When you first chase enterprise deals, you hit a wall every time a prospect asks for a current SOC 2 report. It doesn’t matter if your product is the best. You’ll end up watching a potential million‑dollar contract stall while you scramble for something that makes you credible.
This is why in 2025, we treat SOC 2 compliance as our front‑door key to closing serious deals. Without it, your pitch stops before the demo even starts, and your customer’s procurement team files your answers in a drawer they rarely revisit.
In this guide, you will find everything you need to know about SOC 2, including the checklist, audit processes, certification steps, audit time, and associated costs.
What is SOC 2 Compliance?
SOC 2 stands for System and Organization Controls 2, and it assesses how we secure data, keep systems available, process information accurately, safeguard confidentiality, and respect privacy, all in accordance with the AICPA’s Trust Services Criteria.
When you show a SOC 2 compliance certification, you prove to any security team that you’ve built controls around potential risks, which ultimately signals trust.
SOC 1 focuses on controls related to financial reporting. If you manage payroll, accounting systems, or general ledger data, SOC 1 is the right fit.
SOC 3 offers a public-facing seal of trust but skips the detailed audit report. It is useful for marketing but not for deep due diligence.
SOC 2 is what you aim for when you handle customer data. It gives your buyers the credible, detailed audit report they need to assess risk and move quickly.
You pursue SOC 2 to earn trust before the first sales call even starts.
Handing over a qualified SOC 2 report signals that you understand the same security challenges your customers face, that you've built systems to meet those standards, and that you’re prepared to safeguard their data long after the contract is signed. There are frameworks in place to guide the SOC 2 regulations, which we will discuss further.
SOC 2 Compliance Regulations (SSAE 18 & TSC)
SOC 2 sits on a structure shaped by the AICPA (American Institute of Certified Public Accountants) and formalized through the SSAE 18 attestation standards, which define how service organizations should document and validate their internal controls.
If you’re building a product that handles sensitive or regulated data, understanding this framework helps you align operations with what auditors, procurement teams, and enterprise CISOs expect.
The AICPA’s Statement on Standards for Attestation Engagements No. 18 (SSAE 18) replaced older frameworks like SSAE 16 and introduced stricter rules on third-party vendor oversight and risk assessment practices.
A SOC 2 audit performed under SSAE 18,
- Asks whether your controls exist
- Checks if they operate effectively over time
- Verifies whether you’re accountable for outsourced dependencies.
The AICPA does not prescribe specific technologies. Instead, it requires that your controls meet the Trust Services Criteria, a set of five control domains derived from the COSO internal control framework and tailored for technology environments.
These criteria are not all required. Security is mandatory for every SOC 2 audit, but the other four are scoped in based on your product and customer expectations.
Each criterion is supported by Points of Focus, which help you interpret the abstract control requirements and translate them into specific operational practices relevant to your business.
When you write your system description and design controls, these points of focus guide your auditors in evaluating whether your systems meet the expected standard across technical, procedural, and organizational dimensions.
That’s the structure you operate in.
Trust Services Criteria (TSC): The 5 Pillars of SOC 2 Security
The foundation of SOC 2 rests on the Trust Services Criteria (TSC), which we discussed earlier: Security, Availability, Processing Integrity, Confidentiality, and Privacy.
You must implement and document controls that address relevant criteria. These controls need to be appropriate for your system, your customers, and the data you manage. Understanding each one of it lets you scope your controls with intention instead of blindly over-engineering them.
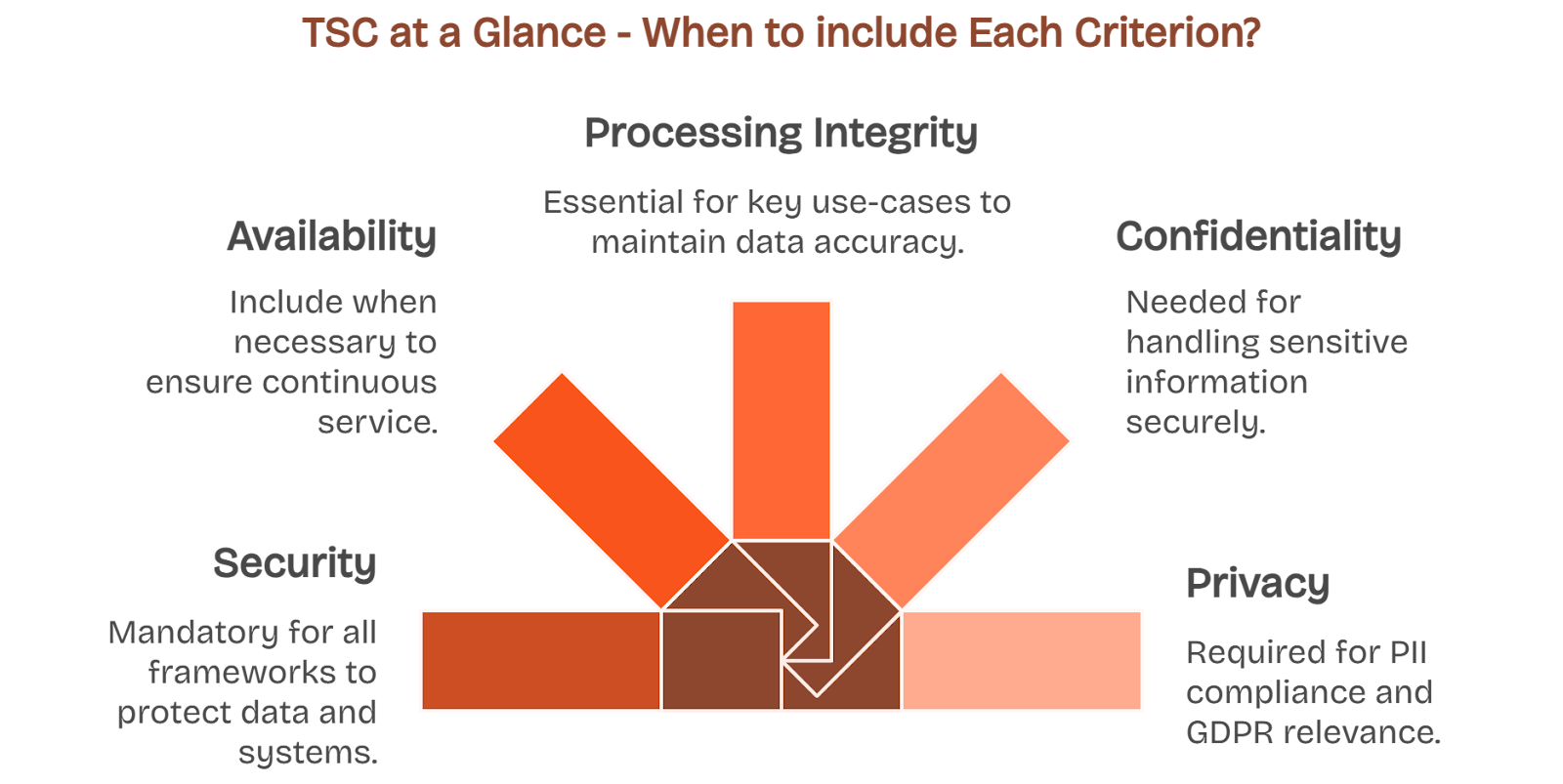
We begin with the Security trust service criteria. It is a required criterion. It covers protection against unauthorized access, data loss, and misuse across both physical and digital layers.
You need to show access control, authentication, intrusion monitoring, vulnerability management, incident response, and audit logging across your systems.
Availability applies when customers depend on uptime or service-level agreements. It focuses on disaster recovery, backups, and infrastructure resilience.
If your product runs with performance guarantees, expect to show recovery plans, failover tests, and capacity planning.
Processing Integrity matters if your system performs business-critical operations. The goal is to confirm that it processes data correctly and completely.
This includes validation, error detection, and reconciliation for systems like billing, transactions, or automation flows.
Confidentiality applies when you handle non-public business data, like trade secrets or internal documentation. It requires encryption, role-based access, and data classification protocols.
Privacy is essential if you store or process personal data, especially under laws like GDPR or CCPA. You’ll need to show consent management, data access controls, and deletion workflows, especially for GDPR or CCPA compliance.
Understanding these control expectations sets the foundation for everything else. Next, we’ll translate them into a practical checklist that drives your SOC 2 implementation forward.
Also read: SOC 2 Compliance Requirements: End-to-End Guide
How to get SOC 2 Compliant?
Getting SOC 2 compliant is a structured process. You’re not guessing what comes next. You’re following a set of repeatable steps that move you from planning to audit. We’ve laid out a basic practical SOC 2 compliance checklist to help you scope your effort, reduce rework, and collect evidence that aligns with what auditors expect.
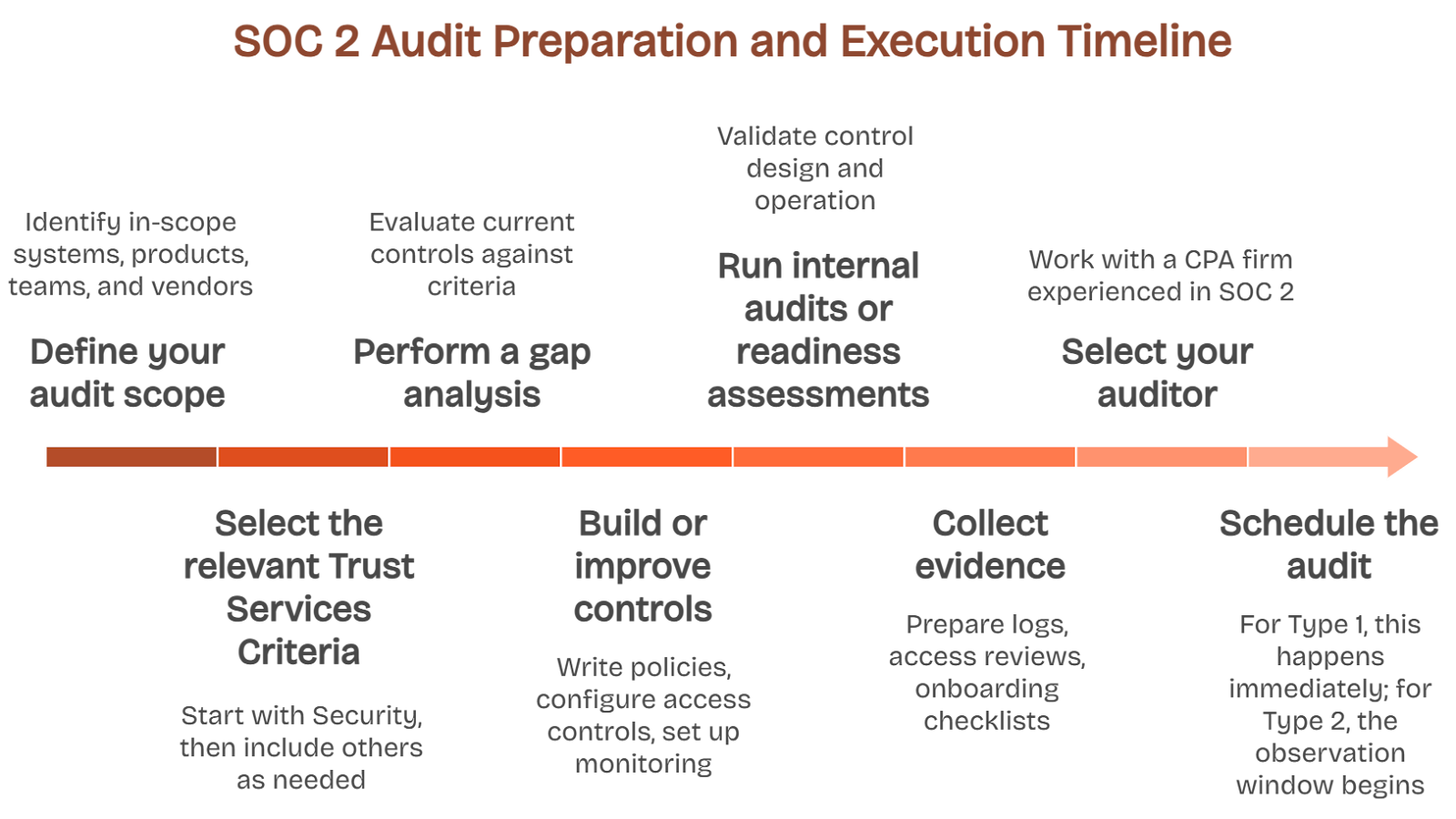
Here’s the basic sequence we recommend:
Define your audit scope: Identify in-scope systems, products, teams, and vendors. Anchor your scope in what your customers care about and where data is stored or processed.
Select the relevant Trust Services Criteria: Start with Security, then include Availability, Processing Integrity, Confidentiality, or Privacy based on your product and customer obligations.
Perform a gap analysis: Evaluate your current controls and policies against the criteria. Identify what’s missing, inconsistent, or undocumented.
Build or improve controls: Write policies, configure access controls, set up monitoring, and automate evidence collection where possible to save time during the audit window.
Run internal audits or readiness assessments: Validate control design and operation before your external auditor steps in. This lowers your risk of findings during the actual audit.
Collect evidence: Prepare logs, access reviews, onboarding checklists, incident response records, and anything else that proves consistent control execution.
Select your auditor: Work with a CPA firm experienced in SOC 2 and your industry. Engage early so they understand your system design and audit expectations.
Schedule the audit: For Type 1, this happens immediately. For Type 2, the observation window begins now. Stay disciplined about control execution across the window.
A well-scoped checklist keeps your team aligned and your systems consistent.
Download our Ultimate 10-Step Checklist that will guide you the way!
Understanding the TSC lets you scope your audit with precision, build relevant controls, and prepare for what auditors actually look for.
Next, we’ll focus on types of SOC 2 reports that match your business needs.
SOC 2 Type 1 vs Type 2: What’s the difference?
Once you commit to SOC 2, the next decision is whether to go with a SOC 2 Type 1 or a SOC 2 Type 2 report. This choice affects how your customers perceive your readiness and how long the audit takes.
The difference isn’t about how serious you are, it’s about what you can prove right now and what your buyers need to see to move forward. This shapes the timing of your compliance journey and your go-to-market plan.
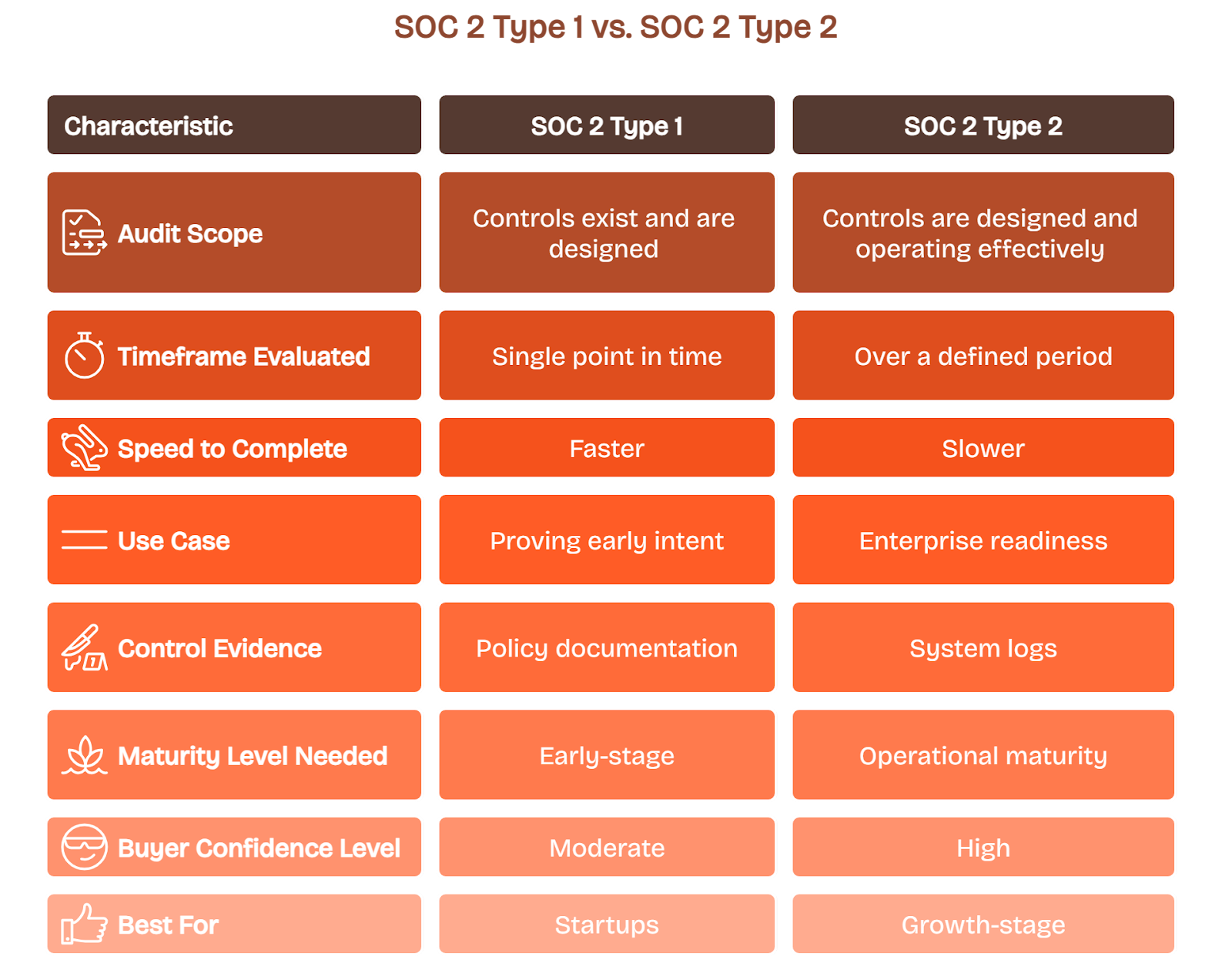
A SOC 2 Type 1 report looks at your controls at a single point in time. It answers whether the controls you’ve designed actually exist and are properly documented.
It’s useful when you’re early in your security maturity curve, need something fast to show intent, and want a short audit window to get a report in hand.
Type 1 is faster and lighter, but it won’t give buyers confidence that your controls actually work over time. It only shows how your systems look on one day.
A SOC 2 Type 2 report goes deeper. It evaluates not just the design but the operating effectiveness of your controls over a sustained period, usually three to twelve months.
When customers ask for SOC 2 Type 2 certification, they’re expecting proof that your security, availability, or privacy controls hold up under real operating conditions. It reflects operational maturity and shows your controls hold up under real conditions.
This means you’ll need policies in place, logs that show consistent execution, and audit trails across change management, access reviews, incident response, and vendor oversight.
If your goal is to close enterprise contracts, Type 2 gives you the credibility to do that. It’s what security teams expect when trust is tied to revenue.
Here’s how to decide:
- Choose Type 1 if you're building trust fast, preparing for fundraising, or need short-term proof during early-stage growth.
- Choose Type 2 if you're closing enterprise deals, handling customer data at scale, or responding to security questionnaires from mid-market and large buyers.
Understanding this distinction helps you scope your first audit properly and align expectations internally and externally. Next, we’ll walk you through the structure of a SOC 2 report.
Read: SOC 2 Type 1 vs Type 2: Detailed Comparison
What is a SOC 2 report? | SOC 2 Report Structure
If someone asks, “What is a SOC 2 report?” they’re usually trying to understand whether it’s something they can show to customers or rely on during procurement.
A SOC 2 report is a formal attestation document, issued by a licensed CPA firm, that confirms how your controls align with the selected Trust Services Criteria.
The report has five standard sections, and each one serves a different audience, from engineers to auditors to legal and procurement stakeholders.
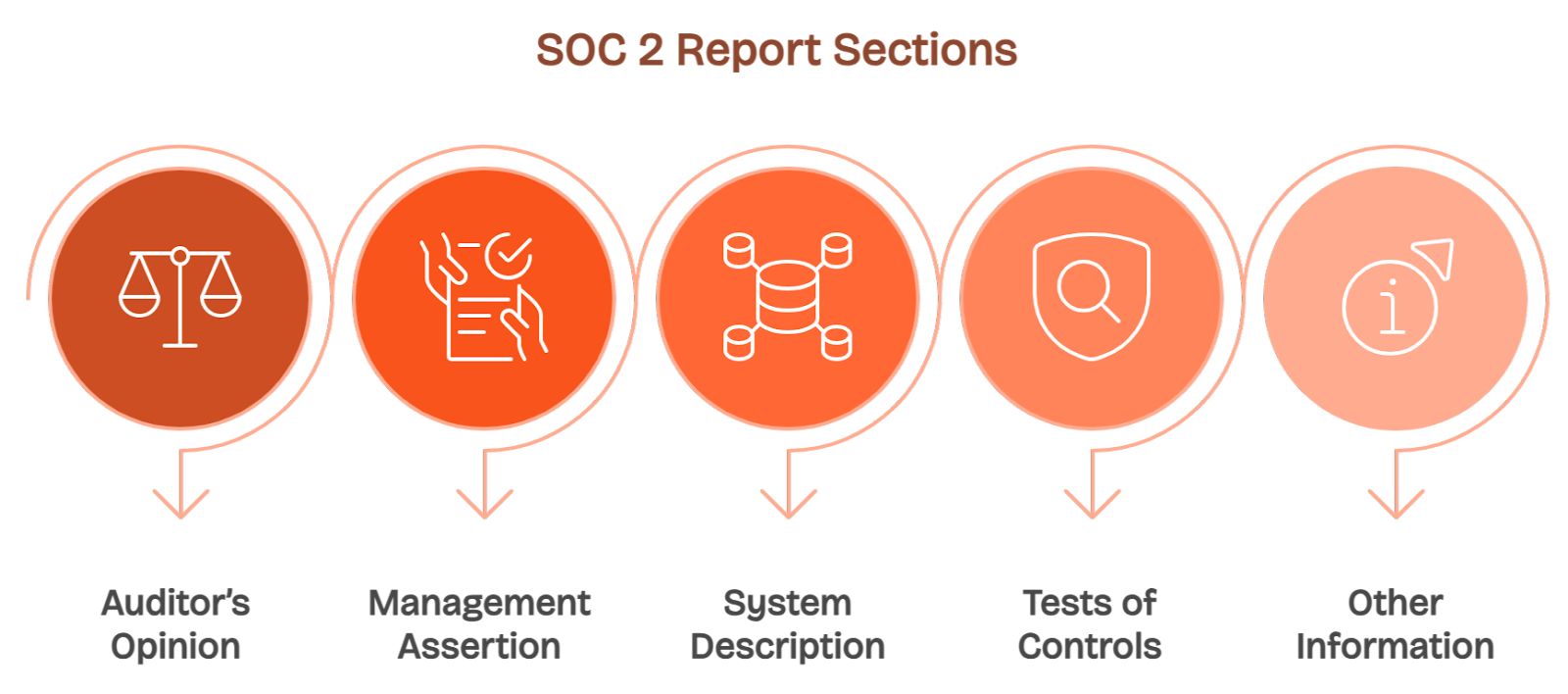
Section I contains the Independent Auditor’s Opinion. This states whether your controls were fairly described and operated effectively during the audit period.
Section II is the Management Assertion, where you affirm that the system was designed and operated according to the documented policies. You sign and date this statement.
Section III includes your System Description, which outlines architecture, control environment, and operational boundaries. This is where auditors understand the context behind your implementation.
Section IV details the Tests of Controls, including auditor procedures and whether each control passed or failed. This section is the most scrutinized during vendor reviews.
Section V lists Other Information, including subservice providers, carve-outs, or complementary user entity controls that your customers are expected to implement.
Take a look at this Sample SOC 2 Report to get an idea of what your report would look like.

Understanding the structure helps you prepare materials properly, communicate with buyers clearly, and use the report as a lever during security reviews. Next, we’ll walk through the SOC 2 audit process so you know exactly what to expect during the engagement.
SOC 2 Audit: How long does it take?
The SOC 2 audit process in 2025 still follows the core audit framework, but expectations around automation, documentation, and evidence have increased across the board.
When you map out your SOC 2 audit timeline, make sure to ensure transparency, avoid delays, and keep customer trust intact through every phase.
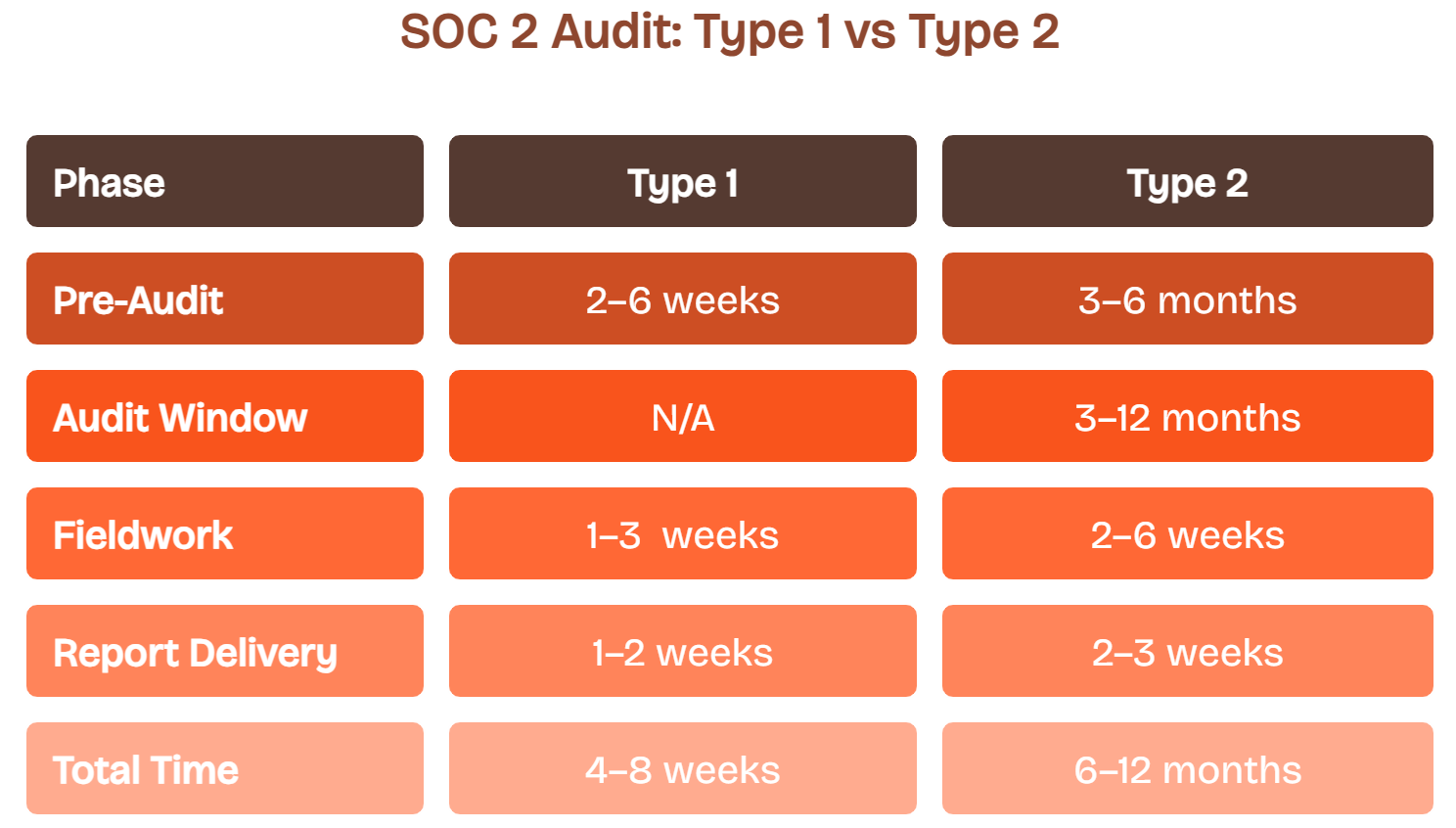
SOC 2 Type 1 spans four to eight weeks, and SOC 2 Type 2 runs six to fifteen months, depending on scope, complexity, and readiness as depicted here.
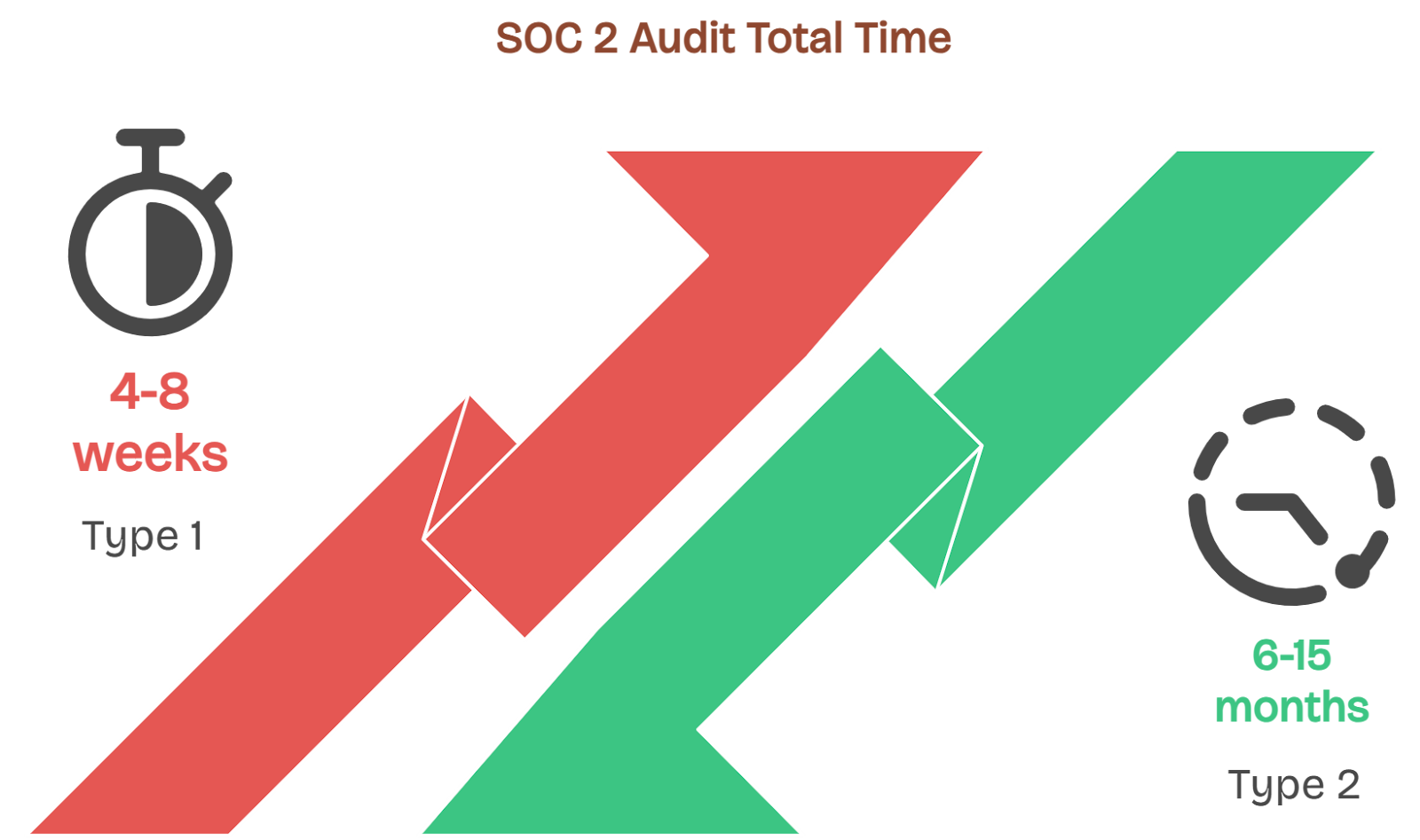
Pre-audit spans from two to nine months and covers:
- Gap analysis and scoping of Trust Services Criteria
- Control implementation, training, and process updates
- Documentation, readiness assessments, and evidence compilation
For Type 2, you maintain controls for three to twelve months while collecting evidence continuously. Audit fieldwork and interviews then run for two to six weeks.
Report generation follows over two to five weeks with:
- Draft report preparation by auditors
- Management review, assertion letter, and representation
- Final report issuance and delivery of the signed report
Next, we’ll explore how these phases translate into budgeting your SOC 2 compliance cost and allocating resources effectively.
How Much Does SOC 2 Compliance Cost?
Understanding the full SOC 2 compliance cost helps you set expectations early and prevents budget surprises when you get deeper into audit readiness or fieldwork.
You’ll face both direct expenses like auditor fees and software licenses, and indirect costs like internal effort, missed feature deadlines, and opportunity cost from resource shifts.
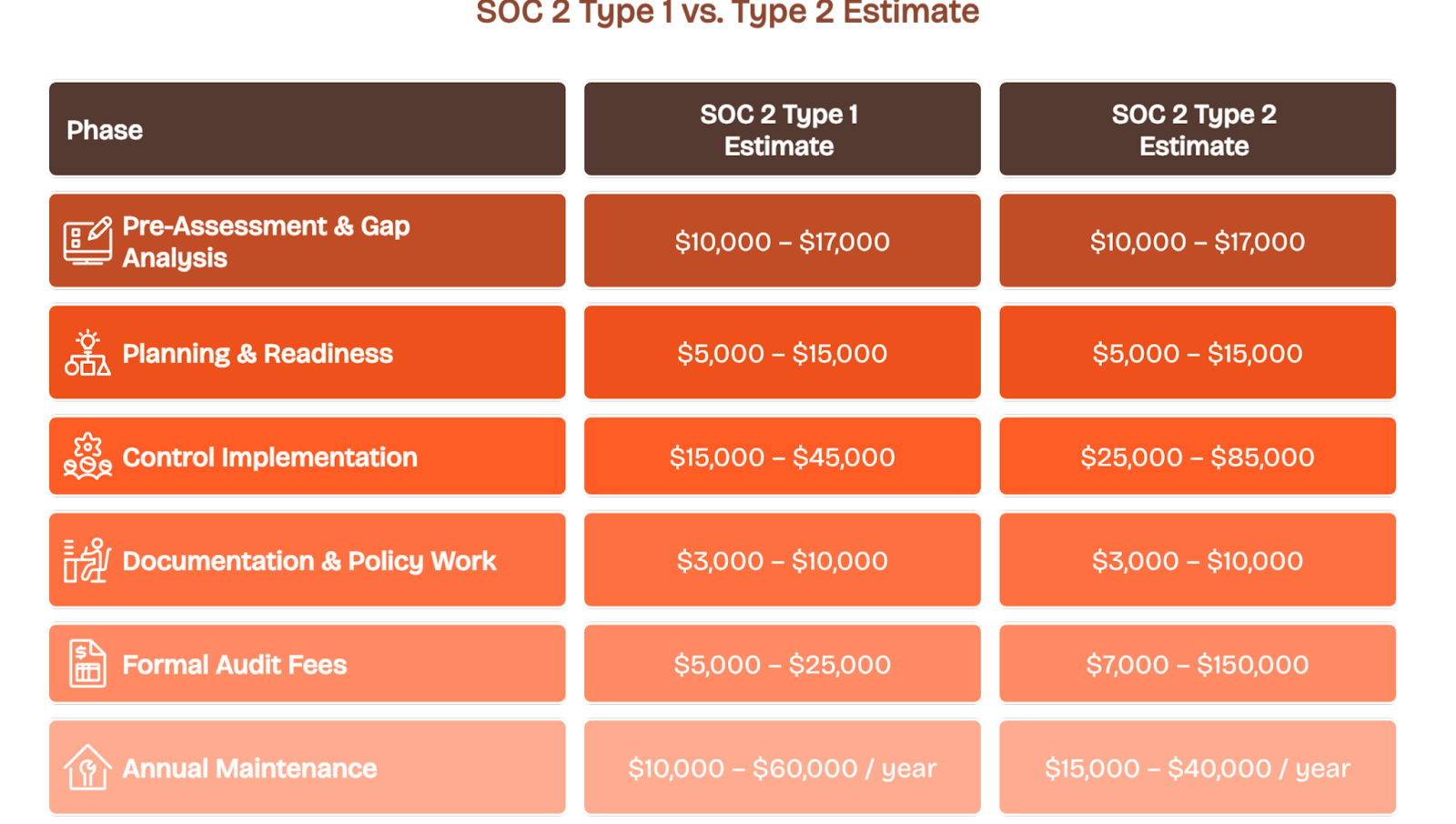
Direct Costs
Type 1 audits generally range from $10,000 to $25,000, while Type 2 audits cost between $20,000 and $60,000, depending on scope and complexity.
Readiness assessments, policy development, and evidence remediation may add $5,000 to $20,00,0, depending on your baseline maturity.
Automation platforms charge $5,000 to $25,000 per year, based on your headcount and infrastructure.
Indirect Costs
Most small teams underestimate the internal time burden. You’ll need engineers, security, HR, and legal to pitch in for evidence, fixes, and process validation.
Downtime from shifting focus can delay product delivery, trigger customer escalations, or limit bandwidth for roadmap priorities.
Opportunity costs arise when early sales cycles stall due to audit timelines that push buyer confidence back by weeks or months.
Here’s the approximate cost breakdown for each phase of the SOC 2 audit:
Budgeting Tips
For early-stage startups, start lean with Type 1 and grow into Type 2 as sales cycles mature.
Use automation software to minimize overhead, but assign a dedicated internal lead who owns policy alignment and stakeholder coordination.
Plan for ongoing cost, not a one-time event. Budget annual evidence upkeep, security reviews, and continuous monitoring to avoid lapses between audits.
Next, we’ll look at the best practices that can make this process smooth.
Best Practices and Considerations for SOC 2 Compliance
Once you're certified, your focus shifts to maintaining compliance without disrupting your product roadmap or draining internal resources year after year.
Continuous monitoring reduces audit fatigue, avoids evidence scrambles, and helps you detect drift before it becomes a control failure or audit exception.
Leverage Automation Thoughtfully
Automate wherever repeatability matters: access reviews, employee offboarding, log retention, and vendor risk checks.
Use APIs to integrate control evidence directly from systems like AWS, Okta, and GitHub.
Tailor Scope to Business Needs
Avoid over-scoping to “play it safe.”
Maintain a focused approach and align with your product's functionality and customer expectations in security reviews.
Map to AICPA Points of Focus
Use the AICPA’s Points of Focus as a checklist for what auditors will ask.
These sub-criteria clarify control intent and help you avoid subjective interpretation during fieldwork.
Simplify Annual Renewals
Build a continuous compliance pipeline: daily checks, automated alerts, and documentation updates tied to control changes.
This prevents year-end surprises and reduces the total cost of recertification.
Next, we’ll see how to choose the right SOC 2 compliance software to streamline control monitoring and reduce prep time before every renewal.
SOC 2 Compliance Software and Automation Tools
As your systems grow and audits become recurring, SOC 2 compliance software shifts from nice-to-have to essential for staying organized, audit-ready, and efficient.
Without automation, you’re chasing screenshots, documenting policies in silos, and manually recreating evidence across tools every year, which introduces drift and burns engineering hours.
Recommended Platforms
Complyjet is an AI-driven compliance automation platform for early-stage startups.
Vanta focuses on early-stage companies with templates and UI-first workflows.
Drata offers deeper integrations and workflows designed for technical teams.
Read: Top 15 Vanta Competitors & Alternatives in 2025: Complete Comparison Guide
Automation Benefits
These platforms connect to your cloud stack, HRIS, version control, and identity provider to automatically collect, timestamp, and organize audit-ready evidence.
You get visibility into control health, alerts on failures, and dashboards that show real-time readiness instead of scrambling at year-end.
They help enforce continuous compliance by flagging access anomalies, expired training, or outdated policies before they become audit blockers.
With the right tool in place, your audit stops being a fire drill and becomes a routine system check.
Here are the real-time SOC 2 Readiness and Evidence dashboards of ComplyJet:
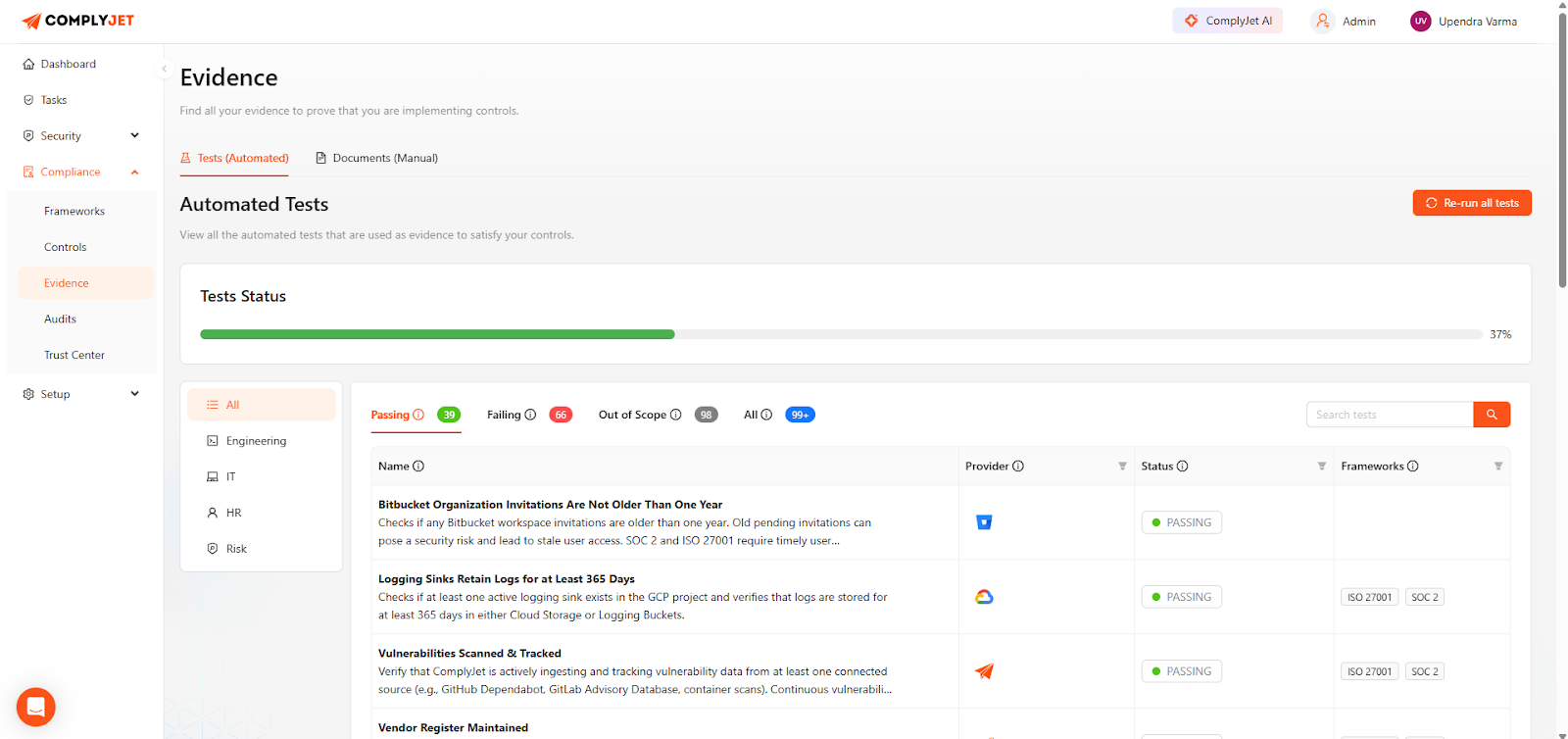
FAQs on SOC 2 Compliance
If you're new to SOC 2 or fielding buyer security questionnaires, a few key questions come up repeatedly. These answers will help you get aligned faster.
What is SOC 2?
SOC 2 is a security compliance framework developed by AICPA that evaluates how well your systems protect customer data based on predefined trust criteria. It focuses on controls around security, availability, processing integrity, confidentiality, and privacy. Your SOC 2 report, issued by a licensed CPA firm, provides external proof of these controls to your customers or partners.
Who needs SOC 2 compliance?
If you process or store customer data in the cloud, SOC 2 likely applies. SaaS providers, API platforms, infrastructure tools, and B2B services handling sensitive or regulated data need it to win trust and move deals forward. Buyers use SOC 2 reports to assess your security readiness during procurement or vendor due diligence.
What does SOC 2 compliance mean for businesses?
SOC 2 signals that your organization has formal controls, policies, and technical safeguards in place to protect customer data. It also shows you can provide audit evidence that those controls operate consistently over time. SOC 2 compliance becomes essential as you scale into mid-market or enterprise sales cycles.
What is the difference between SOC 1 and SOC 2?
SOC 1 focuses on internal controls relevant to financial reporting. It applies to payroll processors, accounting platforms, and financial service providers. SOC 2 is broader and covers operational controls related to security and data protection, making it more relevant for most SaaS and tech platforms.
Read: SOC 2 Type 1 vs Type 2: Detailed Comparison
What is a bridge letter for SOC 2?
A bridge letter fills the gap between the end date of your last SOC 2 report and the date of your next one. It’s usually a short document from your auditor or internal team confirming that no material changes occurred in your control environment during that gap.
Procurement teams may request it during active security reviews or renewals.
Is the SOC 2 audit easy to understand?
The core concepts are straightforward once mapped to your systems and processes. What makes it complex is coordinating evidence across departments, maintaining consistency, and preparing for auditor questions. With the right readiness tools and documentation in place, the audit itself becomes structured and predictable.
That’s where ComplyJet comes into play as a way to simplify readiness, streamline coordination, and reduce manual effort. ComplyJet offers 100+ integrations with 3+ frameworks for an unbelievable price.
ComplyJet is one of the few platforms that also offers a free trial to make an informed decision.
Start your FREE TRIAL now!
Conclusion
SOC 2 is now a baseline for trust. It shortens sales cycles, reduces buyer friction, and signals operational maturity to both customers and investors.
In 2025, security reviews start early. Your SOC 2 report lets you control the narrative before procurement asks for proof.
Compliance also aligns internal teams around shared practices and audit readiness, which becomes critical as you grow into larger markets or regulated industries.
SOC 2 sets you up for future frameworks like ISO 27001 or HIPAA without rebuilding from scratch.
To stay ahead, treat compliance as continuous. Automate reviews, track control health, and build systems that scale.
Start now. Scope your audit, choose a reliable partner, and avoid the cost of delay in every deal you postpone.
.png)


