You might think that using AWS means you're automatically covered for compliance, but that's a common misconception during SOC 2 preparation.
The AWS SOC 2 report is not a shortcut to your own certification. It's a third-party audit of AWS’s internal controls, not yours.
Still, it’s a critical asset if used correctly. You can leverage the AWS compliance report to inherit proven infrastructure controls, then layer your own systems on top.
With over 180 AWS services now in scope and regular updates available via AWS Artifact, it’s become a central tool for security reviews and audits.
In this guide, we’ll break down what the AWS SOC 2 audit report contains, how it fits into the Shared Responsibility Model, and which AWS-native services help you automate evidence collection and accelerate your SOC 2 readiness.
What Is the AWS SOC 2 Report?
The AWS SOC 2 Type 2 report is a third-party attested audit that evaluates how Amazon Web Services manages its own internal security, availability, confidentiality, and privacy controls over a 12-month observation window. It’s not a marketing asset but a formal assurance document prepared to comply with the AICPA Trust Services Criteria under the SSAE 18 standard.
This report is renewed annually, and it’s one of the most referenced pieces of evidence when your own SOC 2 auditor asks, “What controls are you inheriting from AWS?”
But while the AWS SOC 2 report gives you a foundational layer of assurance, it doesn’t make you compliant on its own. To use it effectively, you need to understand what’s in the report and how it connects to your responsibilities.
Read: What is a SOC 2 Report? A security Audit or A sales tool?
What’s Inside the AWS SOC 2 Report?
The AWS SOC 2 Type 2 report isn’t a generic checklist but a structured audit document, built in line with AICPA standards, that your report will mirror.
Think of it as a reference manual that breaks down how AWS secures its systems, what the auditor tested, and where your responsibilities begin.
The report is divided into four key sections. Each serves a specific role in helping you understand what AWS has already done and what’s left for you to do.
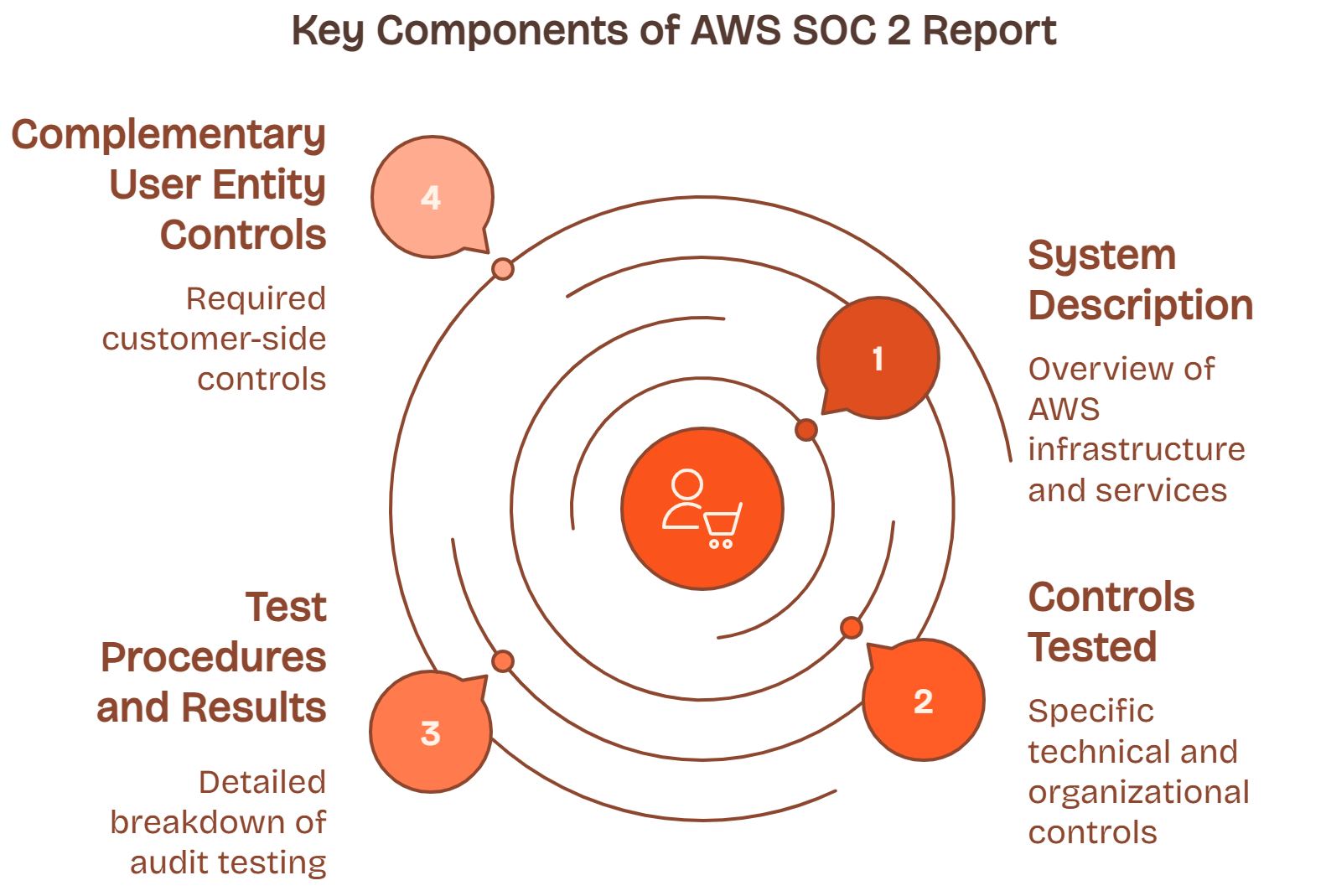
1. System Description
This section lays the foundation. It answers the question: What parts of AWS were included in this audit, and how do they work operationally?
It covers:
- Data Center Design: Where AWS facilities are located, how they control access, and how infrastructure is protected.
- Organizational Structure: Who oversees AWS security, incident response, and compliance operations?
- Services in Scope: Not all AWS services are audited. This part lists the ones that are commonly used like EC2, S3, IAM, RDS, and others.
- Control Ownership: Clarifies which teams or functions inside AWS manage physical security, network controls, or monitoring.
- Operational Processes: Includes overviews of how AWS handles change management, disaster recovery, vulnerability response, and security incidents.
This section is essential because it defines the scope and context for everything that follows. When your auditor asks, “Is AWS’s key management system in scope?”, this is where you find the answer.
2. Controls Tested
This is the major part of the report. It outlines the specific security and operational controls AWS says it has in place and that the auditor evaluated.
You’ll see clear descriptions like:
- “Data centers are equipped with badge-controlled access points and 24/7 surveillance.”
- “Critical vulnerabilities are remediated within SLA-defined timelines.”
- “All customer data is encrypted at rest using AES-256.”
Each control is linked to one or more Trust Services Criteria (TSC), the same criteria your business will be evaluated against. These TSCs cover areas like access control, system availability, and data confidentiality.
Every control also comes with a reference number or identifier, which your team can use to map your own policies against inherited AWS controls.
Why this matters: It shows exactly what AWS is accountable for, and gives you a starting point for mapping your responsibilities on top of it.
3. Test Procedures and Results
This is where the auditor documents how they validated the existence and effectiveness of each AWS control.
The testing approach is formal, and typically includes one or more of the following:
- Inspection: Reviewing evidence like logs or policy files.
- Observation: Watching AWS teams perform tasks like data center access reviews or change approvals.
- Re-performance: Independently testing a control (e.g., trying to reproduce a patch cycle or system alert).
You’ll find specific statements like:
- “Inspected weekly reports of IAM access reviews from Jan to Dec.”
- “Observed badge scan reports during site visit to US-East data center.”
- “Tested sample change tickets for proper authorization workflow.”
Importantly, this isn’t just a design review—it’s an effectiveness evaluation over a 12-month period. That’s why Type 2 reports carry more weight than Type 1, which only assesses design at a single point in time.
Each test result ends with a pass/fail status. In most AWS reports, nearly all controls pass without exceptions, but your auditor may still ask how those findings impact your environment.
4. Complementary User Entity Controls (CUECs)
This is the section that often gets overlooked, but it’s where your responsibilities begin.
CUECs are the assumptions AWS makes about your organization. They’re not optional. AWS is saying, “We’ve done our part, but for this control to be effective, you must do X.”
Examples include:
- IAM Configuration: AWS provides IAM, but you’re responsible for defining role permissions and enabling MFA.
- Encryption Settings: AWS services support encryption, but you must turn it on, manage keys, and enforce usage.
- Log Review: AWS captures access logs, but you need to review and act on them.
- Key Rotation: AWS KMS handles encryption keys, but you’re expected to schedule and document key rotations.
If you don’t address these CUECs, then it doesn’t matter how secure AWS is. Your use of AWS becomes non-compliant, and your SOC 2 auditor will flag the gap.
Understanding these sections is more than just reading a PDF. It’s about building a bridge between AWS’s verified controls and your compliance posture. This bridge is what your auditor will walk across.
Whether you build that bridge manually or through automation tools, it’s the only way to transform AWS’s SOC 2 report from a static document into a meaningful input for your audit.
Read: What does a general SOC 2 Report Contain?
Who Audits AWS, and Under What Standard?
AWS’s SOC 2 report is conducted by an independent CPA firm, typically one of the Big Four or a qualified attestation firm with AICPA credentials. The audit uses the SSAE 18 standard and tests AWS against the AICPA Trust Services Criteria.
This means the controls are consistent with what your auditor will use. But again, AWS is only being assessed on its cloud infrastructure, not on how you use it.
Why You Still Have Work to Do
It’s easy to download the AWS SOC 2 report and assume that your audit is 70% complete. But that’s rarely the case.
AWS’s audit proves that AWS has secure infrastructure and operational practices. It says nothing about how securely you use that infrastructure. You’re still responsible for:
- Designing and enforcing IAM roles
- Encrypting data in transit and at rest
- Setting up backup and disaster recovery processes
- Implementing anomaly detection and alerting
- Writing and maintaining internal security policies
Auditors won’t take AWS’s controls as a proxy for yours. You’ll need to map your cloud configuration to the TSC, identify which responsibilities are inherited, and document or automate the rest. This is where compliance tooling becomes critical.
Without automation, this turns into a manual exercise involving screenshots, log exports, and policy uploads, none of which scale.
With automation, you can centralize evidence, track CUEC completion, and monitor drift across cloud accounts.
Understanding the structure of the AWS SOC 2 Type 2 report is step one. The next step is building your control matrix by connecting the dots between what AWS does, what you do, and what your auditor expects to see.
Just because AWS passed its SOC 2 audit doesn’t mean you’re compliant. You still need to show how you configure your cloud environment, secure your workloads, and monitor your systems.
You’ll also need to produce your control documentation, evidence, and internal policies, especially for the areas AWS marks as customer-controlled.
Read: 70+ Auditor-Approved SOC 2 Control List
What Is a SOC 2 Report Useful For?
If you rely on Amazon Web Services, the AWS SOC 2 report is one of the most important documents you can use to demonstrate trust, readiness, and compliance.
Whether you're preparing for a SOC 2 Type 2 audit, responding to vendor reviews, or aligning with industry regulations like GDPR or CCPA, the report gives you a defensible starting point.
Below are ten real-world use cases that explain why the Amazon AWS SOC 2 report isn’t just useful but foundational to any serious cloud-based compliance strategy.
1. Validating Infrastructure Security With SOC 2 Compliance Evidence
The AWS SOC 2 compliance report provides third-party validation that AWS’s infrastructure meets the AICPA Trust Services Criteria. It covers five key areas such as security, availability, processing integrity, confidentiality, and privacy. This validation gives your team and your auditors confidence that your cloud service provider operates at a high standard.
2. Accelerating Your Own SOC 2 Type 2 Audit Timeline
The AWS SOC 2 Type 2 report is a shortcut for proving what AWS already secures. When you hand this report to your auditor, you reduce the amount of evidence you need to collect for infrastructure-level controls like physical security, patching, or disaster recovery.
3. Helping You Pass Vendor Security Reviews Faster
Enterprise customers regularly ask for proof that you’re using a secure cloud service provider. Providing the AWS SOC 2 audit report as part of your due diligence package helps you satisfy procurement, legal, and IT review checklists, often before you've even finished your own SOC 2 audit.
4. Clarifying the Shared Responsibility Model in Practice
The AWS SOC 2 report explicitly outlines Complementary User Entity Controls (CUECs), which are the controls that AWS expects you and the customer to implement. This is critical for building your control matrix. It distinguishes which parts of your cloud stack you must secure (IAM, encryption, log reviews) versus what AWS already handles.
5. Streamlining Internal and External Audit Preparation
Instead of explaining AWS's security model from scratch, you can simply attach the Amazon AWS SOC 2 report to your audit documentation. It includes test procedures, auditor findings, and control narratives that align with frameworks like SOC 2, ISO 27001, and HITRUST.
6. Providing Regulatory Alignment With GDPR and CCPA
While not a regulatory report itself, the AWS SOC 2 compliance report supports alignment with GDPR, CCPA, and other global privacy laws. It shows that AWS’s infrastructure operates with strong access controls, encryption standards, and breach notification processes essential for privacy programs.
7. Guiding Technical Risk Assessments for AWS Hosted Workloads
The report’s detailed control tests and audit results help your security and engineering teams evaluate potential infrastructure risks. You can use it to assess how AWS handles failover, logging, or intrusion detection and whether you need to add compensating controls in your own environment.
8. Establishing Transparency With Customers and Partners
Sharing the AWS SOC 2 report download (under NDA) demonstrates that your cloud environment is built on infrastructure that’s independently verified. This transparency is essential for companies handling sensitive data, like fintech, healthtech, or enterprise SaaS providers.
9. Supporting Evidence Collection for Multi-Framework Compliance
If you’re pursuing certifications beyond SOC 2, such as SOC 1, SOC 3, or ISO 27001, the AWS SOC 2 report often serves as overlapping evidence. It eliminates the need to recreate audit documentation for infrastructure controls that AWS already validates annually.
10. Serving as the Foundation for Automation and Policy Mapping
Finally, the AWS SOC 2 report can be integrated into tools like AWS Audit Manager, where it helps automate evidence mapping to control sets. For teams using policy-as-code or compliance automation, this report becomes part of the baseline library that aligns your technical stack with audit requirements.
Bottom Line: The AWS SOC 2 audit report is a core artifact for proving infrastructure compliance, managing third-party risk, clarifying control ownership, and scaling securely. Use it early, use it often, and map it tightly to your own SOC 2 readiness process.
How to Get the AWS SOC 2 Report
Start by logging into the AWS Management Console, then navigate to AWS Artifact. From there:
- Select Reports from the left-hand menu.
- Search for “SOC 2 Type II Report” and choose the latest Type 2 report.
- Review the permissions. Only users with appropriate IAM roles can access it.
If needed, assign permissions using AWS’s built-in Artifact access policy templates. Once access is set, you can download the report as a PDF and share it with your audit team.
Read: How to get your own SOC 2 report?
AWS SOC 1 VS SOC 2 VS SOC 3: What’s the Difference?
If you’re reviewing AWS SOC 1, SOC 2, and SOC 3 reports, it’s important to know they serve very different purposes, even though they’re built on similar audit frameworks.
Each report is designed for a specific type of assurance, audience, and use case. Picking the right one depends entirely on what your customers, auditors, or partners need to validate.
SOC 1: For Financial Reporting Controls
SOC 1 is used when your system affects another company’s financial statements. If you’re running a payroll platform or handling billing data, this is what your customers will ask for.
- Scope: Controls relevant to financial reporting (ICFR)
- Audience: Financial auditors, controllers, finance teams
- AWS Use Case: Fintech platforms or ERP backends
SOC 2: For SaaS Security and Operational Assurance
SOC 2 covers the Trust Services Criteria: security, availability, confidentiality, processing integrity, and privacy. This is the gold standard for SaaS platforms hosted on AWS.
- Scope: Information security and service controls
- Audience: CTOs, security teams, compliance officers
- AWS Use Case: Healthtech, devtools, B2B SaaS companies
For further understanding,
Read: SOC 2 Type 1 vs SOC 2 Type: Detailed Comparison
SOC 3: A Publicly Shareable Summary
SOC 3 is a sanitized, public version of the SOC 2 report. It contains no sensitive details but validates that AWS passed its SOC 2 Type 2 audit.
- Scope: Same controls as SOC 2, summarized for public use
- Audience: Prospective customers, marketing materials
- AWS Use Case: When you want to show AWS compliance without disclosing full SOC 2 data
Choosing the Right Report
- Choose SOC 1 if your service impacts accounting records.
- Choose SOC 2 if you’re a SaaS platform needing trust from security teams.
- Use SOC 3 to showcase AWS compliance on your public-facing trust page.
How AWS's Shared Responsibility Model Impacts SOC 2 Compliance
If you're using AWS, your SOC 2 responsibilities don’t stop at application code or infrastructure setup. The real work begins with how you manage that infrastructure. This is where AWS’s Shared Responsibility Model becomes central to your SOC 2 compliance strategy.
The AWS SOC 2 compliance report is often misunderstood.
An AWS SOC 2 report only validates that AWS has secured its environment, but it doesn’t say anything about how secure your setup is.
You still need to show that you’ve configured services correctly and are following operational best practices that align with SOC 2 expectations.
Your Compliance Posture Depends on Shared Ownership
AWS is responsible for protecting the cloud, things like the data center, hardware, and base service operations. But you’re responsible for protecting what’s in the cloud, like your data, your configurations, and how you use AWS services. This shared responsibility is a foundational principle in the AWS SOC 2 audit report, and it directly shapes your own SOC 2 efforts.
Misunderstanding the Boundaries Can Derail Your Audit
Too often, teams assume the AWS SOC 2 report gives them blanket coverage. But your auditor will ask: Have you set up logging? Are your users forced to use MFA? Have you reviewed who has access to production? None of those fall under AWS’s scope, and they’re yours. The moment you miss that distinction, your audit readiness starts to fall apart.
Read: SOC 2 Compliance Requirements
Inherited, Shared, and Customer-Owned Controls: Know the Difference
Every control in your SOC 2 control matrix fits into one of three buckets. This determines what evidence you can inherit from AWS and what you must build yourself.
- Inherited Controls come fully from AWS. These include physical security, building access, and managed encryption protocols within AWS infrastructure. These are already covered in the AWS SOC 2 Type 2 report.
- Shared Controls involve both parties. AWS provides the feature, and you enable or configure it. Logging, encryption toggles, patching schedules, or network rules often fall into this zone. If AWS mentions the control in their SOC 2 report, it will often include a complementary user entity control (CUEC) that spells out your responsibilities.
- Customer Controls are 100% yours. Identity management, internal access reviews, and alert responses do not fall under AWS. Your own SOC 2 audit depends heavily on how well these are implemented and maintained.
The Real Risk: Relying Too Heavily on AWS’s SOC 2 Report
Yes, AWS is compliant, and yes, you can lean on their control documentation, but only where it applies. The AWS SOC 2 report is not a compliance shortcut. It’s a supporting document that must be supplemented by your own controls, evidence, and policies.
If you ignore the Shared Responsibility Model, you’ll miss crucial pieces of your own compliance. For example, AWS supports S3 encryption, but unless you enable it and manage your keys, the encryption is not active. That’s not on AWS, that’s on you.
Why This Matters for Your SOC 2 Type 2 Audit
During your audit, you’ll need to demonstrate how you meet every relevant control under the Trust Services Criteria, especially for security and availability. Your ability to separate what’s inherited from AWS and what needs your direct oversight is critical.
This clarity not only improves your compliance posture but also helps streamline the audit process.
The AWS SOC 2 compliance report, when understood correctly, is a powerful asset.
AWS lets you inherit well-tested infrastructure controls, but only if you pair them with your own operational maturity. Your SOC 2 success depends on that shared commitment.
Here’s Your Free SOC 2 Compliance Checklist to further streamline your SOC 2 compliance journey!
The AWS Tools That Help You Build Your Own SOC 2 Controls
You don’t need to build your SOC 2 system from scratch. AWS offers an overall suite of services that can automate evidence collection and help maintain continuous control over your infrastructure.
AWS Artifact: Access the Source Reports
AWS Artifact is your starting point. This is where you can download the AWS SOC 2 audit report, as well as SOC 1 and SOC 3 reports, ISO certifications, and other audit artifacts.
Use Artifact to show auditors the AWS controls you inherit and match those with your CUECs.
AWS Audit Manager: Map and Track SOC 2 Requirements
AWS Audit Manager includes a pre-built SOC 2 framework based on SSAE 18 standards. It comes with 15 automated controls and 46 manual ones grouped by Trust Services Criteria (TSCs).
Use it to:
- Map each requirement to relevant AWS services
- Assign internal owners
- Collect and attach supporting evidence
AWS Config: Track and Remediate Drift
AWS Config continuously tracks the state of your resources. You can write custom rules or use managed packs to check for compliance gaps.
Examples:
- Detect if encryption is turned off for S3 buckets
- Flag publicly accessible security groups
This helps you detect and correct issues before they show up in an audit.
AWS Security Hub: Unify Compliance Findings
Security Hub integrates with Config, GuardDuty, Inspector, and third-party scanners. It gives you a central dashboard to view findings against standards like CIS AWS Foundations, SOC 2, and PCI DSS.
Enable auto-remediation for common misconfigurations to maintain readiness.
Mapping AWS Controls to the SOC 2 Trust Services Criteria
To make the AWS SOC 2 report actionable, you need to map its contents to your own control system. This means aligning AWS’s audited controls with the Trust Services Criteria (TSCs) defined in your SOC 2 audit scope.
This is where most of the actual work happens and where automation can save you weeks of manual effort.
Step 1: Choose the Applicable Trust Services Criteria
Start with Security, which is non-negotiable. Depending on your product and risk profile, you might also include:
- Availability: For SLAs, failover, and resilience
- Confidentiality: For PII or customer-sensitive data
- Processing Integrity: For the accuracy of transactions or algorithms
- Privacy: For regulated personal data collection and disclosures
This scoping guide aligns with everything that follows, so align early with your auditor.
Step 2: Use AWS Audit Manager’s Prebuilt SOC 2 Framework
AWS offers a SOC 2 framework in Audit Manager that includes:
- 15 AWS-native automated controls
- 46 placeholders for manual inputs
- Grouped by TSC and pre-mapped for faster onboarding
You can enable this within your AWS account. Still, the real benefit comes when you connect it to a compliance automation layer like ComplyJet, which imports these mappings and consolidates your evidence alongside non-AWS systems like GitHub, Okta, and Jira.
Step 3: Build a Control Responsibility Matrix (AWS vs You)
Use the Shared Responsibility Model to classify every control:
- AWS-Owned: Network security, hypervisor patching, physical access
- Customer-Owned: IAM roles, MFA enforcement, backup retention
- Shared: Encryption configuration, OS patching, monitoring setup
This classification becomes your control matrix, which auditors rely on to understand scope and control coverage. ComplyJet includes this matrix out of the box, with control ownership flags based on AWS guidance and auditor expectations.
Step 4: Collect Automated and Manual Evidence
For each mapped control, you’ll need a record of implementation:
- Automated: Pull logs from CloudTrail, rule status from Config, findings from Security Hub
- Manual: Upload your access policy PDFs, screenshots of MFA settings, or calendar invites from quarterly access reviews
ComplyJet streamlines this process by ingesting evidence from AWS and over 100 third-party systems, timestamping it, and mapping it directly to the relevant TSC. That means no hunting through log folders or pasting screenshots into spreadsheets.
Example Control Mapping Table
Callout: Use the AICPA SOC 2 Compliance Guide on AWS
AWS maintains a comprehensive SOC 2 Compliance Guide that maps AWS services to the TSCs and outlines where customer-side controls are required. ComplyJet uses this guidance as part of its default mappings, so you're not rebuilding frameworks from scratch.
Effective mapping is the backbone of a defensible SOC 2 program. Done right, it lets you shift from reactive gap-filling to proactive audit readiness, with AWS services and automation platforms like ComplyJet doing the heavy lifting.
How Automation Tools Help You Operationalise SOC 2 on AWS
If you want to get compliant without burning your team’s time on spreadsheets, tickets, and guesswork, automation platforms like ComplyJet make that feasible.
ComplyJet is built for startups and lean engineering teams who need structure, visibility, and audit readiness with minimal overhead. It integrates natively with AWS, pulling in CloudTrail logs, Config snapshots, IAM settings, and Security Hub findings automatically, so you don’t have to manually stitch that evidence together.
Why ComplyJet Works Well with AWS
- Native AWS Integrations: Plug into CloudTrail, GuardDuty, IAM, and Config without custom scripts.
- Shared Responsibility Mapping: Automatically identifies inherited AWS controls and flags required CUECs on your side.
- Evidence Engine: Gathers artifacts from S3, GitHub, Jira, Okta, and 100+ other tools you already use.
- Audit-Ready Reports: Generate ready-to-review SOC 2 evidence packs, mapped to Trust Services Criteria, in weeks.
To know more about making your SOC 2 pathway less stressful, Talk To The Founders!
Cost-Effective for Early Teams
Most compliance platforms are bloated and priced for mid-market enterprises. ComplyJet flips that with founder-friendly pricing, a flat subscription, and optional audits through vetted CPA firms.
Startups typically save 60–70% over legacy tools, while meeting the same audit bar with real-time control visibility.
Read: SOC 2 Audit Cost Breakdown
FAQs
How do I use the AWS SOC 2 report in my own SOC 2 audit?
You can use the AWS SOC 2 report to demonstrate that your cloud provider has strong infrastructure-level controls. However, you must map those to your internal control matrix and address all customer responsibilities defined in the report’s CUEC section
What are AWS CUECs (Complementary User Entity Controls)?
AWS CUECs are customer responsibilities assumed in the AWS SOC 2 report. They cover tasks AWS doesn’t perform, like configuring IAM, enabling encryption, or reviewing logs. Your organization must implement and document these controls to satisfy SOC 2 requirements.
Is AWS SOC 2 compliance enough for my SaaS platform?
No. While AWS SOC 2 compliance gives you a strong infrastructure foundation, you still need to implement security controls across your own app, data, user access, and third-party integrations to meet the AICPA Trust Services Criteria.
Does the AWS SOC 2 Type 2 report cover all AWS services?
No. The AWS SOC 2 Type 2 report only covers services that were in scope for that audit cycle. As of the latest report, over 180 services are included, but you must check AWS Artifact for the current list before relying on coverage.
How can I verify the AWS SOC 2 report’s authenticity?
The AWS SOC 2 audit report is downloaded directly from AWS Artifact, which ensures it comes from a verified source. Reports are digitally signed and issued by licensed CPA firms, with versioning and dates listed.
Can I share the AWS SOC 2 audit report with customers?
Yes, but with caution. The AWS SOC 2 audit report is restricted under NDA and should only be shared with prospects, customers, or auditors who need it for due diligence and not published publicly. Use AWS SOC 3 for public-facing assurance.
How do I download the AWS SOC 2 report?
To download the AWS SOC 2 report, open AWS Artifact, locate the SOC 2 Type 2 entry under "Available Reports," and click the download button. Ensure you have appropriate IAM roles enabled to access and export audit documentation from AWS Artifact.
How often is the AWS SOC 2 Type 2 report updated?
The AWS SOC 2 Type 2 report is updated once every 12 months. It covers a rolling one-year period and is published annually via AWS Artifact. Customers are expected to use the most recent report during their compliance assessments.
What is the difference between AWS SOC 2 Type 1 and Type 2 reports?
The AWS SOC 2 Type 1 report assesses whether controls are designed appropriately at a point in time. In contrast, the AWS SOC 2 Type 2 report evaluates how those controls operated over a 12-month period, offering a more rigorous and trusted assurance.
How does the AWS SOC 2 report support compliance?
The AWS SOC 2 compliance report offers pre-audited infrastructure controls that customers can inherit. However, it doesn’t cover how you configure or manage your workloads. You still need to implement internal controls for access, logging, encryption, and monitoring.
Which AWS services are included in the AWS SOC 2 audit report?
The AWS SOC 2 audit report includes over 180 services, such as EC2, S3, IAM, CloudTrail, RDS, and Lambda. The full list of in-scope services is detailed within the report and is accessible via AWS Artifact under the "Services in Scope" section.
Can I use the AWS SOC 2 audit report for my own SOC 2 compliance?
You can reference the AWS SOC 2 audit report as supporting evidence for inherited controls, but it doesn’t make your organization SOC 2 compliant. You must implement your own controls and address all complementary user entity responsibilities identified in the report.
Is the AWS SOC II Type 2 report the same as SOC 2 Type 2?
Yes. The AWS SOC II Type 2 report is another way of referring to the AWS SOC 2 Type 2 report. Both describe the same annual, third-party audit evaluating AWS's control effectiveness over a 12-month period using the AICPA Trust Services Criteria.
Conclusion
AWS gives you a solid foundation, but the responsibility is shared. You still need to show how your team configures, monitors, and governs that environment.
With ComplyJet, you can map AWS’s audited controls to your own, integrate with the rest of your stack, and produce audit-ready evidence without second-guessing. You won’t have to dig through CloudTrail logs or manually prove that MFA is enabled everywhere.
Start with three simple steps:
- Download the AWS SOC 2 report from Artifact
- Use ComplyJet to map and automate your controls—Start your FREE TRIAL NOW!
- Build your compliance program like you’d build your product: with clarity, automation, and feedback loops
Compliance doesn’t need to be a distraction. With the right tools, it becomes part of how you build trust.
.png)


