Over 81% of data breaches are caused by weak or stolen passwords, according to the ZIPDO education report 2025.
That’s why auditors pay close attention to your ISO 27001 password policy - not just what it says on the document, but how it’s enforced in practice.
Imagine you’re only a week away from the audit. Everything’s going smoothly until the auditor pulls up your Azure AD settings and asks a simple question:
“Your policy says passwords expire after compromise only, but this shows forced 90-day rotation. Which one is actually enforced?”
You realised the policy was updated months ago. But the system wasn’t.
Result? The auditor marks it as a major non-conformity.
This is one of the most common reasons for ISO 27001 password-related audit failures.
In this article, you’ll learn everything about ISO 27001 password policy, what it is, implementation, password requirements, best practices, and common mistakes.
If you need personal guidance on implementing ISO 27001 password controls, our founders have helped companies pass their audits. Get guidance only if and when you need it.
Let’s break down the ISO 27001 password policy in detail
What Is An ISO 27001 Password Policy?
ISO/IEC defined ISO 27001 password policy as a documented set of rules governing how authentication information (like passwords, MFA, API keys, cryptographic keys and tokens) is created, stored, managed, and protected in alignment with Annex A.5.17 and your organisation’s risk assessment.
It’s the rulebook for how people prove they are who they say they are when accessing your systems.
The policy core idea is to protect the CIA triad -Confidentiality, Integrity, and Availability of information assets.
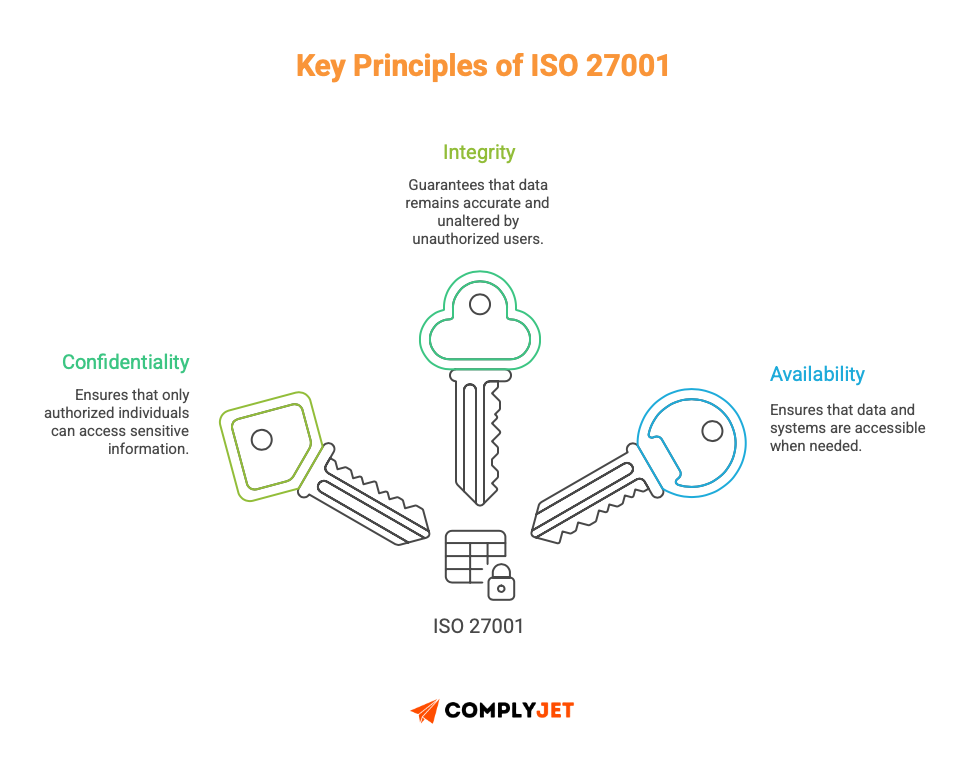
Your policy sits within the broader access control framework, connecting to user access management, identity verification, and information classification.
It’s not standalone, but it is intertwined with onboarding users, revoking access, and acting on security incidents.
ISO 27001:2022 Annex A 5.17 Control Explained
ISO 27001 uses Annex A.5.17 “authentication information” rather than just “passwords.”
The standard (iso 27001:2022 version) released 11 controls to cover everything used to verify identity:
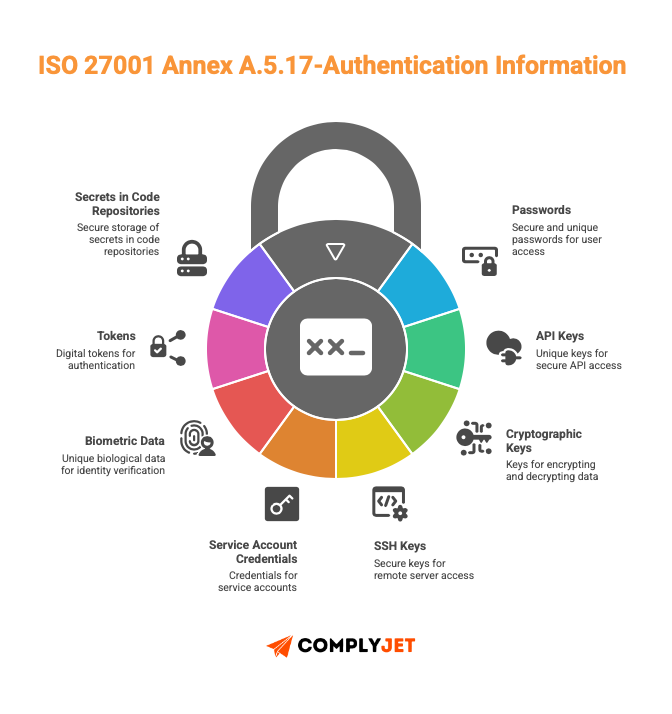
- Passwords
- API keys
- Cryptographic keys
- SSH keys
- Service account credentials
- Biometric data
- Tokens
- Secrets in code repositories.
The organisational control Annex A 5.17 is titled “Authentication information”: allocation and management of authentication information shall be controlled through a formal management process.
Here is what it doesn’t say: “passwords must be 15 characters with special symbols.”
The control then breaks down into specific attributes your process must address:
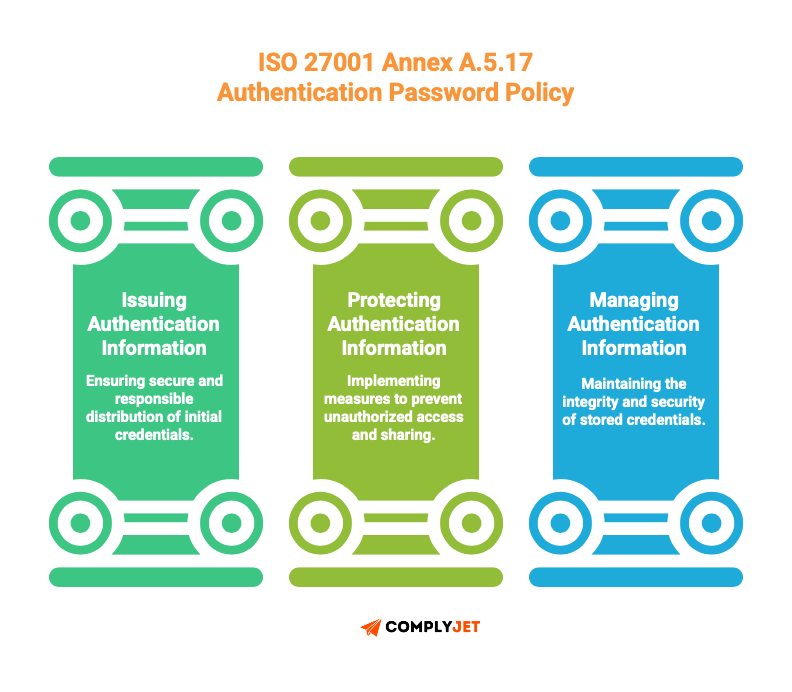
For issuing authentication information:
- Users must be required to sign a statement acknowledging their responsibilities for keeping authentication information confidential.
- Initial temporary passwords must be unique to individuals and not easily guessable.
- Users should be required to change temporary passwords on first use.
- Procedures must exist for verifying the identity of users before issuing new or replacement authentication information.
For protecting authentication information:
- Users must be instructed not to share individual authentication information.
- Users should avoid keeping records of passwords (unless stored securely via approved methods like password managers)
- When passwords are initially displayed or transmitted, they should be adequately protected.
- Default vendor passwords must be changed after system installation.
For managing authentication information:
- Systems must enforce technical controls to ensure quality authentication information (sufficient length, complexity where appropriate, not easily guessable)
- Procedures must exist for changing or updating authentication information.
- Compromised authentication information must be revoked and replaced immediately.
- Passwords stored in systems must be protected using cryptographic techniques.
Auditors look for three things in your password policy:
- Documented rules
- Technical enforcement
- Evidence of review
They want to see conscious decisions about authentication security based on your risk assessment.
For example, a healthcare startup with patient data will have different requirements than a marketing agency.
How Annex A 5.17 Connects to Other Controls
ISO 27001:2022 Annex A 5.17 doesn’t exist in isolation. It ties directly to:
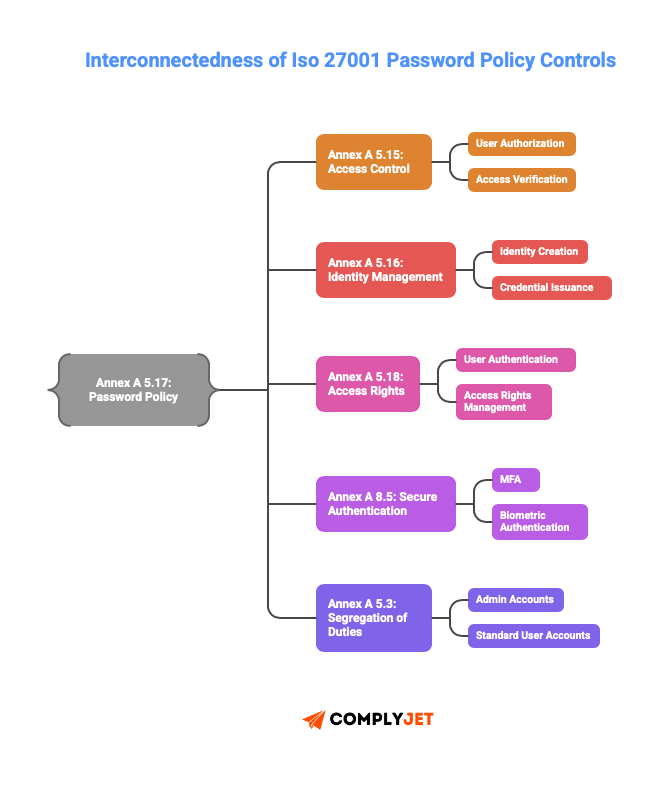
Annex A 5.15 (Access control): Your password policy is how you enforce access control. If A 5.15 requires user access to be authorized, A 5.17 is how you verify that the person requesting access is actually authorized.
Annex A 5.16 (Identity management): This control covers the full lifecycle of user identities. A 5.17 handles the authentication part of that lifecycle. When someone joins your company, A 5.16 governs creating their identity, and A 5.17 governs issuing their initial credentials.
Annex A 5.18 (Access rights): This control manages what users can do after they authenticate. A 5.17 ensures only authenticated users get to the point where access rights matter.
Annex A 8.5 (Secure authentication): This is the technical implementation control. While A 5.17 focuses on the management process, A 8.5 focuses on the technical mechanism – things like MFA, biometric authentication, and cryptographic protection of credentials.
Annex A 5.3 (Segregation of duties): Your password policy should reflect different requirements for different roles. Admin accounts need stronger authentication than standard user accounts. A 5.17 is where you document and enforce those differences.
ISO 27001 is risk-based, not prescriptive. Your password policy needs to align closely with asset management, because weak authentication will directly impact your crucial information assets.
The standard doesn’t mandate specific password lengths because different organizations face different risks.
For instance, your payment processing system needs stronger authentication than your employee parking portal.
ISO 27001 password policy expects you to determine what’s appropriate for your context, document it, implement it, and prove it works.
We have seen a SaaS company spend two months debating 12 vs 14-character passwords. They had a real risk of 23 joint team-level passwords to access production, and this was not covered in their policy at all.
They were not even discussing one of the controls and failed their audit.
Here’s the problem: Most teams treat password policy as paperwork, not a control. Write the requirements, approve them, and proceed. However, ISO 27001 auditors do not simply read your policy; they log into your systems and attempt to breach it. They generate test accounts using 6-character passwords in place of your 12-character minimum policy. They attempt to reuse old passwords. They check if they can disable MFA on privileged accounts.
ISO 27001 Password Requirements vs Password Best Practices
Let’s understand the ISO 27001 password requirements from what people think they require.
ISO 27001 Password Requirements: What the Standard Actually Expects
- You need a documented policy that addresses authentication information management.
The document must be approved, communicated, and accessible to the people who need it.
- Your policy must align with your risk assessment. If you’ve identified unauthorized access to financial systems as a high-impact risk, your policy needs to explain how authentication controls reduce that risk.
Auditors check this connection by pulling your risk register and reading it alongside your policy.
- You need technical enforcement. Your policy can’t say “passwords must be 10 characters” while your systems accept 6-character passwords.
The gap between documentation and reality is where audits fail.
- The policy has to be reviewed periodically. The ISO 27001 requires periodic review of controls.
The majority of organizations do the review once a year, but quarterly is a good idea when you are operating in fast-changing environments.
What ISO 27001 Password Policy Does NOT Require(Length, Rotation, Myths)
No definite password length is mandatory. ISO 27001 doesn’t say 8, 12, or 16 characters.
Mandatory rotation intervals aren’t required. The old “change passwords every 90 days” rule isn’t in ISO 27001. NIST now recommends against forced periodic rotation unless there’s evidence of compromise.
Specific complexity rules aren’t dictated. The standard doesn’t require uppercase, lowercase, numbers, or symbols.
ISO 27001 Best Practices That Auditors Actually Expect
When teams search for iso 27001 best practices, they usually expect a checklist. But here’s where auditors surprise them.
Auditors want risk-based decisions that are clearly documented, enforced, and reviewed, not a mere checklist. The practices below are the ones the auditors actually expect to see in real audits, not in theory.
- Passphrases instead of passwords: Eight random words generate more entropy than P@ssw0rd123! Organizations are moving to a minimum 15-character passphrases on sensitive systems.
- Multi-factor authentication (MFA): To allow access to privileged and remote servers. Though it does not make it obligatory, MFA on admin accounts is becoming a more regular expectation of the auditors.
In case your risk assessment identifies unauthorized access as a high-risk area and you are not employing MFA, you must justify it in writing.
- Password managers: Eliminate password reuse, which creates more risk than weak individual passwords.
Some organizations make the use of a password manager mandatory.
- Rotation after compromise: Not on schedules. Change passwords when there’s evidence of compromise, breach, or when someone with access leaves.
Key Elements of an ISO 27001 Password Requirement
Your iso 27001 password policy document needs these areas covered. But also read them along with the latest NIST guidelines for better implementation to skip last-minute audit failure surprises.
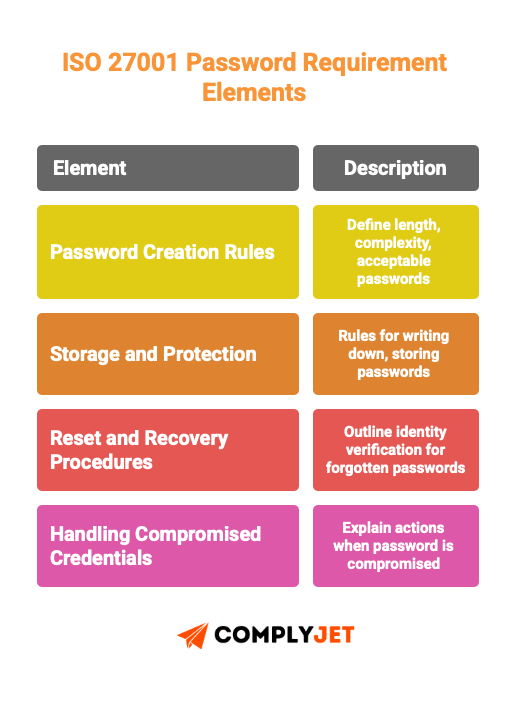
Password creation rules: Define minimum length, complexity requirements (if any), and what constitutes acceptable passwords.
Explain why these rules exist by referencing your risk assessment. If you require 12 characters for standard accounts but 16 for privileged accounts, document the rationale.
Storage and protection: Rules tell people what they can and cannot do. Can they write passwords down? Store them in browsers? Are password managers required or recommended? How should shared credentials be managed?
Reset and recovery procedures: Outline how someone proves their identity when they’ve forgotten their password.
Define what information helpdesk staff can request, what channels are acceptable for reset requests, and how you verify identity remotely.
Social engineering attacks target this process.
Handling compromised credentials: Explains what happens when a password is suspected or confirmed to be compromised. Who gets notified? How quickly must it change? What systems need checking for unauthorized access? Organizations fail audits when they have no documented process for this.
Third-party and contractor access: Needs specific attention. Do contractors use the same authentication standards as employees? How do you handle vendor access? What happens when a contractor’s engagement ends?
Manage the password requirements, and see the controls working in real-time with ComplyJet.
Step-by-Step Guide to Implement and Maintain ISO 27001 Password Policy
When implementing an ISO 27001 password policy, it isn’t about a single task of writing rules. It’s about building a system that aligns with Annex A 5.17, reduces real risk, and stands up during audits.
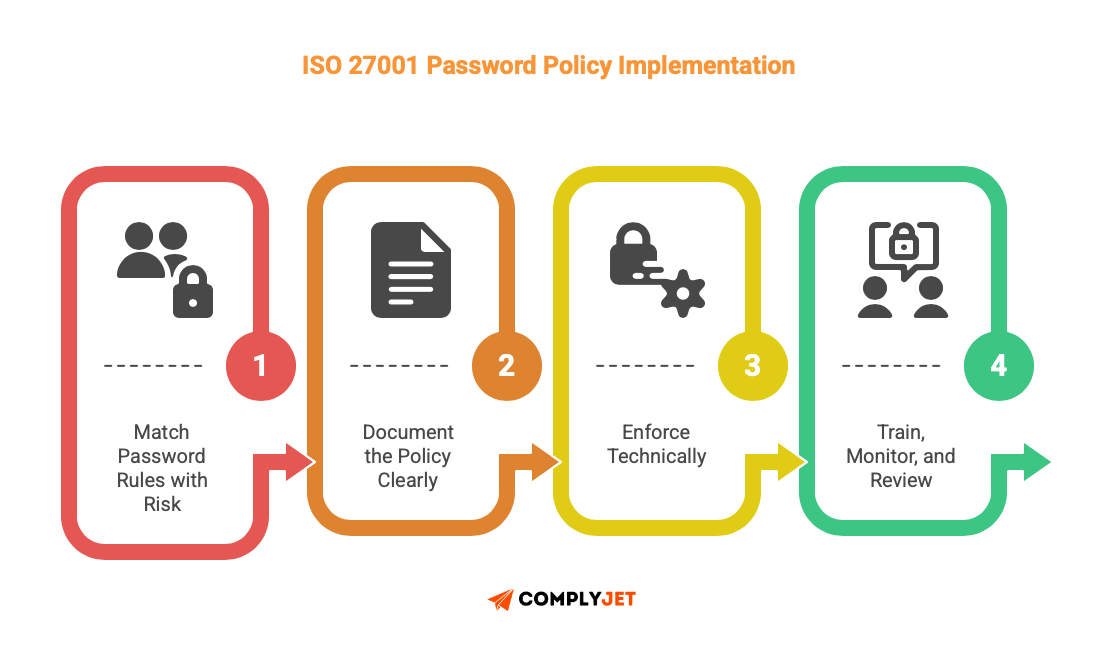
Step 1: Match the Password Rules With Risk
Start with your risk assessment. Consider every system and question: how is it affected when one gets unauthorized access?
- Critical systems: Anything touching customer data, financial information, or intellectual property should apply stronger controls. Longer passwords or passphrases, mandatory MFA, and stricter access logs.
- Privileged access: Utilise your best authentication measures. The accounts of the administration and root access, as well as service accounts with high permissions, require independent and more rigorous rules.
Test this: Pull 10 random privileged accounts and verify they follow your enhanced requirements.
Step 2: Document the Policy Clearly
Your password policy needs formal approval, version control, and communication to relevant personnel. Include:
- Scope (what systems and users it covers)
- Roles and responsibilities (who enforces it, who approves exceptions)
- Specific requirements
Make it readable by non-technical people. Your customer support team should understand what’s expected of them without decoding technical jargon.
Step 3: Enforce Technically
Your Active Directory, Okta, Azure AD, or identity management system must enforce your policy rules.
If your policy says 12-character minimum, someone should be unable to set an 11-character password. Test this yourself before the auditor does.
Use IAM and SSO to centralize authentication control. The more separate login systems you have, the more likely you’ll have enforcement gaps.
Check your AWS console, GitHub organization, customer support platform, and any SaaS tools with separate authentication.
Export a settings report from your directory services and place it next to your policy document. They should match. If they don’t, fix the mismatch.
Enforcement beats intention: A non-enforced policy is one that displays no control. Some of the testing performed by auditors includes the creation of weak passwords, the reuse of old passwords, and the disabling of MFA.
Step 4: Train, Monitor, and Review
Security awareness training should cover password requirements, how to use your password manager, what to do if they suspect compromise, and why credential sharing creates risk.
Monitor for policy violations. Check logs on failed log-ins, password reset trends and shared accounts.
Review your policy at least annually. Ask: Have our risks changed? Are our controls still effective? Have we had authentication-related incidents? What failed during the last audit? Use those answers to update your policy.
How Auditors Evaluate Your Password Policy (Evidence & Audit Traps)
When an auditor evaluates your A 5.17 implementation, here’s their process:
They start by reading your authentication information management policy. They check whether it’s been formally approved, whether it addresses all the attributes listed in the control, and whether it references your risk assessment.
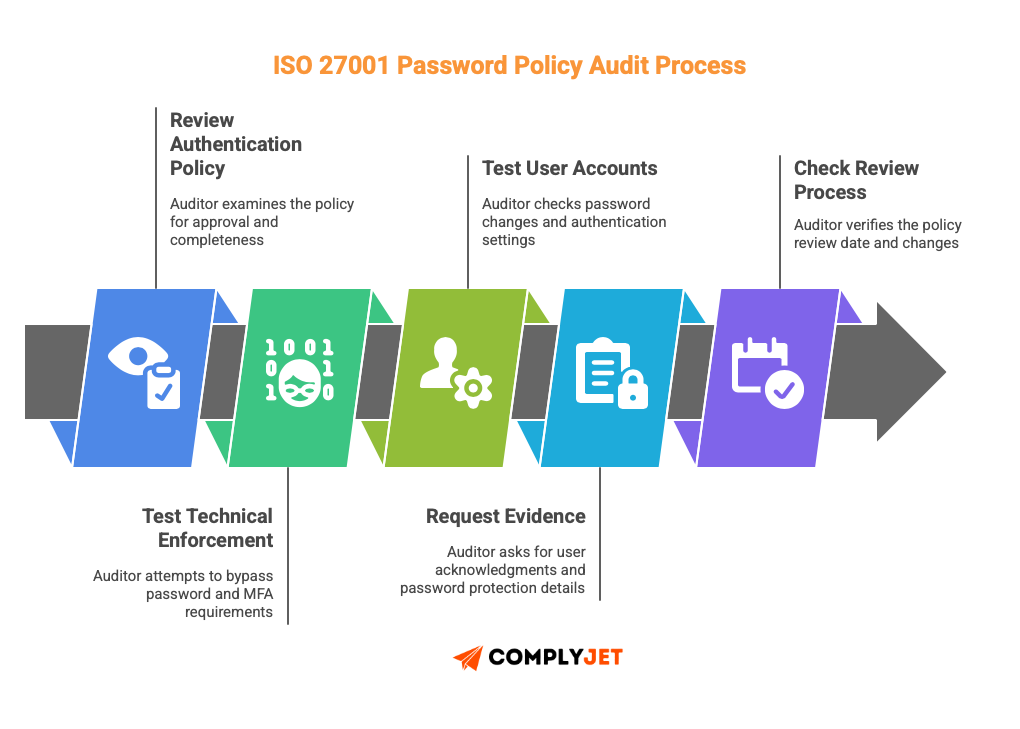
Then they test technical enforcement. They’ll ask for access to a non-production environment and attempt to:
- Create a password shorter than your stated minimum
- Reuse a recently used password
- Set a password that doesn’t meet your complexity requirements
- Disable MFA if your policy requires it
- Register an account without going through the identity check-up.
Test user accounts to check:
- On first use, initial temporary passwords were changed.
- The default passwords of vendors have been modified.
- Enhanced authentication is required on privileged accounts.
- In case of shared credentials, this is recorded with reasons.
Evidence auditors request:
- User acknowledgment of authentication responsibilities (signed statements or training records)
- Your process for handling compromised credentials
- Password reset procedures with identity verification steps
- How passwords are protected when transmitted or displayed
- Cryptographic protection of stored passwords
Checking the Review Process:
- When was the last date of policy review?
- What triggered the review?
- What changes were made based on incidents or risk assessment updates?
- Is there documented management approval of the current version?
When organisations ignore iso 27001 best practices like risk-based authentication, technical enforcement, and regular reviews, gaps appear between policy and reality, where auditors find them quickly.
Your iso 27001 password policy needs to address every method employees and systems use to authenticate. If you’re only thinking about passwords employees type into login screens, you’re missing what auditors will examine.
Common Mistakes Organisations Commit in ISO 27001 Password Policy:
What most organisations and teams fail to understand is that, during an audit, an auditor logs into a test environment and tries to create a password that violates the policy. The system accepts it.
That’s an immediate non-conformity.
For example, one organization had its policy set to 12 characters minimum, but its test environment was still set to 8. They didn’t consider test environments in scope, but the auditor did because they contained production data copies.
Policy vs system enforcement mismatch happens when IT updates the policy document but forgets to update Azure AD settings, or when new systems get deployed without applying password policy configurations.
Undocumented exceptions create violations. A VP has a weak password because “complex ones are hard to remember.”
That’s a violation unless you’ve documented it as an approved risk with compensating controls. Auditors sample user accounts and find these.
Shared credentials are likely to create issues. You need single-user accounts, but the auditor finds out that there are five people under the “admin” account of a vintage system.
In case you have to use common credentials, then put in writing the reasons, to whom the credentials were given, and what compensating controls you have taken.
Missing evidence of review fails audits even if you have a solid policy. Keep meeting minutes, approval emails, or a review log showing you examined the policy within the last 12 months.
The Real Cost of Weak ISO 27001 Password Policy
A weak password policy doesn’t just increase the risk of breaches; it quietly drives audit failures, incident cost, and lost trust. Here you can learn the hidden cost of weak policy.
Audit non-conformities delay certification. A minor non-conformity gives you 90 days to fix the issue and provide evidence.
A major non-conformity, like having no enforced password policy, means you won’t get certified until it’s resolved. That can take six months.
Certification delays have a business impact. If you’re closing an enterprise deal requiring ISO 27001, that deal gets paused.
Many teams identified this during certification discussions. In iso 27001 vs SOC 2, the real difference isn’t the paperwork; it’s that iso 27001 expects evidence that your password controls work in a real environment.
Increased breach impact is the actual risk. Weak authentication controls make breaches easier and more damaging.
When you have an incident, regulators and customers ask why your controls weren’t adequate. “We hadn't updated our policy” doesn’t hold up.
Operational disruption happens during remediation. You can not switch your password policy on and off when you realize it is not working.
You need to update systems, communicate changes to users, handle support tickets from locked-out users, and fix broken integrations that relied on weak shared passwords.
A manufacturing company had certification delayed because it couldn’t enforce password complexity on industrial control systems. They implemented a compensating control –network segmentation plus additional monitoring –which took three months and cost more than addressing it during initial implementation.
When teams reuse credentials, skip MFA, and review gaps, the real cost shows up in fines, downtime, and painful audit findings.
How Tools like ComplyJet Support ISO 27001 Password Compliance
Among all the compliance frameworks existing, ISO 27001 certifications give your company a globally recognised way of proving your commitment to safeguarding data & systems.
That’s why ISO 27001 isn’t a one-time achievement.
Your systems drift, policies get outdated, and audit-readiness deteriorates over time.
ComplyJet gives you visibility into control effectiveness between the audits.
For password policy, you can track when the policy was last reviewed, which systems have been validated for enforcement, and where gaps exist.
Evidence readiness implies that you’re not searching for documents when auditors ask. Policy documents, approval records, review logs, and evidence of technical enforcement stay organized in one place.
Continuous compliance support addresses the reality that your environment changes constantly. New systems get deployed, people join and leave, risks evolve.
ComplyJet helps you track these changes and assess their impact on your ISMS controls.
The platform won’t write your password policy; you still make risk-based decisions about what’s appropriate.
But it helps you maintain the discipline required to keep your ISMS effective between audit cycles.
FAQ’s
Does ISO 27001 mandate a specific password length?
No. ISO 27001 doesn’t specify a minimum password length. Your requirements should reflect your risk assessment.
Organizations typically use 12-16 characters for standard accounts and 16+ for privileged access, but base those choices on your risk profile.
Is password rotation required?
Not on a fixed schedule. ISO 27001 doesn’t require password changes every 90 days. Rotate passwords when there’s evidence of compromise, when someone with knowledge of the password leaves, or when your risk assessment indicates it’s necessary.
Is MFA mandatory for ISO 27001 certification?
ISO 27001 doesn’t explicitly mandate MFA. However, auditors increasingly expect it for privileged access and remote access.
If your risk assessment identifies unauthorized access as a significant risk and you’re not using MFA, you need a strong justification for why single-factor authentication is adequate.
Are password managers allowed under ISO 27001?
Yes. Password managers reduce password reuse, which is one of the biggest authentication vulnerabilities. Your policy should address password manager use –whether it’s required, recommended, which tools are approved, and how master passwords should be managed.
How often should the password policy be reviewed?
ISO 27001 requires periodic review at planned intervals. Most organizations review annually as part of their ISMS review cycle.
You might need more frequent reviews if you operate in rapidly changing environments, have experienced security incidents, or face evolving regulatory requirements.
Key Takeaways
Your ISO 27001 password policy isn’t about picking perfect password length or complexity rules.
It’s about demonstrating risk-based decisions about authentication, documenting those decisions clearly, enforcing them technically, and reviewing them regularly.
Organizations that are audited without a scramble are considered to take their password policy as a living control, and not a written policy that is written once and forgotten.
They also match policy to implementation on the very first day, maintain records of evidence and test their controls before the auditors.
In case you have an audit in the offing, ensure that what you have policy-wise is actually implemented by your technical systems.
Check every authentication point - employee access, contractor access, service accounts, API keys, and legacy systems. That’s where auditors look and where they’ll find problems.
Close the gap between your documented policy and your actual authentication controls before the auditor finds it.
Here’s the fact: Getting compliant isn’t complicated, but it requires attention to detail and honest assessment of where documentation and reality don’t match.
If you want practical feedback on your iso 27001 password policy implementation, we’re happy to walk through it with you.
Start a free trial with us today and cancel anytime!
.png)


