SOC 2 can feel like a maze.
Between confusing acronyms, strict audit requirements, and a million moving parts, it’s easy to feel overwhelmed. But here’s the good news: with the right roadmap, getting SOC 2 compliant doesn’t have to be painful.
Whether you’re a seed-stage startup trying to win your first enterprise deal, or a fast-growing SaaS company preparing for due diligence, this SOC 2 compliance checklist will help you tackle every step with confidence.
We’ve broken it down into 10 clear, actionable phases, so you know exactly what to do, when to do it, and why it matters.
But before we dive into the full SOC 2 audit checklist, let’s quickly cover the basics of what SOC 2 is and why it’s such a big deal in 2025.
SOC 2 in a Nutshell
Framework Basics
So, what even is SOC 2?
In simple terms, SOC 2 is a security framework created by the AICPA that helps tech companies prove they're protecting customer data properly.
If you deal with sensitive customer data (think: SaaS apps, cloud services, fintech), customers will expect you to have it.
SOC 2 revolves around five key Trust Services Criteria (TSC):
- Security (mandatory): This is the core focus. Think firewalls, access controls, and incident response.
- Availability: Ensures your system is reliably up and running.
- Processing Integrity: Confirms your system processes data accurately and as intended.
- Confidentiality: Focuses on restricting access to sensitive information.
- Privacy: Covers how personal data is collected, used, and disposed of.
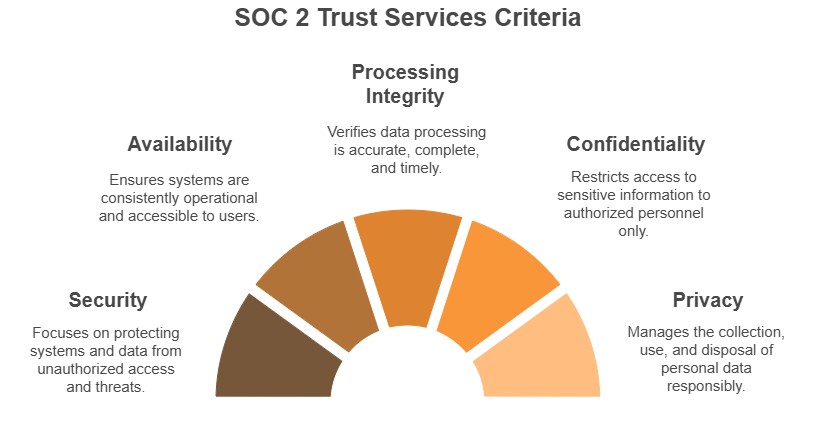
Each of these pillars maps to real-life risks. The more trust criteria you cover, the stronger your SOC 2 compliance checklist becomes.
Report Types
Here’s the deal: not all SOC 2 reports are created equal.
- Type 1 looks at the design of your controls at a single point in time.
- Type 2 evaluates how well those controls actually operate over a period (usually 3–12 months).
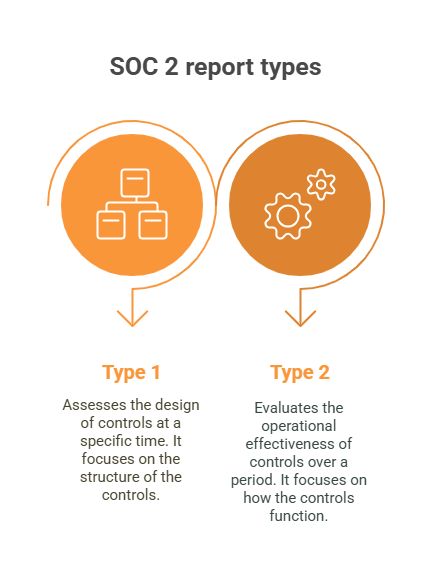
Now which one should you choose?
👉 If you're early in your security journey or under tight timelines, start with Type 1.
👉 If you're already running strong controls and want to impress enterprise clients, go straight to Type 2.
And yes, this choice impacts your entire SOC2 audit checklist, so choose wisely.
Pro-tip: A Type 1 report is often used as a stepping stone—companies use it to get quick validation, then upgrade to Type 2 as controls mature.
SOC 2 Compliance Checklist
Here’s your 10-step SOC 2 compliance checklist for 2025.

1. Define Objectives & Business Drivers
Start with why.
Ask yourself: Are you chasing enterprise deals? Expanding into regulated markets? Or simply tightening your risk posture?
Next, align these goals with revenue-impacting priorities. For example, “We need SOC 2 to close deals with fintech clients” is a clearer driver than “We just want to be compliant.”
2. Choose Your Report Type
Here’s where strategy comes in.
Factor in your sales timeline, how mature your internal controls are, and your available budget.
Use a simple decision tree:
- New to compliance? Start with Type 1.
- Need credibility fast or already running controls? Go directly for Type 2.
3. Scope the Audit
Now it’s time to zoom in.
List every product, service, cloud account, and vendor that touches customer data. That’s your in-scope universe.
Then, create data-flow diagrams to show exactly how customer info moves through your system. This helps auditors—and your team—spot security risks early.
Remember: Security is mandatory. But depending on your business model, you might also include Availability, Confidentiality, and Privacy in your scope.
4. Assemble a Cross-Functional Compliance Team
This isn’t a solo mission.
You’ll need buy-in from across the company. Here’s the dream team:
- Executive Sponsor
- Compliance or GRC Lead
- Security/IT
- Engineering
- HR
- Legal
Map roles clearly using a RACI matrix—who’s Responsible, Accountable, Consulted, and Informed.
5. Decide Your Execution Model
Manual or automated? That’s the question.
Manual = spreadsheets, Jira tickets, and lots of human effort.
Automated = compliance platforms that monitor and gather evidence 24/7.
Consider the trade-offs:
- Manual = cheaper short-term, slower, error-prone
- Automated = faster, more reliable, higher upfront cost
6. Identify Internal Controls
Time to build the backbone of your SOC 2 posture.
Map each Trust Services Criteria to concrete controls in your environment. Think of these as guardrails that prove you're protecting customer data the right way.
Here are some typical control examples:
- Security: MFA enabled for all employees
- Change Management: Ticketing system for code and infrastructure updates
- Vendor Risk: Formal process for reviewing third-party vendors
The key is to document each control clearly—what it is, why it exists, and how it’s monitored.
7. Implement Internal Controls
Now, it’s go-time.
Roll out internal policies across teams, configure tools like identity providers and logging systems, and train employees on security best practices.
Pilot your controls in real scenarios. Run through onboarding/offboarding flows, simulate incidents, and review logs.
Find gaps early—before your auditor does.
Once things are working smoothly, lock in your audit timeline.
8. Gather Evidence
This is where things can get messy—unless you prepare well.
You’ll need to collect evidence that proves each control is working. This includes:
- System screenshots
- Policy documents
- Security logs
- Penetration test reports
- HR onboarding/offboarding artifacts
Pro tip: Automate this wherever possible. Tools like ComplyJet pull evidence from your systems in real time, which saves you hours (and stress).
9. Select an Independent Auditor
Choose your CPA firm carefully.
Look for:
- Deep experience in IT audits
- Familiarity with your industry (SaaS, fintech, healthcare, etc.)
- A platform like ComplyJet which offers an automation-first approach for under $4999/year, giving you built-in SOC 2 controls, ready-to-use policy templates, continuous monitoring, and an exclusive AI assistance without the usual complexity of large enterprise systems. Start our Free Trial today!
Auditor fit matters. A good one will guide, not grill. A bad one? Endless back-and-forth.
Make sure they can flex to your timeline and audit scope.
10. Engage with Auditor & Complete the Audit
Let the audit begin.
Kick things off with an intro call. Then, walk them through your systems and controls. Expect sampling requests (e.g. “show onboarding logs for these 3 hires”) and lots of clarifications.
Keep the convo open. If they flag gaps, fix them quickly and update your documentation.
Once everything checks out, they’ll issue your SOC 2 report, starting with a draft, then the final version after your sign-off.
Congrats! You made it through the full SOC 2 audit checklist.
Conclusion
Let’s be clear: SOC 2 is not a compliance badge but a growth accelerator.
It shows customers, investors, and partners that you take data security seriously. And in today’s market, that’s a competitive edge.
Let this SOC 2 checklist be your launchpad.
.png)


