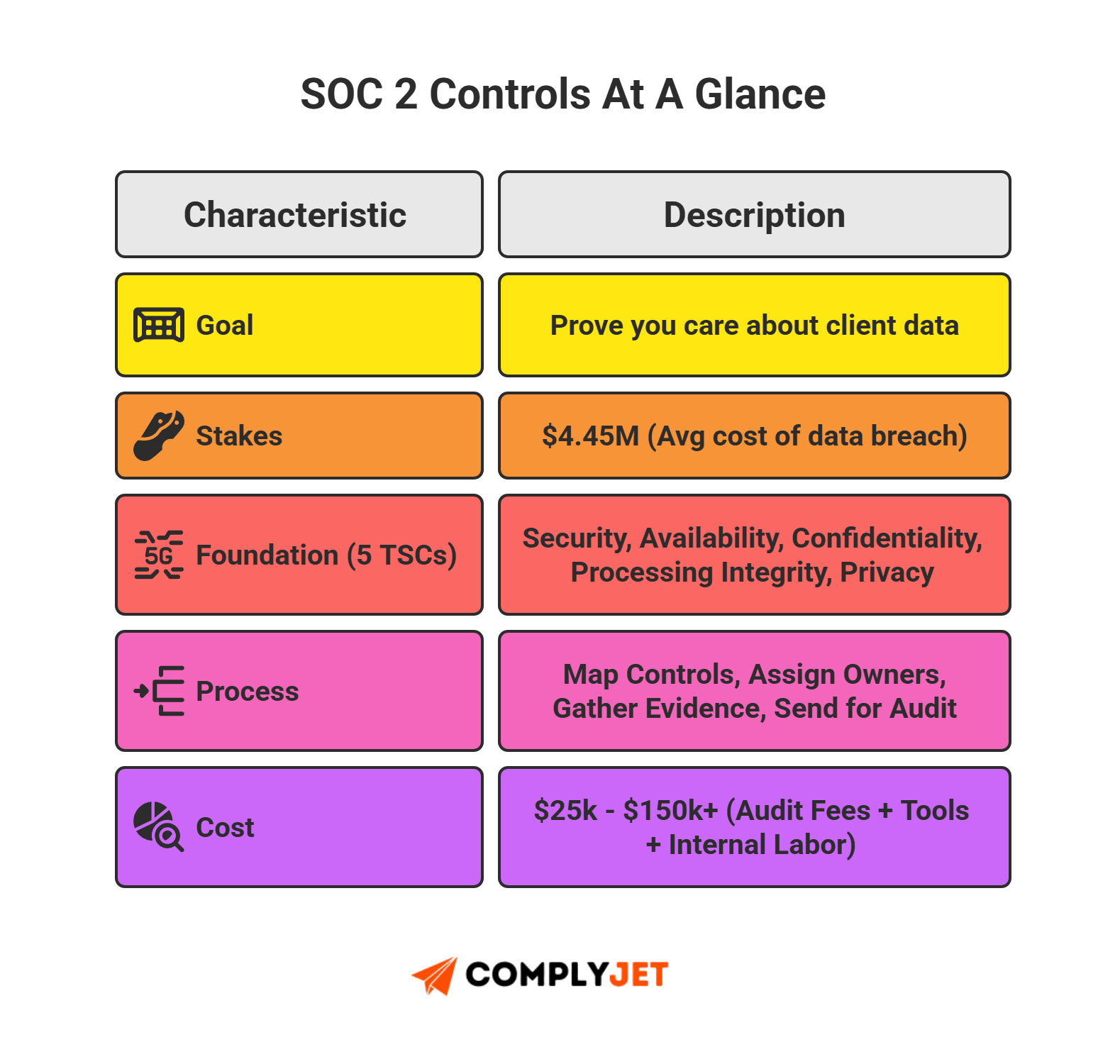
What Are SOC 2 Controls?
Think of SOC 2 controls as your company's defensive playbook. They aren't just abstract rules; they are the documented safeguard policies, technical standards, and operational habits that prove you care about your clients' data.
To pass an audit, you map these practices directly to the SOC 2 trust service criteria and organize them into your official SOC 2 controls list.
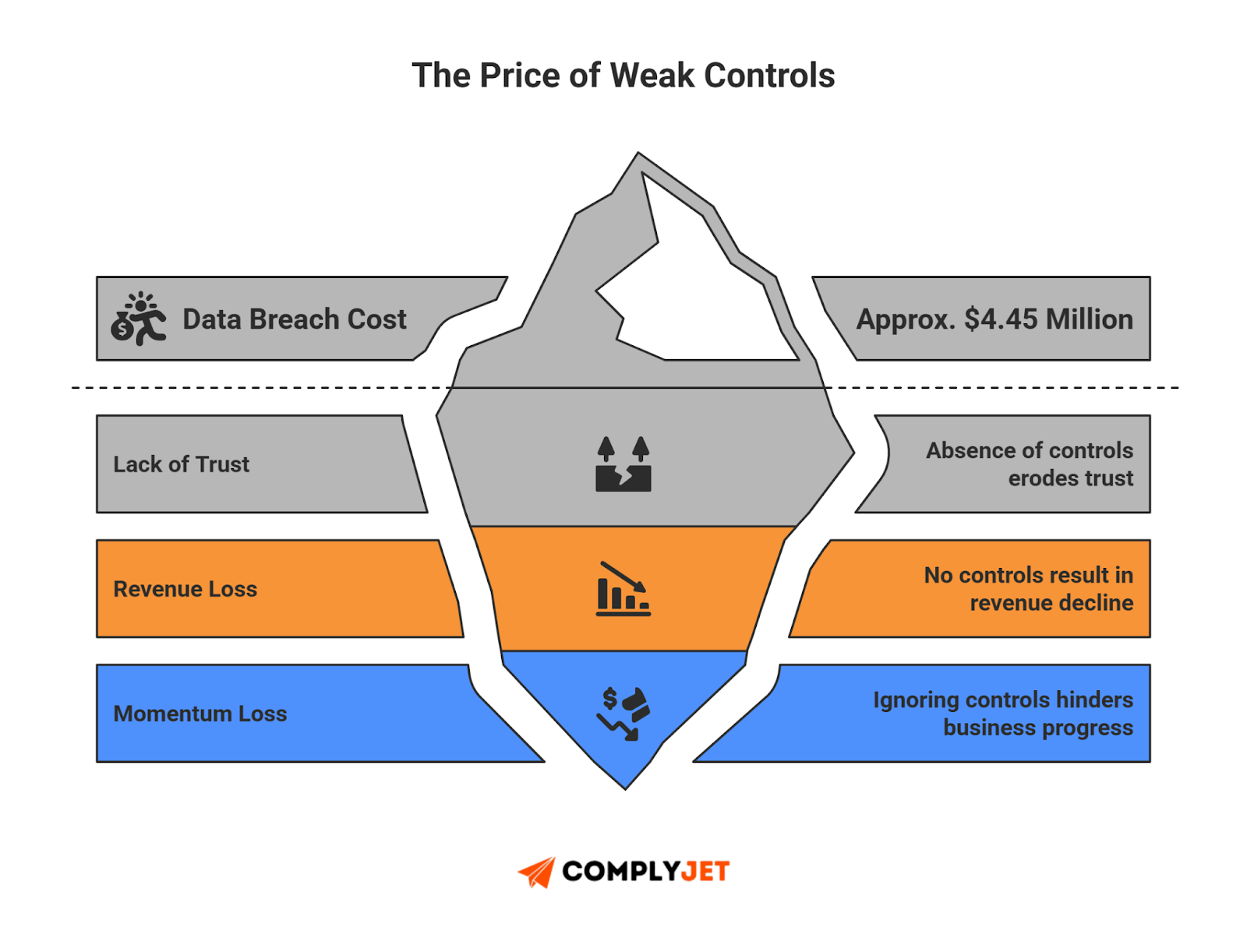
Fact Check: Organizations that fail basic access-control and logging controls incur on average a USD 4.45 million data-breach cost.
Why This Matters For Founders
No defined controls means no trust. SOC 2 controls protect your revenue, your reputation, and your momentum. They define exactly how your business protects systems, applies risk safeguards, and maintains trust.
Your SOC 2 controls list is built upon AICPA's SOC 2 trust service criteria, including security, availability, confidentiality, processing integrity, and privacy. Every control must align with AICPA security principles, satisfy the SOC 2 audit checklist, and meet specific SOC 2 documentation requirements so auditors can verify you actually did the work.
These safeguards operate against clear SOC 2 control objectives covering access, security standards, incident handling, monitoring, vendor oversight, and more.
The Core SOC 2 Control Categories

Core categories commonly found in a SOC 2 controls list include:
- Governance and security policies
- Risk management
- Asset Inventories
- Access and identity controls
- Vendor and third-party management
- Encryption and key security
- Change and deployment controls
- Logging and monitoring
- Incident response
- Business continuity and disaster recovery
If you want to map, track, and manage every SOC 2 control - from access rules to documentation and audits - check out ComplyJet. It's built to make SOC 2 compliance simple, clean, and scalable for fast-moving teams.
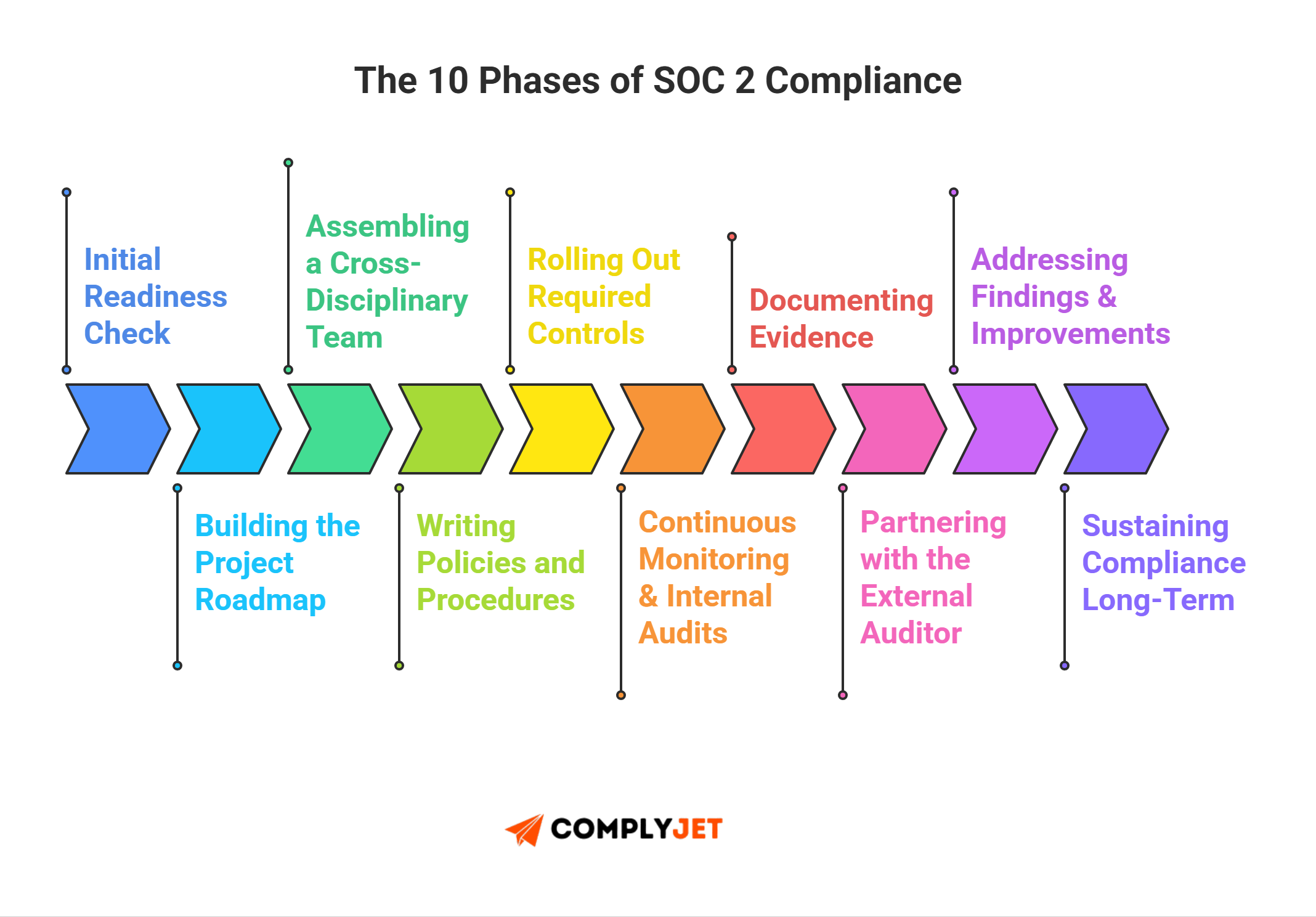
How Auditors Assess SOC 2 Controls And SOC 2 Control Objectives
Auditors don't just check boxes; they stress-test design and enforcement. They verify that every item on your SOC 2 controls list maps to SOC 2 control objectives and is proven by evidence. Strong controls match intent, reduce risk, and satisfy the SOC framework.
Don't want to copy-paste each control one by one? Download the full Master SOC 2 Controls List CSV to get every category pre-mapped and ready for import.
Stat Check: A recent global breach study found that 35.5% of all breaches in 2024 were driven by third-party access, which is exactly the kind of risk SOC 2 controls are meant to contain.
SOC 2 Audit Requirements Overview
Auditors apply the official SOC 2 audit checklist to validate each control, looking for traceable activity like approvals, logs, and tickets. If a control cannot be verified through clear SOC 2 documentation requirements, auditors treat it as weak or incomplete. Good evidence shows ownership and repeatability - not improvisation.
Mapping SOC 2 Controls to TSC Categories
Each item on your SOC 2 controls list maps to the SOC 2 trust service criteria. Controls must support the intent of the criteria and align with modern AICPA security principles. When controls fail to tie back to the criteria, they create disconnects that get flagged.
How Auditors Score SOC 2 Control Objectives
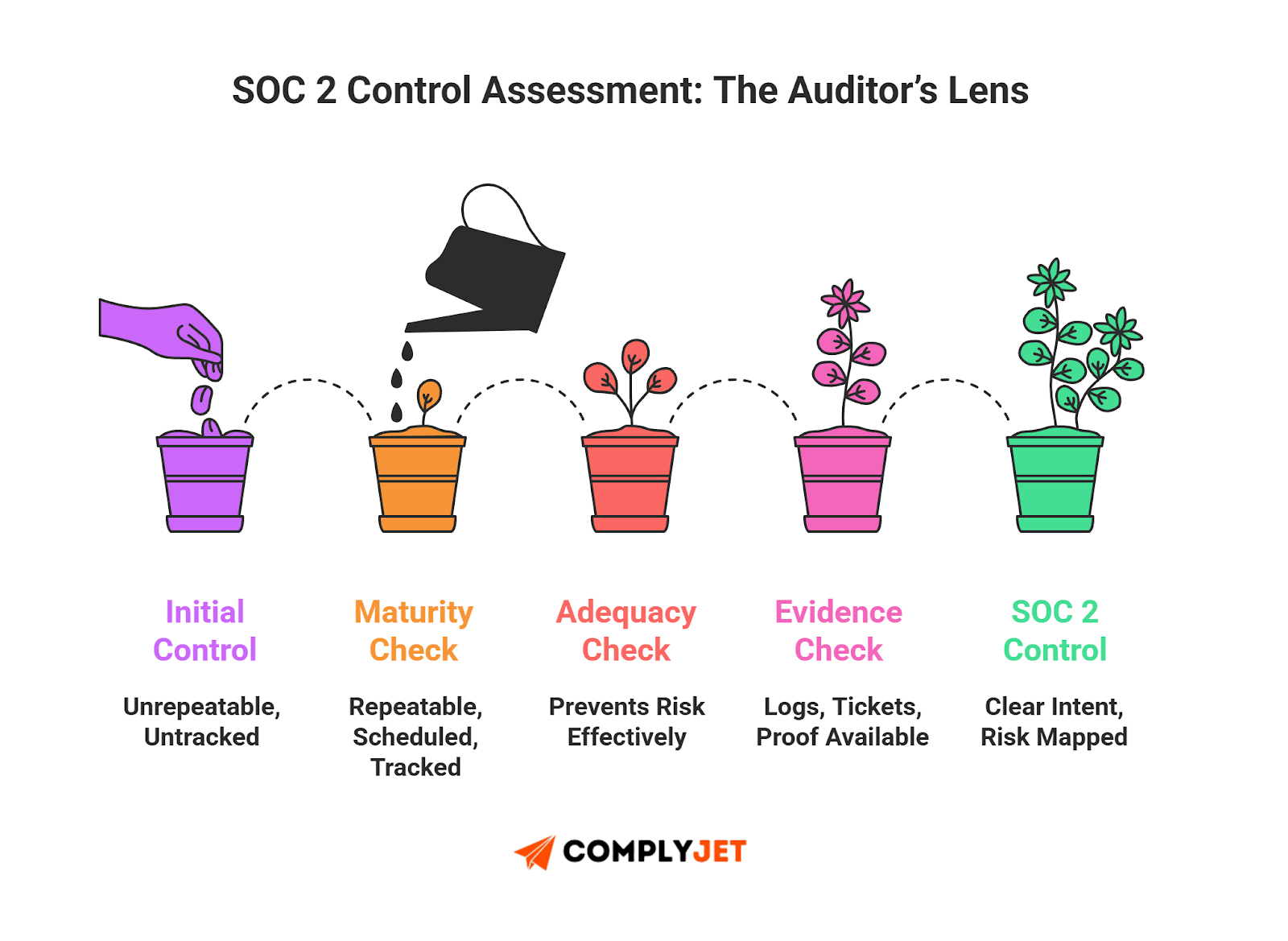
Auditors measure SOC 2 controls against stated SOC 2 control objectives to confirm:
- Maturity: Is the control repeatable, scheduled, and tracked?
- Adequacy: Does the safeguard prevent risk and provide strong evidence?
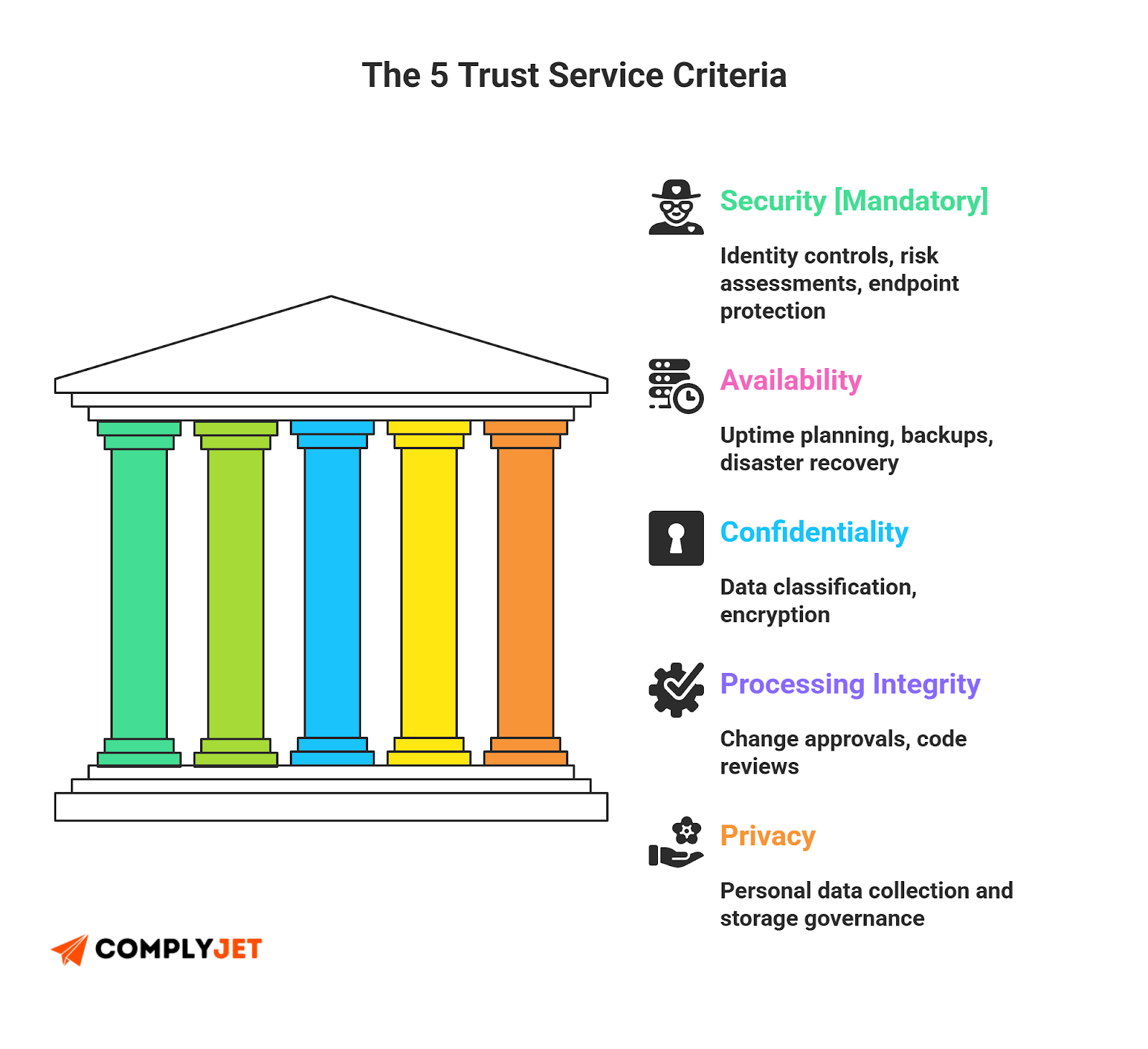
SOC 2 Trust Service Criteria (and How They Shape Your SOC 2 Controls List)
Your SOC 2 controls list isn't a random collection of rules; it's a structured defense built on the SOC 2 trust service criteria. When documented correctly, these criteria form the backbone of your SOC 2 controls matrix, mapping every safeguard to the AICPA security principles.
Security
Security is the foundation. Controls here must show how you protect systems. In your SOC 2 controls list, this includes identity controls, risk assessments, and endpoint protection. These items become auditable when mapped inside a SOC 2 controls matrix.
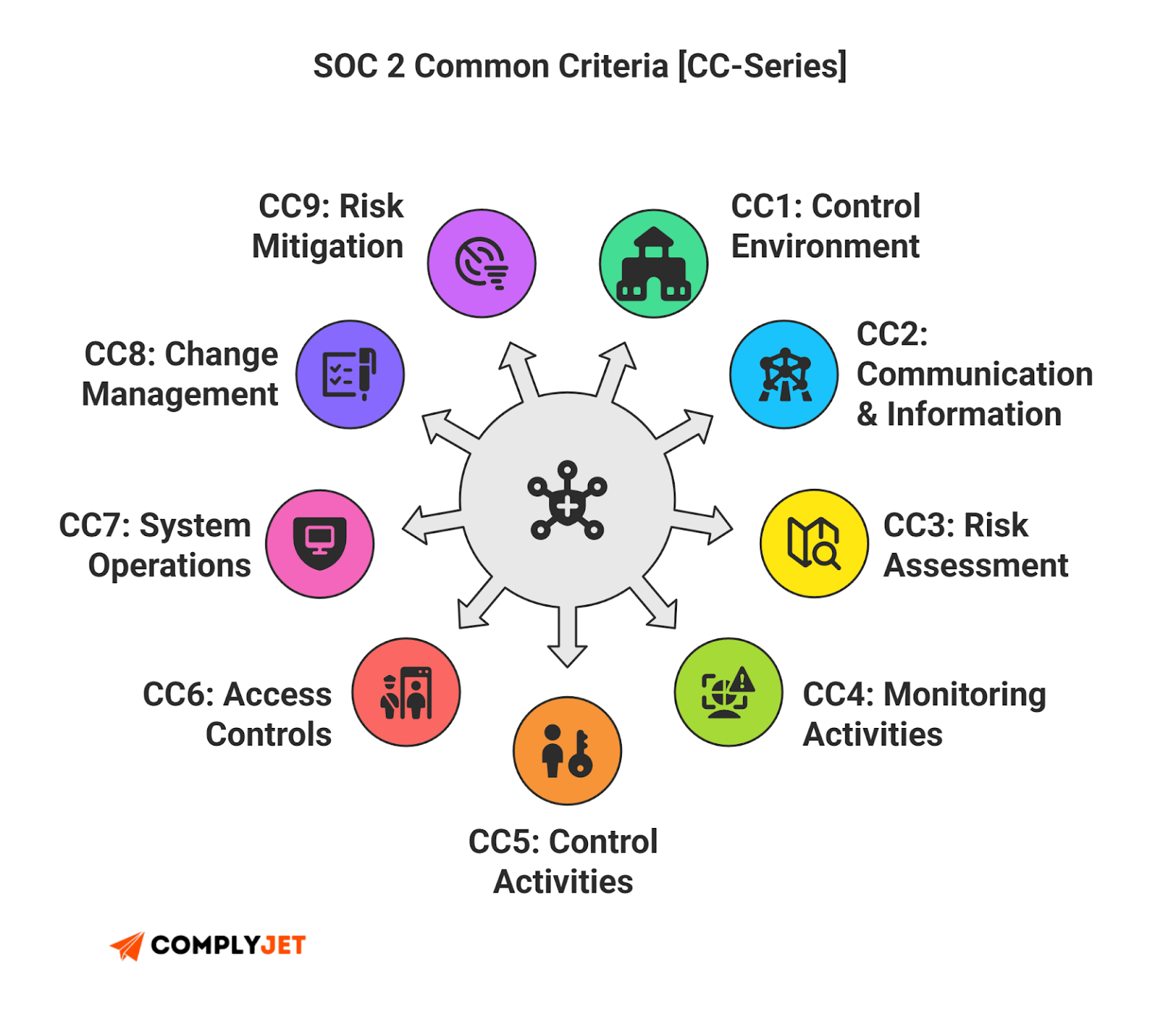
Availability
Availability criteria ensures systems remain stable through uptime planning and backups. When you structure these inside your SOC 2 controls list, you prove services remain operable and link back to SOC 2 control objectives.
Confidentiality
Confidentiality criteria set standards for sensitive data, including classification policies and encryption. Controls tied to confidentiality should be visible in your SOC 2 controls matrix and map to AICPA security principles.
Processing Integrity
Processing integrity ensures systems operate as intended. Safeguards within your SOC 2 controls list often include change approvals and code reviews. When aligned with SOC 2 trust service criteria, your SOC 2 controls reflect maturity.
Privacy
Privacy criteria address how personal data is collected and stored. A solid privacy structure within your SOC 2 controls list confirms good governance and aligns your SOC 2 controls to criteria.
Founder Tip: When reviewing the SOC 2 trust service criteria, start by mapping controls to evidence, not text. The fastest path to clean audits is showing what happened. A small, well-built SOC 2 controls matrix beats scattered policies every time.
The Complete SOC 2 Controls List - 70+ Controls Categorized
Next up, the operational backbone of a strong SOC 2 controls list. These SOC 2 controls tie directly to SOC 2 control objectives, AICPA security principles, and SOC 2 documentation requirements.
Founder Tip: The fastest way to fail a SOC 2 audit is poor documentation. SOC 2 access control policies and evidence trails matter more than fancy tooling - you need written proof that your SOC 2 controls list actually exists in practice.
Governance & Security Policy
- Documented Security Policies: Maintain formal security policies reviewed by leadership at defined intervals.
- Organization Structure Defined: Publish org charts clarifying ownership of security and SOC 2 control objectives.
- Security Roles & Responsibilities: Assign control responsibilities to specific roles. Include ownership for SOC 2 documentation requirements.
- Management Oversight: Senior leadership must oversee SOC 2 compliance controls, metrics, and risk posture.
- Security Governance Charter: Maintain board-reviewed governance materials aligned with AICPA security principles.
Founder Tip: If a control doesn't name an owner, auditors consider it "not implemented". Tie every SOC 2 controls list item to a specific person.

Below, we will break down the operational backbone of a strong security program. To track your progress as you read, grab the complete 70+ SOC 2 Controls CSV.
Risk Management
- Risk Assessment Program: Conduct periodic risk assessments tied to SOC 2 audit requirements.
- Risk Assessment Objectives: Document how risks are identified, scored, and remediated.
- Business Risk Reporting: Generate risk summaries for leadership linked to SOC 2 trust service criteria.
- Security & Risk Governance: Ensure structured oversight of threat scanning and SOC 2 control objectives measurement.
- Cyber Insurance Policy: Maintain corporate cyber insurance for operational continuity.
Stat Check: 38% of organizations have had a compliance report rejected by a vendor or prospect - a failure often rooted in weak risk assessments.
Asset Management
- Asset Inventory: Maintain a catalog of all systems supporting SOC 2 control objectives.
- Data Retention Rules: Define retention periods based on SOC 2 documentation requirements.
- Asset Disposal: Use formal sanitization steps on retired assets.
- Approved Production Inventory: Track production-level services to ensure audit traceability.
- Hardware & Software Lifecycle: Control and document procurement, onboarding, and decommissioning.
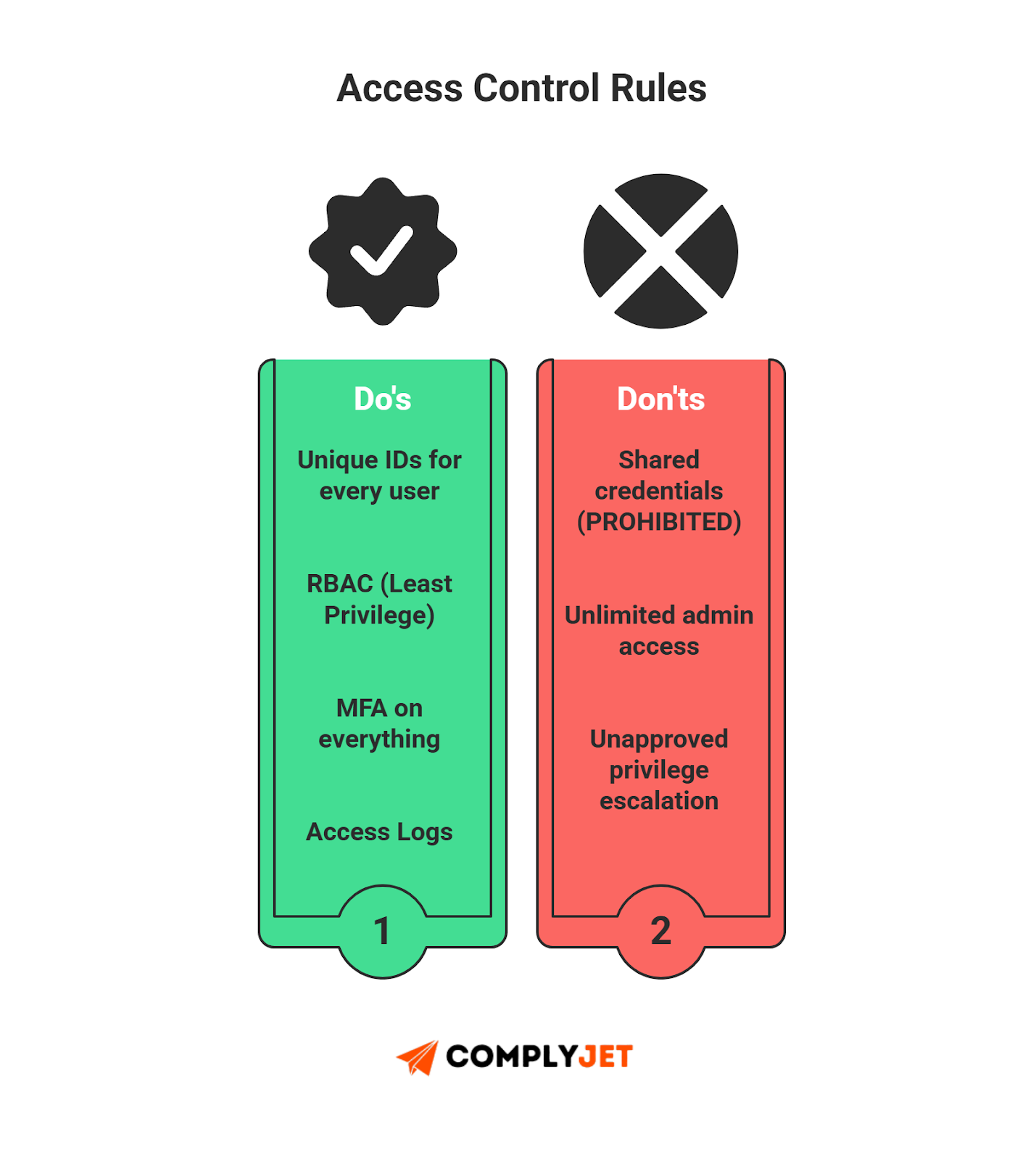
SOC 2 Access Control Policies (Identity, RBAC, MFA)
- Unique Authentication: All users must have individual IDs. Shared credentials are prohibited.
- RBAC Enforcement: Tie access to job roles and least privilege principles.
- Production Deployment Access: Only designated personnel get production access. Document approvals for SOC 2 audit checklist evidence.
- Database Authentication: Enforce structured DB authentication. Review logs for SOC 2 controls traceability.
- Privilege Escalation: Log and approve temporary privilege elevation. Align with AICPA security principles.
- Access Logging: Require logs across critical systems to support SOC 2 documentation requirements.
HR Security
- Background Checks: Verify backgrounds before granting access.
- Employment Agreements: Require contracts acknowledging SOC 2 compliance controls.
- Internal Info Handling: Align HR data-handling standards with SOC 2 trust service criteria.
- Role-Based Training: Train personnel based on control responsibilities.
- Onboarding & Separation: SOC 2 access control policies must extend from hiring to firing.
Vendor & Third-Party Risk
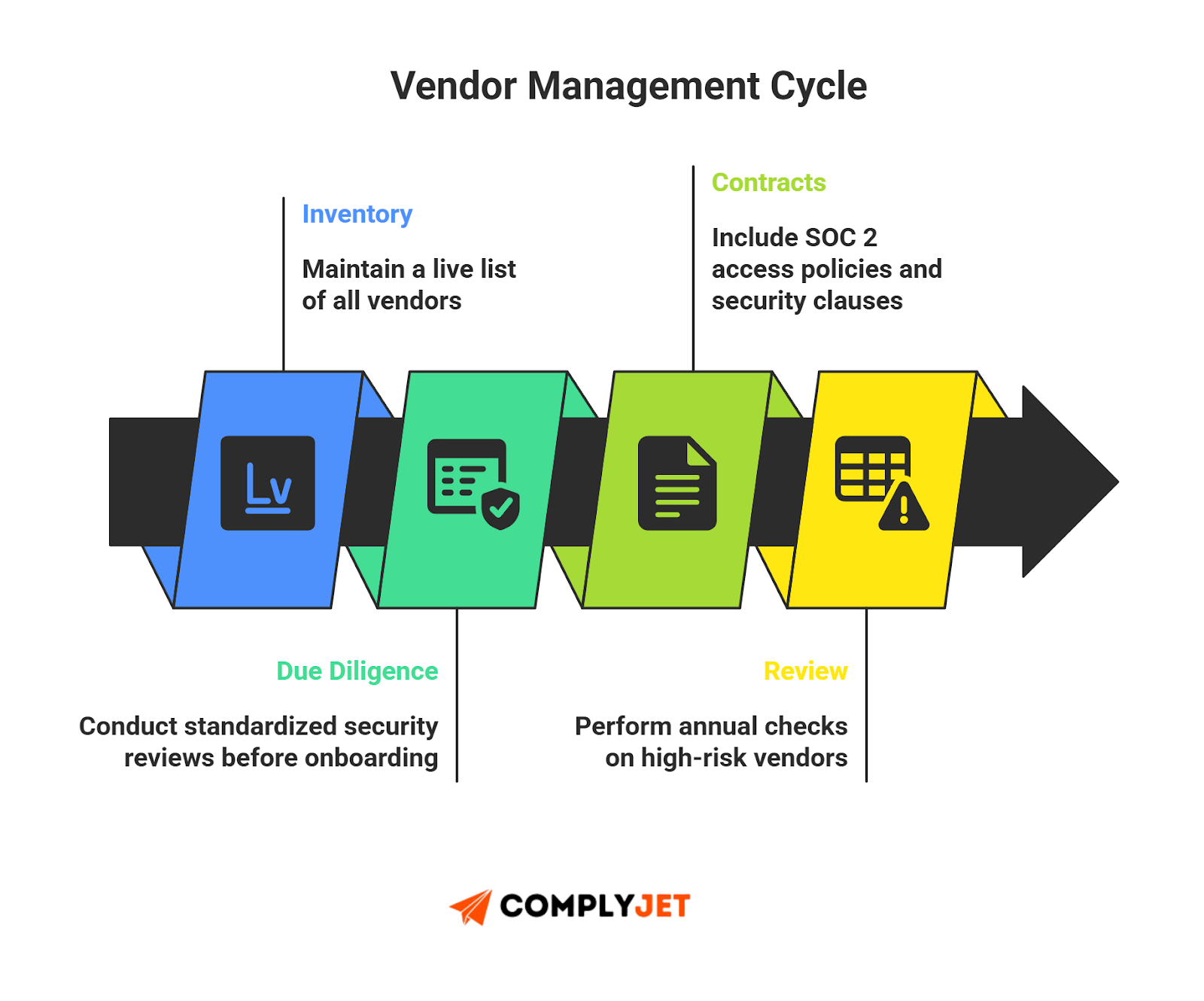
Strong vendor oversight is non-negotiable. This is where your SOC 2 controls list connects to real-world incidents.
- Vendor Inventory: Keep a live inventory of all vendors.
- Standardized Due Diligence: Use a structured SOC 2 audit checklist style review for onboarding.
- Security Clauses: Bake SOC 2 access control policies into contracts.
- Vendor Risk Scoring: Assign risk tiers based on data sensitivity.
- Ongoing Reviews: Review high-risk vendors annually to keep SOC 2 compliance controls current.
- Subprocessor Transparency: Require vendors to disclose their own compliance with your SOC 2 controls matrix.
Founder Tip: Treat vendors like internal teams with elevated risk - same SOC 2 access control policies, same documentation.
Cryptography & Key Management
These SOC 2 security controls prove you protect data:
- Encryption in Transit: Enforce TLS for all traffic.
- Encryption at Rest: Encrypt databases and backups.
- Key Management Policy: Define rotation and revocation for keys.
- Managed Vaults: Use a KMS. Never hard-code keys.
- Crypto Standards Review: Periodically review algorithms against AICPA security principles.
Founder Tip: Key management is where many teams fail. Put one owner in charge of keys.
Configuration & Baselines
- Hardened Baselines: Remove default accounts from server builds.
- Configuration Management: Track changes through a central system.
- Least-Privilege Defaults: Ship new services with minimal permissions.
- Periodic Reviews: Document drifts to satisfy SOC 2 documentation requirements.
- Approval Workflow: Map approvals into your SOC 2 controls matrix.
Secure Development & Change Control
- Secure SDLC: Maintain a written SDLC process.
- Code Review: Enforce peer reviews for production code.
- Dependency Scanning: Scan libraries for vulnerabilities.
- Separated Environments: Isolate dev, staging, and production.
- Formal Change Management: Require approvals and rollback plans.
- Emergency Procedures: Define fast-track processes that still align with SOC 2 control objectives.
Rule of thumb: Never let "we had to ship fast" explain a missing control. Fast is fine; undocumented isn't.
Logging & Monitoring
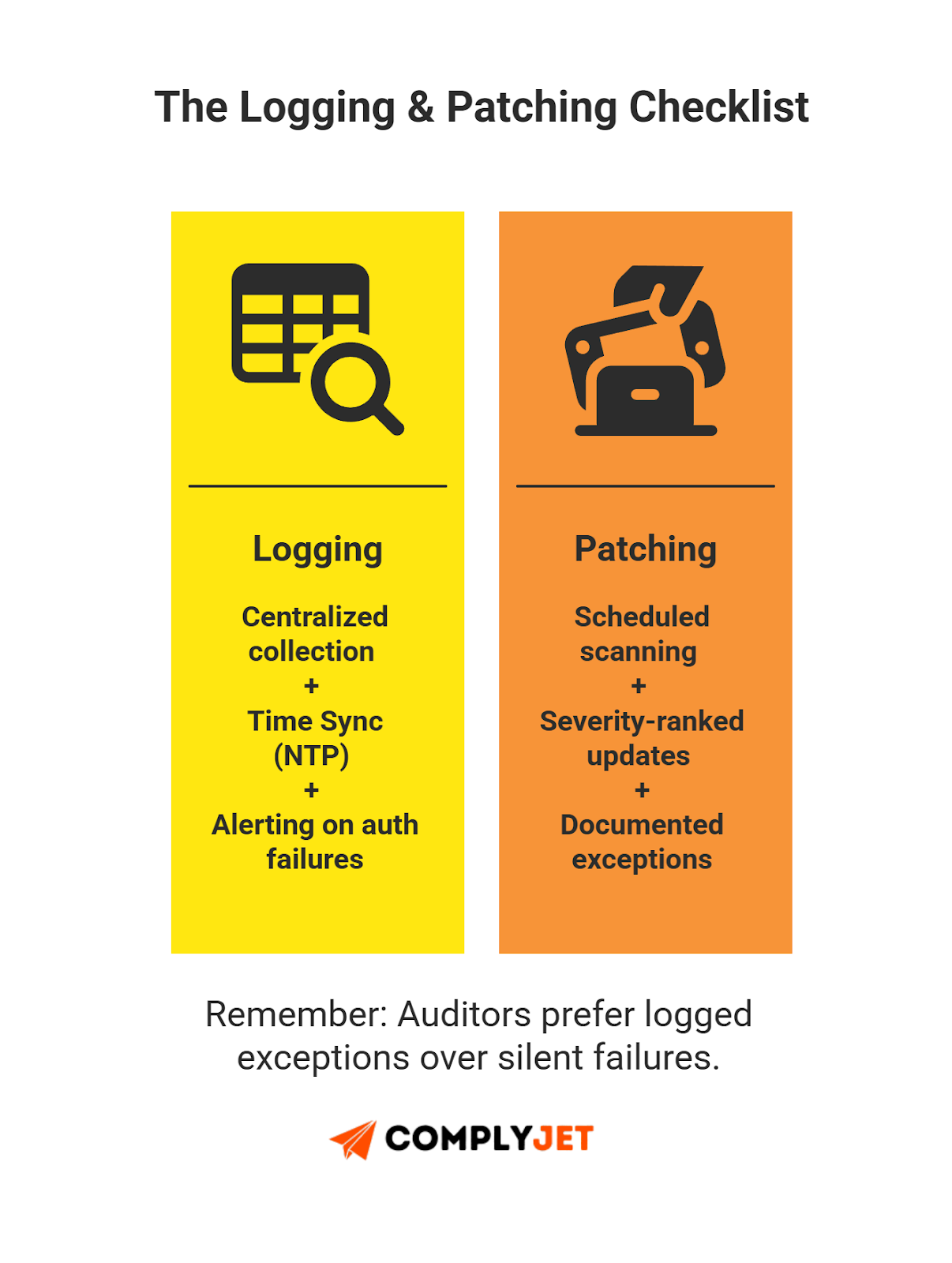
Logging is where your SOC 2 controls list meets incident handling.
- Centralized Collection: Forward logs to a central platform.
- Security Monitoring: Alert on auth failures and admin actions.
- Log Retention: Keep logs to satisfy SOC 2 compliance controls.
- Time Sync: Use NTP for reliable timestamps.
- Regular Review: Review key logs as part of your SOC 2 audit checklist.
Stat Check: It's not surprising that 74% of organizations fear insider threats - without robust logging and monitoring, you're flying blind.
Vulnerability & Patch Management
- Scheduled Scanning: Scan periodically and track remediation.
- Patch Management: Update OS and dependencies. Keep evidence for the SOC 2 audit checklist.
- Prioritization: Patch severity-ranked items first.
- Security Benchmarking: Compare configs against baselines to align with AICPA security principles.
Founder Tip: Don't hide exceptions. Auditors tolerate clearly logged exceptions more than silent patch failures.
Incident Response
Think of these controls as your SOC 2 survival kit-they prove you can take a hit and keep moving.
- IR Plan: Maintain a written policy with assigned roles.
- IR Testing: Run tabletop exercises. Retain logs as SOC 2 documentation requirements evidence.
- Post-Incident Review: Perform retros to tighten SOC 2 control objectives.
Business Continuity & Disaster Recovery (BCDR)

Your SOC 2 security controls list must include resilience.
- BC Plan: Document owner roles and failover expectations.
- DR Procedures: Maintain runbooks for architecture switchover.
- BCDR Testing: Test plans and track evidence.
- Dependencies: Identify vendor reliance.
Founder Tip: DR drills aren't optional. They are the only proof your SOC 2 controls list isn't theoretical.
Backup & Resilience
Backups map to SOC 2 compliance controls.
- File-Level Backups: Back up essential data regularly.
- Encrypted Backups: Encrypt at rest and in transit.
- Off-Site Storage: Store backups separately from primary infrastructure.
- Restoration Testing: Ensure all audit evidence is in the SOC 2 controls matrix.
Physical & Environmental Security
- Physical Access: Limit access to authorized personnel only.
- Visitor Procedures: Log visitors. Store evidence for SOC 2 documentation requirements.
- Periodic Reviews: Audit badge lists to match the SOC 2 controls matrix.

Network Security & Segmentation
Network controls are core items in a SOC 2 controls list.
- Network Policies: Specify filtering and routing rules.
- Firewalls: Restrict traffic by business criteria.
- Vendor Access: Limit vendor routes based on your SOC 2 controls matrix.
- Periodic Review: Review rules to satisfy SOC 2 documentation requirements.
- Segmentation: Separate sensitive environments. This is a key SOC 2 security controls list expectation in AICPA's revised points of focus.
Endpoint & Device Controls
- Device Inventory: Map devices to users.
- Approved Software: Restrict applications to approved lists.
- Configurations: Enforce lock screens and password policies.
- Antivirus/EDR: Deploy protections with event logs.
Data Classification & Handling
Classification meets SOC 2 control objectives here.
- Classification Standards: Assign data tiers (e.g., confidential, public).
- Access Rules: Tie data access to SOC 2 access control policies.
- Disposal: Require irreversible sanitization of media.
Capacity & Operational Resilience
These show SOC 2 controls govern uptime.
- Monitoring: Track compute and storage trends.
- Performance SLAs: Formalize SLAs linked to SOC 2 trust service criteria.
- Failover: Document fallback systems.
Training & Security Awareness
If controls exist only on paper, SOC 2 compliance controls fail.
- Awareness Program: Conduct periodic training.
- Verified Policy Awareness: Don't let policies sit unread. Enforce a signature workflow to confirm every team member knows the standards.
- Evidence Retention: Maintain training logs to satisfy SOC 2 documentation requirements.
SOC 2 Controls Matrix - How to Organize Controls, Evidence & Criteria
A SOC 2 controls matrix helps you structure safeguards. It links them to SOC 2 control objectives and the SOC 2 trust service criteria. When your SOC 2 controls list is sorted into a matrix, each safeguard maps to clear proof.
Building this matrix manually takes hours. We’ve already set up the columns for Objective, Criteria, and Evidence for you. Download the SOC 2 Controls Matrix Template (CSV).
Build Matrix Columns
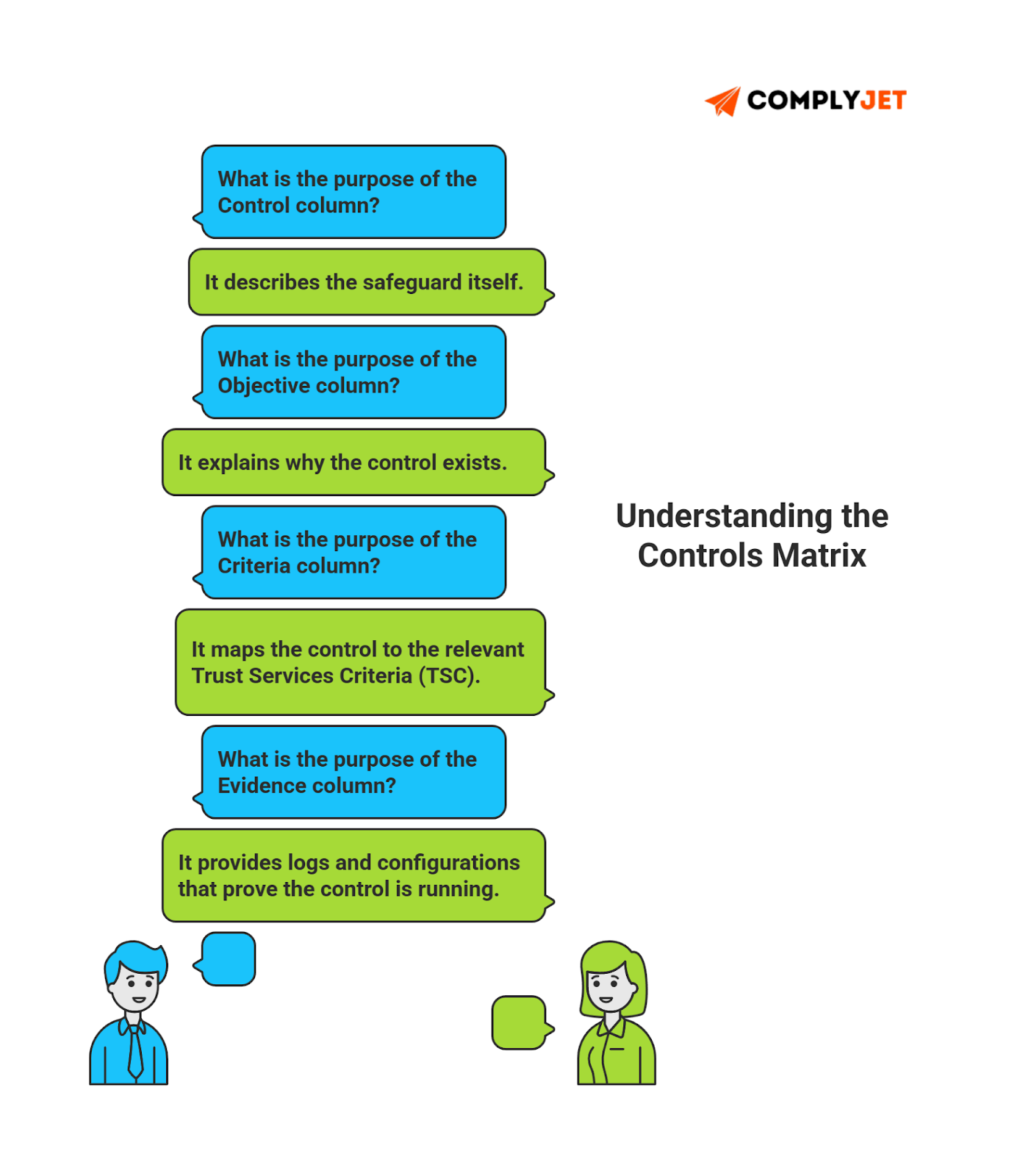
Your SOC 2 controls matrix should center on five core fields:
- Control: The exact safeguard.
- Objective: Which SOC 2 control objectives it supports.
- Criteria: The SOC 2 trust service criteria it aligns with.
- Evidence: Proof the control exists (logs, configs).
- Ownership: A single role.
Founder Tip: The controls that fail fastest are the ones without named owners. If no one "owns" execution, auditors assume the control doesn't exist.
Why SOC 2 Documentation Requirements Matter
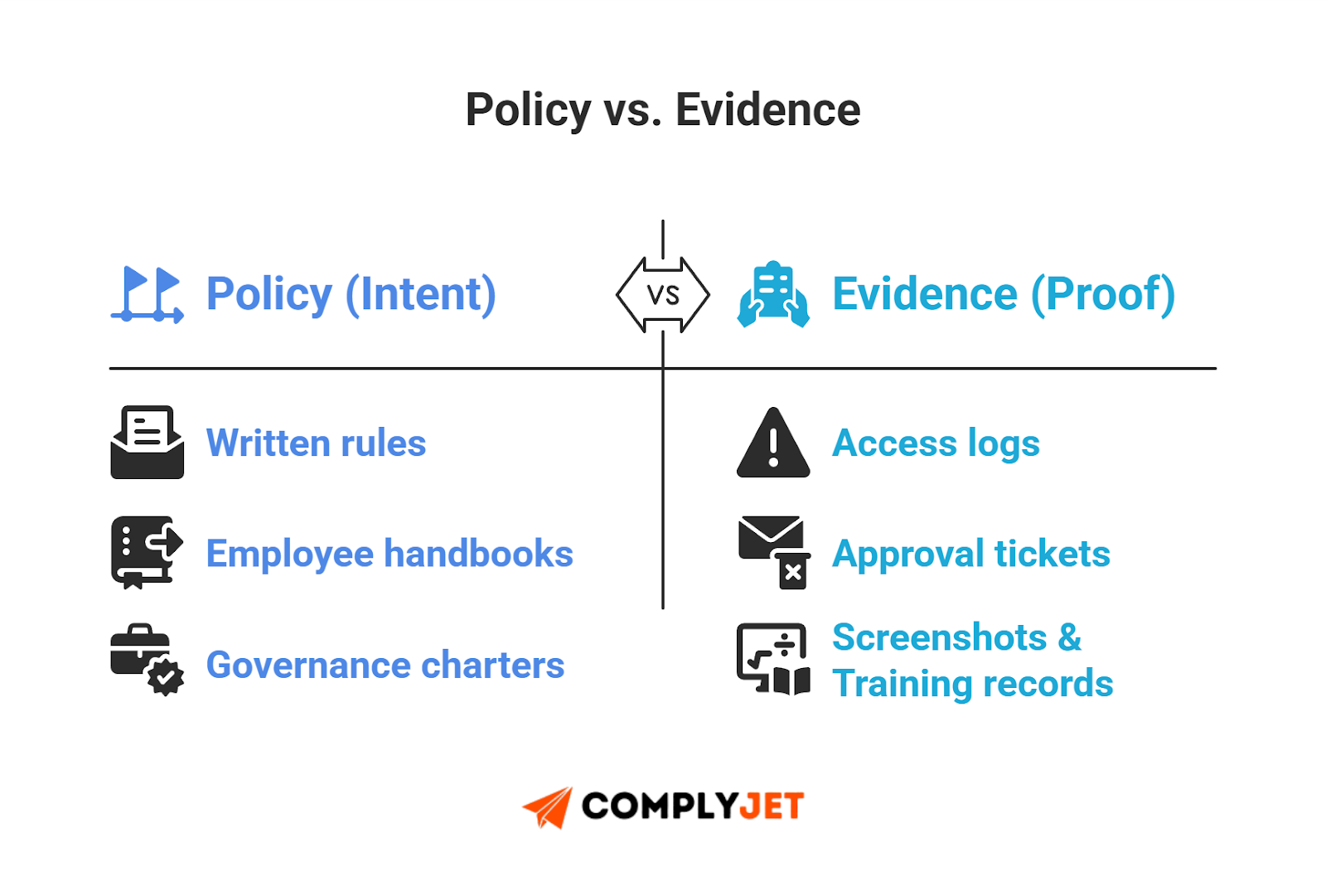
A SOC 2 controls matrix is only as strong as its proof. SOC 2 documentation requirements expect implementation evidence, creating continuity between your SOC 2 controls and the real-world SOC 2 compliance controls auditors test.
SOC 2 Audit Checklist - Internal Validation
A SOC 2 audit checklist helps you verify your SOC 2 controls before auditors arrive. Every safeguard in your SOC 2 controls list must be mapped to proof to meet SOC 2 audit requirements early.
Required Evidence Records
For any SOC 2 audit checklist, evidence is key. Auditors expect you to show that SOC 2 controls actually run. Collect approval logs, access reviews, and screenshots, tying every item to a specific control to support SOC 2 control objectives.
Internal Health Checks
Use the SOC 2 audit checklist to check health and confirm whether SOC 2 controls were executed on schedule. This proves your SOC 2 controls list is enforced and improved.
Automate your SOC 2 audit checklist and close gaps faster with ComplyJet.
SOC 2 Access Control Policies - IAM, Privileges & Reviews
Strong SOC 2 access control policies are your first line of defense. Every item in your SOC 2 controls list must prove how identities are granted, reviewed, and revoked, feeding directly into your SOC 2 security controls list.
Identity & Provisioning Rules
Provisioning is the foundation. Accounts must be tied to real roles and map back to your SOC 2 controls.
Founder Tip: Reject shared logins instantly. They negate traceability.
MFA, JIT, RBAC
These are core items in any SOC 2 security controls list.
- Multi-factor Authentication (MFA) hardens authentication.
- Just-In-Time (JIT) access limits privilege elevation to short, audited time windows. This lessens the blast radius of compromised accounts.
- Role-Based Access Controls (RBAC) ensures permissions match job scope.
All three should appear in your SOC 2 access control policies and must be reflected in your SOC 2 controls list.
Quarterly Access Reviews
Quarterly reviews keep SOC 2 controls current. Each review cycle should be logged as formal evidence to validate SOC 2 access control policies and link findings back to the SOC 2 controls list.
Logging & Access Trails
Logging is the proof behind your SOC 2 access control policies. Logs let you demonstrate that the SOC 2 controls list has real-world enforcement.
SOC 2 Documentation Requirements - Logs, Inventories & Evidence
Your SOC 2 controls list is only as good as its proof. SOC 2 documentation requirements turn abstract policies into audit-ready evidence that aligns with SOC 2 trust service criteria.
Audit-Ready Documentation
Auditors expect structured evidence like access logs and change trails mapped back to the SOC 2 controls list. Store documentation with timestamps to confirm controls support the SOC 2 trust service criteria.
Mandatory Artifacts
Certain evidence is non-negotiable. Auditors request access reviews and training records linked to relevant SOC 2 controls and tagged against the SOC 2 controls list.
Founder Tip: Every artifact should support a control. If it can't be tied to a safeguard, store it outside the data room that you share with the auditor.
SOC 2 Control Objectives - What Auditors Look For
SOC 2 control objectives define the "why" behind every rule. Auditors expect every safeguard in your SOC 2 controls list to support AICPA security principles by proving intent, not just existence.
What a Control Must Prove
For any SOC 2 control objectives review, auditors expect clarity. If a SOC 2 controls item grants access, the objective is to prove least privilege. Each safeguard must show purpose.
SOC 2 Security Controls List for 2025 - Critical Safeguards
The bar for 'secure' has moved, and static checklists won't cut it anymore. We've stripped out the legacy fluff to give you the operational safeguards that auditors are actually hunting for in 2025.
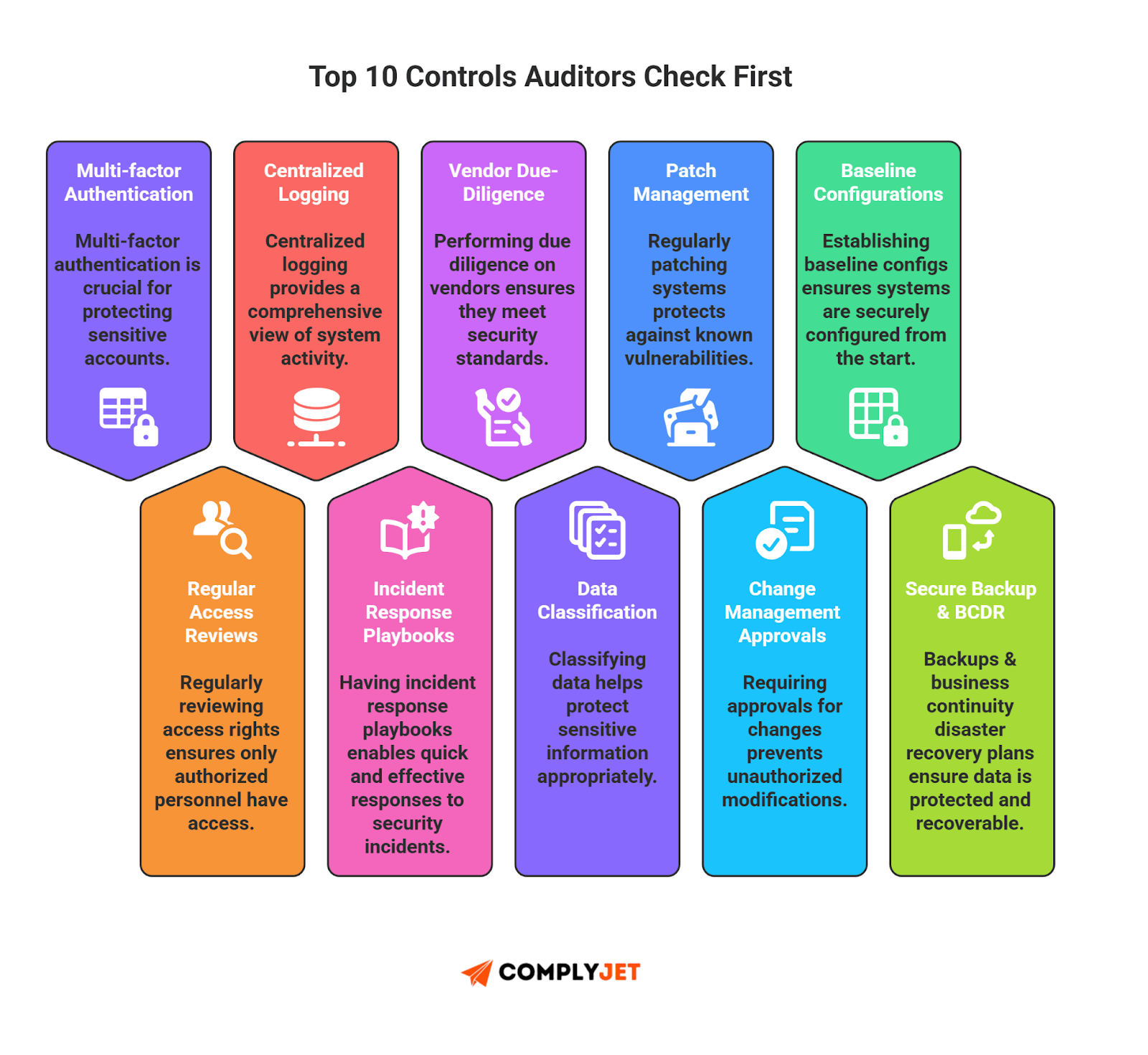
Top 10 Controls Most Auditors Flag
These are the SOC 2 controls auditors examine first. Prioritizing these controls ensures you avoid the common pitfalls tripping up founders during SOC 2 audits in 2025.
- MFA for Sensitive Accounts: Auditors look for enforcement visible across your SOC 2 controls list.
- Regular Access Reviews: Confirm SOC 2 controls stay current.
- Centralized Logging: Logs must satisfy SOC 2 compliance controls.
- Incident Response Playbooks: Every SOC 2 controls list is incomplete without IR triggers.
- Vendor Due-Diligence: Reviews must be traceable back to your SOC 2 controls.
- Data Classification: Tie practices to documented SOC 2 compliance controls.
- Patch Management: Risk acceptance must be written and linked back to SOC 2 controls.
- Change Management Approvals: Artifacts must exist in the SOC 2 controls list.
- Baseline Configurations: Hardening reinforces the maturity of your SOC 2 controls.
- Secure Backup & BCDR: These prove your SOC 2 controls list protects availability.
Auditors will look for these critical safeguards first. Use our checklist to mark them as 'Ready' or 'Missing' before your audit begins. Download the Audit Readiness Checklist CSV.
SOC 2 Audit Requirements for 2025
SOC 2 audit requirements dictate how auditors validate your defense. Your SOC 2 controls list must show real execution-logs, dates, and owners - because theoretical SOC 2 compliance controls don't pass audits.
Type I vs Type II Expectations
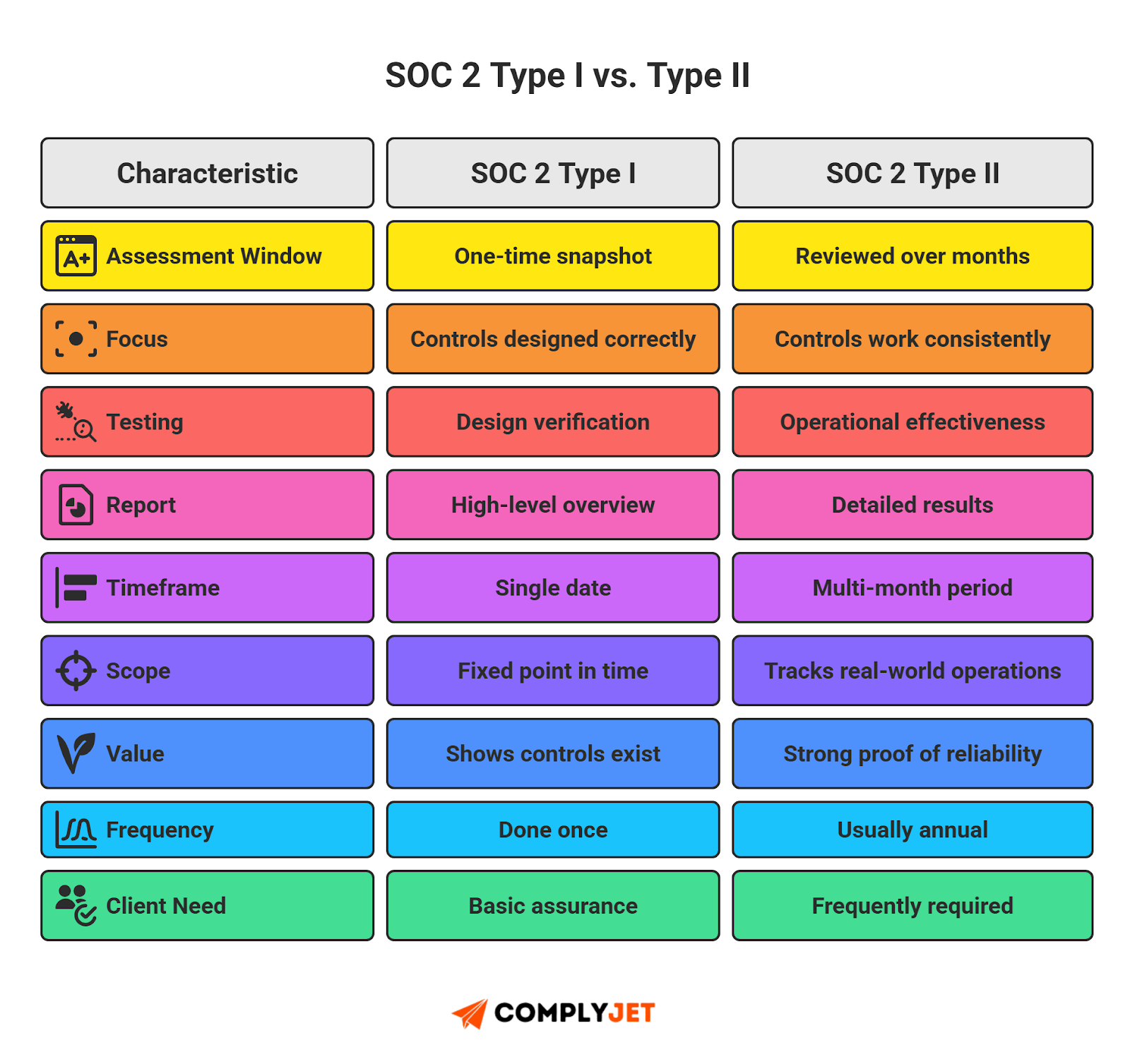
Type I audits validate that SOC 2 controls are designed correctly. Every safeguard in your SOC 2 controls list must map cleanly to intent.
Type II audits go further. Auditors test the same SOC 2 controls across months. Readiness requires logs that satisfy SOC 2 audit requirements.
Testing Period Windows
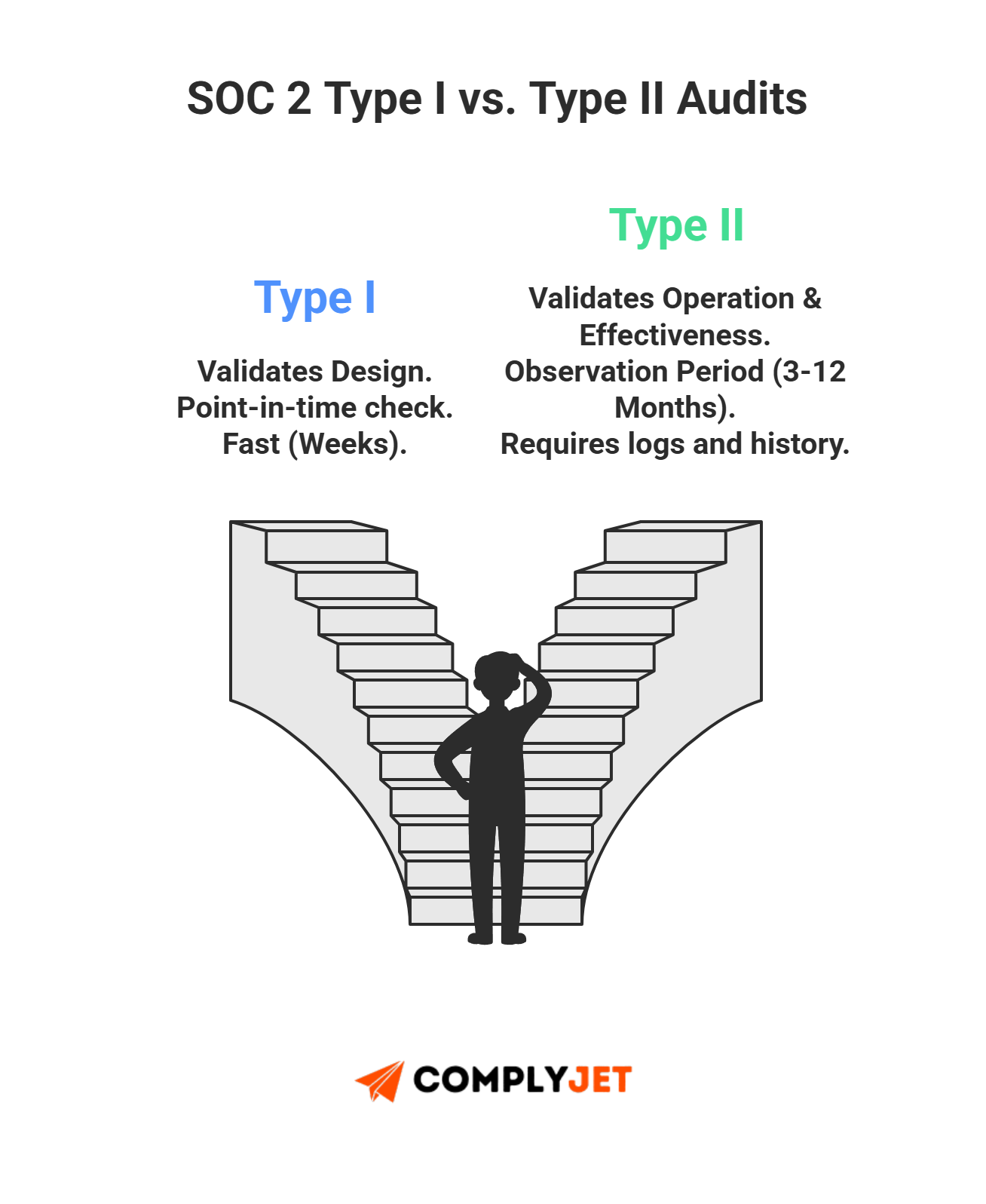
For Type II, SOC 2 controls must show enforcement over 3-12 months. Each action should link to the SOC 2 controls list. Gaps weaken SOC 2 compliance controls. For SOC 2 Type I, it usually takes weeks, especially with automation.
Control Evidence Rules
Auditors look for execution proof tied to SOC 2 audit requirements. Evidence should be attached to the SOC 2 controls list. The clearer the trail, the easier it is to verify that SOC 2 controls were real.
Templates, Checklists & Downloadable Pre-Audit Controls Matrix
Use these to organize SOC 2 controls and build your SOC 2 controls list cleanly. Each item drops into a SOC 2 controls matrix.
Or get the pre-formatted file containing Control Names, Objectives, and Evidence sources.
Download the Master SOC 2 Controls List CSV
SOC 2 Controls Matrix Template
Use this as the base for your SOC 2 controls matrix.
Columns:
- Control Name
- Control ID
- SOC 2 Control Objective
- Trust Criteria
- Evidence Source
- Owner
SOC 2 Documentation Checklist
Use this for meeting SOC 2 documentation requirements:
- Access-review logs
- Change-control approvals
- Incident response drills
- Vendor due-diligence records
- SOC 2 controls list policies
Every artifact should tie back to SOC 2 controls.
SOC 2 Audit Checklist for Internal Readiness
This aligns to the SOC 2 audit checklist structure:
- All controls mapped to evidence
- SOC 2 controls list aligned to type (I or II)
- Owners assigned for each safeguard
Trust Criteria Controls Mapping Sheet
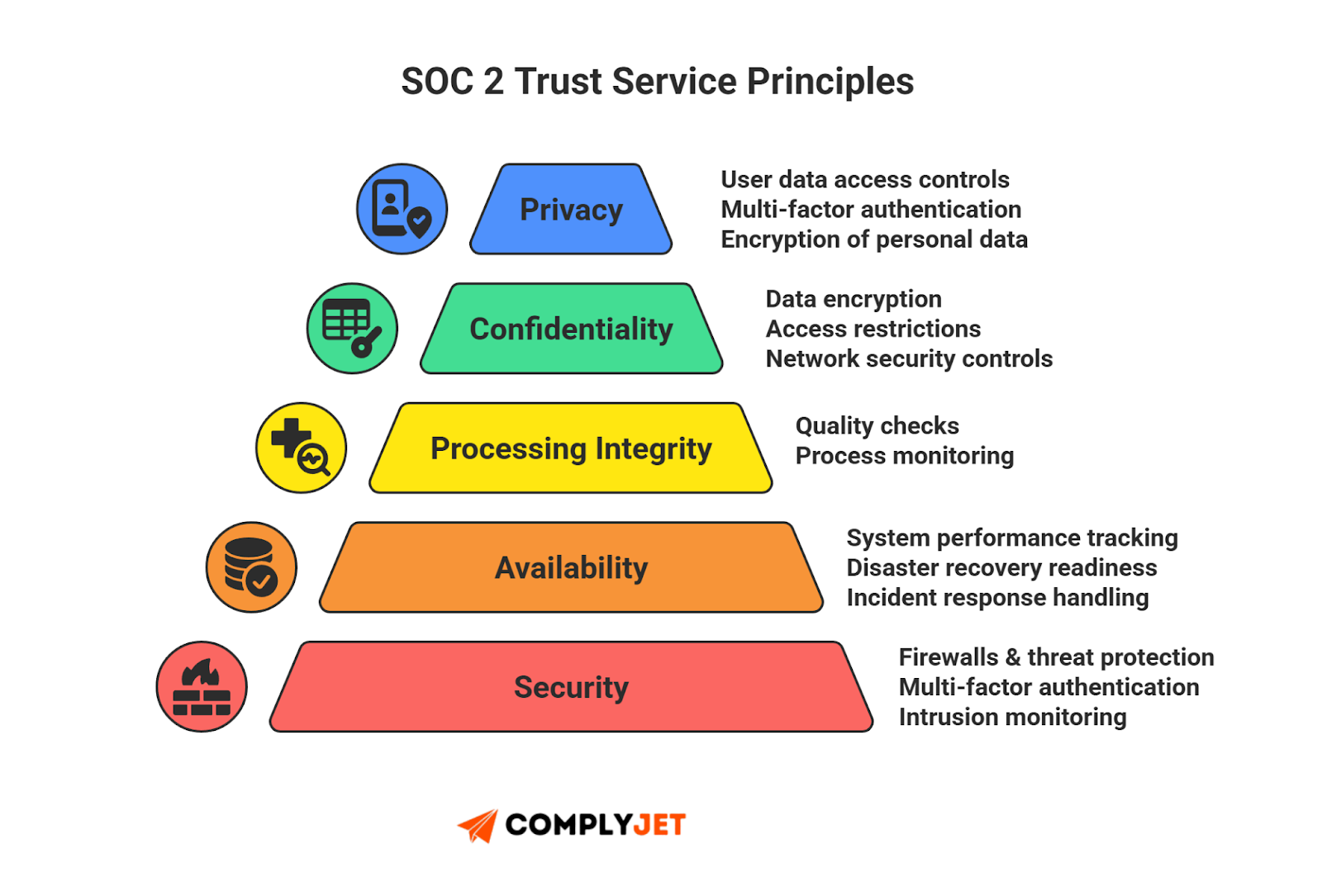
Use this to connect SOC 2 controls to objectives.
- Security (MFA/Logging)
- Availability (BCDR/Backups)
- Confidentiality (Classification)
Map your controls once. Attach evidence. This proves SOC 2 control objectives are met.
SOC 2 Audit Timeline and Cost
The following table breaks down typical costs and timelines for 2025*:
*Please note that the information above is meant to be indicative and not conclusive. Real costs and timelines fluctuate significantly based on your enterprise's needs and structure. Also keep in mind that many compliance solutions are often notorious in their lack of transparency regarding exact pricing.
If you're looking for clarity in pricing, try ComplyJet and fulfill your compliance needs without burning a hole through your wallet. Start your free trial now.
Founder-to-Founder FAQs: The Real Questions You Have
Can I just skip to SOC 2 Type 2, or do I need Type 1 first?
Technically, you can go straight to Type 2, but it's rarely the right strategic move for a startup needing to unblock sales immediately.
- The Reality: A Type 1 report is a "snapshot" that proves your design is correct at a single point in time. You can achieve this in weeks to satisfy an urgent enterprise contract.
- The Trap: A Type 2 requires a mandatory observation window (usually 3-12 months) where auditors watch your controls in action. You literally cannot speed this up.
- Founder Verdict: Start with Type 1 to close deals now, then immediately flip the switch to your Type 2 observation period.
How much is this actually going to cost me?
Expect to spend between $25,000 and $100,000 in your first year when combining audit fees, tooling, and internal labor.
- Audit Fees: A Type 1 audit fee typically lands between $5,000-$25,000. Type 2 fees jump to $7,000-$50,000+ because the auditor does more work.
- Hidden Costs: The real killer is internal labor-engineers dropping product work to gather evidence, which can cost an estimated $30,000-$75,000 in productivity if done manually.
- Readiness: Consulting or gap analysis can add another $5,000-$15,000 if you don't use automation software.
What happens if we "fail" a control? Do we lose the certification?
SOC 2 isn't a pass/fail test; it's an opinion.
- The "Qualified" Opinion: If an auditor finds significant gaps (exceptions), they issue a "Qualified Opinion". This isn't a failure, but it is a "red flag" that you must explain to customers.
- The "Unqualified" Opinion: This is the "clean" report everyone wants, meaning no material exceptions were found.
- Recovery: You can use Section 5 of the report to explain your remediation plan, which can often reassure clients despite the exception.
Do I really need to implement all 5 Trust Service Criteria (TSC)?
Not really. You need to pick your scope.
- Mandatory: Only Security (Common Criteria) is required for every SOC 2 audit.
- Optional: Availability, Confidentiality, Processing Integrity, and Privacy are optional add-ons.
- Founder Verdict: Don't bloat your audit. Most SaaS startups only need Security and Confidentiality (if handling sensitive IP) or Availability (if you have strict SLAs). Adding "Privacy" or "Processing Integrity" significantly increases your workload.
How much time will this steal from my team?
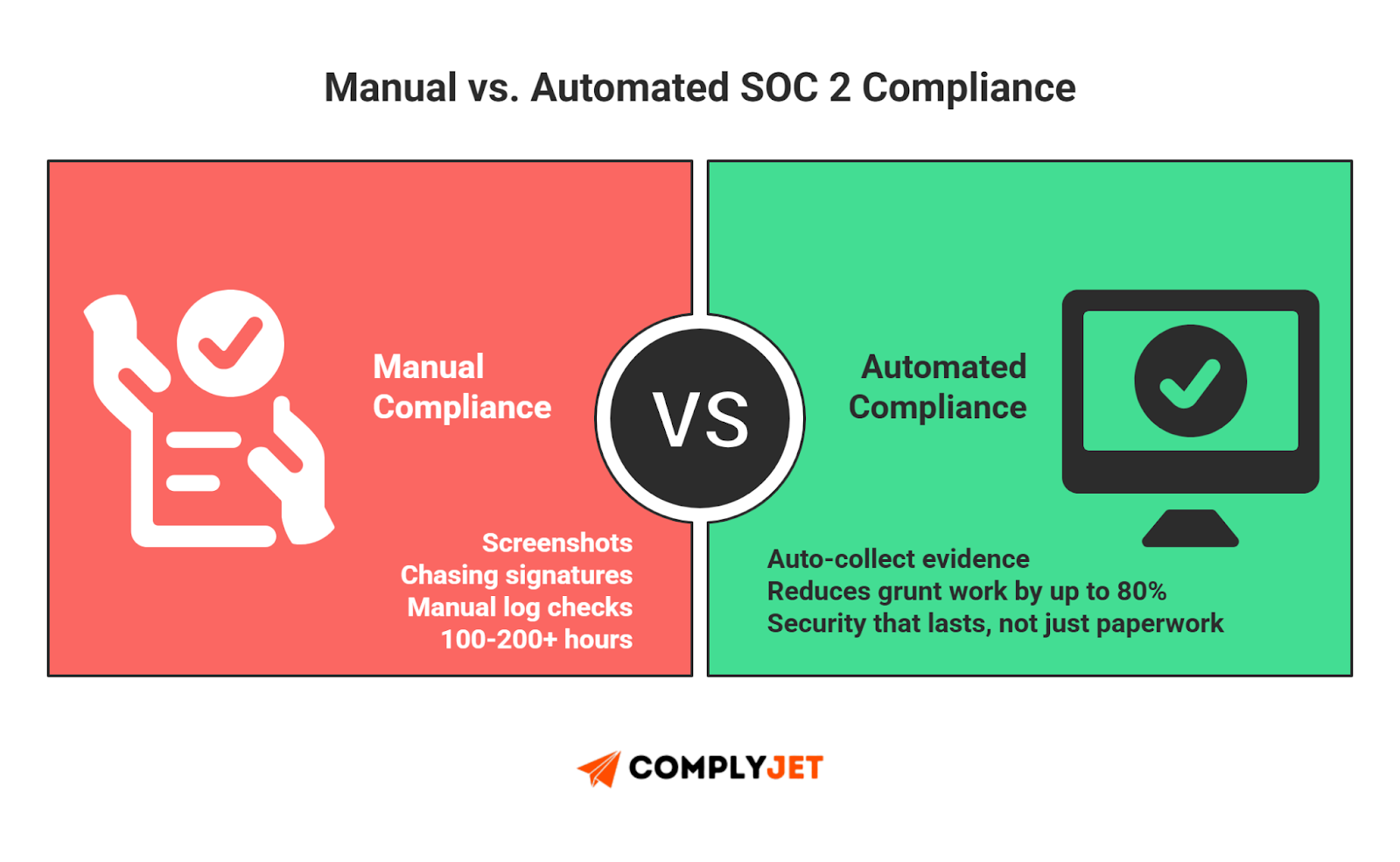
If you do it manually using spreadsheets, expect to burn 100-200+ hours across your engineering and admin teams.
- The Manual Drag: You will spend hours taking screenshots, chasing policy signatures, and manually checking logs.
- The Automation Fix: Using a compliance automation platform can reduce this manual grunt work by up to 80% by automatically collecting evidence from your tech stack.
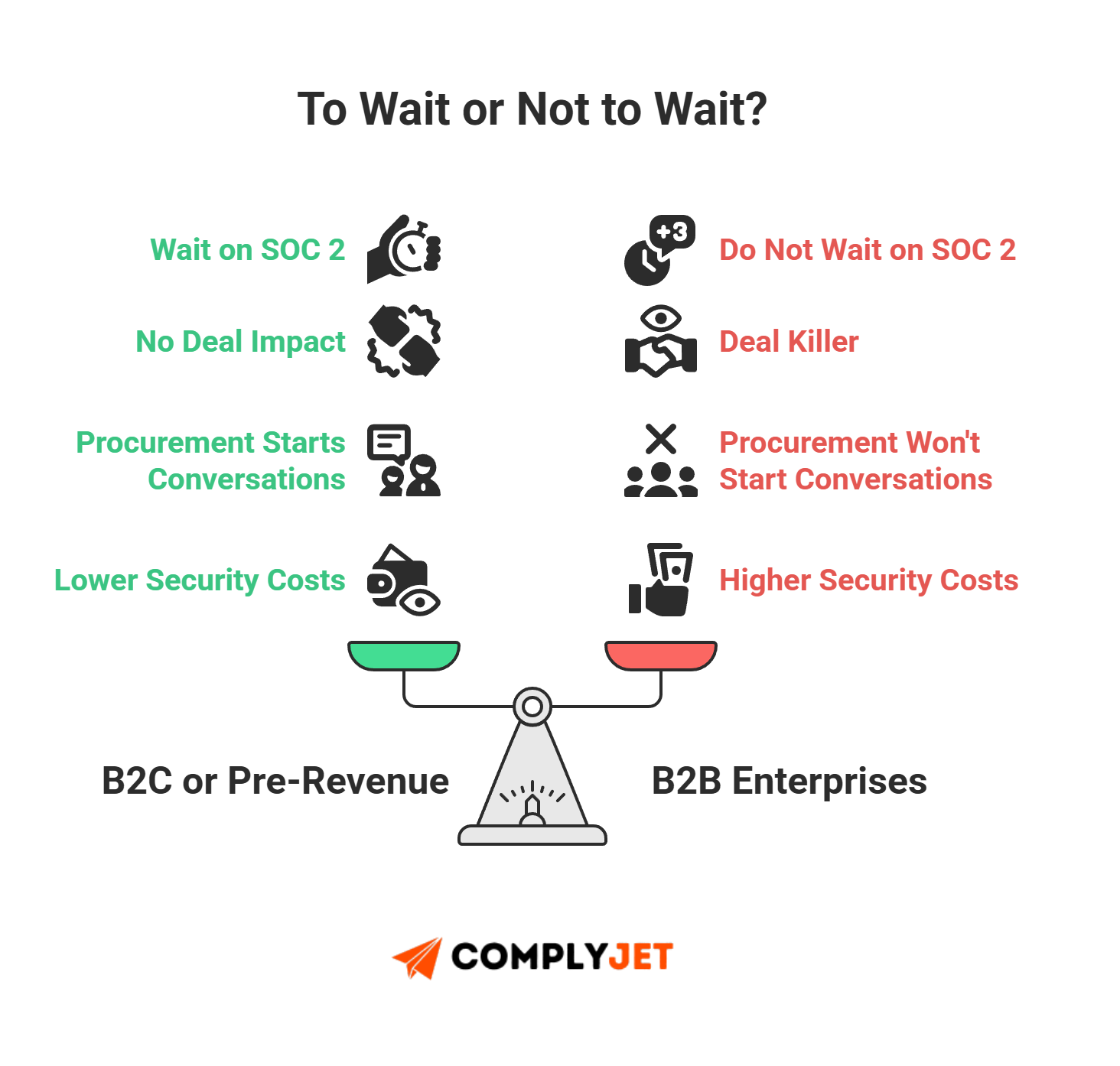
We are pre-Series A. Can we just wait?
You can wait only if you are strictly B2C or pre-revenue.
- The Sales Blocker: If you sell to B2B enterprises, lack of SOC 2 is a "deal killer." Procurement teams often won't even start the conversation without it.
- The "Tax" of Waiting: Trying to retrofit security controls after you've built a complex product is painful and expensive. Building "security by design" early is cheaper than refactoring your entire codebase later.
If you're tired of breaking the bank for your security needs, try ComplyJet. We offer transparent, cost-effective compliance solutions with a pricing structure that actually scales with you. Stop overpaying for rigid frameworks-get audit-ready faster with our affordable, high-utility automation tools.
Final Guidance
SOC 2 isn't passed by paperwork - it's passed by proof. Your SOC 2 controls must run consistently, tie back to purpose, and show execution through clean evidence. If every safeguard in your SOC 2 controls list has ownership, intent, approvals, and logs that meet SOC 2 documentation requirements, the audit stops being stressful and becomes a confirmation of discipline.
Keep controls lean, review them on schedule, treat evidence as operational hygiene, and let structure speak for you when auditors arrive. The teams that invest in clarity end up with security that lasts, not security that's just certified once.
Run your entire SOC 2 controls matrix, evidence, policies and audits on ComplyJet. Build controls, attach artifacts, track ownership, and stay audit-ready year-round without the spreadsheets or the anxiety. Book a demo to see how.



