Thinking about getting SOC 2 Type 2 compliant but have zero clue where to begin (or just dreading the whole process)? You’re not alone.
In this guide, we’re cutting through the jargon and breaking down SOC 2 Type 2 in plain English. You’ll learn what it actually is, why it matters for your business, and how to get it done without burning out your team.
Whether you're a lean SaaS startup or scaling like crazy, we’ll walk you through the entire journey—prep, audit, reports, and keeping it all on track for the long haul.
By the end, you’ll know exactly what it takes to nail this audit and turn compliance into a business win (not a buzzkill).
Let’s get into it.
What Is SOC 2 Type 2 ?
Alright, let’s break this down.
SOC 2 Type 2 is basically a formal pat on the back from a third-party auditor saying, “Yep, this company doesn’t just talk about security—they actually do it, consistently, over time.”
It’s an attestation, not a certification—meaning a third-party auditor verifies your controls and vouches for how well they’re working, but there’s no official certifying body handing out gold stars.
This independent auditor CPA firm checks out your internal controls—things like how you handle access, data, incidents, etc.—and confirms they were not only set up correctly, but also ran smoothly and effectively over a period of 3 to 12 months.
This is a big deal if you’re storing or processing customer data in the cloud. SaaS? Fintech? Health-tech? Managed services? You need this report to prove you're serious about security and privacy.
You might also hear it called SOC Type II or SOC Type 2—yep, they’re all the same thing.
So… what about all the other SOCs?
If your brain short-circuits every time someone says “SOC 1” or “SOC 3,” you’re not alone.
Here’s the cheat code:
- SOC 1 = All about financial reporting. Think accounting systems, payroll, etc.
- SOC 2 = Focuses on trust principles like security, availability, and confidentiality. Aka, what most SaaS businesses care about.
- SOC 3 = Basically a high-level version of SOC 2 that you can publish publicly for bragging rights.
If you’re not dealing with someone else’s financial data, SOC 2 is the one you want.
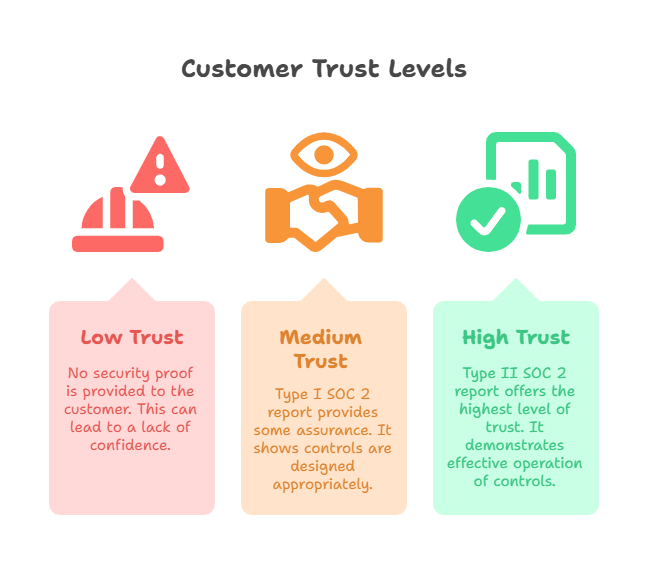
SOC 2 Type 1 vs SOC 2 Type 2: What’s the real difference?
Think of Type 1 like a snapshot—it checks if your controls are properly designed at a specific moment in time. It’s kind of like saying, “Cool, you’ve got smoke alarms installed.”
Now, Type 2 is the full movie. It says, “Not only do you have smoke alarms, but they’ve been working perfectly for months—and here’s the proof.” That’s why enterprise buyers care way more about Type 2.
Most companies start with a Type 1 to get their foot in the door (especially if you’re rushing to close a deal), then move to SOC 2 Type 2 once your controls are fully operational and humming along.
Why SOC 2 Type II Matters
If you’re wondering whether SOC 2 Type II is really worth the time, effort, and money—spoiler alert: it is.
Let’s break it down by the two biggest motivators—business growth and building trust.
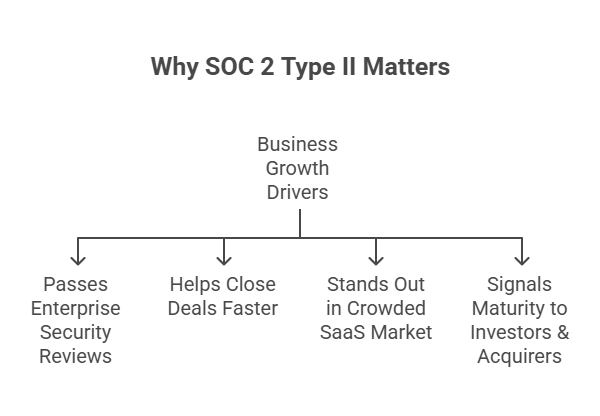
Business Drivers
First, let’s talk sales.
SOC Type 2 reports are often deal-breakers when you’re chasing enterprise customers. Security questionnaires, vendor risk reviews, and procurement red tape? All become a lot easier with that SOC 2 logo in your pocket.
It’s also a huge differentiator in saturated SaaS markets. When everyone claims to be “secure,” your SOC 2 Type II report is a verified proof point.
And don’t forget the internal crowd—your board, your investors, your future acquirer. They expect mature controls, not just good intentions.
Security & Trust Drivers
Now, let’s talk about reputation.
According to IBM’s Cost of a Data Breach report, the global average cost of a breach is $4.45 million. Ouch.
But SOC 2 Type II isn’t just about avoiding disaster. It’s about proactively showing customers you take security seriously.
This builds trust, strengthens your brand, and makes you the kind of company others want to do business with.
Who Needs a SOC 2 Type II ?
So, who actually needs to go through a SOC 2 Type II audit?
If you're handling customer data in the cloud, there's a good chance you're on the list. Here's exactly who should pay attention.
Cloud-Based and Tech-Heavy Companies
If you’re a SaaS platform, managed service provider, data center, fintech, or health-tech company—this is non-negotiable. You're dealing with sensitive information that customers expect you to protect.
When a Type I Just Isn’t Enough
Starting with a SOC 2 Type I makes sense when you’re just getting started. But once you're selling to larger enterprises, Type II becomes the new bar.
These customers won’t just take your word for it—they want proof that your controls actually work over time.
Regulatory or Contractual Requirements
Sometimes, you don’t even get a choice.
You may be required to provide a SOC Type 2 report under customer contracts, industry regulations, or partnership agreements.
Pro tip: Read your contracts closely—many contain language around ongoing security compliance or third-party attestation.
What’s Inside a SOC 2 Type II Report ?
So what’s actually inside a SOC 2 Type II report? Let’s unpack it section by section, starting with what auditors are evaluating.
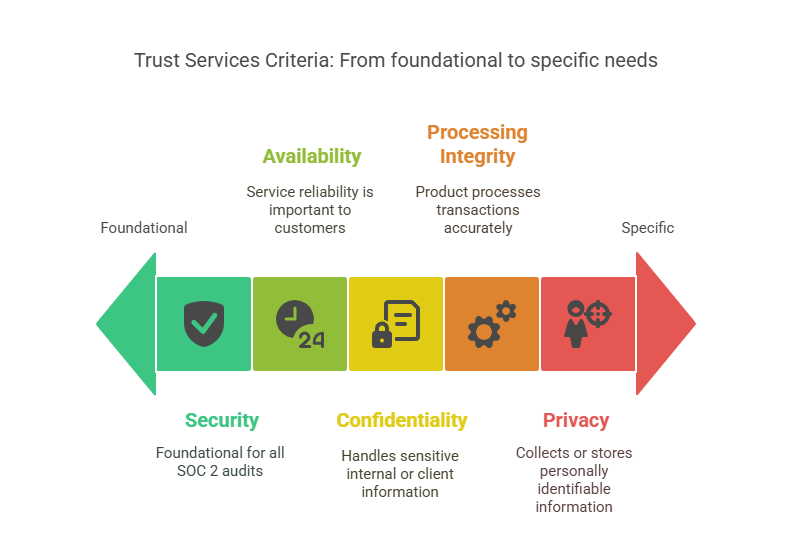
Trust Services Criteria & Scope
At the heart of your audit are the Trust Services Criteria (TSC)—the standards your controls are measured against.
Here’s the five you need to know:
- Security (mandatory): Protecting against unauthorized access.
- Availability: Ensuring your system is operational when promised.
- Processing Integrity: Making sure data is processed accurately.
- Confidentiality: Protecting sensitive data from exposure.
- Privacy: Properly collecting, storing, and disposing of personal information.
Most companies focus on Security plus one or two others, depending on customer expectations or industry needs.
Scoping tip: Be intentional. Define which TSCs apply, which systems are in scope (e.g. product infrastructure vs marketing site), and which locations or teams are involved.
Four Core Sections Auditors Deliver
Every SOC 2 Type II report includes four key parts:
- Management Assertion
Your company’s official statement about the controls in place and what was audited. - Independent Auditor’s Opinion
The main verdict. It says whether your controls were fairly presented and operated effectively during the audit period. - System Description
A detailed overview of your environment—people, processes, technologies, and data flows. - Tests of Controls & Results
The real meat of the report. It outlines each control, how it was tested, and whether it passed or failed.
Pro tip: This is what prospects and customers read most closely, so keep it tight and accurate.
How do you actually get this report? Let’s walk through the full audit journey.
The SOC 2 Type II Audit Journey
Getting a SOC 2 Type II report isn’t a one-and-done task—it’s a structured process that happens in four key stages. Here’s exactly what each one involves.
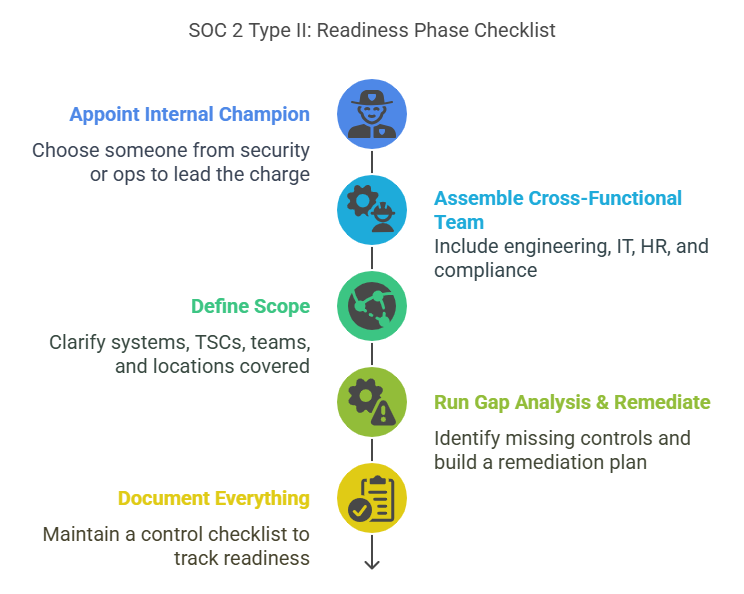
1. Preparation / Readiness
First things first—get your house in order.
Start by appointing an internal champion (often from security or ops) and assemble a cross-functional team. Think engineering, IT, HR, and compliance.
Next, define your scope. Which systems? Which Trust Services Criteria? Which teams and offices?
Run a gap analysis to identify missing controls, then build a remediation plan. This could include writing policies, tightening access, or implementing new tooling.
Finally, document everything. Create a control checklist to track what’s in place and what’s still in progress.
2. Fieldwork (Audit Window)
This is when the auditor steps in.
They’ll collect evidence—think screenshots, logs, tickets, and policy docs—to validate your controls. Some items will be sampled across the audit period (e.g., user access reviews every quarter).
Expect interviews with team members, especially around onboarding, incident response, and system monitoring.
Some firms perform real-time testing, while others review evidence retrospectively. Either way, your job is to show consistent control operation.
3. Reporting & Management Response
After fieldwork, you’ll receive a draft report. Review it closely.
If there are any exceptions (controls that failed or were inconsistently applied), you’ll have a chance to explain or remediate.
If the findings are serious, the auditor might issue a qualified opinion—which is like a partial thumbs-up. Not ideal, but not the end of the world either.
4. Continuous Compliance
Once you get your report, the clock starts ticking.
SOC 2 Type II reports are valid for 12 months, so you'll need to stay compliant year-round. That means setting up alerts and tools to monitor for drift—any changes that might affect your control environment.
Automation can help a ton here (more on that in a bit).
Next, let’s talk timing. How long does all of this actually take?
Timeline: How Long Does SOC 2 Type II Really Take?
Let’s be honest—SOC 2 Type II isn’t a weekend project. But with the right prep, it doesn’t have to drag on forever either.
Here’s a realistic look at how long you’ll need from start to finish.
Prep Phase: 4–12 Weeks
This stage includes defining your scope, running a gap analysis, implementing controls, and collecting documentation.
How fast this goes depends on:
- How mature your security processes already are
- How many teams need to be involved
- Whether you’re using automation or flying manual
Audit Window: 3–12 Months
This is the minimum period your controls need to operate effectively before an auditor can evaluate them.
Shorter windows (like 3 months) are common for first-time audits. Mature orgs often go for 6–12 months to show consistent control performance.
Pro tip: Choose a window that aligns with your sales cycles—so you can share your final report when prospects ask for it.
Factors That Can Speed (or Slow) Things Down
- Team size & focus: Fewer bottlenecks = faster progress.
- Number of TSCs: More criteria = more controls to prove.
- Tooling: Using compliance platforms can cut prep time in half.
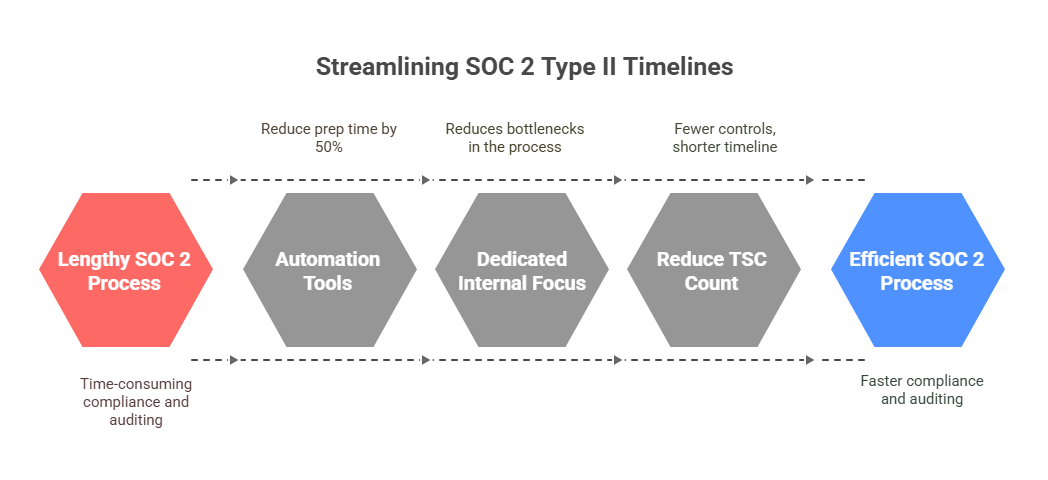
Now that you know the timeline, let’s break down what it’s going to cost you.
Cost Breakdown
Wondering what a SOC 2 Type II audit will cost? The short answer: it depends.
But here’s a breakdown so you can plan—and avoid budget surprises.
Auditor Fees: $10K–$60K
The biggest chunk goes to your auditor.
Prices vary based on:
- Company size
- Number of systems and locations in scope
- How many Trust Services Criteria you're being audited against
- Whether it’s your first audit or a renewal
Smaller startups might land around $10K–$20K. Larger or more complex orgs can easily hit $50K+.
Hidden Costs to Plan For
There’s more to the cost than just the audit fee.
- Readiness assessments (consultants or platforms): $5K–$15K+
- Internal team time: Expect 100–200+ hours across engineering, ops, and security
- Tools (e.g., policy templates, monitoring platforms): Varies by vendor
These add up fast—so budget beyond just the audit invoice.
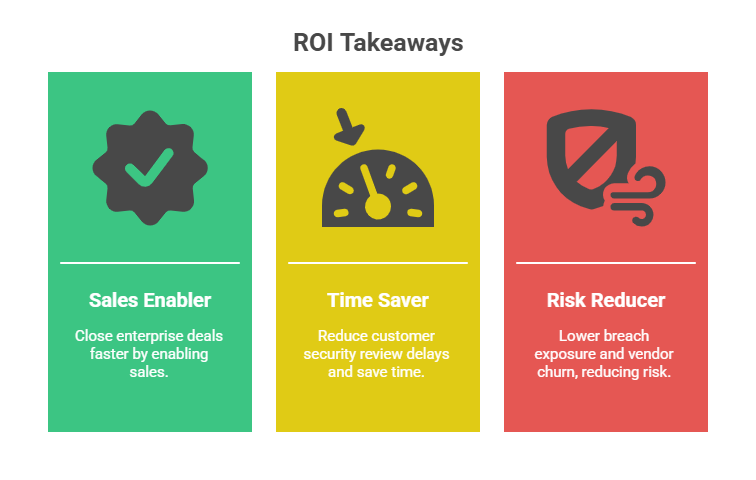
Budgeting Tips & ROI Talking Points
Here’s how to make the case:
- Sales enabler: SOC 2 Type II helps close enterprise deals faster
- Time saver: Reduces back-and-forth on customer security reviews
- Risk reducer: Helps avoid costly breaches or vendor churn
Now that we’ve covered the cost, let’s make sure you don’t stumble on common mistakes. Let’s dive into the pitfalls next.
Common Pitfalls & How to Avoid Them
Here’s the truth: even well-prepared teams can slip up during a SOC 2 Type II audit. But the good news? Most issues are totally avoidable.
Let’s break down the big ones—and how you can steer clear.
Under-Scoping Controls
Trying to keep the audit small? Makes sense—until the report comes back full of gaps.
If you leave critical systems or functions out of scope, you risk getting “exceptions” in your final report. These red flags can scare off potential customers.
What to do instead: Scope thoughtfully, not sparingly. Make sure your control environment actually covers what your business does.
Last-Minute Evidence Scramble
Nothing tanks a team’s morale faster than scrambling for screenshots, logs, or access reviews at the 11th hour.
Plus, it increases the chance you’ll miss something or send incomplete evidence.
Fix it: Assign control owners early and use a tracker or compliance tool to collect evidence as you go.
Overlooking Third-Party Controls
Got vendors handling critical systems or data? Your customers care about their security too.
For example, if AWS or a payroll provider is part of your operations, you’ll need to show how they protect your data.
Action step: Maintain a third-party risk register and gather SOC reports or security attestations from key vendors.
Cultural Resistance to Process
Let’s be real—audits can bring friction. Engineers hate documentation. Teams ignore new policies. It’s normal.
But if your culture resists change, controls won’t stick—and your audit results will reflect that.
Tip: Communicate the “why” behind each policy. Make compliance part of onboarding, not an afterthought.
Now let’s look at how automation can turn this whole process from painful to powerful. Ready?
Leveraging Automation for Faster SOC 2 Type II
Here’s the secret sauce to surviving (and even thriving in) your SOC 2 Type II journey: automation.
Done right, it can save you months of prep, eliminate human error, and keep your controls humming all year long.
Continuous Control Monitoring
Instead of manually checking if controls are in place, use tools that track them 24/7.
Think dashboards that alert you when something drifts—like a user who still has admin access after leaving the company.
Pro tip: Set up automated alerts and dashboards to monitor critical systems in real time.
Automated Evidence Collection
Forget digging through old emails and Slack messages for screenshots.
Modern compliance platforms plug directly into your stack—GitHub, AWS, HR tools, ticketing systems—and auto-pull the evidence auditors need.
Examples:
- Code repo changes (GitHub)
- IAM policy reviews (AWS)
- Onboarding/offboarding logs (HRIS)
This reduces errors and saves your team hours.
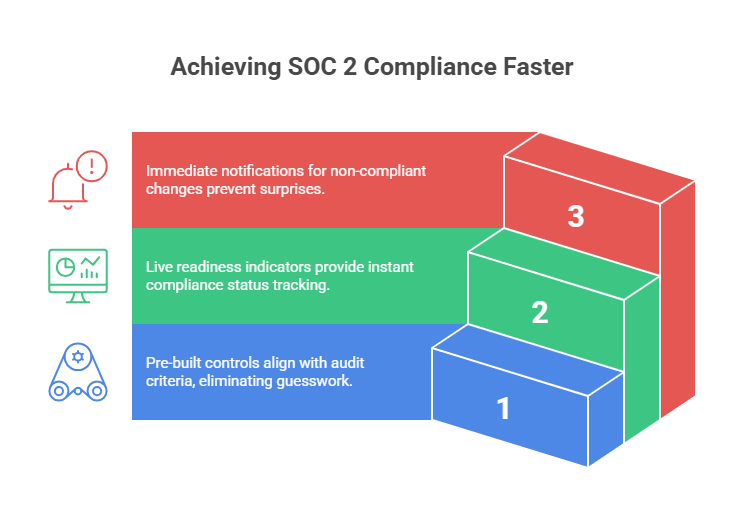
Cut Your Prep Time in Half
Tools like ComplyJet or other GRC platforms can cut your SOC 2 readiness time by 50% or more.

They provide:
- Control templates mapped to TSCs
- Real-time dashboards
- Auto-alerts for non-compliant changes
Mapping SOC 2 Type II to Other Frameworks
So you’ve nailed your SOC 2 Type II—nice work. Now you’re probably wondering: can we reuse any of this effort for other frameworks?
Short answer? Absolutely. And if you’re aiming to expand globally or level up your security maturity, ISO 27001 is the logical next step.
SOC 2 Type II vs ISO 27001
Both SOC 2 and ISO 27001 focus on how you protect data—but they do it in slightly different ways.
SOC 2 Type II is all about showing that your security and operational controls are running effectively over time. It's an attestation, meaning an independent auditor checks your systems and gives you a thumbs-up if everything’s solid. It's most common in the U.S., especially for SaaS and cloud-native companies.
ISO 27001, on the other hand, is a formal certification. It’s globally recognized and focuses on building and maintaining a full Information Security Management System (ISMS)—a structured, repeatable way to manage risk and protect information across your organization.
If you're selling internationally or to larger enterprises, ISO 27001 can open doors SOC 2 can't.
Reuse What You've Built
Here’s the good news: a lot of your SOC 2 controls can carry over into your ISO 27001 journey.
For example:
- Your access controls, incident response plans, and data protection measures? Already relevant.
- Your policies and documentation? Probably 70% there.
- Your team’s security mindset? That’s the foundation of both.
Many companies start with SOC 2, then roll that momentum into ISO 27001 certification.
Pro tip: Use a compliance platform that supports both frameworks—so you can map, track, and manage everything in one place.
Best‑Practice Checklist
Want to crush your SOC 2 Type II audit without the stress? Start with this simple 10-point checklist.
Copy, paste, and customize it to your team’s workflow. This isn’t just busywork—it’s your SOC 2 controls game plan.
SOC 2 Type II Prep Checklist
- Define your audit scope (TSCs, systems, teams, locations).
- Assign a compliance lead and build a cross-functional team.
- Run a gap analysis using a readiness tool or consultant.
- Document all required policies (access control, incident response, etc.).
- Map controls to Trust Services Criteria with clear ownership.
- Set up continuous monitoring for critical systems and user access.
- Automate evidence collection with integrations (AWS, GitHub, HRIS, etc.).
- Conduct regular internal audits or walkthroughs before fieldwork.
- Keep a third-party vendor risk register with updated security reports.
- Create a compliance calendar for ongoing audits, reviews, and renewals.
Frequently Asked Questions
Still have questions about SOC 2 Type II? You’re not alone.
Here are the answers to the ones we hear the most:
How often do I need a SOC 2 Type II?
Every 12 months. SOC 2 Type II reports are valid for a year, so you’ll need to renew annually to stay compliant—and keep customers happy.
Can startups skip Type I?
Technically, yes. But most early-stage companies start with SOC 2 Type I to show initial intent, then follow up with SOC Type II once controls are operating over time.
Does SOC 2 Type II equal certification?
Nope. It’s an attestation, not a certification. That means an independent CPA firm has reviewed and verified your controls—but there’s no official certifying body like ISO.
What if my controls change mid-audit?
That’s okay—as long as the changes are documented and controls still meet requirements.
But big shifts (like migrating infrastructure) can complicate the audit. Best to time those moves outside your audit window if possible.
Conclusion
Let’s be real—SOC 2 Type II can feel like a beast. But it doesn’t have to be.
This isn’t just about passing an audit. It’s about showing the world you take security seriously. It’s your fast-track to unlocking enterprise deals, standing out in a crowded SaaS market, and building real trust with customers.
And the best part? You don’t have to figure it all out alone.
ComplyJet uses a mix of smart AI and real compliance experts to help B2B SaaS startups get SOC 2 Type II ready in just 7 days. Yep—seven days from “we should probably do this” to “we’ve got a game plan.”
You get automation where it counts (evidence collection, control tracking, reminders), plus real humans to guide you through every step. No guesswork. No jargon overload. Just clarity and speed.
Let’s turn SOC 2 from a blocker into a badge of trust—faster than you ever thought possible.
.png)


