Ever wondered what that “SOC 2 Type 1” badge really means and why everyone suddenly expects you to have it?
Here’s the scoop: SOC 2 Type 1 is a snapshot audit that verifies your security controls are designed properly at a single moment in time. It doesn’t just say, “We care about security.” It proves you’ve built the right foundation.
And in 2025? It’s not optional. Buyers, especially the big ones, want that proof before they even talk about contracts.
In this guide, we’ll break down exactly what SOC 2 Type 1 is, why it matters, who needs it, how to get it, and how to avoid the common traps. Think of it as your fast-track manual to winning trust and speeding up deals.

What Is SOC 2 Type 1?
Let’s clear the air!
SOC reports can be confusing. SOC 1, SOC 2, SOC 3… what’s the difference, and where does Type 1 fit in?
Let’s start with a quick clarity check.
- SOC 1 is all about financial reporting controls. If you're a payroll processor or deal with clients' financial data, this is your lane.
- SOC 2 is what you care about. It focuses on how you protect customer data focusing on security, privacy, availability, and all that good stuff.
- SOC 3 is basically SOC 2’s PR-friendly cousin. Same principles, but no gritty technical detail. Just a public badge.
So let’s focus on SOC 2, because that’s what buyers, investors, and enterprise clients want to see from SaaS platforms, cloud tools, and IT service providers.
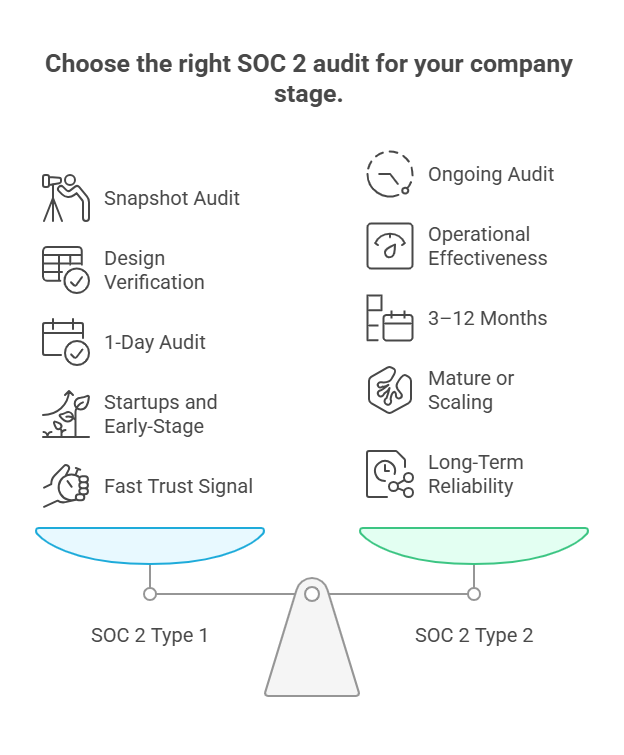
Now here’s where it splits: SOC 2 Type 1 vs SOC 2 Type 2.
- Type 1 is your starting point. It’s a point-in-time audit that checks whether your security controls are designed correctly. Think of it like a blueprint review, “are the right protections in place today?”
- Type 2 goes deeper. It monitors those same controls over 3 to 12 months to make sure they actually work consistently. It’s the real-world performance check.
If you're just getting started or need to prove your security posture fast, SOC 2 Type 1 is your best first step. It’s quicker, cheaper, and opens doors with buyers who need assurance that you’re on the right path.
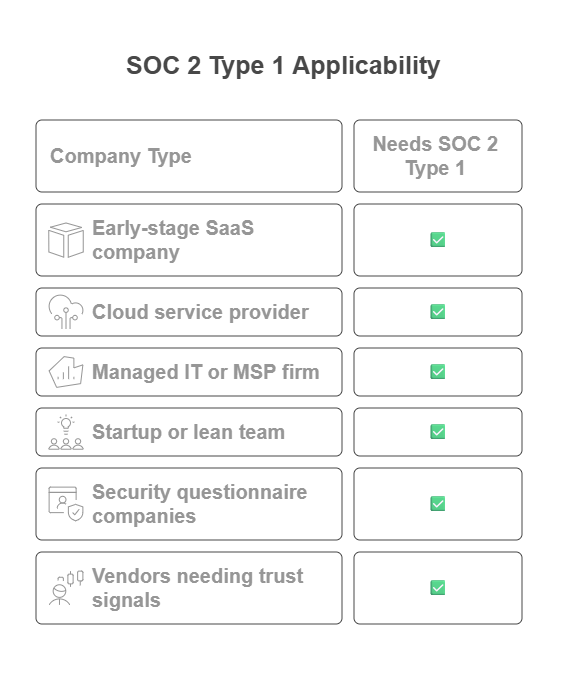
Who Needs SOC 2 Type 1 ?
If you're handling customer data and looking to earn trust quickly, SOC 2 Type 1 is for you.
First, if you're an early-stage SaaS company, this is your fastest way to prove to prospects that you're serious about security, without waiting months for a Type 2.
Next, cloud service providers and managed IT firms rely on SOC 2 Type 1 to show that their infrastructure and systems are built on secure foundations.
If you're getting hammered with enterprise security questionnaires or facing a deal-breaker without an attestation, this report can be your shortcut to the "approved vendor" list.
And for startups or lean teams on a budget, SOC II Type 1 gives you credibility without the time and cost commitment of a full Type 2 cycle.
Bottom line: if customer trust and data security are critical to your growth, you probably need it
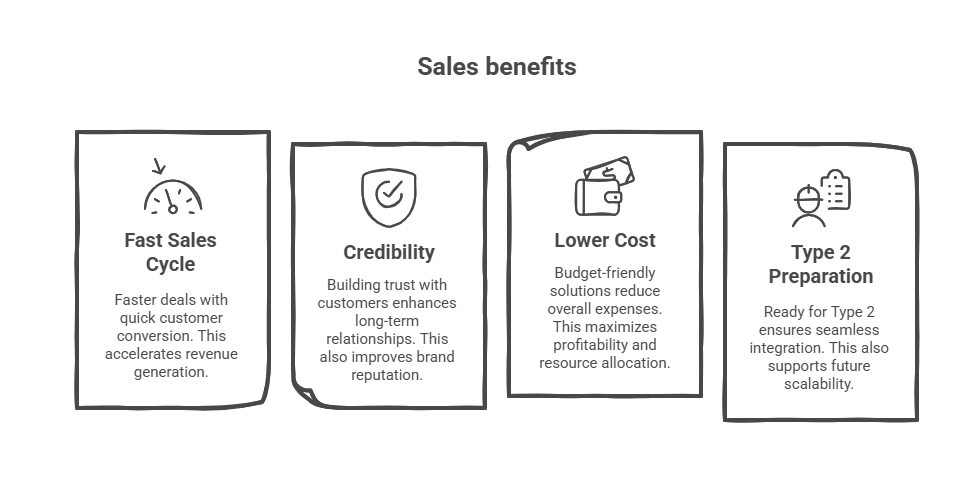
Key Benefits of Achieving SOC 2 Type 1
SOC 2 Type 1 actually helps you move faster and build trust.
First, it can speed up your sales cycle by clearing those pesky infosec reviews early. When a buyer sees you’ve passed SOC 2 Type 1, they ask fewer questions.
Second, it gives you a competitive edge. It’s a clear signal to buyers and partners that your company takes data protection seriously even if you're small or just starting out.
Third, it’s way more affordable than a full-blown SOC 2 Type 2. If you’re watching your budget, this is the smart first step.
And finally, it's the perfect trial run. You get to test your policies, controls, and processes, so by the time you go for Type 2, you're way ahead of the curve.
What Exactly Do You Need to Get a SOC 2 Type 1 Report?
So, you're sold on getting SOC 2 Type 1, but what do you actually have to do to get that shiny report?
Let’s break it down.
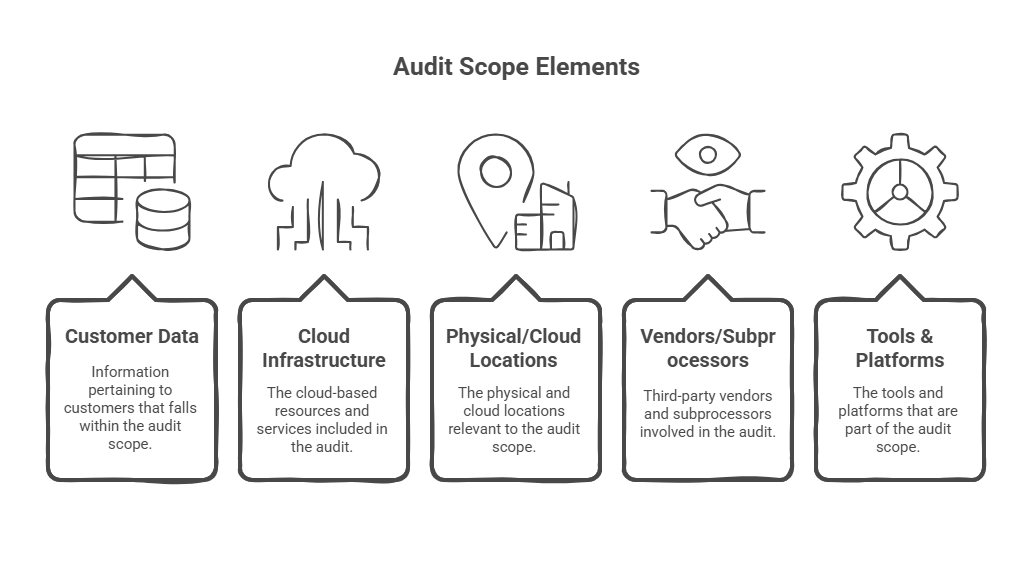
1. Define the Scope of Your Audit
Before anything else, figure out what you're actually getting audited on. This means clearly defining your audit scope:
- Which systems store, process, or transmit customer data?
- What infrastructure (cloud services, databases, tools) supports those systems?
- Which physical or cloud locations are involved?
- Which vendors or subprocessors have access to sensitive data?
Your scope determines how big and complex the audit is. Keep it tight. More systems = more controls = more evidence = more cost
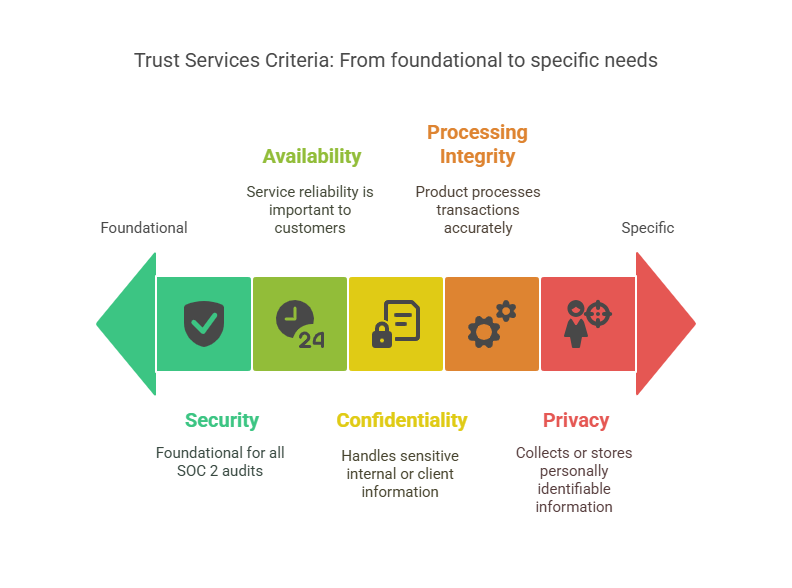
2. Choose Your Trust Services Criteria (TSCs)
All SOC 2 audits revolve around the Trust Services Criteria framework. There are five:
- Security (required)
- Availability
- Confidentiality
- Processing Integrity
- Privacy
You must include Security. The others are optional. Add them only if they’re relevant to your product, service commitments, or customer expectations.
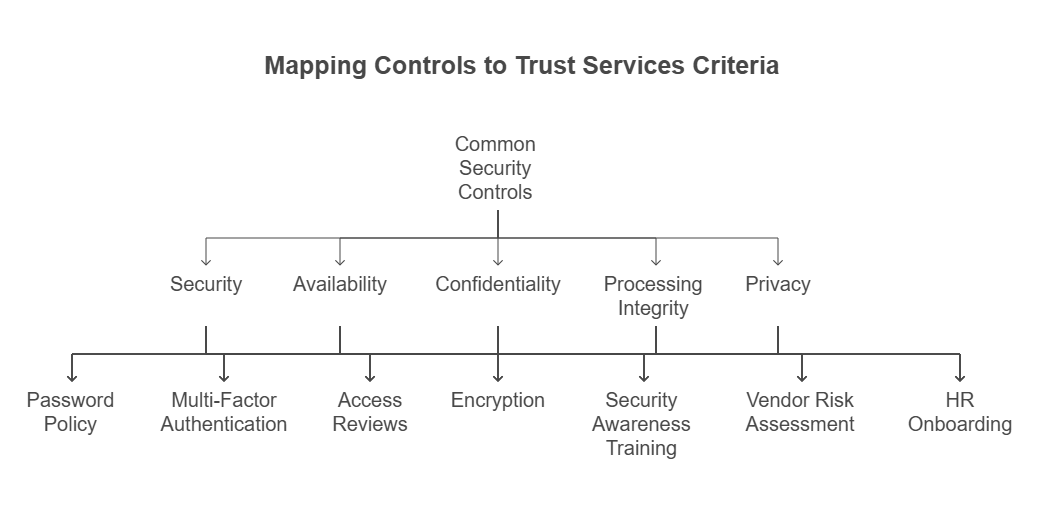
3. Define and Map Your Controls
Now that your scope and TSCs are clear, it’s time to design your controls these are the specific actions, systems, and policies that meet the criteria.
Here’s the catch: the AICPA doesn’t give you a list. You have to define your own.
Here’s how to do it:
- Choose 40–50 baseline controls that align with the TSCs you selected.
- Map each control to a specific TSC - for example, your password policy maps to “Security.”
- Controls can cover things like MFA, encryption, access reviews, training, HR onboarding, and vendor risk assessments.
🛠️ Pro tip: Use a readiness platform like Vanta or ComplyJet - they come pre-loaded with control libraries to help you hit the ground running.
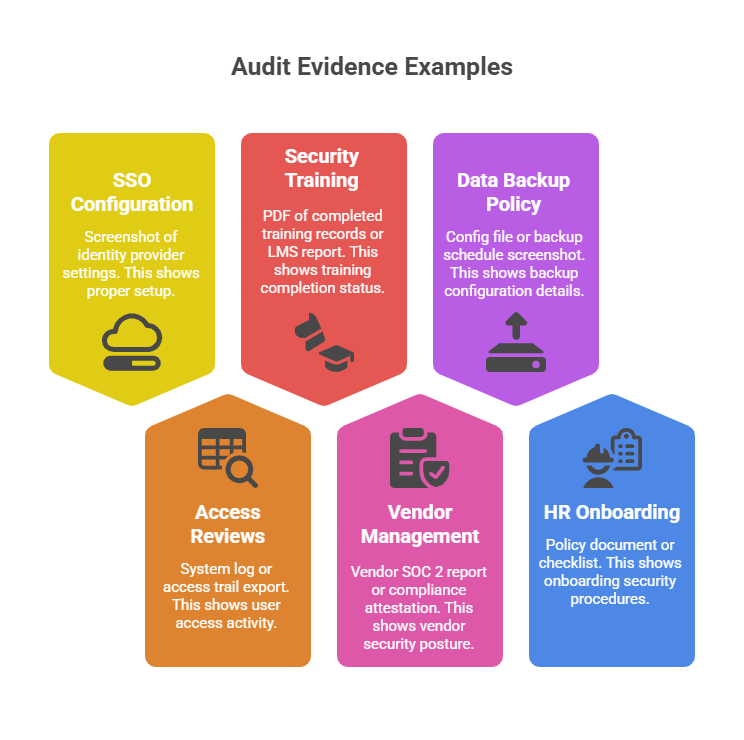
4. Collect Evidence to Prove Your Controls Exist
Auditors don’t just take your word for it - they want proof.
For each control, gather evidence that shows it’s been implemented. This could be:
- Screenshots of tools (e.g., Google Workspace admin panel)
- System logs (e.g., access logs, audit trails)
- Config files or settings (e.g., SSO, backups)
- Policy docs (e.g., onboarding, security training)
- Vendor compliance reports (e.g., their own SOC 2)
Don’t wait until audit week - collect and organize as you go.
5. Engage a SOC 2 Auditor
Once you’re confident in your controls and evidence, reach out to an AICPA-certified auditor (a CPA firm with SOC 2 experience).
They’ll:
- Interview your team
- Review all your control documentation
- Ask for evidence or clarifications
- Issue your official SOC 2 Type 1 report within a couple of weeks
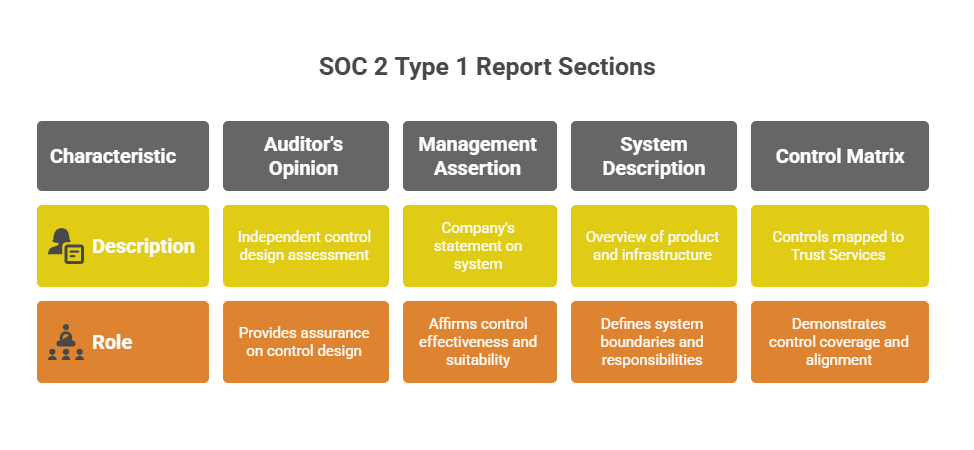
The report includes:
- Auditor’s opinion
- Management assertion
- System description
- Control matrix with mapped criteria
Audit Process for SOC 2 Type 1
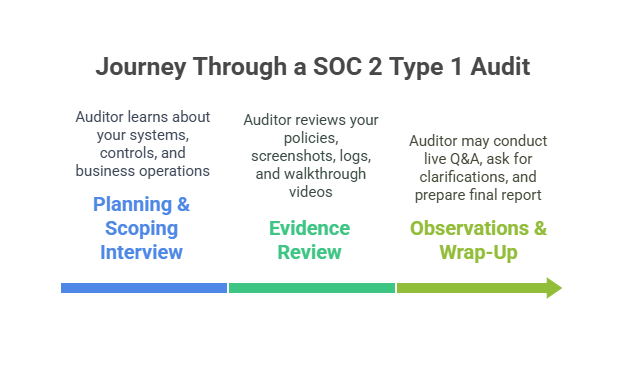
Here’s what to expect once your audit officially kicks off:
First, there’s a planning and scoping interview. The auditor will ask about your systems, controls, and business operations to understand your environment.
Next, they’ll review evidence - think policies, screenshots, logs, and walkthrough videos. You’ll need to show that your controls exist and are designed properly.
Depending on your setup, there might be on-site or remote observations. The auditor may ask questions in real time and request clarifications or additional documentation.
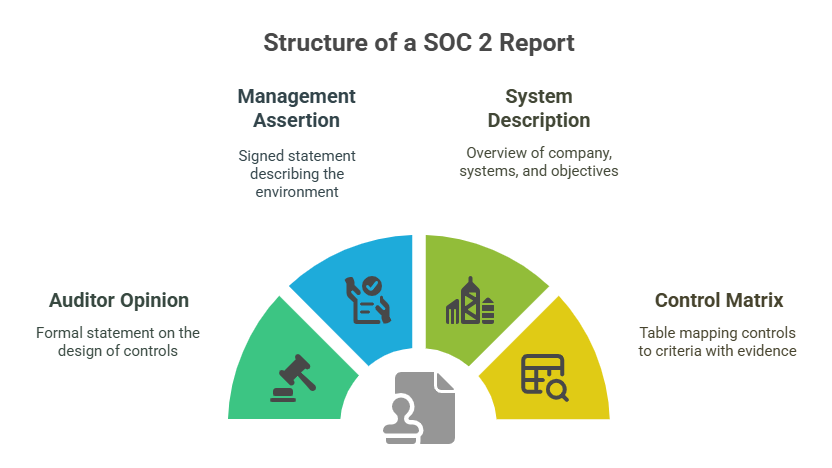
Your final SOC 2 Type 1 report will contain four main parts:
- Auditor Opinion – a formal statement saying your controls are suitably designed.
- Management Assertion – a signed statement from your team describing your control environment.
- System Description – an overview of your company, systems, and control objectives.
- Control Matrix – a table that maps each control to a Trust Services Criteria and notes the evidence reviewed.
This report is what you’ll share with customers and prospects. It’s your proof that your security design meets industry standards.
Timeline & Cost for SOC 2 Type 1
Wondering how long this will take - and how much it’s going to cost you? Let’s break it down.
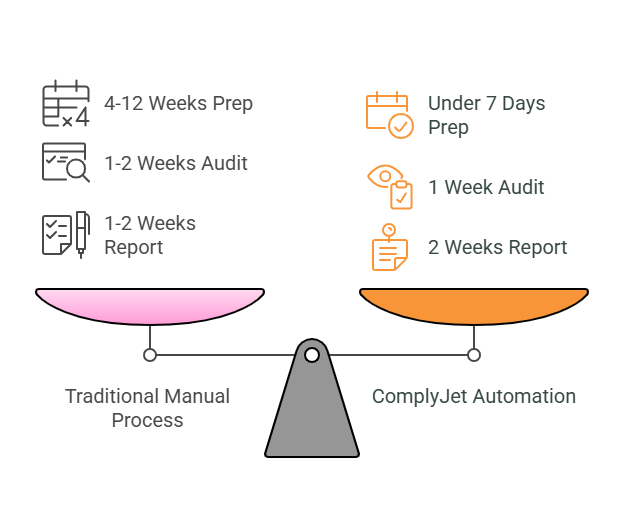
On average, preparing for a SOC 2 Type 1 audit takes 4 to 12 weeks. If your controls are immature or you’re starting from zero, expect to spend more time upfront drafting policies, implementing tools, and collecting evidence.
Once prep is done, the actual audit fieldwork takes 1–2 weeks, followed by another 1–2 weeks for your official report to be issued.
Cost-wise, audits typically range from $8,000 to $30,000, depending on your scope, system complexity, and the auditor you choose. But that’s just the surface.
Here’s the catch: internal costs - like time spent by your security, HR, and engineering teams - can add up fast. Manual evidence collection, policy creation, and endless back-and-forth with auditors can drain hours (and energy).
That’s where ComplyJet comes in.
With ComplyJet’s automation, companies can get SOC 2 ready in under 7 days & get that report within just 21 days from the day you start . You’ll get pre-built controls, automated evidence gathering, and a guided path to readiness - so you’re not reinventing the wheel.
Maintaining SOC 2 Type 1 & Planning for Type 2
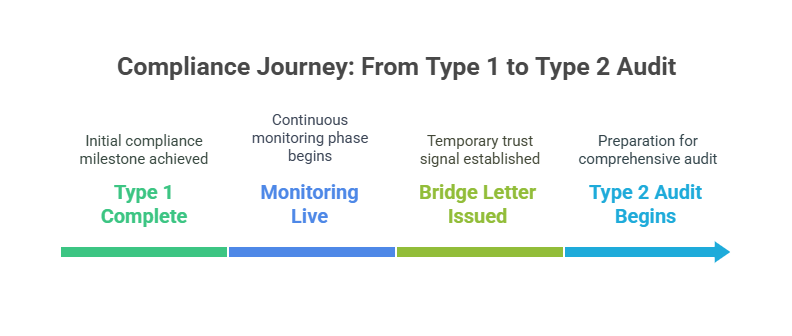
So you’ve nailed your SOC 2 Type 1 - nice. But here’s the thing: that shiny report is just the beginning. To keep buyer trust high and move toward long-term compliance, you need to stay in motion.
Let’s break down exactly how to maintain momentum and confidently level up to SOC 2 Type 2.
1. Shift from Point-in-Time to Ongoing Monitoring
SOC 2 Type 1 is a snapshot. SOC 2 Type 2? That’s a documentary series. It shows how your controls perform over time - usually 3 to 12 months.
That means you’ll need to monitor your controls continuously, not just check a box once.
Start automating evidence collection across your key systems:
- Access logs
- Change management records
- Employee onboarding/offboarding activities
- Security alerts
🛠️ With ComplyJet, you can automate all of this - so evidence is captured in real time and your team isn’t buried in manual screenshots.
2. Know When (and How) to Move to SOC 2 Type 2
Here’s your ideal timeline: 3 to 6 months after your Type 1 report, begin your Type 2 audit window.
Why that range? It gives you enough time to:
- Operate your controls consistently
- Smooth out any gaps discovered in Type 1
- Get your team used to ongoing compliance habits
Bonus: That timing keeps you looking sharp to customers, too. They’ll see you’re not just secure - you’re staying secure.
3. Use Bridge Letters to Keep Buyers Confident
If there’s a gap between your Type 1 and Type 2 audits, you can issue a bridge letter.
This is a formal document from your auditor that:
- Confirms no material changes in your environment
- Extends confidence in your control design during the gap period
It’s not a substitute for Type 2 - but it’s a great short-term trust signal while you prepare.
Bottom line: Getting Type 1 shows you care. Maintaining it and transitioning to Type 2 shows you mean it.
FAQs
How long is a SOC 2 Type 1 valid?
Technically, it’s valid as long as your controls haven’t changed - but most companies refresh it annually or move to Type 2 within 6–12 months.
Can I skip Type 1 and go straight to Type 2?
Yes, you can skip but it’s riskier. Type 1 is a great warm-up. Going straight to Type 2 means you must have your controls running smoothly for months already.
Do I need all five Trust Services Criteria (TSC)?
Nope, you don’t need all five trust services criteria! Only Security is required. The others (Availability, Confidentiality, Processing Integrity, Privacy) are optional based on your business.
Does SOC 2 meet GDPR or HIPAA?
Not exactly. SOC 2 helps with some overlapping controls, but it’s not a one-to-one match. You’ll still need separate assessments for GDPR or HIPAA compliance.
How often should we re-audit?
At least once a year. If anything major changes (like systems, vendors, or policies), you may need to do it sooner or issue a bridge letter in the meantime.
Conclusion
Let’s wrap it up.
SOC 2 Type 1 is your first real proof that your company takes security seriously.
It tells your customers:
“We’ve had a third-party confirm our systems are designed to protect your data and to do it right”
And in 2025? That’s the trust signal buyers expect before they even think about closing a deal.
But here’s the bigger picture: Type 1 is just the starting line.
What comes next is creating simple, repeatable processes that keep your security strong, scale as your team grows, and get you fully ready for SOC 2 Type 2 and beyond.
.png)


