In 2025, security compliance isn’t optional anymore. It’s the cost of doing business.
Whether you're closing big enterprise deals, expanding globally, or just protecting customer data, having the right security certification (or attestation) is a must-have rather than just a checkbox.
This guide cuts through the noise. We’ll break down ISO 27001 vs SOC 2, what they are, how they’re different, when to choose one over the other, and why more companies are going for both.
We’ll keep it simple, visual, and ridiculously practical.
Ready to get clear? Let’s dive in.
ISO 27001 vs SOC 2 : Quick Comparison
Here’s the deal: if you're short on time and need the TL;DR on ISO 27001 vs SOC 2, this snapshot is for you.
ISO 27001 is a globally recognized certification for building an Information Security Management System (ISMS).
SOC 2 is a US-originated attestation that proves your controls meet the Trust Services Criteria (TSC).
➡️ Certificate vs Attestation?
ISO 27001 results in a formal certificate. SOC 2 gives you an auditor’s report.
ISO 27001 vs SOC 2 : Key Differences
How these two frameworks think about security is completely different. Let’s ponder through the key ones.
Philosophy & Focus
ISO 27001 is all about building a system of a full ISMS that covers your people, processes, and tech.
SOC 2? It’s about proving you’re already doing the right things, mapped to the Trust Services Criteria (TSC).
Quick tip: If you need a long-term security framework, ISO 27001 fits. If you're proving current practices for US clients, go with SOC 2.
Certification vs Attestation
ISO 27001 gives you a 3-year cert, with annual check-ins to stay compliant.
SOC 2 provides a detailed auditor’s report (Type 1 = point in time, Type 2 = 3–12 month window) that clients review directly.
💡 Why it matters: ISO 27001 proves you’re managing security well. SOC 2 shows you actually did what you said you would.
Control Approach
ISO 27001 comes with Annex A of 93 defined controls you map your org against (some can be excluded).
SOC 2 uses flexible criteria under 5 pillars: Security (always required), Availability, Confidentiality, Processing Integrity, and Privacy.
🎯 Pro tip: SOC 2 gives more wiggle room. ISO is stricter but more structured.
Scope, Evidence & Deliverables
ISO 27001 audits your ISMS: policies, risk register, internal audits, leadership involvement.
SOC 2 audits evidence of control operation: logs, screenshots, tickets, access reviews (especially for Type 2).
Timeline & Effort
For ISO 27001, expect 2–6 months of prep, then Stage 1 & 2 audits.
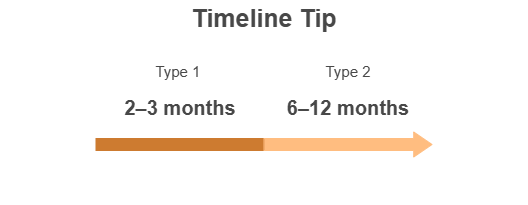
SOC 2 Type 1 can be done in a couple of months. Type 2 takes longer (3–12 months) since it evaluates performance over time.
⏱️ Speed tip: ISO takes more structured effort. SOC 2 Type 1 is fastest to attain.
Budget
ISO 27001 typically costs $15k–$60k+ depending on org size and consultant involvement.
SOC 2 runs ~$15k–$70k+, especially for Type 2 with automation or multiple TSCs.
💸 Smart move: Consider bundling both with a single audit firm. Tools like ComplyJet can save time and money with unified control tracking.
SOC 2 & ISO 27001: What’s Common?
SOC 2 and ISO 27001 aren’t rivals in general. They’re overlapping frameworks built on the same foundation. That’s why more and more companies are doing both (and saving serious time doing it).
Same Market Pressure, Different Labels
SOC 2 dominates in the U.S., especially in B2B SaaS, fintech, and any industry handling sensitive customer data. If you’re selling to American clients, it’s usually the first ask.
ISO 27001 rules in Europe, APAC, and across globally regulated sectors. It’s favored for GDPR alignment, cross-border contracts, and international trust.
🌍 Real-world scenario: A U.S.-based SaaS expanding into Europe? You’ll likely need to add ISO 27001 even if you already have SOC 2.
80–96% Control Overlap = Major Time Savings
Here’s the good news: these two standards share a massive chunk of controls. Risk assessments, access policies, incident response, training, vendor reviews—they’re core to both.
Many teams reuse 80–96% of the same controls between SOC 2 and ISO 27001. That’s huge when it comes to time, effort, and budget.
⚙️ Smart move: ComplyJet helps you map once and track everything in a single dashboard with no double work and just smart reuse.
Auditor Synergy
Both SOC 2 and ISO 27001 are built on the same goal: protecting the Confidentiality, Integrity, and Availability (CIA) of information.
Auditors know this too. If you’ve nailed SOC 2, you’re already well on your way to ISO 27001 and vice versa.
🔁 Bottom line: Dual compliance doesn’t mean double the work. Done right, it’s more like 1.5x the effort with 2x the credibility.
Control Mapping = Your Secret Weapon
The overlap isn’t just conceptual but mappable. The AICPA even published an official sheet linking ISO 27001:2013 controls with SOC 2’s Trust Services Criteria (TSC). And while ISO got an update in 2022, the core mapping still holds.
Use that mapping to align controls and reuse your evidence for things like:
- Security training logs
- Vendor risk reviews
- Access control documentation
- Incident response records
📎 Pro tip: ComplyJet lets you map ISO controls to SOC 2 TSC (and vice versa), so you only collect evidence once.
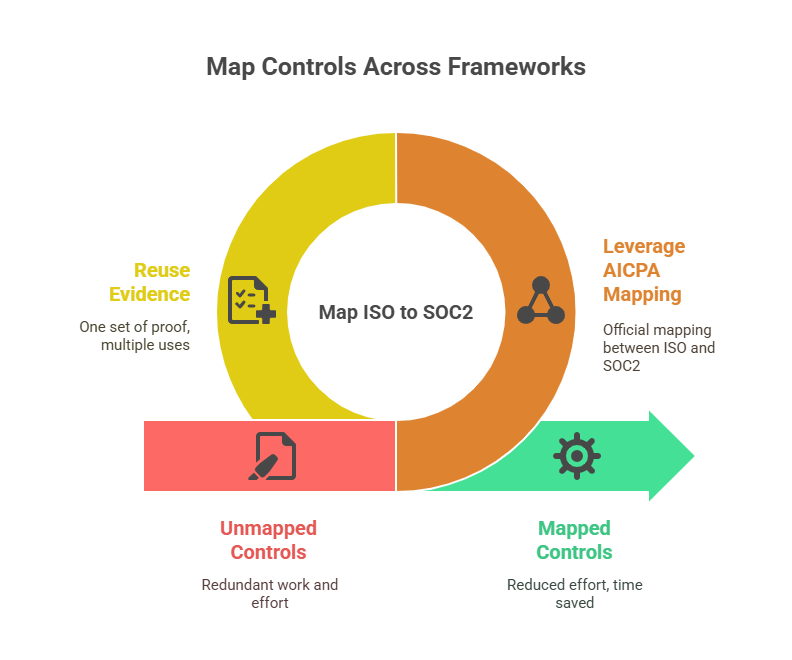
Picking ISO 27001, SOC 2 or Both
Not all customers care about the same compliance badge. Your strategy should match your market, industry, and growth goals.
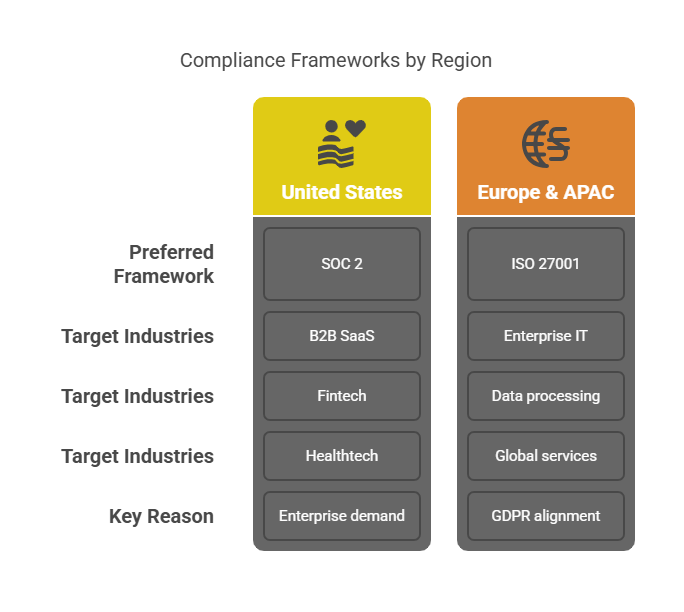
Who Wants What? (And Where)
In the U.S., SOC 2 is the go-to. If you're selling B2B SaaS or handling sensitive data for fintech, healthtech, or cloud platforms, this is probably your first hurdle.
In Europe and APAC, ISO 27001 leads the pack. It aligns with GDPR, international standards, and enterprise procurement requirements.
🧭 Quick takeaway:
U.S. = SOC 2
Global/EU = ISO 27001
When Regulated or Enterprise = Both
Targeting Fortune 500s, government contracts, or regulated industries (finance, healthcare, defense)? They’ll likely expect dual compliance.
Here’s why:
- ISO shows your system is built to last.
- SOC 2 proves it's actually working.
Together, they check both boxes.
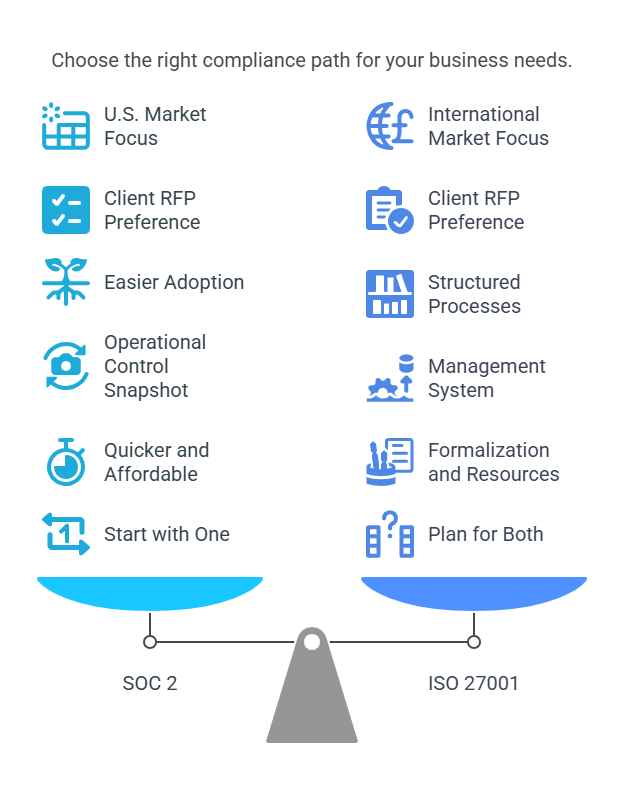
How to Choose ?
- Where are your customers?
US-heavy? Go SOC 2. Global clients? ISO 27001’s your friend. - What do RFPs ask for?
Don’t guess but check. Some prospects require one, the other, or both. - How mature is your program?
SOC 2 is lighter to start. ISO 27001 fits best if you’ve already got structure in place. - System vs snapshot?
ISO = management system. SOC 2 = operating controls in action. - What's your budget and headcount?
ISO can be resource-heavy. SOC 2 tends to be faster if you’re looking for quick validation. - Are you scaling fast?
High-growth teams often need both eventually so, start with one, but architect for both.
Dual Strategy: Phased vs Parallel
If both frameworks are in your future, two proven paths:
- Phased:
Launch SOC 2 Type 1 first (quick win), then build toward ISO 27001 in 6–12 months. - Parallel:
Set up unified controls, track shared evidence, and get both done with a single audit partner.
⏱️ Fast-track tip: ComplyJet helps you manage both frameworks through a single dashboard—shared controls, mapped evidence, one streamlined process.
Practical Implementation
You’ve picked your path—ISO 27001, SOC 2, or both. Now let’s make it real, without the overwhelm.
Here’s exactly how to get certified or attested—step by step.
ISO 27001:2022 – 10 Steps to Certification
- Get leadership buy-in.
ISO requires top-level support. Make sure execs are on board early. - Define your ISMS scope.
Decide which systems, teams, and offices the ISMS will cover. - Run a risk assessment.
Identify potential threats, vulnerabilities, and business impacts. - Create your Statement of Applicability (SoA).
Map which Annex A controls apply—and explain any you skip. - Draft core InfoSec policies.
At minimum, cover Access Control, Risk Management, and Security Policy. - Do internal audits.
Test your ISMS yourself before inviting the external auditors in. - Train your team.
ISO demands security awareness company-wide. No one’s off the hook. - Pick a certifying body.
Choose an accredited registrar to conduct your audit. - Stage 1 Audit – Readiness check.
Auditors review your docs and flag early gaps. - Stage 2 Audit – Full review.
They test your system. Pass this, and boom—you’re certified!
📅 Timeline tip: Expect 6–12 months depending on company size and how ready you are.
SOC 2 – Type 1 & Type 2 Paths
Type 1 – Fastest way in:
- Define your scope & trust criteria.
Security is mandatory. Add others like Availability or Privacy as needed. - Implement key controls.
Focus on essentials—access control, monitoring, incident handling. - Document your policies.
Auditors need clear written procedures to review. - Run a readiness assessment.
Check for gaps before the official audit begins. - Audit day!
Your auditor validates controls as of a specific date. - Get your Type 1 report.
It includes a system description + the auditor’s opinion on your setup.
Type 2 – More rigorous, more respected:
- Define your scope & trust criteria.
Security is mandatory. Add others like Availability or Privacy as needed. - Implement key controls.
Focus on essentials—access control, monitoring, incident handling. - Document your policies.
Auditors need clear written procedures to review. - Run a readiness assessment.
Check for gaps before the official audit begins. - Kick off the observation window.
Track your controls in action over 3–12 months. - Maintain controls & collect evidence.
Think access logs, support tickets, system screenshots. - Final audit & Type 2 report.
Auditor checks that your controls actually worked over time.
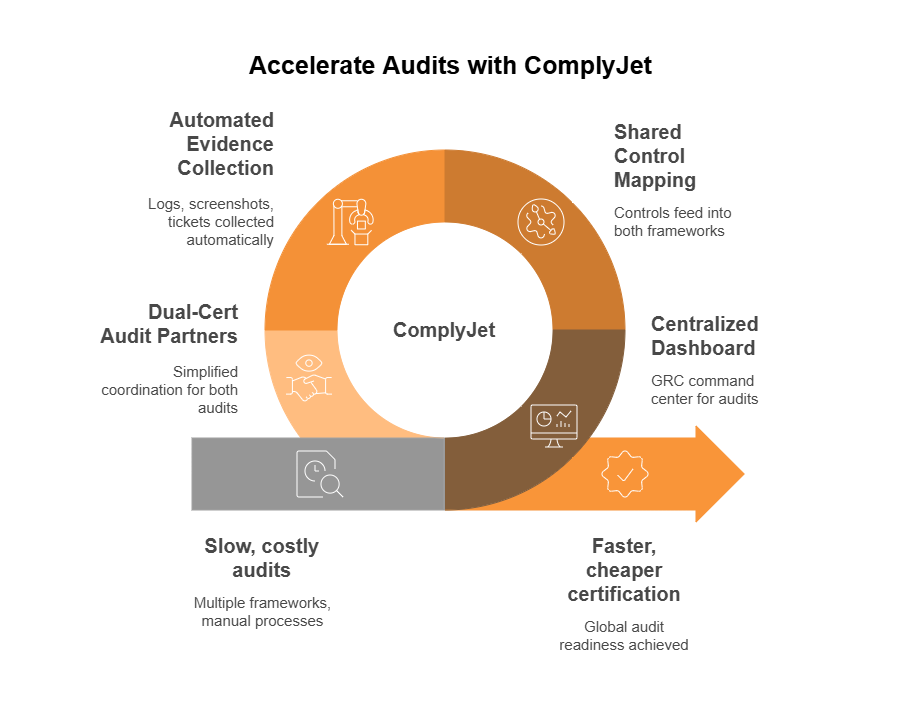
Combined Fast‑Track Strategy – Do Both, Smarter
- Start with ComplyJet as your GRC command center.
Build and manage one unified control set for both ISO 27001 and SOC 2, straight from a single dashboard. - Map shared controls once, use them twice.
With ComplyJet, controls like access reviews, password policies, and monitoring logs sync to both frameworks automatically. - Automate evidence collection like a pro.
ComplyJet pulls logs, screenshots, tickets, and access records from your existing stack so, no more chasing down artifacts manually. - Use ComplyJet’s dual-cert audit partners.
We work with top-tier audit firms certified for both ISO 27001 and SOC 2, so you only coordinate once and streamline the whole process. - Run parallel or staggered audit; your call.
Start with SOC 2 Type 1 while building your ISMS for ISO. Or go big and knock both out together. Either way, ComplyJet keeps it all in sync.
🚀 Why this works:
You avoid duplication, speed up both audits, save budget—and look super polished to customers worldwide.
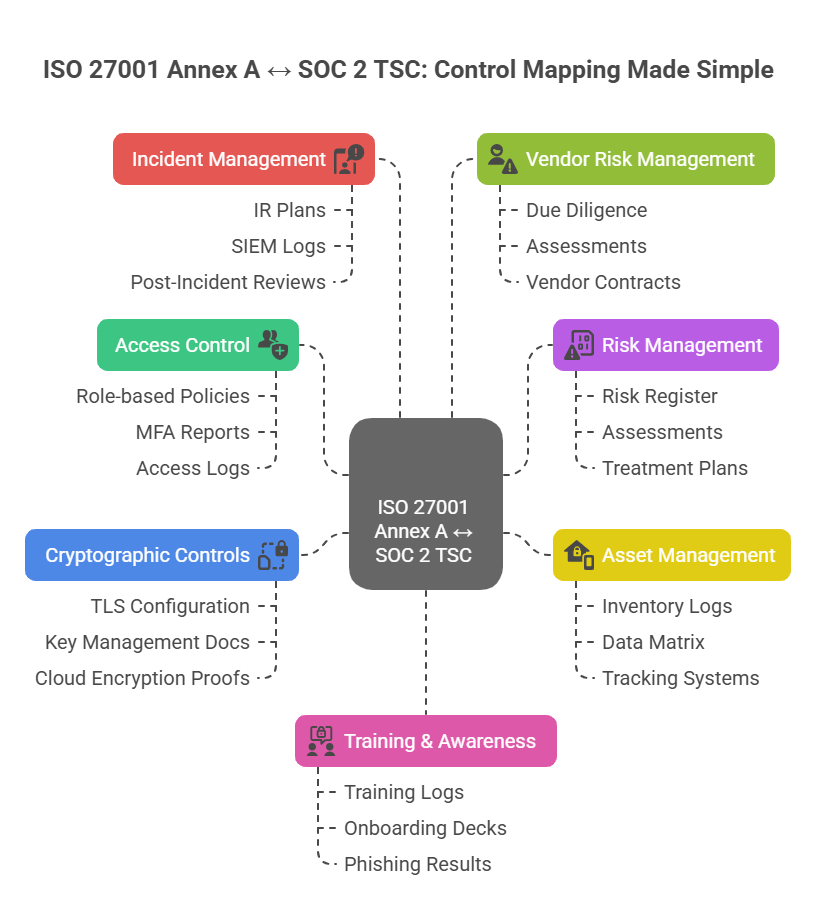
ISO 27001 & SOC 2: Control Mapping
Let’s get tactical: if you're going for both ISO 27001 and SOC 2, mapping controls between them is the move to cut time, reduce duplicate effort, and breeze through audits.
ISO 27001:2022 has 93 controls grouped into four themes namely, Organizational, People, Physical, and Technological.
SOC 2 evaluates controls under the Trust Services Criteria (TSC), broken down into Security (mandatory), Availability, Confidentiality, Processing Integrity, and Privacy.
Despite different structures, the overlap is huge. With smart mapping, you can align your controls and reuse 80–90% of your evidence across both.
To help you visualize just how much overlap exists, here’s a breakdown of key ISO 27001 controls and how they directly map to SOC 2 Trust Services Criteria (TSC). We’ll also show you what evidence typically satisfies both frameworks.
Access Control
ISO 27001 Controls: A.5.15 – A.5.18
SOC 2 TSC Mapping: CC6.1 – CC6.8
These controls ensure only authorized users access systems and data, based on roles and responsibilities.
Examples of Common Evidence:
- Role-based access policies
- User provisioning/de-provisioning logs
- MFA enforcement reports
- Periodic access reviews
Risk Management
ISO 27001 Controls: A.5.4, A.8.2
SOC 2 TSC Mapping: CC3.1 – CC3.4
Both frameworks require organizations to identify, assess, and manage information security risks on an ongoing basis.
Examples of Common Evidence:
- Documented risk register
- Risk assessment reports
- Risk treatment plans
- Risk acceptance records
Asset Management
ISO 27001 Controls: A.5.9 – A.5.12
SOC 2 TSC Mapping: CC6.2, CC9.1
Controls that deal with managing and securing company assets, including devices, data, and systems.
Examples of Common Evidence:
- Asset inventory logs
- Data classification matrix
- Asset handling procedures
- Laptop tracking systems
Cryptographic Controls
ISO 27001 Control: A.8.24
SOC 2 TSC Mapping: CC6.10
Both standards require strong encryption protocols to protect sensitive information—at rest and in transit.
Examples of Common Evidence:
- TLS configuration reports
- Encryption policies
- Key management documentation
- Data-at-rest encryption proofs from cloud providers
Incident Management
ISO 27001 Controls: A.5.25 – A.5.27
SOC 2 TSC Mapping: CC7.1 – CC7.4
These controls focus on detecting, responding to, and learning from security incidents.
Examples of Common Evidence:
- Incident response plan
- Security monitoring system logs
- Incident tickets & resolution documentation
- Post-incident review summaries
Vendor Risk Management
ISO 27001 Controls: A.5.19 – A.5.22
SOC 2 TSC Mapping: CC9.2
Addresses the risks introduced by third-party providers and outlines how to manage them.
Examples of Common Evidence:
- Vendor due diligence questionnaires
- Third-party security assessments
- Contracts with data protection clauses
- Ongoing vendor review logs
Training & Awareness
ISO 27001 Control: A.6.3
SOC 2 TSC Mapping: CC3.3, CC2.2
Security is only as strong as your people. These controls ensure employees are trained and aware of risks and responsibilities.
Examples of Common Evidence:
- Security awareness training completion logs
- Onboarding decks
- Annual refresher course materials
- Phishing simulation results
FAQs
Here are some of the most common questions companies ask when comparing ISO 27001 vs SOC 2, with straight-to-the-point answers.
Is ISO 27001 equivalent to SOC 2?
Not quite. ISO 27001 is a certification for your security management system. SOC 2 is an attestation of how your controls operate. They overlap in content but differ in purpose and form.
Does SOC 2 Type 2 replace ISO 27001?
Nope. SOC 2 Type 2 proves control effectiveness over time, but it doesn’t replace the structured ISMS approach of ISO 27001. Many companies eventually need both.
Can I certify ISO 27001 and attest SOC 2 together?
Yes, and it’s actually efficient! Many audit firms handle both, and control overlap (80%+) means shared evidence, less work, and faster results.
What is the renewal frequency?
ISO 27001: Valid for 3 years with annual surveillance audits.
SOC 2: Annual renewal for both Type 1 and Type 2 (re-attestation).
What changed in ISO 27001:2022?
The 2022 update merged and simplified Annex A controls, down from 114 to 93 and added themes like threat intelligence and cloud services. It's more modern and aligned with today’s risks.
Conclusion
Here’s the bottom line: ISO 27001 helps you build a rock-solid security system. SOC 2 proves your controls actually work.
They’re not rivals—they’re a power duo. And in 2025, more customers are asking for both.
Which one should you tackle first? It depends on your geography, industry, and how mature your security posture is today. But here’s the good news: doing both isn’t just doable—it’s efficient when you plan it right.
So, what now?
Run a gap analysis. Figure out where your security posture stands today.
Leverage automation with ComplyJet. Streamline both ISO and SOC 2 in one smart workflow.
Talk to your auditor early. Set the right scope and avoid surprises later.
.png)


