"Move fast and break things" is dead. In 2026, the winners are the companies that move fast and prove they won't break anything.
And that should be at the heart of any ISO 27001 checklist in 2026. It is the difference between a risky vendor and a scalable enterprise partner.
If you want to close contracts with Fortune 500s or your clients in the healthcare industry, they don't just ask if you are secure. They demand proof. That is where the ISO 27001 checklist comes in. It is no longer optional for B2B SaaS scaling; it is a revenue enabler.

However, most guides you find online are outdated and/or written for auditors, not operators. They are full of academic fluff that doesn't tell you what to actually do to clear your ISO 27001 checklist in the strict, modern compliance landscape.
Founder Tip: Don't view this process as just "checking boxes." View it as building the trust layer of your product. A clean ISO 27001 checklist is often the difference between a 2-week and a 6-month procurement cycle.
This guide is different. It assumes you have a report of your ISO 27001 internal audit ready, and are gearing up for the final push towards certification. We aren't going to lecture you on the history of the standard. Instead, we are giving you a practical, "no-fluff" ISO 27001 checklist tailored for teams who like to move fast. The goal is to provide you with a quick but concrete checklist to get your audit started - covering some tricky ISO 27001 requirements, the new Annex A 2022 updates, and the exact documentation you need to pass your audit without hiring an army of consultants.
New to the compliance landscape? For a step-by-step breakdown of the entire ISO 27001 audit process and their realistic timelines, check out our ISO 27001 for Startups guide.
Ready to tackle your ISO 27001 checklist and get the tricky parts covered? Let's dive in.
Meet enterprise compliance standards without enterprise-level pricing. ComplyJet helps you achieve the same certifications most vendors offer - at nearly half the cost. Start your free trial now.
ISO 27001 in a Nutshell
Before we tackle the controls, we need to clarify what we are actually building.
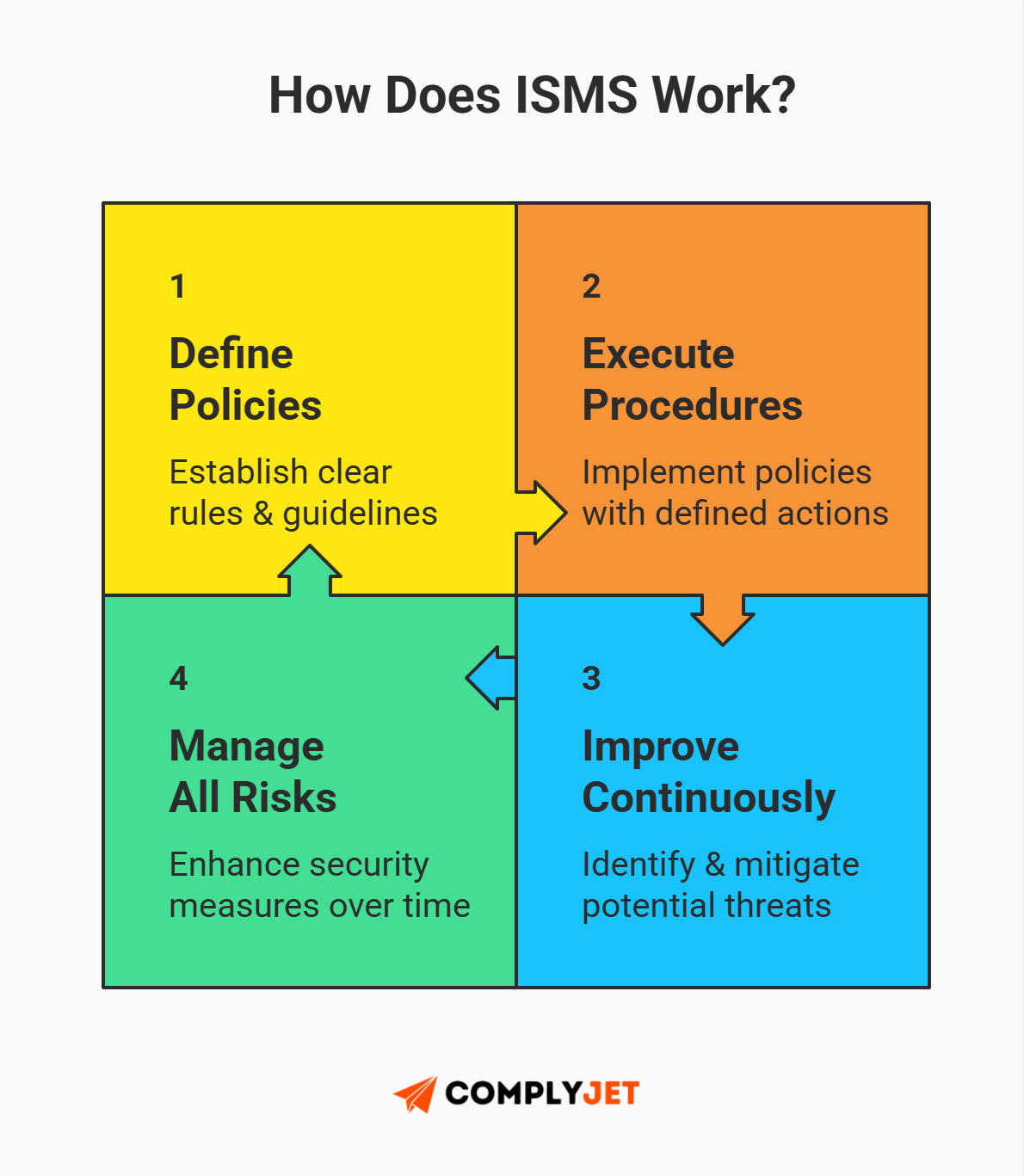
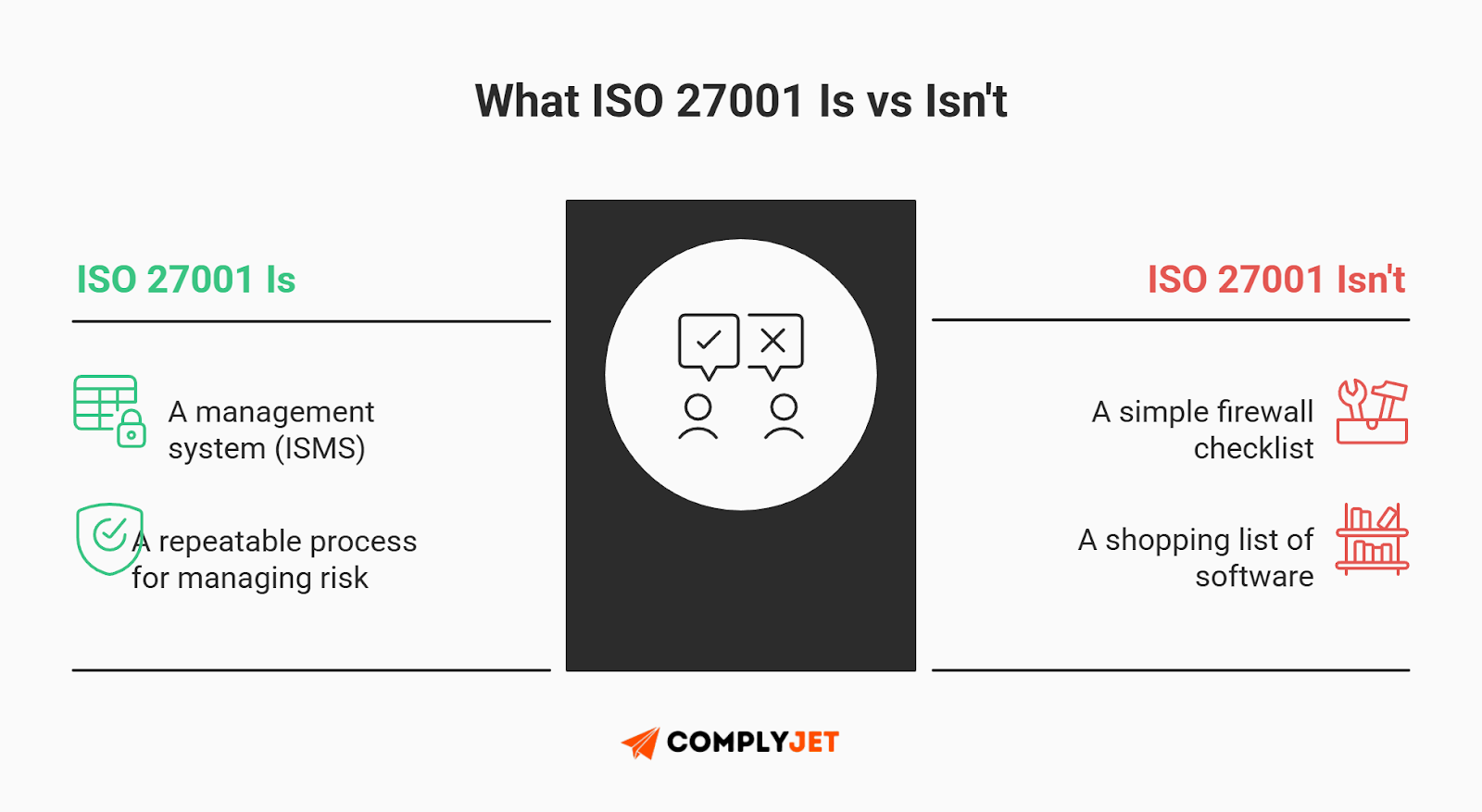
At its core, ISO 27001 is not a list of firewalls you must buy. It is a framework for an Information Security Management System (ISMS). It proves you have a process to identify, manage, and reduce risks to the data you hold.
Definition: An ISMS is a set of policies and procedures for systematically managing an organization's sensitive data. Think of it as the "operating system" for your company's security.
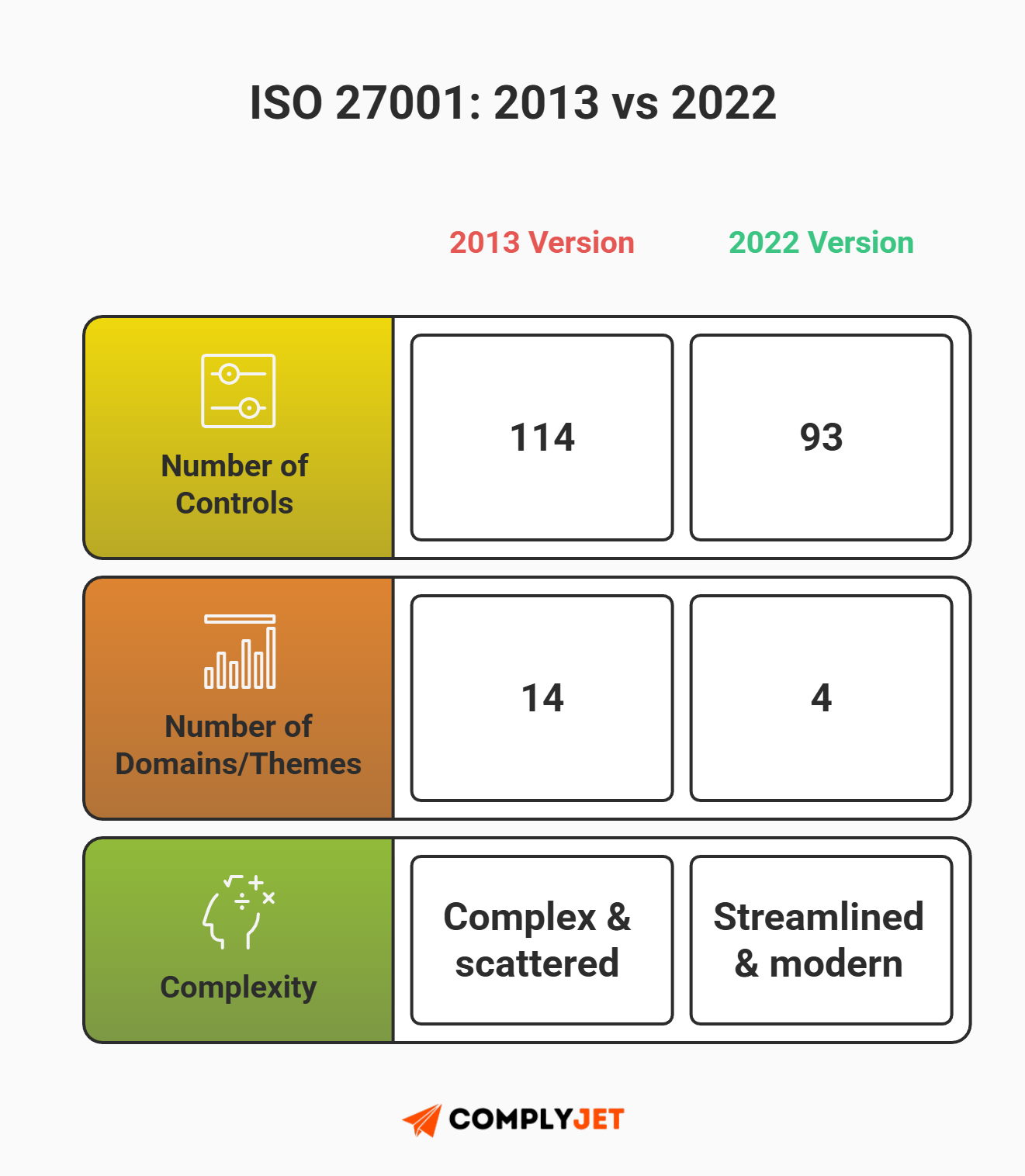
The Update You Need to Know: 2013 vs. 2022
If you are Googling guides, be careful. Many older articles reference the 2013 standard. That version is outdated.
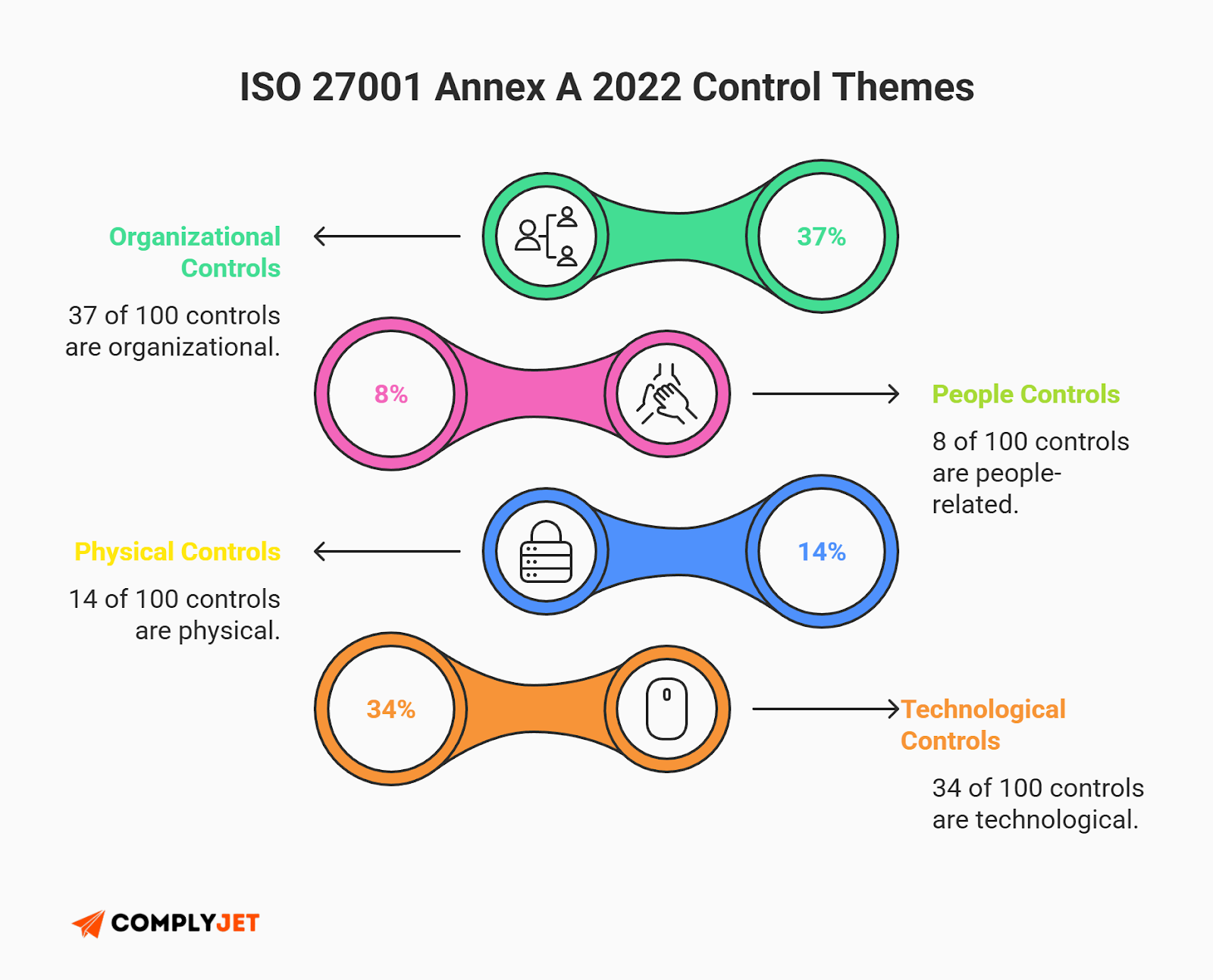
In October 2022, ISO released a major update. The old version had 114 controls organized into 14 complex domains. The new ISO 27001 2022 checklist is much more streamlined. It merges those controls into just 93 controls categorized into 4 simple themes:
- Organizational (37 controls)
- People (8 controls)
- Physical (14 controls)
- Technological (34 controls)
This guide focuses strictly on the new 2022 standards. If you are starting today, you should not be looking at 2013 documentation.
Who Actually Needs This?
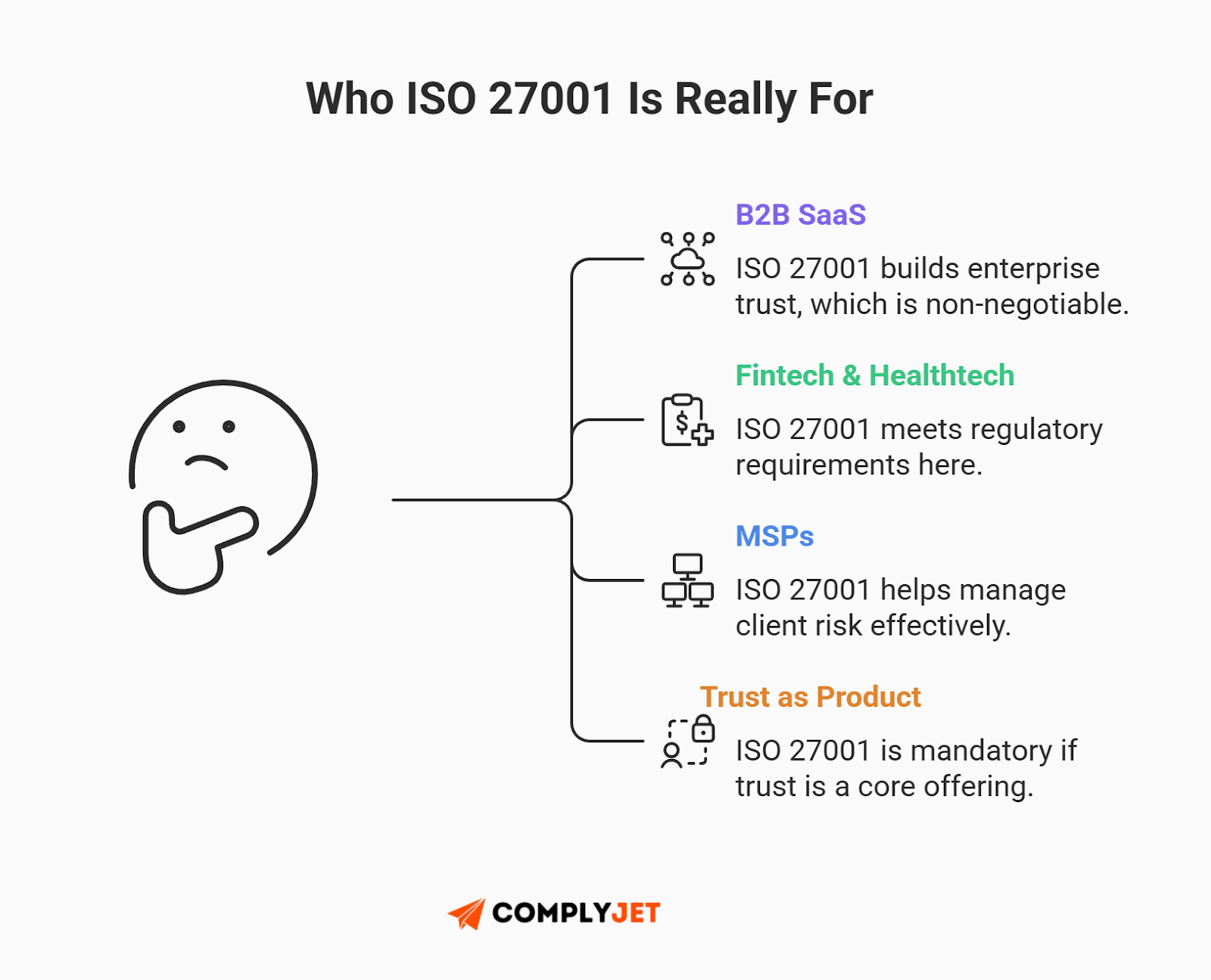
Technically, any company can get certified. But practically, this ISO 27001 checklist is designed for companies where trust is the product.
- B2B SaaS: If you sell to enterprises, this is table stakes.
- Fintech & Healthtech: Highly regulated industries often use ISO 27001 as a baseline before tackling SOC 2 or HIPAA.
- Managed Service Providers (MSPs): You hold the keys to other people's kingdoms; you need to prove you are safe.
If you fit one of these buckets, an ISO 27001 checklist isn't paperwork - it's your license to operate.
Still stuck in a dilemma whether its time for your enterprise to get ISO 27001 certified? Our complete ISO 27001 guide for founders may help you make your decision easier.
You shouldn't need a massive budget or a dedicated security hire to get certified. ComplyJet is designed specifically for startups that need to move fast. We help you get audit-ready without the enterprise price tag. Check out our ISO 27001 compliance offerings.
Phase 1: Before You Start with the ISO 27001 Checklist
Most companies fail before they even look at a control because they try to "boil the ocean." They attempt to apply strict security rules to the entire company instantly. That is a recipe for burnout.
Before you open your spreadsheet or compliance platform, you need to nail these three "Pre-Flight" steps.
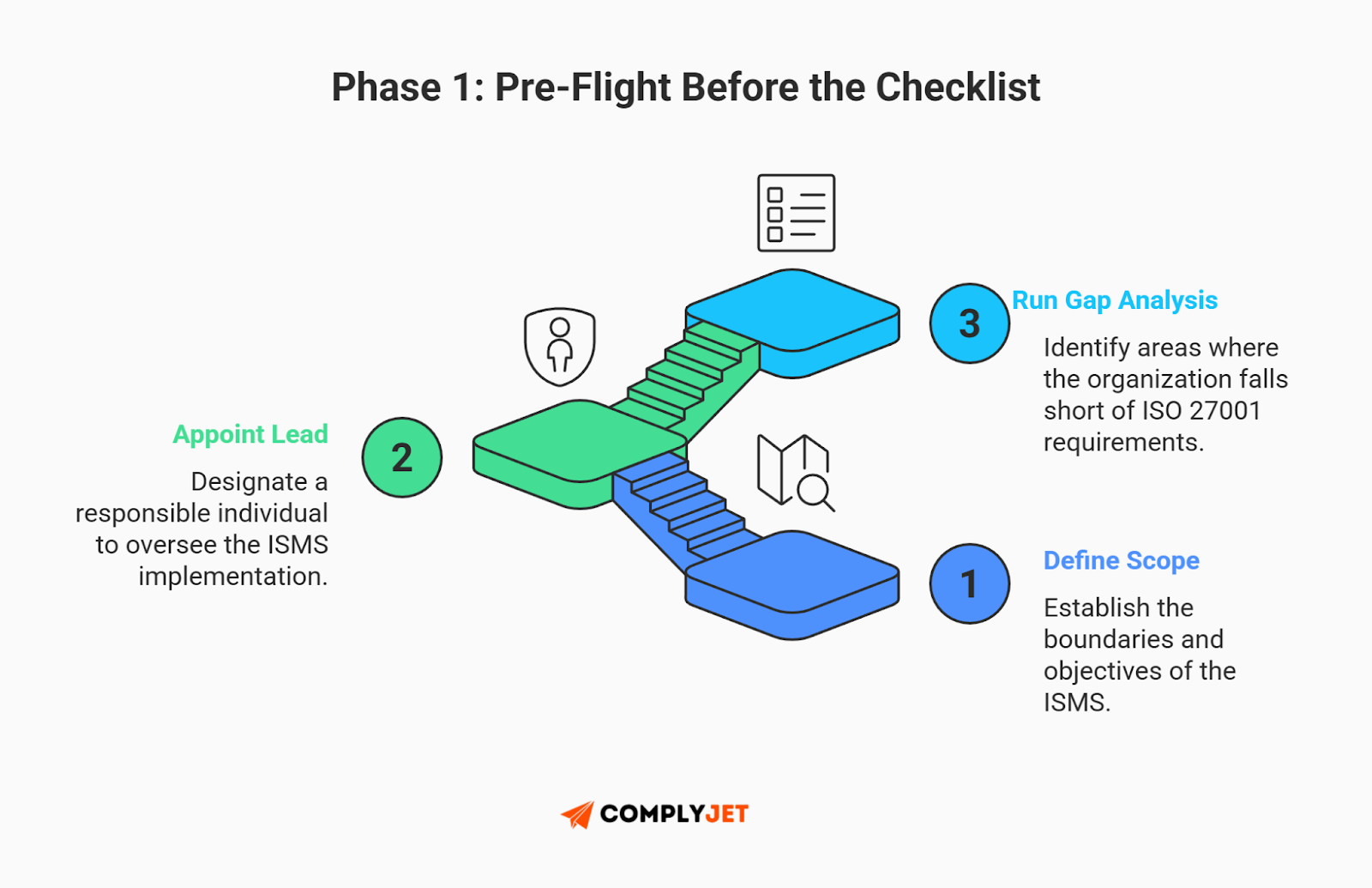
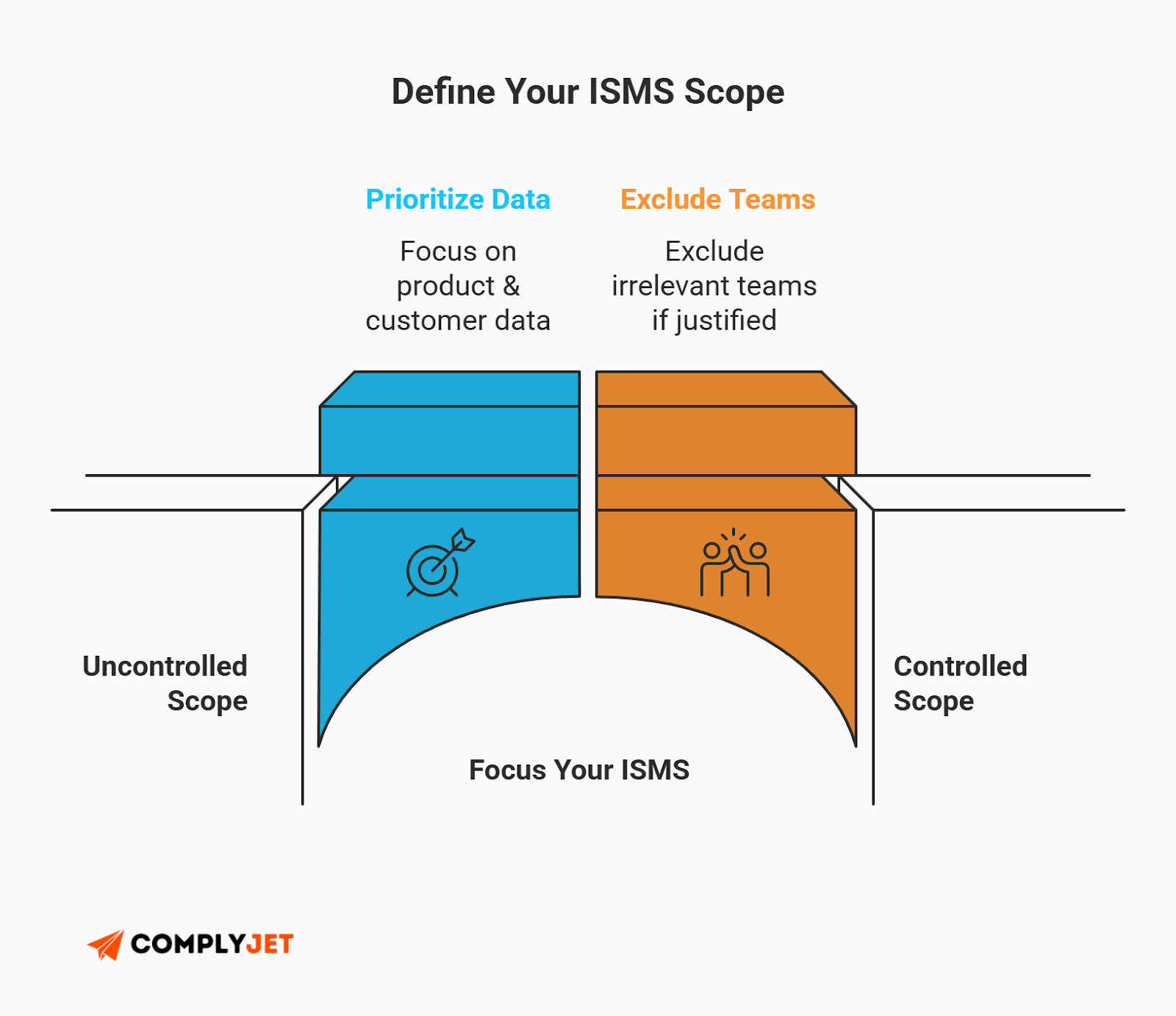
Step 1: Define Your ISMS Scope
This is the most critical decision you will make. Your ISMS Scope defines the boundaries of what is being audited.
Does every laptop in your company need to be locked down? Maybe not. If your marketing team never touches customer data, you might be able to exclude them from the initial certification.
Founder Tip: Keep your ISMS Scope as tight as possible for Year 1. Focus strictly on the people, systems, and locations that support your product and customer data. You can always expand the scope in Year 2, but starting small makes the audit survivable.
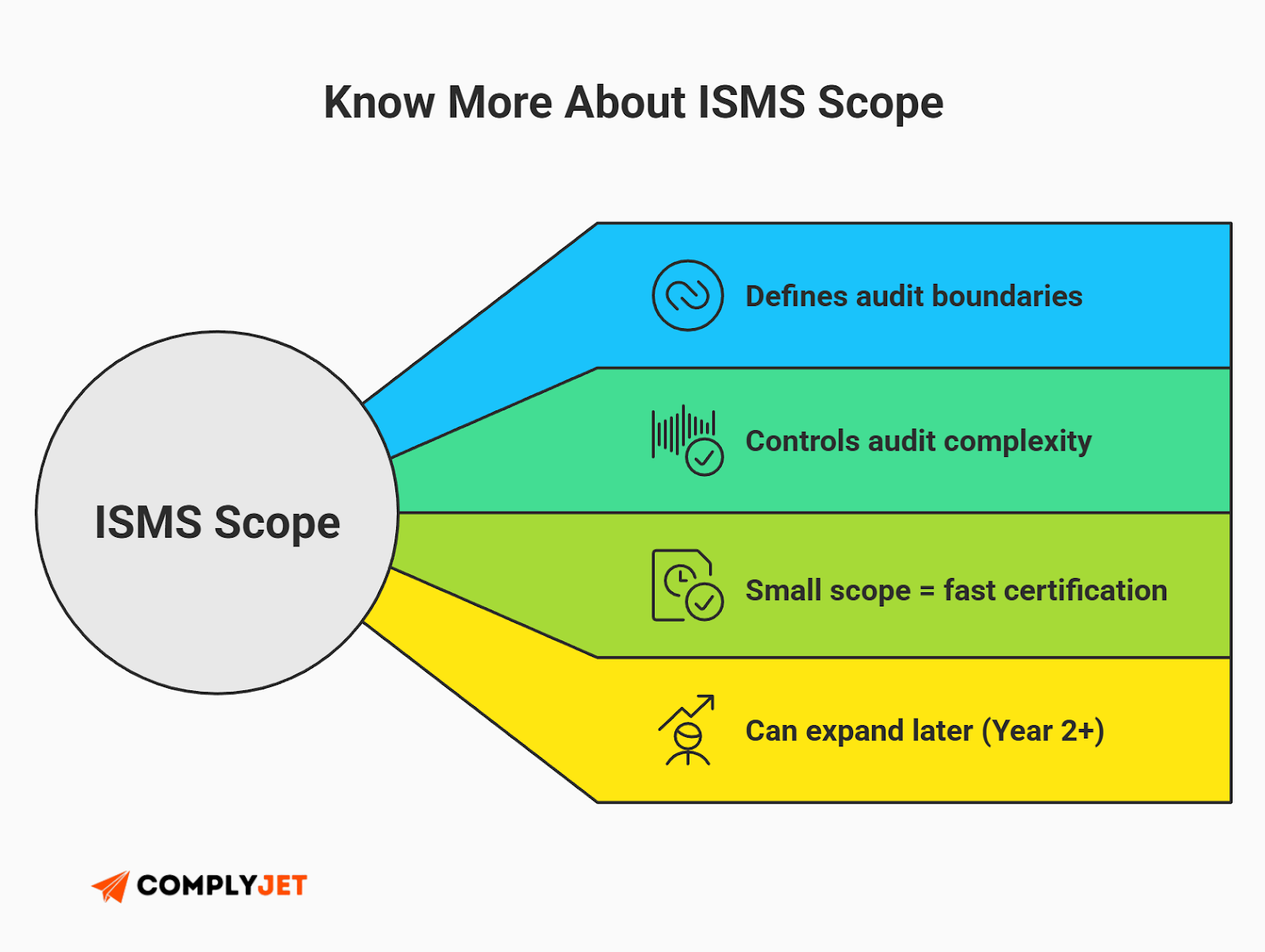
Defining a clear ISMS Scope prevents "scope creep," where auditors start asking questions about departments that have nothing to do with security.
Step 2: Appoint Your Security Lead
You need a "Management Representative" - the single person responsible for your ISO 27001 checklist.
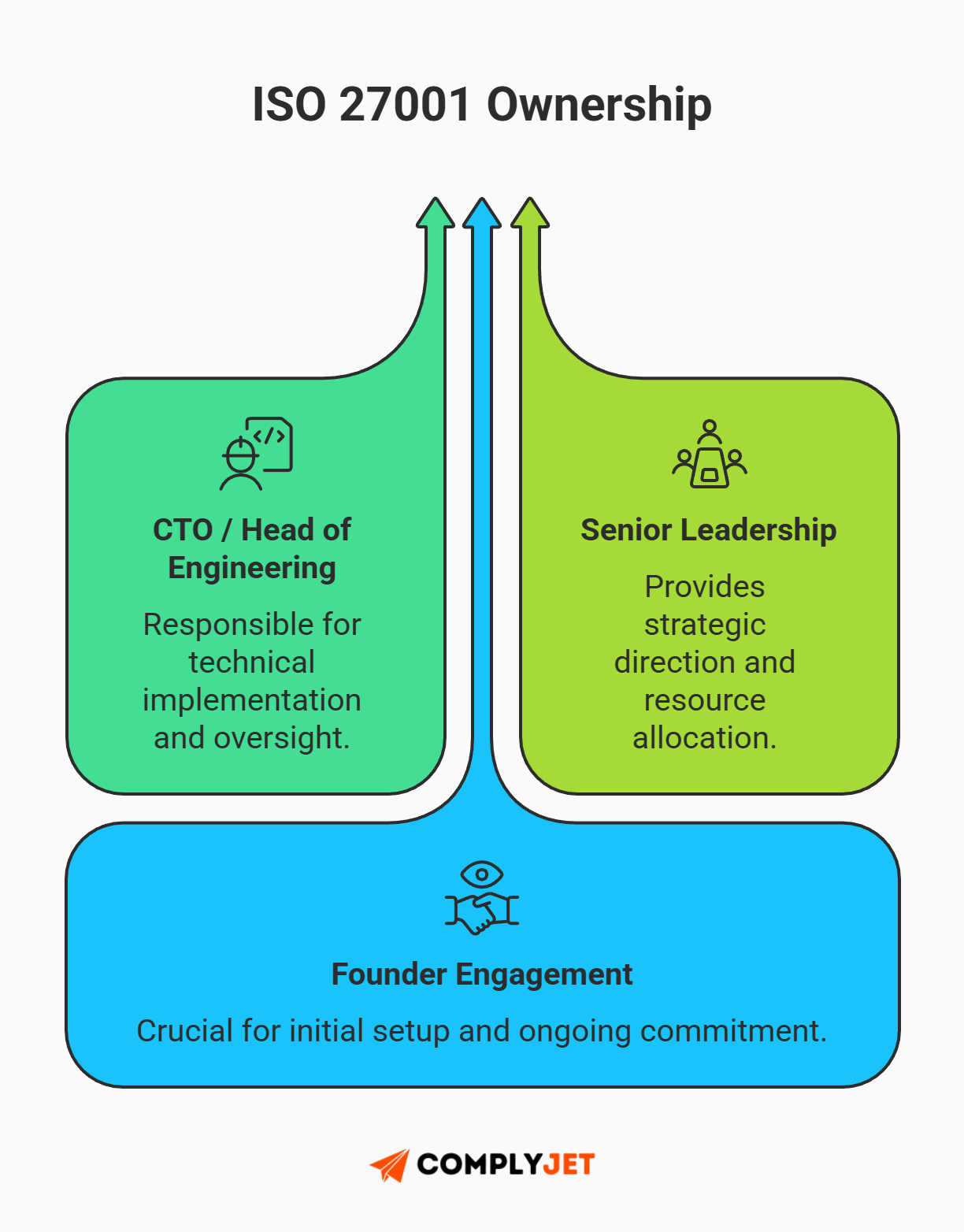
In a startup, this is usually the CTO or a Head of Engineering.
Warning: Do not make this a "side hustle" for a junior developer. The auditor needs to see that senior management is involved. If the founder is completely checked out, you will catch a "Major Non-Conformity" (more on that later) for lack of leadership commitment, leaving your curated ISO 27001 checklist dead on arrival.
Step 3: Run a Gap Analysis
You can't fix what you don't measure. A Gap Analysis is a mock audit you do on Day 1. It compares your current messy reality against the ISO 27001 checklist to see what's missing.
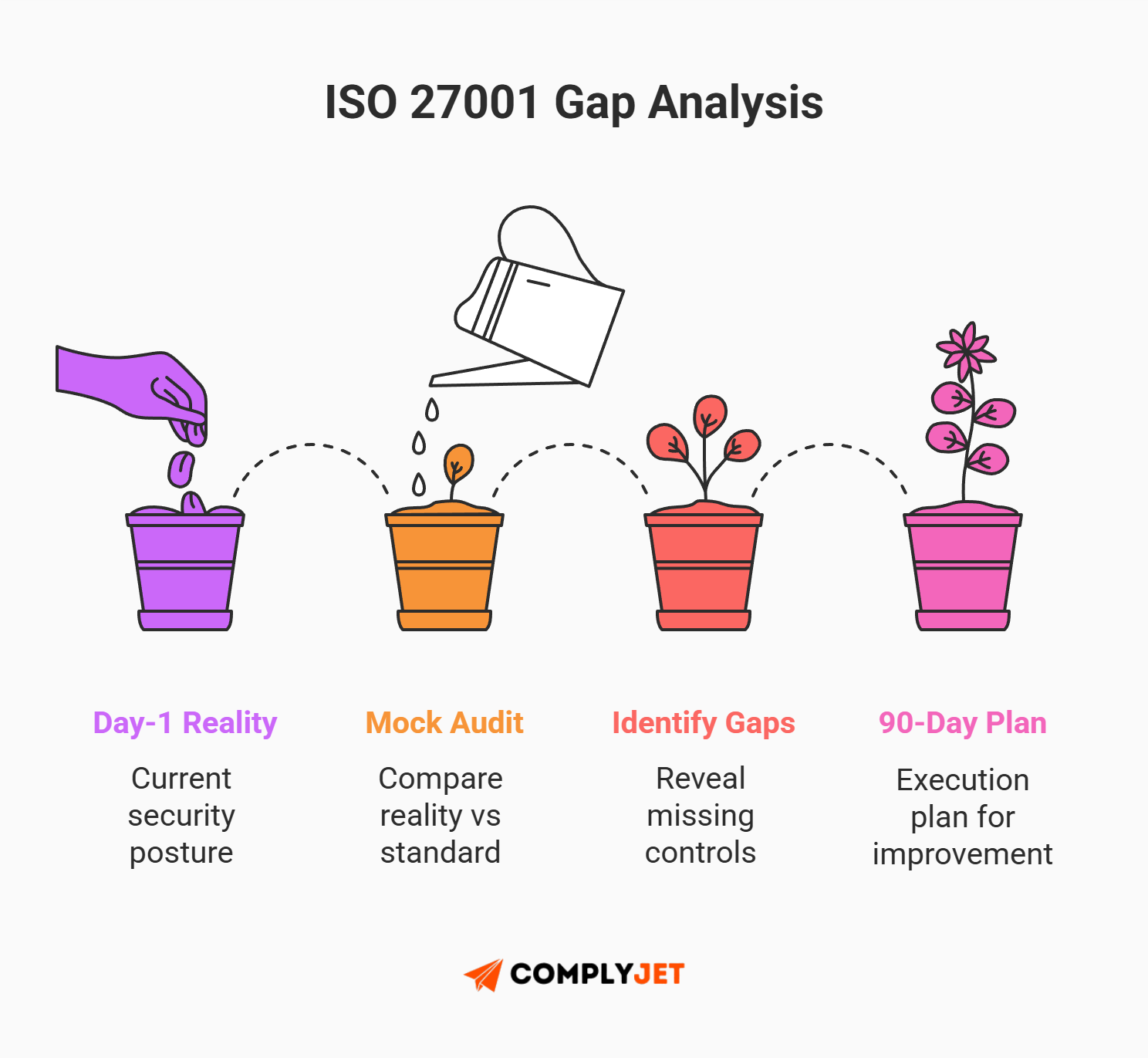
- Do you have an onboarding checklist? (Probably not).
- Do you have Multi-Factor Authentication (MFA) everywhere? (Maybe).
- Do you have offboarding logs? (Unlikely).
The output of your Gap Analysis becomes your "To-Do List" for the next 3 months. Without this, you are flying blind and your ISO 27001 checklist lacks teeth.
Phase 2: The Mandatory Documentation Checklist (Clauses 4-10)
If you think compliance is just about buying antivirus software, think again. The bulk of your initial work involves defining the "rules of the game" through documentation.
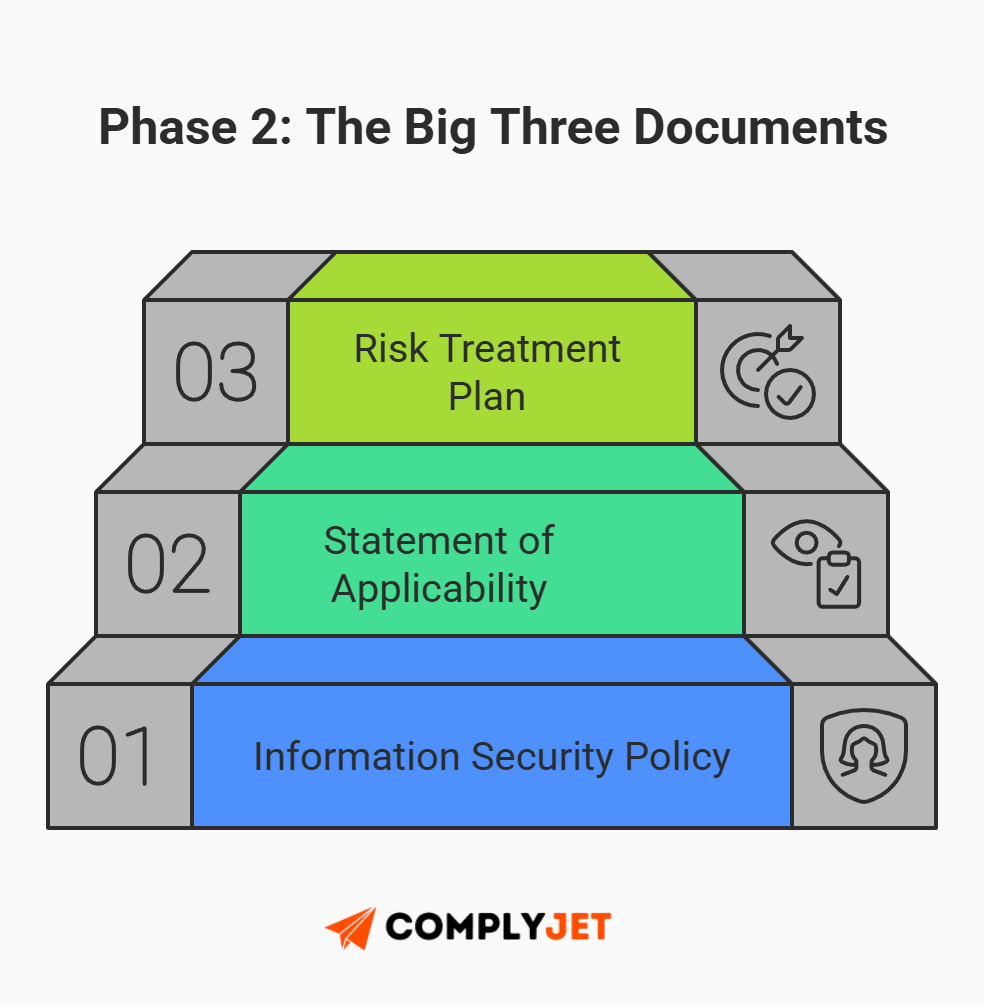
While the standard lists dozens of potential documents, you should focus on the "Big Three." These are the non-negotiables that form the backbone of your ISO 27001 requirements.
The "Big Three" Must-Have ISO 27001 Documents
- The Information Security Policy (ISP)
This is your constitution. It is a high-level document signed by leadership that states, "We care about security, and here are our general goals." It doesn't need to be 50 pages. It just needs to prove that security is a top-down mandate, not just an IT problem.
- The Statement of Applicability (SoA)
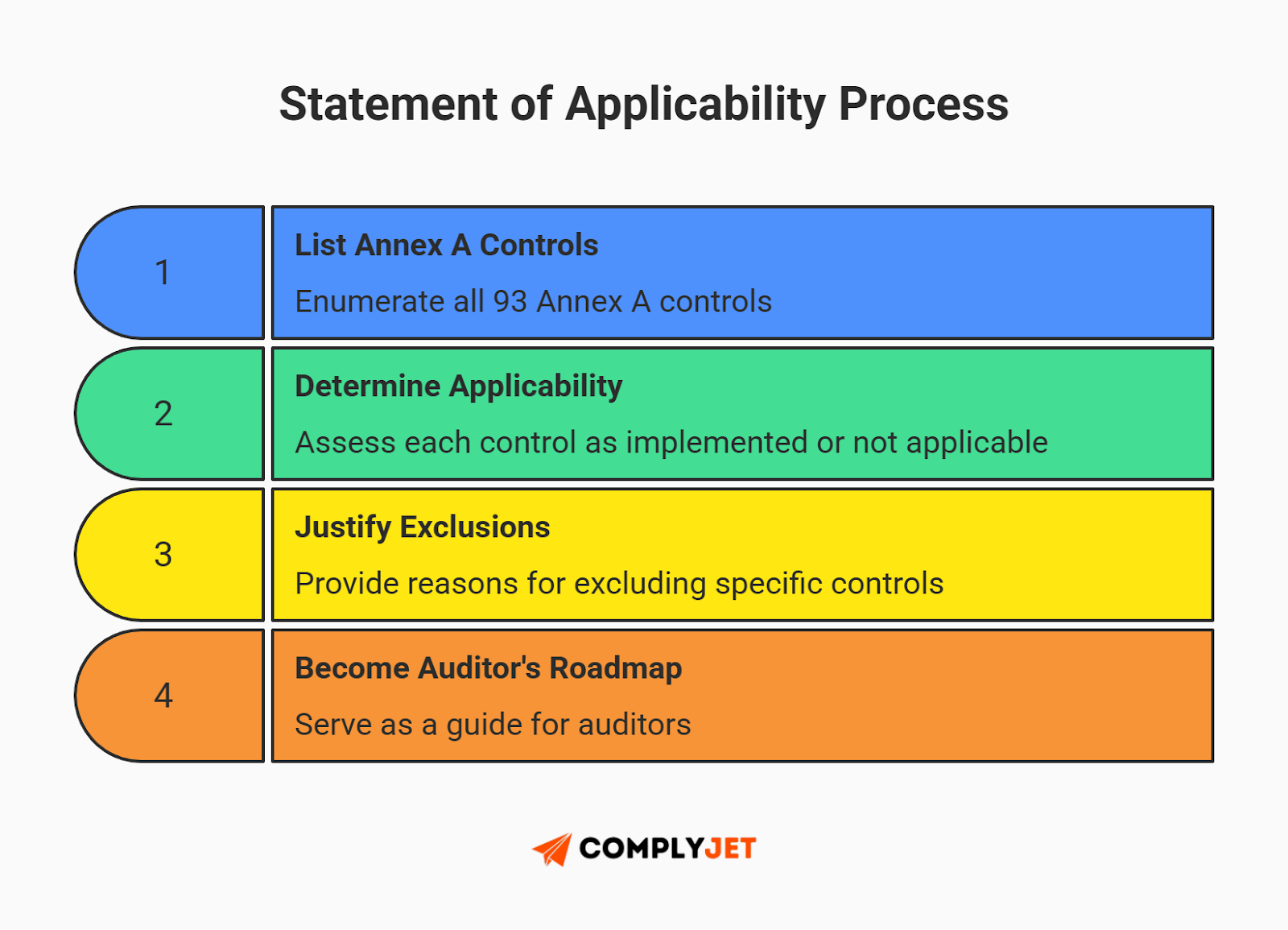
Pay attention here. If you only remember one thing from this ISO 27001 checklist, let it be the Statement of Applicability (SoA). The SoA is a master list of all 93 Annex A controls where you declare:
- "Yes, we do this."
- "No, we don't do this, and here is why."
Example: A fully remote SaaS company can exclude "Physical Delivery and Loading Docks" from their SoA. Your auditor will use your Statement of Applicability (SoA) as their roadmap. If it's not in the SoA, they (usually) won't check it.
Founder Tip: Do not write these from scratch. Writing a Statement of Applicability (SoA) manually in Word is a waste of 40 hours. Use templates or a compliance platform to generate the first draft, then customize it to your reality.
- The Risk Treatment Plan (RTP)
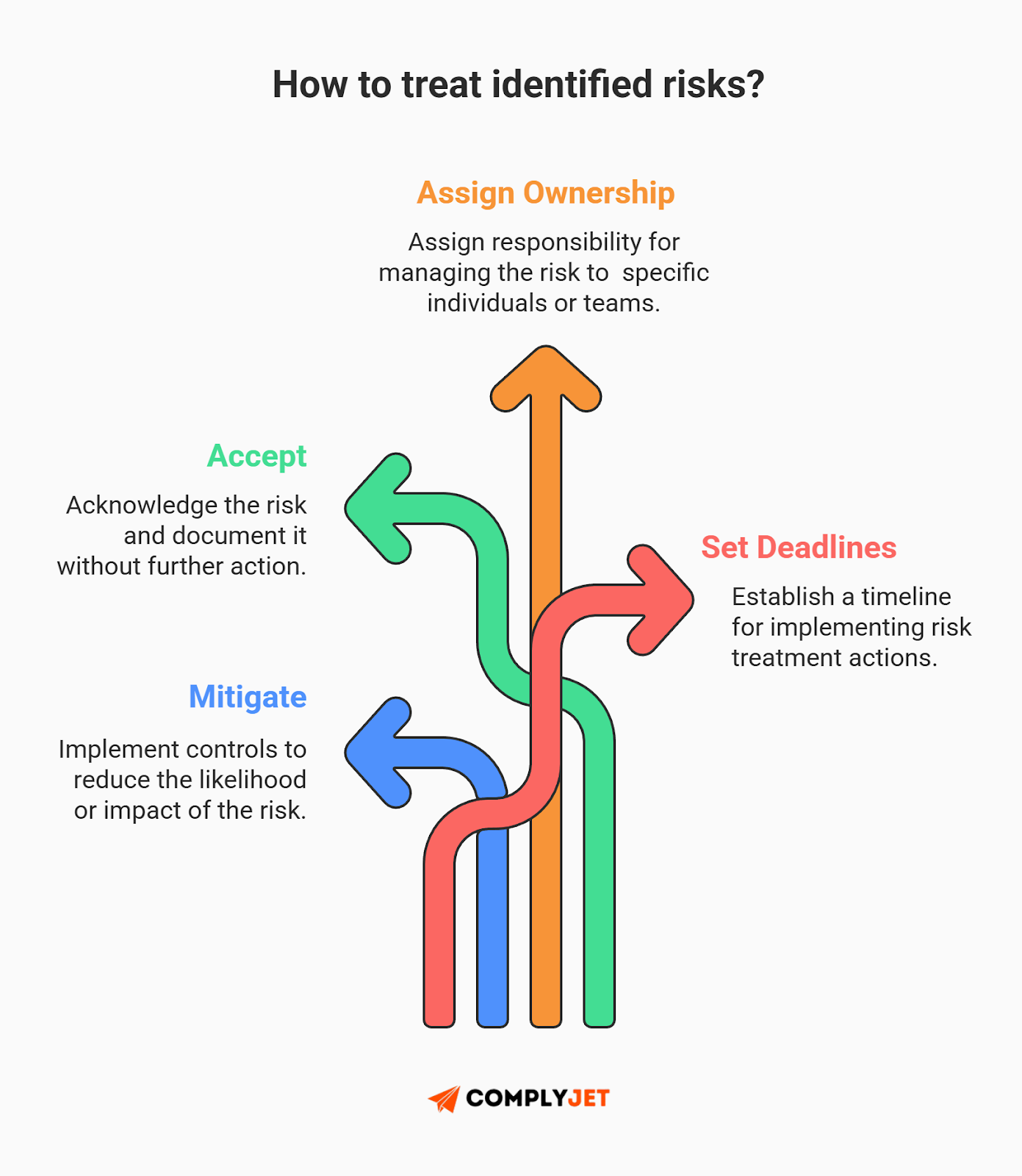
You identified your gaps in Phase 1. The RTP is your plan to fix them. It details who is responsible for each risk, what the deadline is, and whether you are "mitigating" it (fixing it) or "accepting" it (living with the risk).
The Supporting Documentation Stack
Beyond the Big Three, you will need specific policies to satisfy the remaining ISO 27001 requirements. A standard startup stack includes:
- Access Control Policy: Who gets access to AWS/GitHub?
- Asset Management Policy: Who owns the laptops?
- Supplier Security Policy: How do you vet 3rd party vendors?
- Incident Response Plan: What happens when (not if) you get hacked?
ISO 27001 vs. ISO 9001
A common mistake founders make is grabbing templates from their operations team. This doesn't work.
Unlike an ISO 9001 audit checklist which focuses on quality consistency and customer satisfaction, an ISO 27001 checklist is strictly focused on information security and risk management. An operational manual for a factory floor (ISO 9001) will not satisfy a cybersecurity auditor.
Phase 3: The Detailed Annex A ISO 27001 Checklist (All 93 Controls)
This is where the rubber meets the road.
In the old version of ISO 27001, controls were scattered across 14 confusing domains. The new ISO 27001 checklist simplifies this into 4 logical themes.
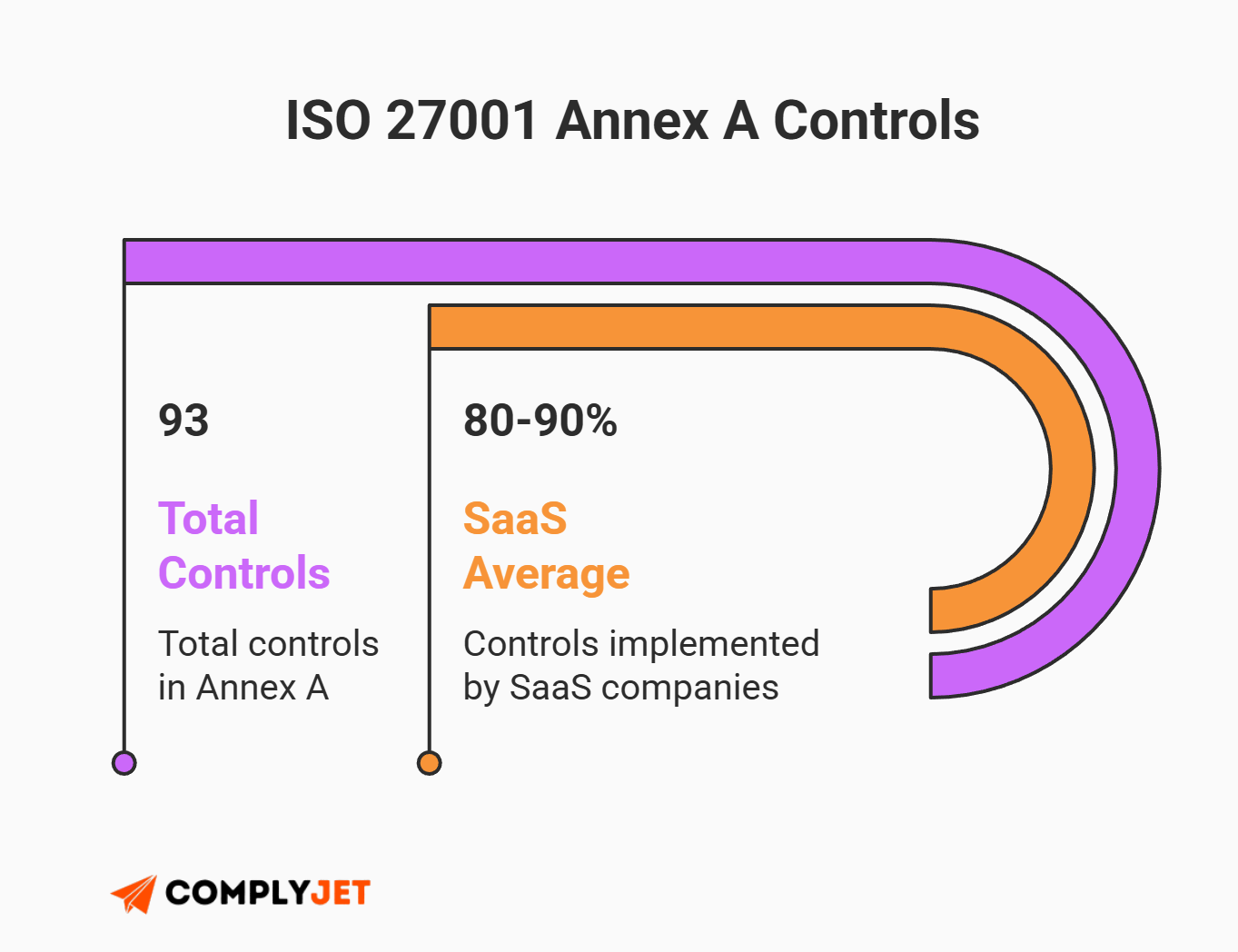
Remember: You do not need to implement all 93 controls. You only need to implement the ones you listed in your Statement of Applicability (SoA). However, for a standard SaaS company, you will likely need about 80-90% of them.
Here is a breakdown of the essential ISO 27001 controls.
Theme 1: People Controls (8 Controls)
Focus: Ensuring your employees aren't the weakest link.
- Screening (Background Checks): Do you background check employees before they touch production data? (You must).
- Terms and Conditions of Employment: Do your contracts explicitly state that employees must follow security rules?
- Awareness Training: This is a big one. You need proof (logs/certificates) that every employee has completed security training upon hiring and annually thereafter.
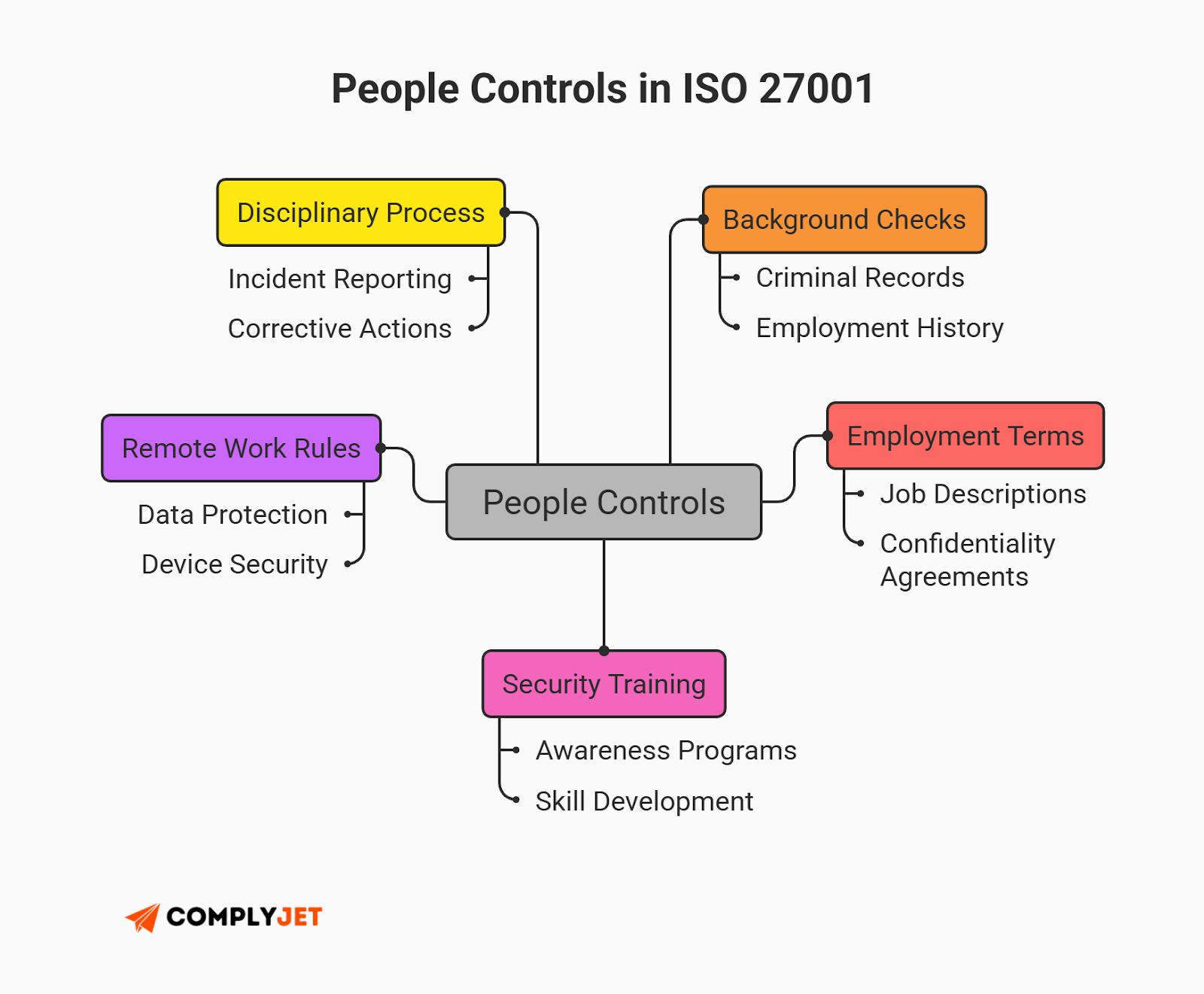
- Disciplinary Process: What happens if an employee ignores the rules? You need a documented process for this.
- Remote Working: If you are a remote-first startup, you need a policy governing how employees secure their home networks (e.g., "Don't work from an open cafe Wi-Fi without a VPN").
Theme 2: Organizational Controls (37 Controls)
Focus: The rules, policies, and management of the company.
- Policies for Information Security: The "Big Three" documents we mentioned in Phase 2 live here.
- Asset Management: You need an inventory of all hardware (laptops) and software (SaaS tools).
Founder Tip: You don't need a fancy tool. A well-maintained Excel sheet listing 'MacBook Pro - Serial #123 - Assigned to John Doe' is perfectly acceptable for your first audit.
- Access Control: Who can see what? You must follow the "Principle of Least Privilege." Marketing should not have admin access to the production database.
- Supplier Relationships: You are responsible for your vendors. If you use AWS or Slack, you need to review their security certificates (usually SOC 2 or ISO 27001 reports) annually.
- Cloud Services: Specifically for SaaS, you need rules for how you spin up and secure cloud instances (e.g., "No public S3 buckets").
Theme 3: Technological Controls (34 Controls)
Focus: The engineering and IT heavy lifting.
- Secure Authentication: Passwords are dead. You need Multi-Factor Authentication (MFA) enabled everywhere - Google Workspace, AWS, GitHub, etc. No exceptions.
- Access Rights: When someone leaves, do you cut their access immediately? You need a "leavers checklist" to prove this happens within 24 hours.
- Cryptography (Encryption): Data must be encrypted "at rest" (on the disk) and "in transit" (over the internet). For most modern startups, standard HTTPS (TLS 1.2+) and AWS/GCP default encryption satisfy this.
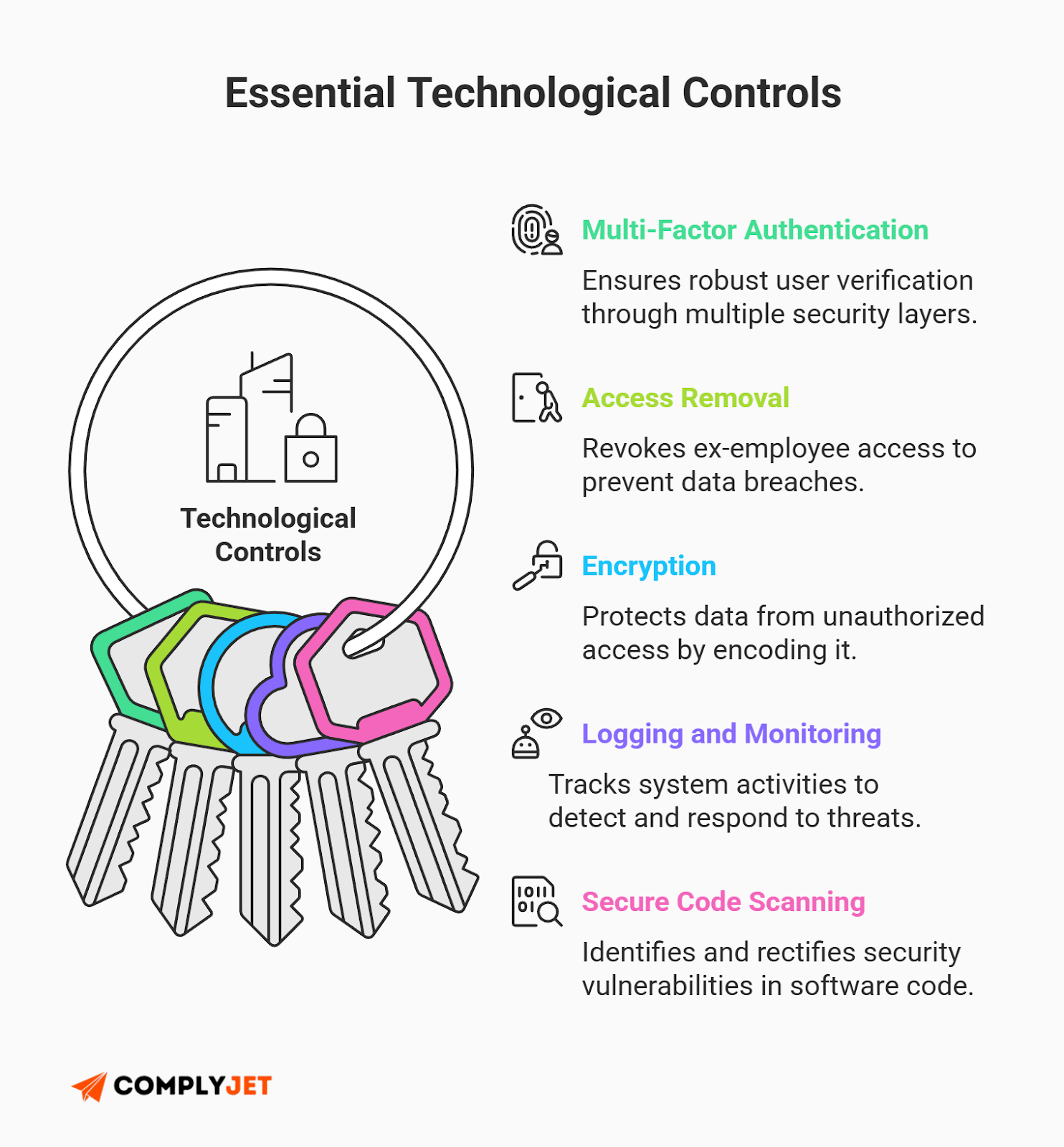
- Logging and Monitoring: Are you tracking who logs in? You need logs to detect suspicious activity.
- Secure Coding: If you build software, you need to scan your code for vulnerabilities (using tools like Snyk or Dependabot) before merging it.
Founder Tip: Do not get overwhelmed by the sheer volume of ISO 27001 controls. Group them. "Onboarding" covers screening, terms of employment, and access rights. "Engineering" covers secure coding, logging, and encryption. Tackle them in batches, not one by one.
Theme 4: Physical Controls (14 Controls)
Focus: Protecting the real-world stuff.
- Physical Security Perimeters: If you have an office, do you have a badge system or a lock on the server room door?
- Clear Desk and Clear Screen: Auditors love to walk around and check if people left passwords on sticky notes or left their screens unlocked while at lunch.
- Equipment Siting: Are your servers protected from environmental threats? (If you are 100% cloud, this is largely handled by your cloud provider's certifications, but you must note that in your SoA).
Stuck on a Control? Ask a Human. Automated platforms are great, but sometimes you just need an expert. Unlike other tools, ComplyJet doesn't just rely on chatbots. You get direct access to real compliance experts who are always on call to guide you through the tricky parts of Annex A. Book a demo with our founders to find out more.
Phase 4: The ISO 27001 Audit Phase
You have built the controls. You have written the policies. Now, it is time for the exam.
The ISO 27001 audit is not a one-day event. It is a multi-stage process designed to validate that your security isn't just paper-thin.
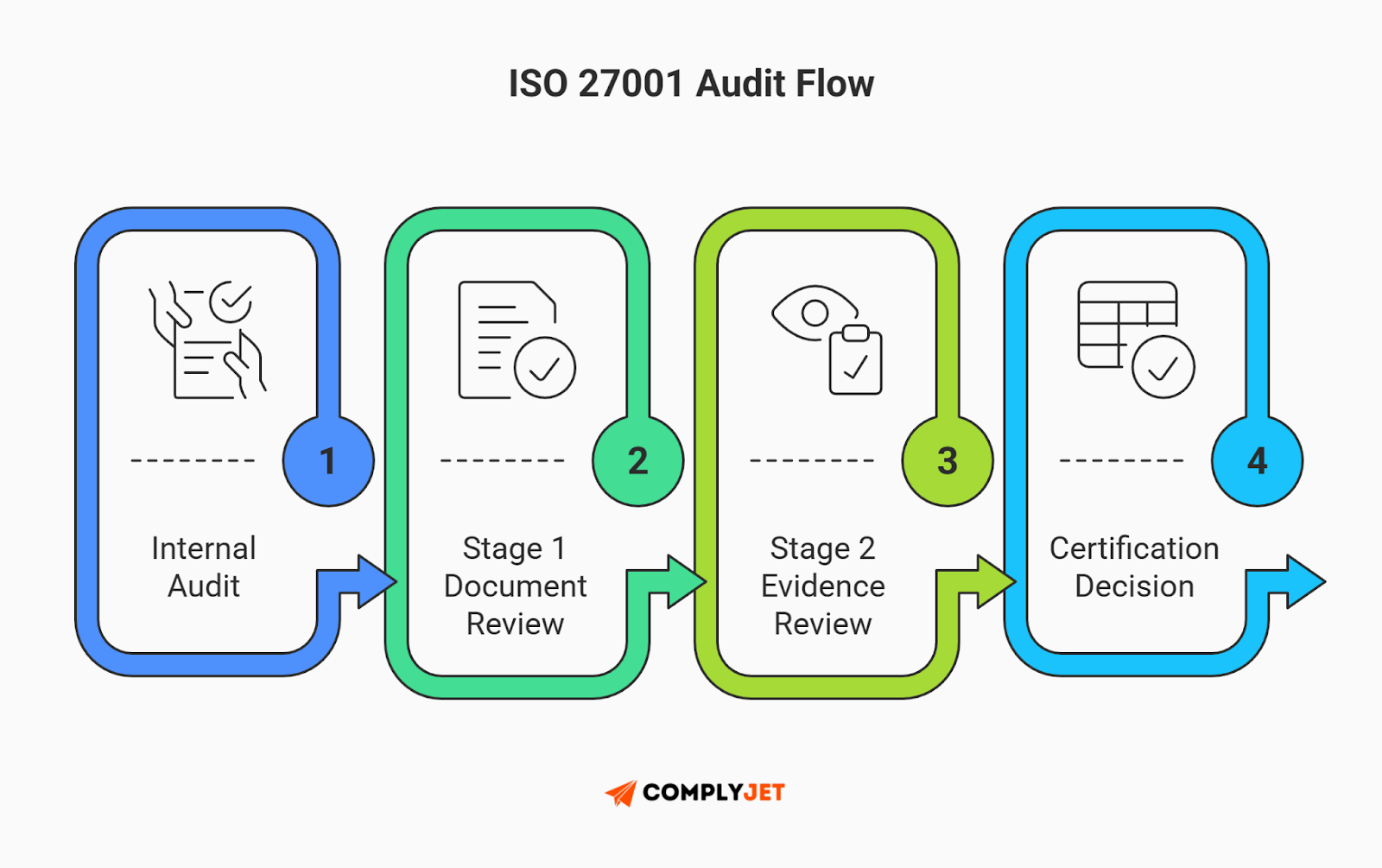
Step 1: The Internal Audit (The Rehearsal)
Before you invite an external certification body, you must conduct an internal ISO 27001 audit. This is a mandatory requirement (Clause 9.2).
You cannot do the audit yourself. You must either have an independent employee (who isn't in the security team) or hire a consultant to check your work. They will run through your entire ISO 27001 checklist to find gaps. If they find issues, fix them now. It is much cheaper to fail an internal audit than a real one.
Step 2: The Stage 1 Audit (Document Review)
This is the "Desktop Audit." The auditor will review your documentation to see if your design is sound.
They are checking for existence, not operation.
- Do you have a policy?
- Is the scope defined?
- Does the ISO 27001 checklist match the SoA?
If you pass Stage 1, they give you the green light for the main event. If you have "Areas of Concern," you usually have a few weeks to fix them before Stage 2.
Step 3: The Stage 2 Audit (Evidence Review)
This is the "Main Event." The auditor visits you (virtually or physically) to see if you actually follow your own rules.
This step is more evidence-based when compared to others in the ISO 27001 audit process.
- You said you onboard employees with a background check? "Show me the report for the last 3 hires."
- You said you review access logs? "Show me the ticket where you flagged a suspicious login last month."
Founder Tip: During the Stage 2 ISO 27001 audit, only answer exactly what is asked. Do not volunteer extra information. If they ask for "Evidence A," give them "Evidence A." Don't give them "Evidence A, B, and C," or you might accidentally open a new line of questioning you aren't prepared for.
If you pass Stage 2, congratulations. You are recommended for certification.
When an ISO 27001 Checklist Isn't Always Enough
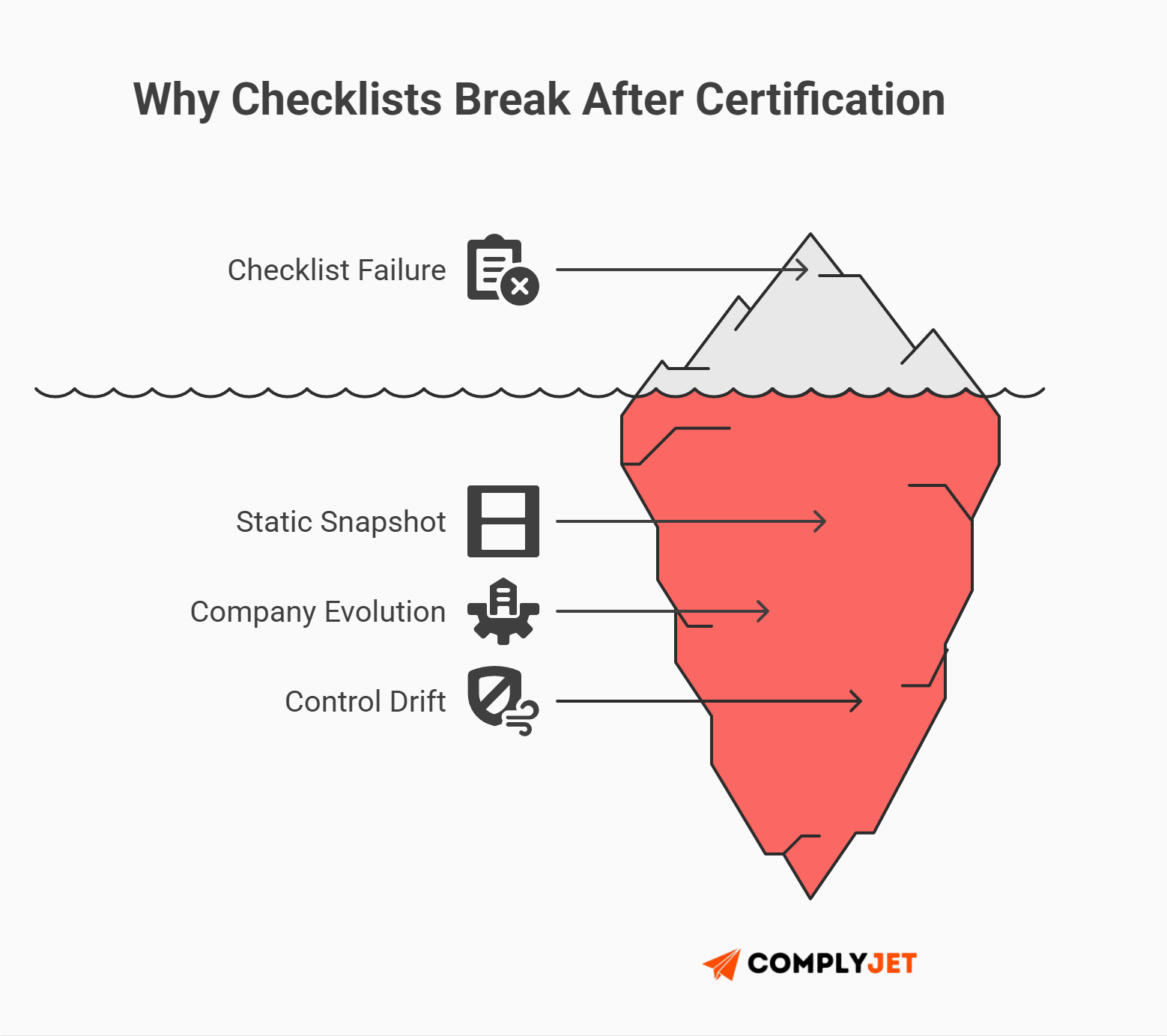
Here is the hard truth: An ISO 27001 checklist is static, but your company is dynamic.
You can download the perfect ISO 27001 checklist, fill out every row in Excel, and pass your audit on a Tuesday. But what happens on Wednesday?
- A developer spins up a new AWS instance without tagging it.
- HR hires a contractor but forgets to sign the NDA.
- An employee turns off MFA because it's "annoying."
Suddenly, your perfect ISO 27001 checklist is obsolete. You are no longer compliant, and you won't know it until the auditor returns next year to revoke your certificate.
The Problem with "Snapshot" Compliance
Relying solely on a manual ISO 27001 checklist creates a false sense of security. It treats security as a "one-and-done" project. But the ISO 27001 requirements demand continuous improvement (Clause 10.1).
Maintaining this manually means you are constantly chasing evidence. It turns your CTO into a part-time compliance officer, nagging the team for screenshots and logs just to keep the ISO 27001 checklist green. This is the hidden cost of the "spreadsheet method" - it burns expensive engineering hours on administrative grunt work.
The Automator's Advantage
This is why modern startups are moving away from static files and toward continuous compliance platforms like ComplyJet.
Instead of manually updating an ISO 27001 checklist every quarter, ComplyJet integrates with your tech stack (AWS, GitHub, Google Workspace, Jira) to monitor your controls 24/7.
- Did a laptop miss an update? ComplyJet flags it instantly.
- Did a user bypass 2FA? You get an alert before it becomes a non-conformity.
ComplyJet transforms your ISO 27001 checklist from a static document into a living, breathing dashboard. It automates ~80% of the evidence collection, ensuring that when the ISO 27001 audit rolls around, you aren't scrambling - you are already ready.
Founders' FAQs on ISO 27001 Checklists
Even with a perfect strategy, the path to certification is full of unknowns. Here are the honest answers to the questions most founders are too afraid to ask their auditors.
What happens if we fail the audit?
This is the number one fear, but it is largely unfounded. Auditors rarely "fail" a company outright. Instead, they issue "non-conformities."
To survive the audit, you need to ensure your ISO 27001 checklist execution is solid and understand the difference between a Major vs Minor non-conformity.
- Minor Non-Conformity: This is a small slip-up. Maybe one new hire missed a training session, or a single laptop wasn't patched on time. It is an isolated incident. The auditor will still issue your certificate, provided you submit a plan to fix it.
- Major Non-Conformity: This is a total breakdown of a process. If you have no evidence of security training for anyone, or if you completely ignored items on your mandatory ISO 27001 checklist or requirements, that would be considered a major non-conformity issue.
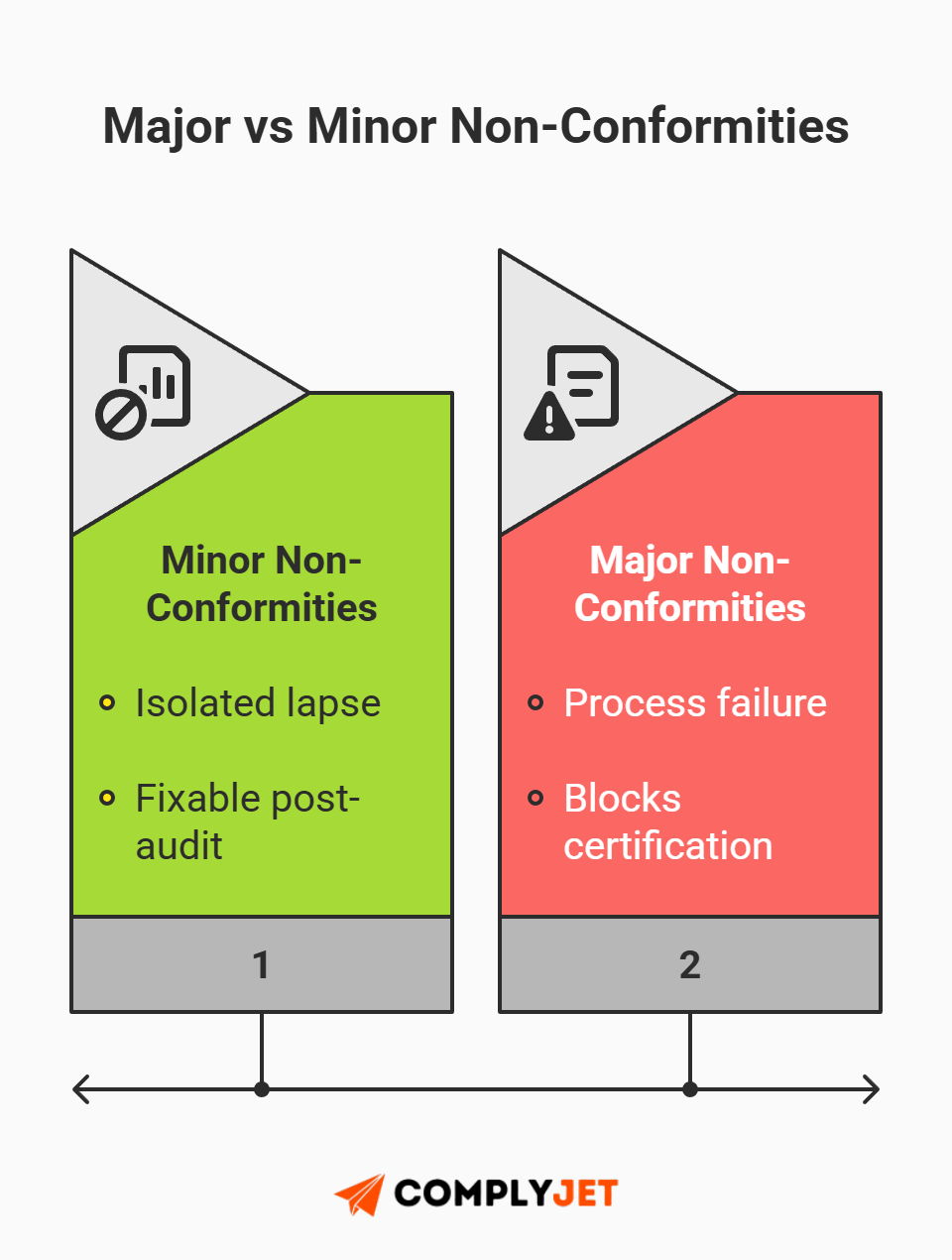
A Major vs Minor non-conformity distinction is critical because a "Major" stops certification until the issue is resolved. Your goal isn't 100% perfection; it is to avoid the systemic negligence that triggers a Major vs Minor non-conformity conversation.
How much does ISO 27001 actually cost?
The cost varies wildly depending on your approach.
- The DIY Route: Free (monetarily), but it will cost you 400+ hours of founder time to decipher the ISO 27001 checklist and write policies.
- The Consultant Route: ~$20k - $40k. They do the heavy lifting, but it is slow and expensive.
- The Hybrid/Platform Route: This is usually the sweet spot for startups. Using a platform like ComplyJet to automate your ISO 27001 checklist typically costs 30-50% less than traditional consulting while moving twice as fast.
No Hidden Fees. We believe in complete transparency. Check out our Pricing hub to see our clear pricing models and pick a plan fit for your needs.
Is this a one-time thing?
No. This is a common misconception. ISO 27001 is normally a 3-year cycle.
- Year 1: Initial Certification Audit (The big one).
- Year 2 & 3: Surveillance Audits (Smaller "check-up" audits).
- Year 4: Recertification (The big one again).
If you treat your ISO 27001 checklist as a one-time homework assignment, you will fail the surveillance audit in Year 2. You must build processes that stick.
The Final Takeaway
Getting certified is a significant milestone. It signals to the market that you have matured from a risky startup into a trustworthy enterprise. But as you may have noticed, maintaining a manual ISO 27001 checklist is a heavy lift.
Between navigating the complex ISO 27001 requirements, defining your scope, and preparing for the ISO 27001 audit, it is easy for founders to lose focus on what they do best: building the product.
The goal of this guide was to demystify the new ISO 27001 2022 checklist standards and give you a fighting chance. However, knowing what to do is only half the battle. Doing it consistently is where most companies struggle.
Why stay in "Spreadsheet Hell"? You don't track your sales pipeline on a napkin, so why manage your security posture on a static spreadsheet?
ComplyJet transforms your static ISO 27001 checklist into an automated security engine. We integrate with your existing tools - AWS, GitHub, Slack, and HRIS - to automatically collect evidence, monitor your ISO 27001 controls, and flag risks in real-time.
Don't just check the box. Own the process.
We at ComplyJet know the struggle. You want to close the deal, not drown in paperwork or pay a "brand tax" just to get certified. ComplyJet was created with one goal: to give young founders the same enterprise-grade ISO 27001 power as the giants - at a fraction of the price. We are leveling the playing field so you can focus on building, not just complying. Book a demo with our founders to learn more.



