If you have ever wondered “what is a BAA?”, it’s the contract that controls how your partners handle protected health information under HIPAA.
A HIPAA Business Associate Agreement ensures that covered entities, business associates, and service providers follow the same standards when handling patient data.
In 2025 alone, the Office for Civil Rights (OCR) has already announced 18 enforcement actions, many tied directly to Business Associate Agreement failures.
Earlier, Catholic Health Care Services paid $650,000 in the first-ever settlement against a business associate after an unencrypted iPhone breach exposed patient details. These cases show that OCR now holds business associates just as accountable as covered entities.
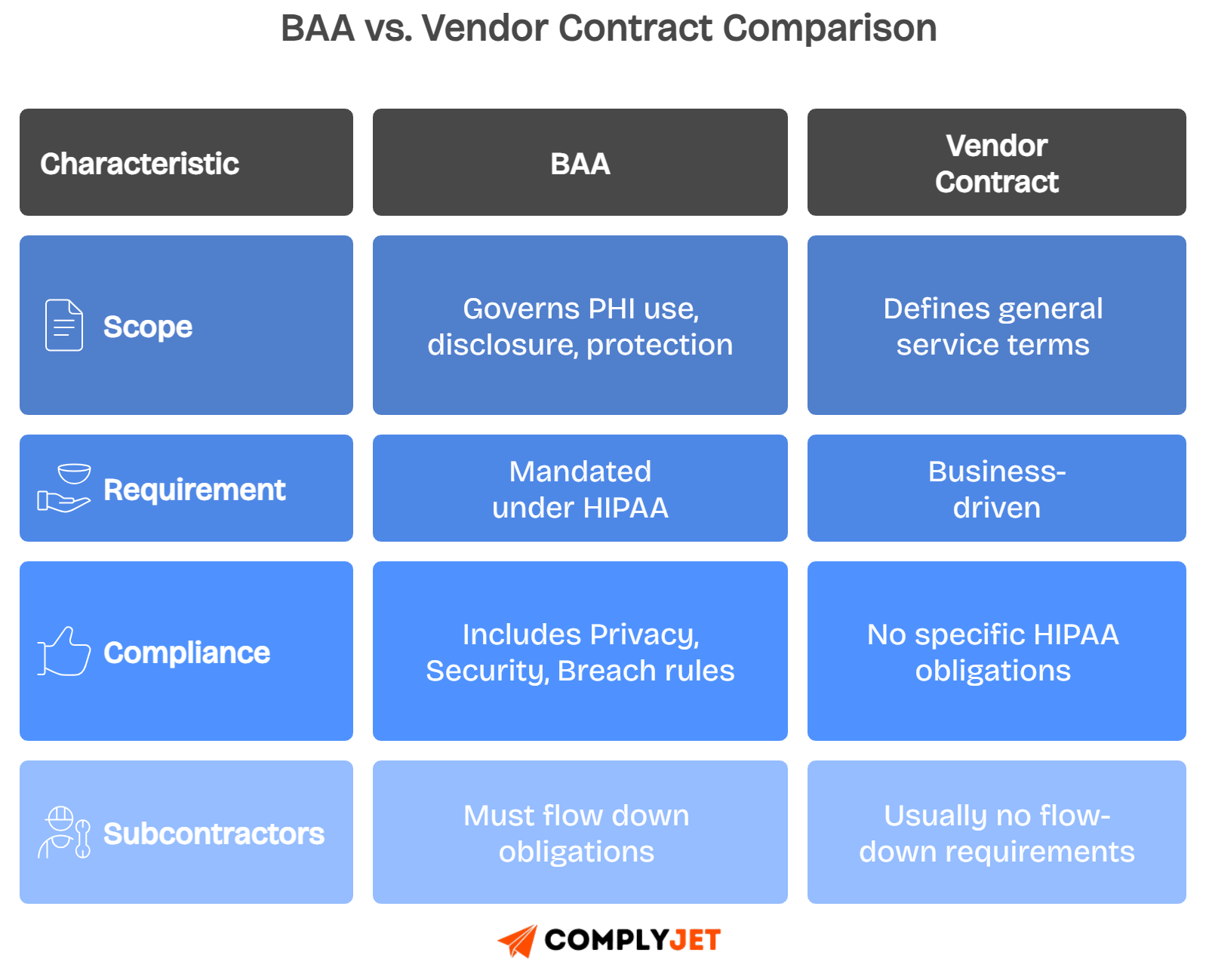
A business associate agreement enforces the Privacy Rule, Security Rule, and Breach Notification Rule, which are the pillars of HIPAA compliance and directly influence your risk posture.
In this blog article, you’ll learn who qualifies as a business associate, when a BAA is required, what clauses must be included, and common mistakes that will save millions in penalties.
If you want a ready-to-ship business associate agreement template, grab ComplyJet’s free download today and start aligning your vendors with HIPAA requirements.
Let's get into basics first.
What is a Business Associate Agreement?
Understanding BAA is your first step in building HIPAA compliance into daily operations. A Business Associate Agreement (BAA) is a legal contract that defines how protected health information is handled when shared outside your direct control.
The HIPAA Business Associate Agreement binds three main parties: covered entities like hospitals or health plans, business associates such as service providers, and subcontractors that further support them. Each must follow identical safeguards for handling patient data.
Within the broader Health Insurance Portability and Accountability Act, BAAs sit alongside the Privacy Rule, Security Rule, and Breach Notification Rule. Together, they create the foundation for protecting patient privacy.
The agreement also enforces the “minimum necessary” principle, meaning a business associate may only access the smallest possible amount of data required. This limits risk and ensures strong internal practices.
This foundation leads directly into identifying who qualifies as a business associate under HIPAA, since the definition determines when a BAA becomes legally required.
Who is a Business Associate under HIPAA?
To answer this, look at how HIPAA defines the role. A business associate is any person or organization that creates, receives, maintains, or transmits PHI or ePHI on behalf of a covered entity.
If you fall into this category, you are legally required to sign a HIPAA Business Associate Agreement and comply with the same privacy and security standards as healthcare providers themselves.
The distinction is important. A workforce member, such as an employee, is not a business associate, but a third party providing services with PHI access is.
Recognizing this line is essential. It prevents both overreaching contracts, like landscapers being asked to sign BAAs, and under-contracting, which risks compliance failures.
Common examples of Business Associates
- Healthcare providers’ support services: billing companies, claims processing vendors, transcription services, and utilization review contractors.
- Cloud storage providers and infrastructure like AWS, Azure, or GCP that have persistent access to PHI.
- EHR vendors, IT managed service providers, SOC monitoring, data destruction vendors, legal firms, CPA firms, or marketing agencies handling PHI.
- Health plans and clearinghouse support vendors that touch patient data indirectly.
Who is not a business associate under HIPAA?
Some roles do not count as business associates under HIPAA. Services that don’t store PHI permanently with persistent access fall under the conduit rule, like postal carriers delivering documents
Treatment disclosures between providers made purely for patient care are exempt.
Standard payment processors handling financial transactions without retaining PHI also do not qualify as business associates.
Finally, workforce members under the direct control of the covered entity are not treated as business associates. Their responsibilities fall under employer policies, not BAAs.
With these distinctions clear, the next step is learning when BAAs are required and when they are not, since that decision determines how you structure vendor relationships.
Also Read: Are you a HIPAA Covered Entity?
When is a BAA required?
Knowing when you must sign a Business Associate Agreement is vital because missing one can expose your company to heavy penalties and audit risks.
A BAA is required whenever a covered entity shares protected health information with a third party that creates, receives, maintains, or transmits that information on its behalf.
You must also sign a BAA when using SaaS applications or cloud storage providers with persistent access to encrypted data, since encryption alone does not exempt responsibility.
In some cases, a covered entity may act as a business associate for another covered entity. These relationships still require a clear BAA to define responsibilities.
Here's quick overview of when you might need a BAA:
Clear criteria avoid confusion. Now that you know when agreements are needed, let’s explore the required clauses inside every HIPAA Business Associate Agreement.
Required Clauses in HIPAA Business Associate Agreement
A HIPAA Business Associate Agreement is only effective when it includes mandatory clauses. These provisions safeguard Protected Health Information (PHI) and define accountability for all parties.
Permitted uses and disclosures
Permitted uses of PHI are restricted to services defined in the agreement or lawful requirements under HIPAA. Broader use creates compliance gaps.
Define exactly how PHI can be used. Allow only contracted services or legal obligations, and restrict all other disclosures without clear written authorization.
Block unauthorized PHI use for marketing, research, or unrelated operations. This ensures PHI remains tied to legitimate healthcare or compliance purposes.
Document every disclosure. Maintain complete records to demonstrate accountability, satisfy audit requirements, and support covered entities during compliance reviews.
Once boundaries are clear, move next to specifying strong safeguards under the HIPAA Security Rule.
Security measures and the minimum necessary
Implement administrative safeguards. Train employees, enforce written security policies, and perform regular access reviews to minimize mistakes. These establish consistent protection for PHI across your workforce.
Apply technical safeguards. Use encryption, access controls, and monitoring to protect electronic PHI against cyberattacks and internal misuse.
Maintain physical safeguards. Restrict offices, lock cabinets, and secure devices that store or transmit PHI. These reduce the risks of physical breaches.
Follow the minimum necessary rule, which requires that PHI exposure be reduced to the smallest scope needed for business tasks.
Incident handling, individual rights, and subcontractors
Security incident handling must be written with timelines. Write clear security incident reporting rules. Require notifications to covered entities within five business days of an event.
Breach Notification must follow HIPAA requirements. Include breach notification obligations. Follow HIPAA’s mandate to report without delay and never later than sixty days after discovery.
Individual rights must be supported. Guarantee processes for PHI access, amendment, and disclosure accounting within defined timelines.
Subcontractor obligations flow down. Ensure subcontractors handling PHI sign equivalent business associate contracts, preventing weak points in the compliance chain.
Termination, data location, and audit
Termination procedures require PHI to be returned or securely destroyed at contract end. Address it explicitly. Use compensating safeguards if destruction is impossible.
Data location constraints may restrict PHI storage to specific jurisdictions. Define permitted PHI storage locations to avoid cross-border conflicts and compliance challenges.
Audit and inspection clauses require cooperation with OCR or HHS. Prepare for inspection and include cooperation language. Provide access to records and practices on request.
These clauses create enforceable protections. Here’s a sample of languages to be used:
With clauses outlined, the next section explains how to build a compliant BAA step by step.
How to Build a HIPAA Compliant BAA: Step-by-Step
Creating a compliant Business Associate Agreement requires structured steps. Each action aligns your obligations with HIPAA rules and your real operating environment.
Step 1: Identify PHI data flows and systems
First, map where Protected Health Information lives, how it moves, and which people or systems access it. This visibility eliminates blind spots.
Document every system that stores or transmits PHI. Include cloud storage, email, billing platforms, and shared tools.
Mark external touchpoints clearly. Knowing who touches PHI, inside and outside, reduces the risk of oversight.
Once PHI flows are visible, classify vendors as business associates or not.
Step 2: Determine BA status for service providers and third parties
Check whether vendors “create, receive, maintain, or transmit PHI.” Those entities qualify as business associates under HIPAA.
Separate direct workforce members from third parties. Employees under your control do not require BAAs. External service providers do.
Include IT providers, legal consultants, billing agencies, and cloud storage providers. Each has potential PHI exposure.
With business associates identified, establish a contract baseline.
Step 3: Select a BAA template baseline
Start with a business associate agreement template like ComplyJet’s. Templates map directly to HIPAA requirements, simplifying drafting.
Using a tested baseline ensures mandatory clauses are not missed. Examples include permitted uses, breach handling, and audit cooperation.
Templates accelerate review, reducing time to compliance. They also provide consistency across all agreements.
Once the baseline exists, adjust it to reflect your unique workflows.
Step 4: Customize permitted use cases and safeguards
Tailor permitted PHI uses to actual services. Limit handling to only what is required for specific tasks.
Define safeguards clearly. Address administrative, physical, and technical protections that match your environment.
Add data residency rules. Specify if PHI may be stored internationally or restricted to domestic systems.
When use cases and safeguards align, focus shifts to incident response.
Step 5: Define breach and incident SLAs, contacts, and reporting paths
Write service-level agreements for breach and security incident handling.
Define response times, escalation paths, and reporting duties. Add named contacts for both sides. This prevents delays during security events.
Include multiple communication channels. Redundant contact options reduce missed alerts.
After SLAs are set, subcontractor controls must follow.
Step 6: Add subcontractor controls and downstream obligations
Require subcontractors with PHI access to sign BAAs. Flow obligations downstream with equal or stricter protections.
Include oversight processes. Audit subcontractors periodically to verify compliance.
Restrict subcontractor data storage or transfer if needed. Align rules with your internal policies.
The last step is formal legal review and signature.
Step 7: Final legal review and repository storage
Complete a legal review before signing. Confirm clauses meet HIPAA and state law requirements.
Store signed BAAs in a contract repository. This ensures access during OCR audits.
Track expiration and renewal dates proactively. Regular reviews prevent outdated agreements from lingering.
Once stored, your BAAs become enforceable compliance tools.
With agreements in place, the real test comes with enforcement. That is where penalties and risks must be understood.
Enforcement & Penalties: Civil and Criminal
The Office for Civil Rights (OCR) enforces HIPAA compliance. BAA failures often attract direct penalties ranging from fines to criminal penalties.
OCR enforcement posture and penalty tiers
Civil penalties follow four tiers. Amounts range from $137 per violation to over $68,000, capped annually at more than $2 million.
Higher tiers apply when violations are due to willful neglect. Corrected issues reduce severity, but unresolved failures trigger maximum penalties.
Criminal penalties apply when PHI is misused intentionally. Prison terms range from one to ten years, depending on misconduct.
Civil and criminal actions often overlap, magnifying organizational risk.
Common failure themes
Missing BAAs remain a leading cause of OCR settlements. Covered entities sharing PHI without contracts are regularly penalized.
Weak internal practices compound risks. Examples include unencrypted devices or missing breach policies.
Delayed breach notifications are another trigger. HIPAA requires reporting within sixty days, yet many organizations exceed this.
Failure themes repeat, proving preventable errors drive most enforcement cases.
Risk scenarios for data breaches
A stolen device without encryption exposes thousands of health information records. Without a valid BAA, liability spreads.
Cloud vendors with persistent PHI access are treated as business associates. Failure to sign BAAs with them creates compliance gaps.
Large-scale data breaches tied to business associates remain common. In May 2025 alone, 1.8 million patient records were exposed.
Such scenarios highlight why BAAs remain central to HIPAA compliance.
Understanding penalties clarifies why BAAs are non-negotiable. The following section focuses on best practices for avoiding enforcement entirely.
Breach Notification & Incident Response inside the BAA
A HIPAA Business Associate Agreement must define exactly how security events are handled. Clear rules reduce confusion when incidents inevitably happen.
Security incident vs breach
Distinguishing between a security incident and a breach is important.
Incidents may include failed logins, while breaches involve actual exposure of Protected Health Information.
HIPAA sets a 60-day deadline for external notifications. Most agreements require much faster internal reporting to limit potential harm.
You should specify reporting windows such as one, three, or seven days, depending on the incident type.
Clear definitions prevent partners from delaying disclosure by calling breaches “incidents.”
Forensics, mitigation, and notification content
Every BAA should require forensic investigation when a breach occurs. You need evidence about what happened, how, and how many records were affected.
Mitigation steps must be documented. These include system isolation, patching, and access revocation.
Notification content must cover what data was exposed, who was affected, and steps to protect individuals.
Agreements should align with state breach laws, which often impose stricter timelines or additional content requirements.
Coordination with regulators
Covered entities and business associates must coordinate with the Office for Civil Rights (OCR). Reporting typically happens through HHS portals.
Your BAA should define who files notices to OCR, and how updates are shared.
Both parties must agree on escalation triggers. Regulators will expect coordinated, consistent communication.
Well-documented processes reduce liability during government investigations.
Having structured response rules in your BAA ensures accountability. The next piece extends this accountability to subcontractors handling PHI.
Subcontractors & Chain of Custody
Business associates often rely on subcontractors. HIPAA requires extending protections downstream to every entity handling PHI.
Requiring and verifying downstream BAAs
Subcontractors with PHI access must sign equivalent business associate agreements. This keeps protections consistent across the data chain.
Your agreements should require proof of signed subcontractor BAAs. Without verification, blind spots appear.
Covered entities often audit prime contractors for evidence of subcontractor compliance.
Accountability improves when obligations cascade clearly.
Due diligence expectations
You should evaluate subcontractors like you would primary vendors. Request SOC 2 reports, ISO 27001 certifications, or third-party penetration tests.
Ask for recent risk assessments. These highlight vulnerabilities and show whether subcontractors take HIPAA compliance seriously.
Keep records of due diligence reviews. OCR may request them during audits.
Verification protects both your business and your clients’ PHI.
Practical auditing and cadence
Subcontractors should be audited on a defined schedule. Many organizations choose annual reviews, while high-risk vendors may need quarterly checks.
Require subcontractors to provide security attestations regularly. Attestations should confirm continued HIPAA compliance.
Use a standardized checklist to compare subcontractor practices against your own obligations.
Maintaining cadence avoids “set and forget” compliance.
With subcontractor compliance secured, the next step is monitoring common pitfalls organizations face when managing BAAs.
Cloud, SaaS, and “Persistent Access” Scenarios
When PHI lives in the cloud, HIPAA compliance depends on contracts and controls. BAAs must capture how providers handle ongoing access.
Why cloud storage providers are often business associates
Cloud platforms like AWS, Azure, and Google Cloud store PHI on behalf of healthcare clients. That qualifies them as business associates under HIPAA.
Managed service providers, including IT outsourcers and database administrators, often maintain direct access to PHI systems. Their services make them responsible for HIPAA compliance.
Even if subcontractors provide short-term technical support, persistent system access usually makes them business associates. They also require BAAs.
Without contracts, covered entities risk regulatory penalties when cloud providers touch PHI.
Why Encryption is not an exception
Encryption is critical for securing PHI. However, encryption alone does not exempt a vendor from HIPAA when operational access exists.
Support staff may view logs containing identifiers. This indirect exposure creates HIPAA obligations, even with encrypted databases.
Telemetry collected for monitoring can include sensitive information. Without controls, those details count as PHI under HIPAA rules.
A business associate agreement remains necessary whenever vendors can interact with PHI.
Shared responsibility and logging expectations
Cloud vendors manage infrastructure security, while customers control configurations, applications, and access. This division is the shared responsibility model.
BAAs should define how logging works. Logs must be retained, secured, and made available for audits.
Support tickets must avoid containing PHI. If unavoidable, events should be documented in compliance with contract terms.
Clarity in shared accountability builds audit readiness and limits disputes with regulators.
Understanding persistent access scenarios ensures that cloud adoption stays compliant. The next section reviews mistakes that weaken BAAs.
What are the Common BAA Mistakes to Avoid?
Most HIPAA Business Associate Agreements fail due to generic templates, missing details, or vague enforcement. Each gap creates risk for covered entities.
One-size-fits-all templates
Generic sample business associate agreements rarely address unique vendor services. Boilerplate language often leaves PHI risks uncovered.
Without tailoring, BAAs become ineffective. OCR frequently penalizes organizations for using copied contracts with no customization.
Customization makes obligations enforceable and relevant.
Missing data flows
BAAs often miss utilization review processes or marketing data paths. Both can involve PHI and must be explicitly covered.
Unmonitored data flows expose organizations to hidden risks. For example, marketing platforms may hold PHI email lists without oversight.
Mapping and documenting all PHI flows ensures nothing is missed.
Weak safeguards and role confusion
Some BAAs describe security measures vaguely. Without details, controls remain unclear and unenforceable.
Undefined internal practices weaken compliance. Vendors may interpret obligations differently.
Confusion between business associate and covered entity roles causes disputes. Roles must be assigned explicitly in writing.
Poor termination language
Vague termination clauses create compliance failures. PHI may be retained indefinitely without accountability.
Agreements must require return or certified destruction of PHI. Vendors should provide proof of destruction when contracts end.
Strong termination language protects data and reduces liability.
Avoiding these pitfalls keeps BAAs effective and defensible. The next section highlights practical strategies for ongoing contract management.
Operationalizing Your BAAs for HIPAA Compliance
Having BAAs on file is not enough. You must operationalize them so compliance holds across the lifecycle, audits, and daily vendor interactions.
Contract lifecycle management
Drafting starts with a baseline template adapted for vendor services. Approval flows should involve security, legal, and leadership sign-off before execution.
Store signed agreements in a central repository. Renewal schedules must be tracked automatically to prevent expired or outdated contracts from lingering unnoticed.
Termination handling should include certified PHI return or destruction. Without clear closure steps, compliance gaps emerge after relationships end.
Centralizing this lifecycle builds reliability and reduces audit risk.
Evidence for audits
Auditors often ask for proof beyond signed BAAs. You should retain evidence of vendor diligence, training, and incident management.
Vendor diligence includes SOC 2 reports, questionnaires, or penetration test results. These validate the vendor’s security posture.
Training records for staff show you prepared workforce members to handle PHI properly. Incident logs confirm responsive security practices.
Maintaining these records builds defensibility when regulators test compliance rigor.
Training workforce members
Employees who interact with vendors must understand BAA obligations. Training should cover identifying PHI, vendor reporting lines, and incident escalation procedures.
Practical exercises such as mock vendor escalations help reinforce policy. This makes compliance less theoretical and more actionable.
Regular refreshers should be built into onboarding and annual training. A knowledgeable workforce strengthens every contract.
With operations secured, you can now leverage ready-made tools like a HIPAA BAA template to streamline adoption.
Free HIPAA Business Associate Agreement Template
A business associate agreement (BAA) template gives you a reliable starting point. It ensures required clauses are captured without missing critical obligations.
Customizing for your role
If you are a covered entity, emphasize obligations for PHI protection and downstream subcontractor controls.
If you are a business associate, clarify your permitted uses and responsibilities without overcommitting beyond HIPAA requirements.
Customization ensures the template aligns with your actual data flows. Tailoring is the difference between compliance and vulnerability.
Legal review and formats
Always have your legal counsel review the draft before execution. Regulatory expectations shift, and state laws may impose extra obligations.
ComplyJet provides editable formats in both DOCX and Google Docs. This makes revisions practical for your legal and compliance teams.
Download the HIPAA Business Associate Agreement Template (DOCX + GDocs) — by ComplyJet
With templates and operational practices combined, your BAAs become more than contracts. They become enforceable tools for long-term HIPAA compliance.
FAQs
What is a BAA in HIPAA and when do I need one?
A Business Associate Agreement (BAA) is a legal contract required under HIPAA whenever a vendor or partner handles Protected Health Information (PHI) on your behalf. You need one before sharing PHI with billing firms, cloud providers, consultants, or any third party that touches patient data.
Business Associate vs Covered Entity: how do I tell the difference?
A covered entity is a healthcare provider, health plan, or clearinghouse that creates or stores PHI. A business associate supports these entities by performing services that involve PHI. Knowing which role applies helps you assign correct compliance responsibilities in contracts.
Do Cloud Storage Providers need a BAA if data is encrypted?
Yes. Even if data is encrypted, cloud storage providers often qualify as business associates because their staff may access systems, logs, or telemetry that expose PHI. HIPAA requires a BAA whenever persistent or potential access exists.
What are the HIPAA Business Associate Agreement requirements most teams miss?
Teams frequently miss clauses covering subcontractor obligations, breach notification timelines, and the minimum necessary standard for PHI access. These overlooked requirements often appear in OCR enforcement cases and should always be built into your BAAs.
Who signs a BAA at a Healthcare Provider or health plan?
The signatory is usually a compliance officer, general counsel, or authorized executive with contract authority. The signer must understand both HIPAA rules and the organization’s PHI workflows.
What is considered a security incident vs a breach under HIPAA?
A security incident is any attempted or successful unauthorized use of systems. A breach occurs when PHI is compromised, requiring notification to affected individuals, regulators, and sometimes the media, depending on severity.
What is a good business associate agreement template starting point?
A strong starting point is a template that already contains HIPAA-required clauses, such as ComplyJet’s business associate agreement template. It can be customized to reflect your role as a covered entity or business associate, and then reviewed by legal counsel.
How do I manage subcontractors that access PHI?
Subcontractors who touch PHI must also sign BAAs. You should perform due diligence, request SOC 2 or ISO reports, and review risk assessments regularly to confirm they follow HIPAA obligations.
Are there criminal penalties for BAA violations?
Yes. HIPAA allows criminal penalties for willful misuse or disclosure of PHI. Penalties can include significant fines and even jail time, especially for intentional misconduct.
How can I automate BAA tracking and compliance evidence?
Using platforms like ComplyJet, you can centralize BAA storage, automate renewal reminders, and capture vendor diligence evidence. This ensures OCR readiness and reduces manual administrative workload.
Conclusion
Think of your HIPAA Business Associate Agreement as more than paperwork. It’s a live control that reduces your breach exposure and makes audits less painful.
When a vendor mishandles PHI, a strong BAA limits the damage and proves you took compliance seriously.
Ask yourself: when was the last time you reviewed your BAAs? If the answer is “when we first signed them,” you’re already behind.
Regulators expect active oversight, and outdated agreements quickly become liabilities during investigations.
If you want a practical starting point, use ComplyJet’s free business associate agreement template and explore the workflow demo. It shows how centralization, automation, and monitoring can turn BAAs into an advantage rather than an administrative burden.
Relying on spreadsheets or email reminders almost always leads to gaps. Centralizing your BAAs in a single workflow helps you track renewals, capture evidence, and connect obligations across HIPAA, SOC 2, and ISO controls. That way, your contracts actually work for you instead of sitting forgotten in a folder.
Start our Free Trial Right Now!
.png)


