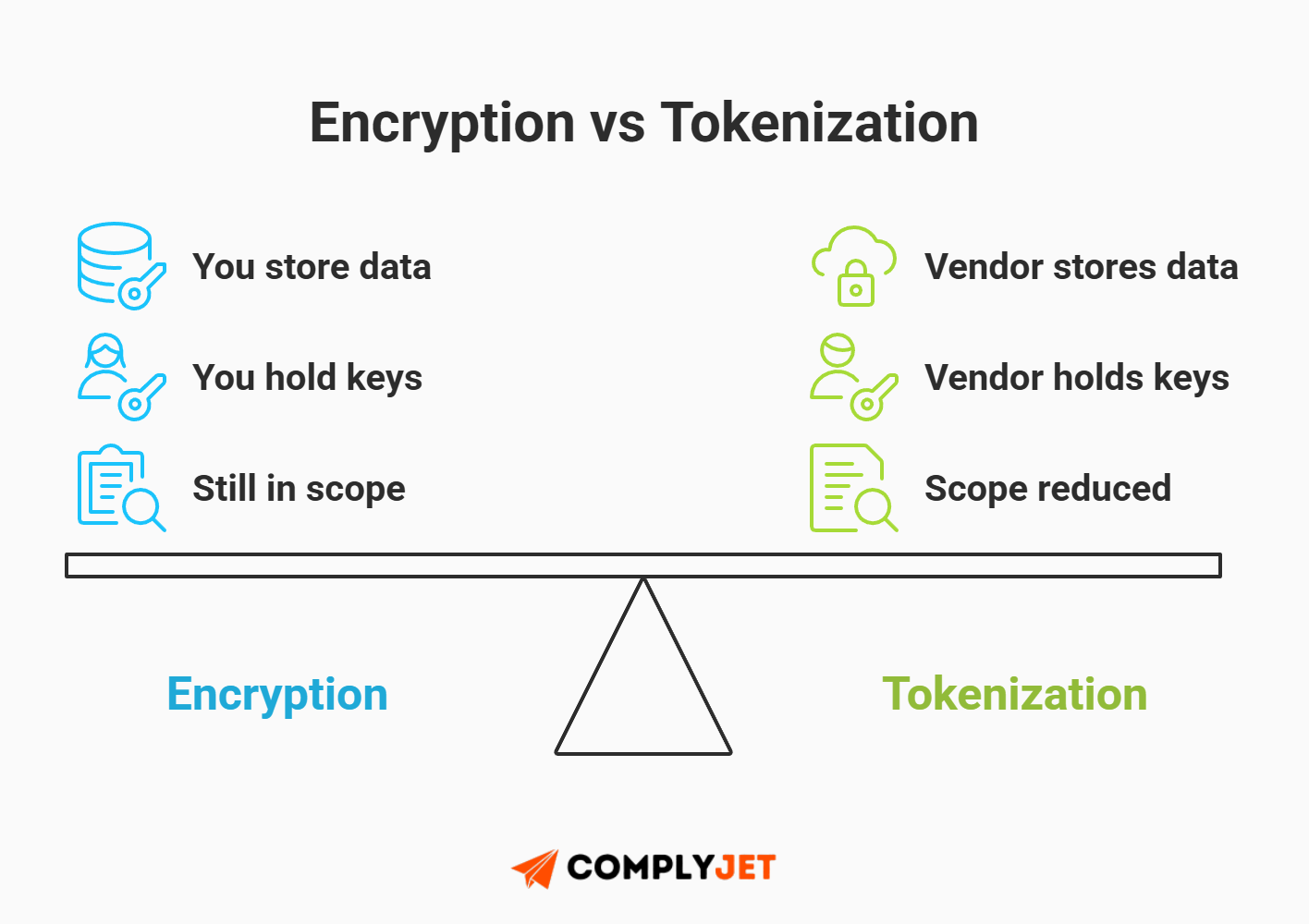
With tokenization, you exchange the sensitive data for a "token" (a random string of characters) that has no intrinsic value. The actual data is stored in a "Toxic Data Vault" managed by a third party.
The Founder's Takeaway: Do not build your own payments page. Use a hosted field (like Stripe Elements). If the raw Primary Account Number (PAN) never touches your server, you effectively bypass about 90% of the hardest audit requirements.
The "Toxic Data Vault" and Redaction Rules
You can apply this same logic beyond payments to significantly reduce the headache of PHI vs PCI vs PII compliance. By isolating high-risk data from your application logic, you essentially create a "clean room" for your engineering team to work in without fear of accidentally triggering a massive audit event.
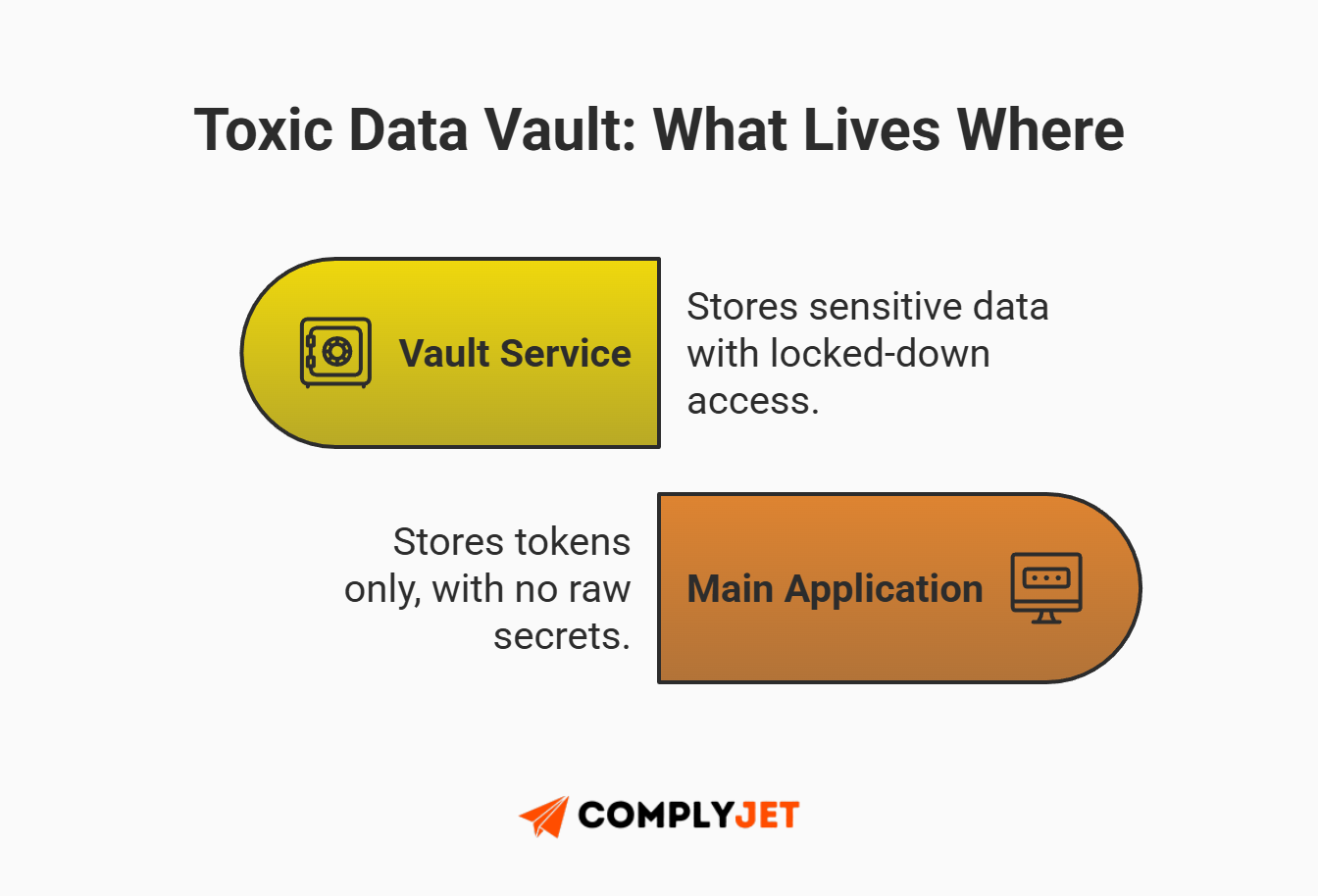
Instead of scattering sensitive fields across your main "Users" table, create a dedicated, isolated microservice whose only job is to store sensitive data. Your main application (the "monolith") only stores reference IDs. If your main app is compromised, the attacker only finds useless tokens.
This isolation is the architectural backbone of a modern B2B compliance strategy and simplifies the path to PHI vs PCI vs PII compliance.
The Redaction Rule for PHI
While tokenization handles storage, you must also control display. Does your support agent need to see a patient's full diagnosis to reset their password? No. Yet, many support dashboards query select and dump everything onto the screen.
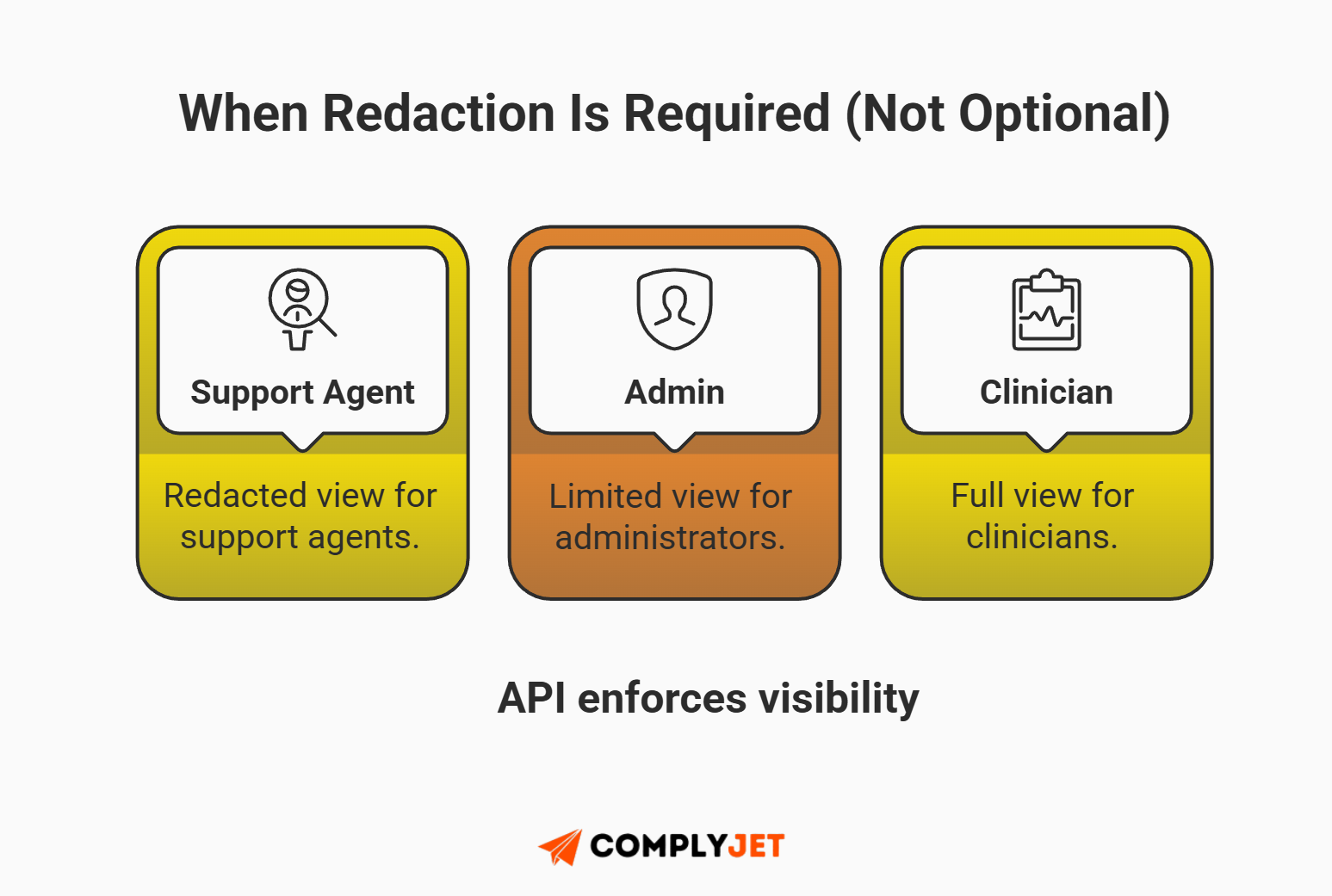
You must implement API-level redaction.
- If a support agent requests data, the diagnosis field returns *******.
- If a licensed doctor requests it, they see the record.
By redacting data at the transmission layer, you ensure that internal tools don't accidentally expand your PHI vs PCI vs PII compliance footprint into your Slack channels or support tickets. Achieving comprehensive PHI vs PCI vs PII compliance requires this level of visibility control to prevent "operational leakage."
Building a Unified Compliance Framework
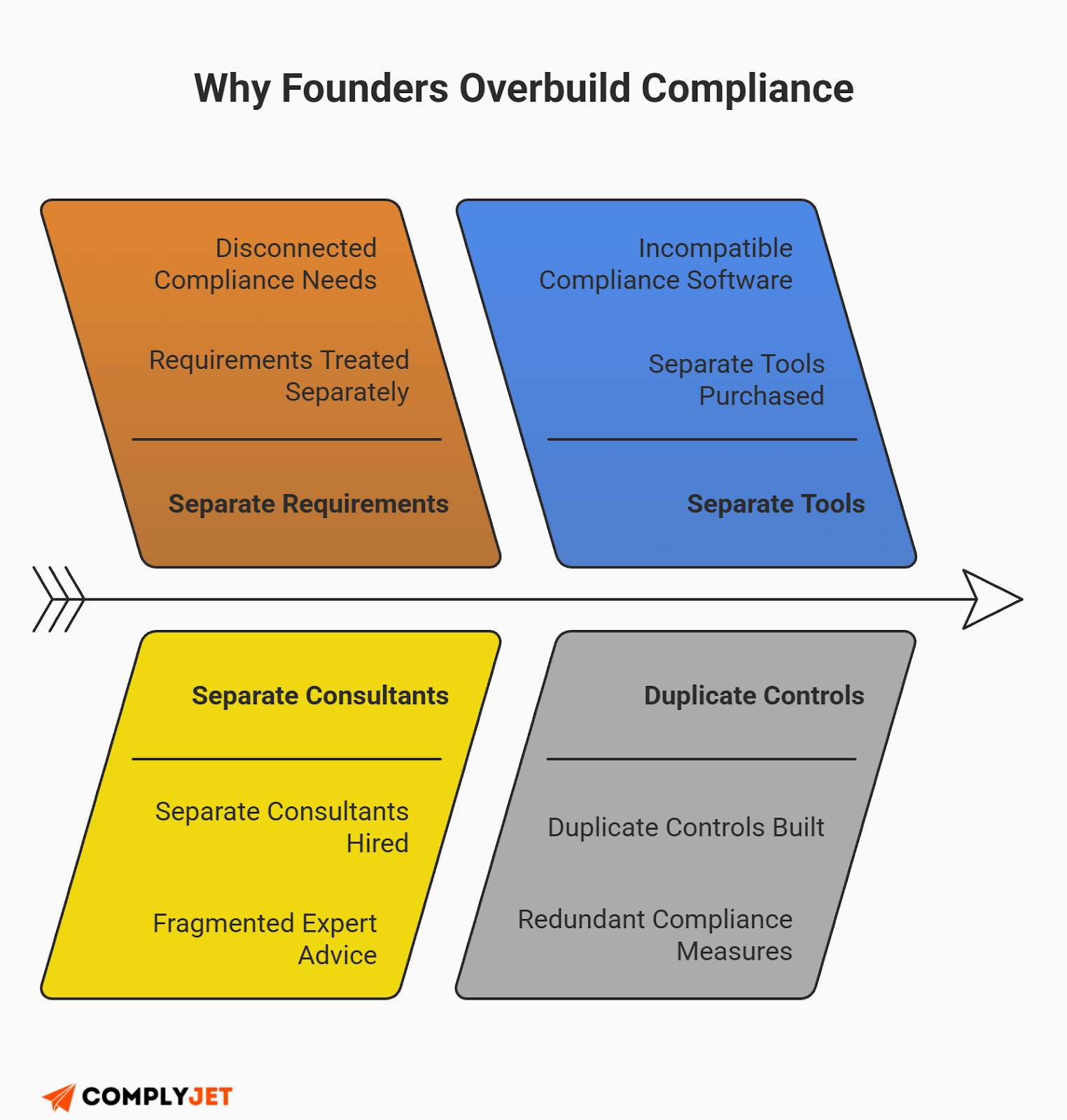
The biggest mistake founders make is treating compliance as a series of disconnected checklists. You hire a consultant for HIPAA, then another for SOC 2, and a third for PCI. This leads to "compliance debt" - a tangle of contradictory policies that makes managing PHI vs PCI vs PII compliance a nightmare.
The smarter path is to build a unified compliance framework. Instead of asking "What does HIPAA want?", ask "What does a secure SaaS architecture look like?" You will quickly realize the regulations are all asking for the same things.
The "70% Overlap" Rule
Whether you are protecting health records or credit cards, the foundational controls for PHI vs PCI vs PII compliance are nearly identical. There is an approximate 70% overlap in what auditors look for:
- Encryption: Everyone demands it. AES-256 encryption for data at rest and TLS 1.2+ for data in transit covers all bases simultaneously.
- Access Control: Every standard requires "least privilege." Implementing strict Role-Based Access Control (RBAC) satisfies HIPAA's "Minimum Necessary" rule and PCI's restrictions on cardholder data.
- Logging: Maintaining immutable audit logs is non-negotiable. You cannot prove you are secure if you aren't watching who accessed what and when.
By focusing on these three pillars, you build a unified compliance framework that serves as a solid foundation for any future audit, regardless of the acronym.
Confused by the mapping? We've got you. Most tools just give you a checklist and wish you luck. At ComplyJet, our team of experts walk you through the setup, ensuring you map your controls correctly the first time. We don't just sell software; we offer peace of mind. Book a meeting with our founder and learn what is the right move for your team.
The "Super-Standard" Approach
Once you acknowledge the overlap in PHI vs PCI vs PII compliance, how do you handle the differences?
Instead of maintaining different policies for different clients, identify the strictest requirement across all your frameworks - we call this the "Super-Standard" - and make that your company-wide default.
Take Penetration Testing as an example:
- HIPAA: Vague requirements regarding "technical evaluations."
- SOC 2: Expects regular testing but doesn't always mandate a specific cadence.
- PCI DSS: Mandates rigorous annual testing by a qualified professional.
In a unified compliance framework, you simply adopt the PCI standard. By performing a rigorous annual pen test, you automatically satisfy HIPAA and SOC 2. This reduces decision fatigue and ensures that compliance is a byproduct of good engineering, not a frantic box-checking exercise.
Modern Hazards: LLMs and Data Sprawl
In 2026, the fastest way to fail a PHI vs PCI vs PII compliance audit isn't a database leak - it's your engineering team pasting customer logs into an AI model for debugging.
If you send a "masked" error log to an LLM, but that log contains a patient ID or a credit card fragment, you have just transmitted regulated data to a third-party processor that may not be under a Business Associate Agreement (BAA) or PCI agreement.
The Founder's Takeaway: Treat your AI prompts as "Public Internet." If you wouldn't tweet the information, don't prompt it.
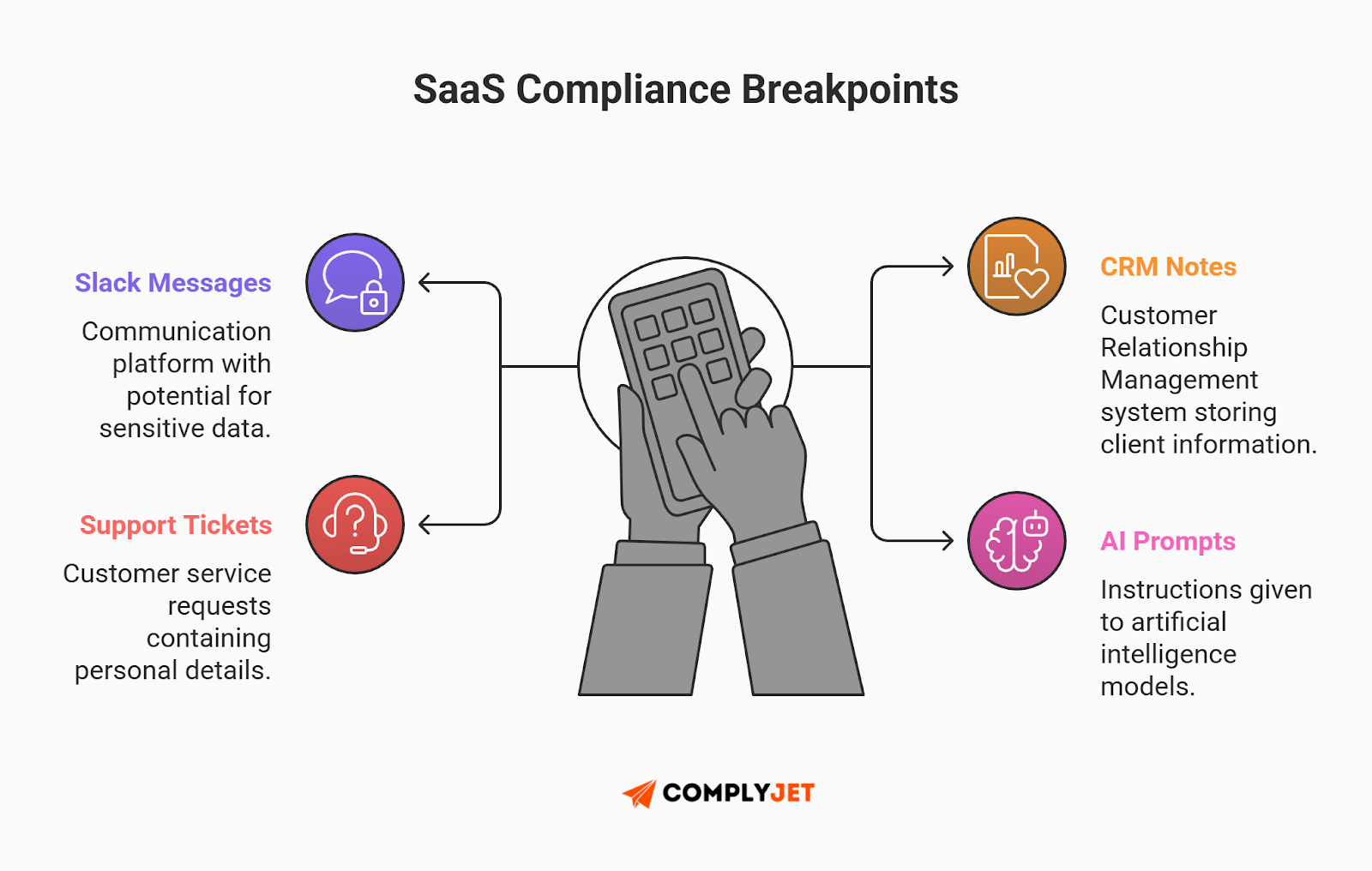
Furthermore, modern SaaS companies run on third-party tools like Salesforce, HubSpot, and Slack. But remember: compliance follows the data. If a sales rep puts a credit card number in a CRM note, that CRM is now "in scope" for PCI. Modern SaaS data classification must account for this operational reality.
To fix this, you need a defensive B2B compliance strategy:
- Automate Defense with DLP: Use Data Loss Prevention (DLP) tools that scan Slack and Jira in real-time. If they detect a credit card pattern or an SSN, they should automatically redact it.
- The BAA Mandate: If you share any PHI with a vendor (including your cloud provider like AWS or Google Cloud), you must have a signed BAA on file.
One pasted screenshot in a support channel can burn your PHI vs PCI vs PII compliance status instantly. A comprehensive strategy accepts that data travels; your job is to secure the journey.
Questions Auditors Actually Ask (FAQs)
At ComplyJet, we’ve seen young founders repeatedly struggle with the same misunderstandings around PHI vs PCI vs PII compliance. Below are the answers most blogs leave out.
If I use Stripe, am I automatically PCI compliant?
No, you are "compliant-capable" but must still file a Self-Assessment Questionnaire (SAQ). If your server touches raw card data, your compliance scope jumps to the most difficult audit level.
Can the same data be PHI in one database and PII in another?
Yes, because context is king; an email in a marketing tool is PII, but that same email in a medical portal becomes PHI. Mapping these specific data flows is the most complex part of PHI vs PCI vs PII compliance.
Does encrypting data make it "out of scope" for an audit?
No, if you hold the encryption keys, the data remains in scope because you still have the power to view it. Only third-party tokenization truly removes the data from your audit environment.
How do I handle compliance for remote employees?
You must secure the access point via strict VPNs or VDI so that sensitive data never physically lands on a local laptop. For HIPAA, this typically requires disabling split-tunneling to ensure all traffic stays within your PHI vs PCI vs PII compliance perimeter.
What happens if a customer puts a credit card into a support ticket?
This is a "toxic data spill" that requires immediate redaction; otherwise, your support database becomes technically in scope. Using automated DLP tools is the only way to manage these spills without breaking your PHI vs PCI vs PII compliance status.
The Final Takeaway
Ultimately, you need to reframe your mindset. Compliance isn't a "tax" you pay to do business; it is a premium feature that allows you to sell to the world's largest companies.
When an Enterprise buyer asks about your security, being able to say, "We handle PHI vs PCI vs PII compliance through a segmented, tokenized vault architecture," wins the deal. It proves operational maturity and technical excellence.
However, reaching this state shouldn't require a team of expensive auditors. For lean startups, manual evidence gathering is a trap that leads to burnout. This is where automation becomes your unfair advantage.
Platforms like ComplyJet allow you to map these controls once and automatically gather the evidence you need. Instead of chasing screenshots of your firewall settings, you build a system that updates itself.
Stop letting security questionnaires be the bottleneck to your growth. Move from manual panic to automated confidence. Make compliance boring again, so you can get back to what you actually love - building your product.
At ComplyJet we understand that for young teams, the only thing worse than a security questionnaire is the anxiety of filling it out. Let ComplyJet automate the evidence gathering so you can get back to what you actually love - building your product. Begin your free trial of ComplyJet today!



